如今,勒索软件(Ransomware)已成为网络世界的严重威胁。世界各地的许多软件公司、大学、公司和组织都在尝试采取预防措施来保护自己免受勒索软件攻击。美国和加拿大政府已(States)就(United) 勒索软件攻击发表联合声明,敦促用户保持警惕并采取预防措施。最近在5 月 19(May 19)日,瑞士政府举办了勒索软件信息日活动(Ransomware Info Day),以传播有关勒索软件及其影响的意识。印度的勒索软件也在增加。
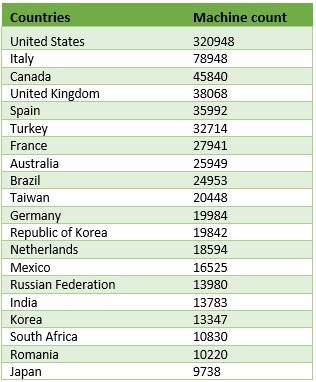
微软(Microsoft)最近发布了一份数据,提到了全球有多少机器(用户)受到勒索软件攻击的影响。发现美国(United) 处于勒索软件攻击的首位;(States)其次是意大利(Italy)和加拿大(Canada)。以下是受勒索软件攻击影响最大的 20 个国家/地区。
这是一篇详细的文章,可以回答您关于勒索软件的大部分问题。这篇文章将介绍什么是勒索软件攻击、勒索软件的类型、勒索软件如何进入您的计算机并建议处理勒索软件的方法。
(Here is a detailed write-up that will answer most of your questions regarding ransomware. This post will take a look at What are Ransomware Attacks, the Types of ransomware, How does ransomware gets on your computer and suggests ways of dealing with ransomware.)
勒索软件攻击
什么是勒索软件
勒索软件(Ransomware)是一种恶意软件,它会锁定您的文件、数据或 PC 本身,并向您勒索金钱以提供访问权限。这是恶意软件编写者为他们在网络上的非法活动“筹集资金”的一种新方式。
勒索软件如何进入您的计算机
如果您单击错误链接或打开恶意电子邮件附件,您可能会获得勒索软件。这张来自Microsoft的图片描述了勒索软件感染是如何发生的。
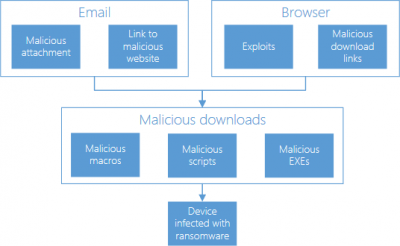
勒索软件(Ransomware)看起来像一个无辜的程序或插件或带有“干净”附件的电子邮件,在用户不知情的情况下被安装。一旦它获得对用户系统的访问权,它就会开始在整个系统中传播。最后,在某个时间点,勒索软件会锁定系统或特定文件并限制用户访问它。有时,这些文件是加密的。勒索软件编写者需要一定数量的资金来提供访问或解密文件。
勒索软件发出的虚假警告消息如下所示:
但是,在勒索软件攻击期间,无法保证即使支付了赎金,用户也能取回文件。因此(Hence),最好防止勒索软件攻击,而不是试图以某种方式取回您的数据。您可以使用RanSim Ransomware Simulator来检查您的计算机是否受到足够的保护。
阅读(Read):在您的 Windows 计算机上遭到勒索软件攻击后该怎么办?(What to do after a Ransomware attack on your Windows computer?)
如何识别勒索软件攻击
勒索软件通常攻击个人数据,例如用户的图片、文档、文件和数据。很容易识别勒索软件(identify the ransomware)。如果您看到勒索软件提示要求您花钱访问您的文件或加密文件、重命名文件、锁定浏览器或锁定您的 PC 屏幕,您可以说勒索软件已经控制了您的系统。
但是,勒索软件攻击的症状可能会根据勒索软件的类型而变化。
阅读(Read):恶意软件跟踪器地图,可让您实时查看网络攻击。(Cyber Attacks)
勒索软件攻击的类型
早些时候,勒索软件曾经显示一条消息,指出用户做了违法的事情,他们正在被警方或政府机构根据某些政策罚款。为了摆脱这些“指控”(这绝对是虚假指控),用户被要求支付这些罚款。
如今,勒索软件的攻击有两种方式。它要么锁定计算机屏幕,要么使用密码加密某些文件。基于这两种类型,勒索软件分为两种:
- 锁屏勒索软件
- 加密勒索软件。
锁屏勒索软件(Lock screen ransomware)会锁定您的系统,并要求您支付赎金才能再次访问它。第二种类型,即加密勒索软件(Encryption ransomware),会更改您系统中的文件并要求金钱再次解密它们。
其他类型的勒索软件是:
- 主引导记录(Master Boot Record)(MBR) 勒索软件
- 勒索软件加密 Web 服务器
- Android 移动设备勒索软件
- 物联网勒索软件。
以下是一些勒索软件家族及其攻击统计数据:
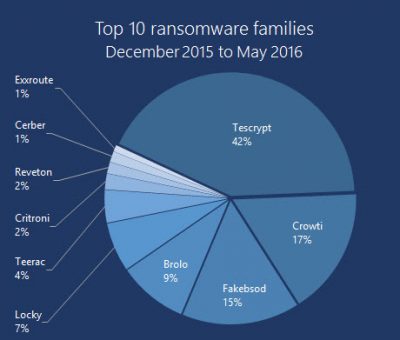
此外,请查看勒索软件的增长及其感染统计数据。
谁会受到勒索软件攻击的影响
无论您身在何处以及使用什么设备都无关紧要。勒索软件(Ransomware)可以随时随地攻击任何人。当您使用互联网进行冲浪、发送电子邮件、工作或在线购物时,勒索软件攻击可能发生在任何移动设备、PC 或笔记本电脑上。一旦它找到通往您的移动设备或 PC 的方法,它就会将其加密和货币化策略应用到该 PC 和移动设备中。
勒索软件什么时候有机会攻击
那么当勒索软件袭击时可能发生的事件是什么?
- 如果您正在浏览不受信任的网站
- 下载或打开从未知电子邮件发件人收到的文件附件(垃圾邮件)。这些附件的一些文件扩展名可以是(.ade、.adp、.ani、.bas、.bat、.chm、.cmd、.com、.cpl、.crt、.hlp、.ht、.hta,.inf,.ins,.isp,.job,.js,.jse,.lnk,.mda,.mdb,.mde,.mdz,.msc,.msi、.msp、.mst、.pcd、.reg、.scr、.sct、.shs、.url、.vb、.vbe、.vbs、.wsc、.wsf、.wsh、.exe、.pif .) 以及支持宏的文件类型(.doc、.xls、.docm、.xlsm、.pptm等)
- 安装盗版软件、过时的软件程序或操作系统
- 登录到属于已感染网络的 PC
勒索软件攻击的预防措施
创建勒索软件的唯一原因是恶意软件编写者将其视为一种简单的赚钱方式。诸如未打补丁的软件、过时的操作系统或人们的无知之类的漏洞对具有恶意和犯罪意图的人是有益的。因此(Hence),意识(awareness)是避免勒索软件攻击的最佳方式。
以下是您可以采取的几个步骤来应对或应对勒索软件攻击:
- Windows 用户建议保持他们的 Windows 操作系统是(System)最新的。如果您升级到Windows 10,您将最大程度地减少勒索软件攻击的事件。
- 始终在外部硬盘驱动器中备份您的重要数据。
- 启用文件历史记录或系统保护。
- 谨防(Beware)网络钓鱼电子邮件、垃圾邮件,并在单击恶意附件之前检查电子邮件。
- 禁用在 Office 程序中加载宏。
- 尽可能禁用您的远程桌面功能。(Desktop)
- 使用双重身份验证。
- 使用安全且受密码保护的互联网连接。
- 避免(Avoid)浏览通常是恶意软件滋生地的网站,例如非法下载网站、成人网站和赌博网站。
- 安装(Install)、使用和定期更新防病毒解决方案
- 利用一些好的反勒索软件(anti-ransomware software)
- 认真对待您的MongoDB 安全,以防止您的数据库被勒索软件劫持。
Ransomware Tracker可帮助您跟踪、减轻和保护自己免受恶意软件的侵害。
阅读(Read):防止和防止勒索软件攻击(Protect against and prevent Ransomware attacks)(Protect against and prevent Ransomware attacks)。
虽然有一些可用的勒索软件解密工具(ransomware decryptor tools),但建议您认真对待勒索软件攻击的问题。它不仅会危及您的数据,而且还会在一定程度上侵犯您的隐私,从而损害您的声誉。
微软(Microsoft)说,
The number of enterprise victims being targeted by ransomware is increasing. The sensitive files are encrypted, and large amounts of money are demanded to restore the files. Due to the encryption of the files, it can be practically impossible to reverse-engineer the encryption or “crack” the files without the original encryption key – which only the attackers will have access to. The best advice for prevention is to ensure confidential, sensitive, or important files are securely backed up in a remote, unconnected backup or storage facility.
如果您碰巧不幸感染了勒索软件,您可以根据需要向FBI、警察(Police)或有关当局报告勒索软件。(report Ransomware)(report Ransomware)
现在阅读Windows 中的勒索软件保护(Ransomware protection in Windows)。
Ransomware Attacks, Definition, Examples, Protection, Removal
Ransomware has become a serious threat to the online world these days. Many software firms, universities, companies, and organizations around the world are trying to take precautionary measures to save themselves from ransomware attacks. The United States and Canadian governments have issued a joint statement about ransomware attacks urging users to stay alert and take precautions. Recently on May 19th, the Swiss government observed the Ransomware Info Day, to spread awareness regarding ransomware and its effects. Ransomware in India too is on the rise.
Microsoft recently published a data mentioning how many machines (users) were affected by ransomware attacks across the world. It was found that the United States was on the top of ransomware attacks; followed by Italy and Canada. Here are the top 20 countries which are majorly affected by ransomware attacks.

Here is a detailed write-up that will answer most of your questions regarding ransomware. This post will take a look at What are Ransomware Attacks, the Types of ransomware, How does ransomware gets on your computer and suggests ways of dealing with ransomware.
Ransomware attacks
What is Ransomware
Ransomware is a type of malware that locks your files, data or the PC itself and extorts money from you in order to provide access. This is a new way for malware writers to ‘collect funds’ for their illegitimate activities on the web.
How does ransomware get on your computer
You could get ransomware if you click on a bad link or open a malicious email attachment. This image from Microsoft describes how the ransomware infection takes place.

Ransomware looks like an innocent program or a plugin or an email with a ‘clean’ looking attachment that gets installed without the user’s knowledge. As soon as it gets its access to the user’s system, it starts spreading across the system. Finally, at one point of time, the ransomware locks the system or particular files and restricts the user from accessing it. Sometimes, these files are encrypted. A ransomware writer demands a certain amount of money to provide access or decrypt the files.
A fake warning message by a ransomware looks as follows:

However, during the ransomware attacks, there is no guarantee that the users will get back their files even after paying the ransom. Hence, it is better to prevent ransomware attacks than trying to get back your data from some way or another. You may use RanSim Ransomware Simulator to check if your computer is sufficiently protected.
Read: What to do after a Ransomware attack on your Windows computer?
How to identify ransomware attacks
The ransomware generally attacks the personal data, such as user’s pictures, documents, files, and data. It is easy to identify the ransomware. If you see a ransomware note demanding money to give access to your files, or encrypted files, renamed files, locked browser or a locked screen of your PC, you can say that ransomware has got a grip on your system.

However, the symptoms of ransomware attacks can change as per the types of ransomware.
Read: Malware Tracker Maps that let you view Cyber Attacks in real-time.
Types of ransomware attacks
Earlier, ransomware used to display a message stating that the user has done something illegal and they are being fined by the police or the government agency on the basis of some policy. To get rid of these ‘charges’ (which were definitely false charges), users were asked to pay these fines.
Nowadays, a ransomware attack in two ways. It either locks the computer screen or encrypts certain files with a password. Based on these two types, the ransomware is divided into two types:
- Lock screen ransomware
- Encryption ransomware.
Lock screen ransomware locks your system and demands a ransom for letting you access it once again. The second type, i.e. the Encryption ransomware, changes the files in your system and demands money to decrypt them again.
The other types of ransomware are:
- Master Boot Record (MBR) ransomware
- Ransomware encrypting web servers
- Android mobile device ransomware
- IoT ransomware.
Here are some ransomware families and their statistics of attacks:

Also, take a look at the Ransomware growth and its infection statistics.
Who can be affected by the ransomware attacks
It doesn’t matter where you are and what device you are using. Ransomware can attack anybody, anytime and anywhere. The ransomware attacks can take place on any mobile device, PC or laptop when you are using the internet for surfing, emailing, working, or shopping online. Once it finds a way to your mobile device or the PC, it will employ its encryption and monetization strategies into that PC and mobile device.
When can ransomware get a chance to attack
So what are the possible events when ransomware can strike?
- If you are browsing untrusted websites
- Downloading or opening file attachments received from unknown email senders (spam emails). Some of the file extensions of these attachments can be, (.ade, .adp, .ani, .bas, .bat, .chm, .cmd, .com, .cpl, .crt, .hlp, .ht, .hta, .inf, .ins, .isp, .job, .js, .jse, .lnk, .mda, .mdb, .mde, .mdz, .msc, .msi, .msp, .mst, .pcd, .reg, .scr, .sct, .shs, .url, .vb, .vbe, .vbs, .wsc, .wsf, .wsh, .exe, .pif.) And also he file types that support macros (.doc, .xls, .docm, .xlsm, .pptm, etc.)
- Installing pirated software, outdated software programs or operating systems
- Logging into a PC that is a part of the already infected network
Precautions against ransomware attacks
The only reason ransomware is created, is because the malware writers see it as an easy way to make money. Vulnerabilities such as unpatched software, outdated operating systems or people’s ignorance is beneficial for such people with malicious and criminal intentions. Hence, awareness is the best way to avoid any attacks by ransomware.
Here are are a few steps you can take to tackle or deal with ransomware attacks:
- Windows users advised keeping their Windows Operating System up-to-date. If you upgrade to Windows 10, you will reduce the events of the ransomware attack to the maximum extent.
- Always back-up your important data in an external hard-drive.
- Enable file history or system protection.
- Beware of phishing emails, spam, and check the email before clicking the malicious attachment.
- Disable the loading of macros in your Office programs.
- Disable your Remote Desktop feature whenever possible.
- Use two-factor authentication.
- Use a safe and password-protected internet connection.
- Avoid browsing websites that are often the breeding grounds for malware such as illegal download sites, adult sites and gambling sites.
- Install, use, and regularly update an antivirus solution
- Make use of some good anti-ransomware software
- Take your MongoDB security seriously to prevent your database from being hijacked by ransomware.
The Ransomware Tracker helps you track, mitigate and protect yourself from malware.
Read: Protect against and prevent Ransomware attacks.
While there are some ransomware decryptor tools available, it is advisable that you take the problem of ransomware attacks seriously. It not only endangers your data, but it can also breach your privacy to such extent that it can harm your reputation also.
Says Microsoft,
The number of enterprise victims being targeted by ransomware is increasing. The sensitive files are encrypted, and large amounts of money are demanded to restore the files. Due to the encryption of the files, it can be practically impossible to reverse-engineer the encryption or “crack” the files without the original encryption key – which only the attackers will have access to. The best advice for prevention is to ensure confidential, sensitive, or important files are securely backed up in a remote, unconnected backup or storage facility.
If you do happen to have the misfortune of being infected with ransomware, you can if you wish, report Ransomware to FBI, Police or appropriate authorities.
Now read about Ransomware protection in Windows.





