您可能听说过DoS和DDoS。这种攻击背后的想法是关闭任何组织的服务器,从而不允许它们向其用户提供服务。通常,组织的主服务器受到如此多的访问请求的攻击而崩溃,从而完全拒绝向任何人提供任何服务。勒索拒绝服务 (RDoS)(Ransom Denial of Service (RDoS))与此类似,只是黑客也兼作敲诈勒索者。让我们看看什么是勒索拒绝(Ransom Denial)服务(Service)( RDoS ),以及如何通过采取足够的预防措施来预防它。
什么是赎金拒绝服务
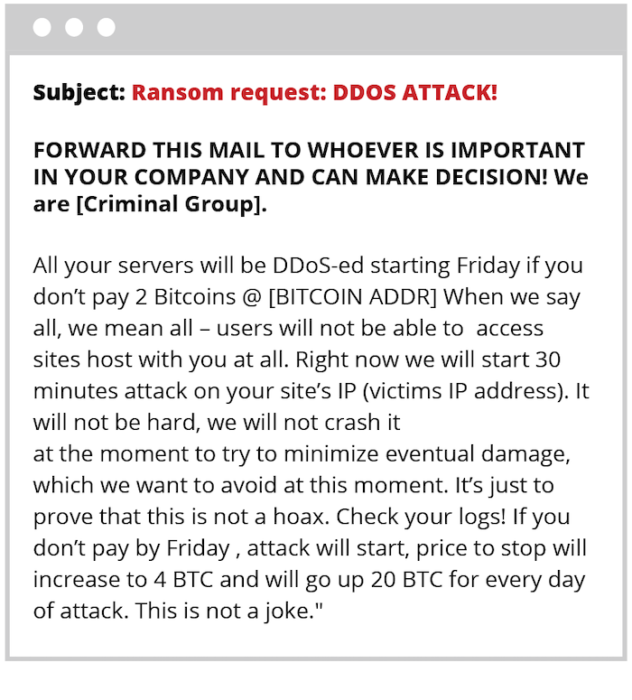
勒索拒绝(Ransom Denial)服务(Service)是指黑客要求您向他们支付一些钱,如果您在特定日期和时间之前不付款,就会威胁发起分布式拒绝服务 (DDoS)攻击。(Distributed Denial of Service (DDoS))
为了表明他们对RDoS攻击的认真态度,他们还可能对他们要求赎金的机构发起一小段时间的DDoS攻击。(DDoS)您可能还听说过勒索软件:黑客在加密任何实体服务器上的所有数据后索取的钱。
在勒索软件的情况下,(Ransomware)黑客首先加密机构的数据,然后发送一张便条要求赎金,说他们(黑客)拿到钱后会解密数据。(AFTER)使用RDoS时,会在代表黑客采取任何行动之前(PRIOR)发送注释。它明确指出,黑客可以访问公司服务器,并在特定日期之前要求一定数量的加密货币(Cryptocurrency)(参见比特币)。(Bitcoins)如果资金没有转移给黑客,他们可能会继续加密机构的数据,也可能会离开。
RDoS利用了对损失的恐惧,并在人们支付费用时帮助黑客避免DDoS攻击。由于只涉及恐惧,业余黑客也开始要钱。他们可能有也可能没有资源来对公司服务器进行DDoS 攻击(DDoS),但要求敲诈并没有害处,除了被抓到并送进监狱的机会。
你应该付钱吗?
专家说你不应该。他们表示,即使一个机构向敲诈的黑客付款,其他黑客也想赚钱。这会鼓励其他黑客,他们也可能会要求赎金(敲诈勒索),说如果不付款,他们将对公司服务器进行DDoS 攻击。(DDoS)
专家还表示,即使支付了敲诈勒索的钱,也不能保证不会发生DDoS攻击或勒索软件攻击。(DDoS)此外,此类行为将鼓励其他黑客。
您是否应该让黑客敲诈勒索者吓到您并支付他们要的钱?不,最好有一个应对这种情况的计划。下一节将讨论如何准备和处理DDoS攻击。如果您有适当的计划,您不必担心DDoS、RDoS、勒索软件或类似的黑客问题。
… but then again – it is a practical decision you will have to take seeing what is at stake for you!
RDoS –(RDoS – Precautions)在受到攻击时防止停机的预防措施
当DDoS在赎金要求后袭击时,做好准备是轻松处理这种情况的关键。这就是为什么需要DDoS保护计划的原因。在规划DDoS保护计划时,假设它是一个常见的过程——也就是说,它会一次又一次地发生。这样,您将能够制定更好的计划。
有些人创建灾难恢复计划(Disaster Recovery Plan)并使用它从DDoS攻击中恢复。但这不是我们的主要目的。我们需要减少到公司网站或网站服务器的流量。
对于业余博客来说,一个小时的停机时间可能并不意味着什么。但对于实时处理服务——银行、网上商店和类似服务——每一秒都很重要。这就是创建DDoS 响应计划(DDoS Response Plan)而不是DDoS 恢复计划(DDoS Recovery Plan)时应牢记的内容。
供您参考,本网站使用Sucuri来保护自己。
创建RDoS或DDoS攻击时要考虑的一些要点是:
- 您的互联网服务提供商(Internet Service Provider)如何帮助您?
- 您的托管服务提供商(Hosting Service Provider)能否帮助您将网站从主机上关闭一段时间(直到DDoS攻击停止)?
- 您是否有第三方安全提供商,例如Susuri、Akamai或Ceroro,可以在DDoS攻击开始时立即检测到它们?这些服务还可以通过识别地理等不同因素来阻止攻击。
- 更改服务器的 IP 地址需要多长时间才能停止攻击(失败)?
- 您是否考虑过在(Did)DDoS发生时可以增加带宽的基于云的计划?增加带宽意味着部分黑客需要付出更多努力。如果您选择无限计划,DDoS攻击会很快停止,因为黑客将不得不安排更多资源来关闭公司服务器
这解释了勒索拒绝(Ransom Denial)服务(Service)( RDoS ) 以及如何准备DDoS攻击。如果您有什么要补充的,请在下方评论。
What is Ransom Denial of Service (RDoS)? Prevention and precautions
Υou might have heard of DoS and DDoS. The idea behind such an attack is to bring down the servers of any organization, thereby not allowing them to provide service to its users. Usually, the main server of the organization is attacked by so many access requests that it crashes, denying any service to anyone at all. Ransom Denial of Service (RDoS) is similar except that the hackers double up as extortionists too. Let’s see what Ransom Denial of Service (RDoS) is, and how to prevent it by taking adequate precautions.

What is Ransom Denial of Service
Ransom Denial of Service is when hackers ask you to pay them some money, threatening to launch a Distributed Denial of Service (DDoS) attack if you don’t pay up before a certain date and time.
To show that they are serious about the RDoS attack, they may also launch a DDoS attack for a small period on the institution from who they are demanding the ransom. You might have also heard of ransomware: money asked by hackers after encrypting all data on any entity’s servers.
In the case of Ransomware, hackers first encrypt an institutions’ data and then send a note to demand ransom saying they’ll decrypt the data AFTER they (the hackers) get the money. With RDoS, the note is sent PRIOR to any action on behalf of the hackers. It states clearly that the hackers have access to company servers, and they ask for a certain amount of money in Cryptocurrency (see Bitcoins) before a specific date. If money is not transferred to the hackers, they may proceed to encrypt the institution’s data or may leave it.
The RDoS employs the fear of loss and helps the hackers as people pay up to avoid a DDoS attack. Since only fear is involved, amateur hackers too, start asking for money. They may or may not have resources to DDoS a company server but there’s no harm in demanding extortions, except the chances of being caught and sent to jail.
Should you pay up?
Experts say that you shouldn’t. They state that if even one institution pays the extortionist hackers, other hackers will also want to earn money. It will encourage other hackers and they too may demand a ransom (extortion money) saying they’ll DDoS the company servers if not paid.
Experts also say that there is no guarantee that there won’t be a DDoS attack or a ransomware attack even if the extortion money is paid. Further, such acts will encourage other hackers.
Should you let the hacker extortionists frighten you and pay them the money they are asking? No. It is always better to have a plan to counter such a scenario. The next section talks about how to prepare and deal with a DDoS attack. If you have a plan in place, you need not fear DDoS, RDoS, ransomware, or similar hacking issues.
… but then again – it is a practical decision you will have to take seeing what is at stake for you!
RDoS – Precautions to prevent downtime when under attack
When a DDoS strikes after ransom demand, being prepared is key to stress-free handling of the situation. That’s why a DDoS protection plan is required. When planning a DDoS protection plan, assume that it is a common procedure – that is, it happens time and again. That way, you will be able to create a better plan.
Some people create a Disaster Recovery Plan and use it to recover from a DDoS attack. But this is not our primary purpose. We need to mitigate the traffic flow to the company website or the website servers.
For an amateur blog, a downtime of an hour may not mean much. But for real-time processing services – banking, online shops, and similar services – each second matters. That’s what you should keep in mind to create a DDoS Response Plan instead of a DDoS Recovery Plan.
For your information, this website uses Sucuri to protect itself.
Some of the important points to consider while creating a RDoS or DDoS attack are:
- How can your Internet Service Provider help you?
- Can your Hosting Service Provider help you by taking the website off the host for a while (Until the DDoS attack stops)?
- Do you have third-party security providers, like Susuri, Akamai or Ceroro that can detect DDoS attacks as soon as they begin? These services can also block the attack by identifying different factors like geography etc.
- How long will it take to change the server’s IP address so that the attack stops (misfires)?
- Did you consider a cloud-based plan that can increase bandwidth when DDoS happens? Increased bandwidth means more efforts on part of the hackers. If you opt for an infinity plan, DDoS attacks stop quickly because the hackers will have to arrange more resources for bringing down the company server
This explains the Ransom Denial of Service (RDoS) and how to prepare for a DDoS attack. If you have anything to add, please comment below.

