边界网关协议(Border Gateway Protocol)或简称BGP有助于跟踪数据包的路由,以便可以使用尽可能少的节点传递数据包。这里的节点,是指所有联合起来创建一个巨大的互联网(Internet)的自治网络。
什么是边界网关协议
当我在学校时,我们班参观了一家邮局,看看它是如何运作的。邮政局长告诉我们,他们按目的地对邮件进行分类,然后将它们放入相应的袋子中。有时不可能有直接的路线,因此一些邮件被转发到目的地附近的邮局,并且该邮局可以通过根据地址转发来传递邮件。
边界网关协议(Border Gateway Protocol)代表一个邮局。可以说是互联网(Internet)的邮局。我们在Internet(Internet)上工作时生成的数据包,必须通过不同的自治网络进行路由,以便它们能够到达目标 IP 地址。互联网(Internet)实际上是许多看起来像一个巨大网络的网络。因此,互联网(Internet)是一个自治网络的网络。这些自治网络由ISP(ISPs)、政府和技术组织等提供。
BGP安全吗?BGP如何被劫持?
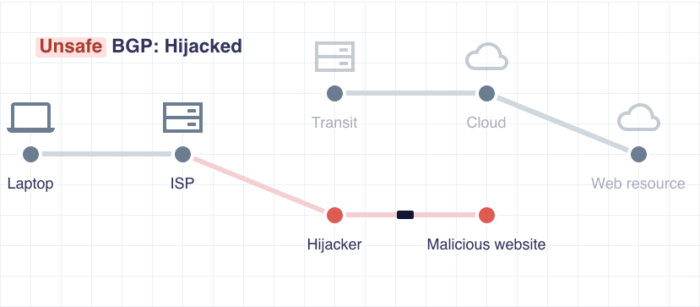
这些自治网络由不同的实体建立,并决定使用Internet的哪些节点,以便数据包到达目的地而不会丢失。但它恰好在路径上有流氓节点通过毒害互联网(Internet)上的一个或多个真实节点来劫持数据路由。
发生的情况是,当数据包要从 A 移动到 B 到 C 到 D 时,其中 D 是目的地,数据包被发送到 A。这个节点联系下一个节点 B,以便它可以被转发到目的地。如果任何劫持者创建了一个假节点 B 并毒害了真正的 B,数据包将从 A 移动到假节点 B。这个恶意节点现在会将数据包重定向到一些看起来相似的恶意网站。
换句话说,边界网关协议(Border Gateway Protocol)在单独使用时并不安全。根据Cloudflare的说法,有一种方法可以更安全地使用Internet,而不会成为劫机者的牺牲品。
资源公钥基础设施(Resource Public Key Infrastructure)( RPKI )
资源公钥基础设施(Resource Public Key Infrastructure)或RPKI是一种保护数据包不被BGP网络劫持的服务。该技术在查询要为数据包采用的路由时采用加密技术。因此,通过边界网关协议(Border Gateway Protocol)( BGP ) 使用(BGP)RPKI有助于保护数据并防止在Internet路由中使用的节点被劫持。
要查看您的Internet 服务提供商(Internet Service Provider)是否正确使用边界网关协议(Border Gateway Protocol),请访问IsBGPsafeyet.com并单击页面上的测试您的 ISP(Test your ISP)按钮。
总结一下:
- BGP是一种协议,它为数据包创建到达目的地的路由
- 如果单独实施BGP(BGP)不是很安全
- RPKI采用加密技术,因此在与(RPKI)边界安全协议(Border Security Protocol)( BGP )结合使用时有助于避免恶意节点。
What is Border Gateway Protocol? Does your ISP use BGP?
Border Gateway Protocol or BGP, for short, helps in tracing the route of data packets so that the packets can be delivered using as few nodes as possible. The nodes here, refer to autonomous networks that are all joined to create one vast Internet.
What is Border Gateway Protocol

When I was in school, our class visited a post office to see how it works. The postmaster told us that they sort mail by destinations and put them in corresponding bags. Sometimes a straight route is not possible, so some mail is forwarded to a post office near to the destination and that post office makes it possible to deliver the mail by sending it forward according to the address.
Border Gateway Protocol represents a post office. You can say it is the post office of the Internet. The data packets we generate while working on the Internet, have to be routed through different autonomous networks so that they can reach the destination IP address. An Internet is actually a lot of networks that look like one huge network. The Internet is thus a network of autonomous networks. These autonomous networks are provided by ISPs, governments, and tech organizations, etc.
Is BGP safe? How can BGP be hijacked?
These autonomous networks are set up by different entities and decide what nodes of the Internet to use so that the data packets reach their destination without getting lost. But it happens that there are rogue nodes on the path that hijack the data route by poisoning one or more real nodes on the Internet.
What happens is, when a data packet is to be moved from A to B to C to D, where D is the destination, the data packet is sent to A. This node contacts the next node, B, so that it can be forwarded to the destination. If any hijacker creates a fake node B and poisons the real B, the data packet will move from A to the fake node B. This malicious node will now redirect the data packets to some similar-looking malicious website.
In other words, the Border Gateway Protocol is not safer when used only by itself. There is a method according to Cloudflare that makes it safer to use the Internet without falling prey to hijackers.
Resource Public Key Infrastructure (RPKI)
The Resource Public Key Infrastructure or RPKI is a service that protects data packets from being hijacked on BGP networks. This technique employs cryptography when querying for the route to be taken for the data packets. Thus, using RPKI over Border Gateway Protocol (BGP) helps in securing data and prevents the hijack of nodes being used in an Internet route.
To see if your Internet Service Provider is using Border Gateway Protocol properly, visit IsBGPsafeyet.com and click Test your ISP button on the page.
To sum up:
- BGP is a protocol that creates a route for data packets to reach their destination
- BGP is not very safe if implemented alone
- RPKI employs cryptography so helps in avoiding malicious nodes when used in combination with the Border Security Protocol (BGP).

