Windows 10 提供了一个内置的网络嗅探器工具(Network Sniffer Tool)— PktMon.exe — 来监控内部数据包传播和数据包丢弃报告。这个工具可以帮助你窥探。网络并帮助您解决网络延迟的原因,识别受影响的应用程序,并且在与一组额外的工具一起使用时,可以提供对主要指标的洞察。在这篇文章中,我们将展示如何在Windows 10中使用新的(Windows 10)网络嗅探器工具(Network Sniffer Tool)( PktMon.exe ) 。
(Network Sniffer Tool)Windows 10中的(Windows 10)网络嗅探器工具pktmon.exe
PktMon.exe或Packet Monitor是新的网络嗅探器或网络诊断和数据包监控工具。它位于Systems文件夹中,这意味着您可以从Run或Command Prompt或PowerShell调用它。
如果程序提醒您有关Netsh Trace命令,那么您是对的。Netsh Trace命令可帮助您启用和配置网络跟踪,以帮助您解决网络连接问题。
PktMon 能做什么?
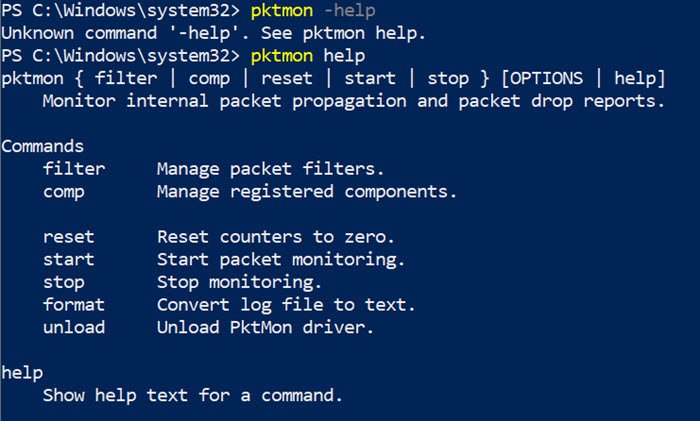
如果在命令提示符下运行 PktMon.exe 帮助(PktMon.exe Help)。这是你得到的:
- filter:管理数据包过滤器。
- comp:管理注册的组件。
- 重置:将(reset:)计数器重置为零。
- start:开始数据包监控。
- 停止:(stop:)停止监控。
- 格式:(format:)将日志文件转换为文本。
- unload:卸载 PktMon 驱动程序。
如果您需要有关特定命令的进一步帮助,则可以针对该命令运行帮助。这是它的样子:
pktmon filter help
pktmon filter { list | add | remove } [OPTIONS | help]
Commands
list Display active packet filters.
add Add a filter to control which packets are reported.
remove Removes all filters.
PktMon.exe 还带有对 PCAPNG文件格式的实时监控和支持。
阅读(Read):如何在 Windows 10 中通过 HTTPS 启用和测试 DNS(How to enable and test DNS over HTTPS in Windows 10)。
如何使用PktMon监控网络流量
这是一个如何通过一个简单示例使用它的示例。
- 创建过滤器来监控端口
- 开始监控
- 将日志导出为可读格式
此示例假设您要监视计算机上的端口号,这可能经常出现问题。
1.创建过滤器
允许您监控流量的主要选项是 —filter。使用此选项,您可以创建一个过滤器,以根据以太网帧(Ethernet Frame)、IP 标头、TCP标头和封装(Encapsulation)来控制报告哪些数据包。如果您运行下面提到的程序,您将获得有关您可以使用过滤器做什么的完整详细信息。
pktmon filter add help
回到我们的话题,假设我们要监控 TCP 端口(monitor TCP port)号 1088。它可能是您的自定义应用程序使用的端口,它正在崩溃,PktMon可以帮助您确定网络是否有问题。
使用管理员权限打开命令提示符(Command Prompt)或PowerShell
使用命令创建数据包过滤器:“pktmon filter add -p [port]”
pktmon filter add -p 1088
然后,您可以运行命令“pktmon filter list”来查看添加的过滤器列表。

要删除所有过滤器,请运行命令“pktmon filter remove”
2.开始监控
由于这不是在后台运行的自动化程序,而是按需运行,因此您需要手动启动监控。运行以下命令开始监控数据包
pktmon start --etw - p 0
它将开始监控并在提到的位置创建一个日志文件。您必须手动停止使用“停止”参数来停止记录,否则它将在计算机关闭时结束。如果您使用“-p 0”运行该命令,那么它将仅捕获 128 个字节的数据包。
Log filename: C:\Windows\system32\PktMon.etl
Logging mode: Circular
Maximum file size: 512 MB
3. 将日志(Log)导出为可读格式
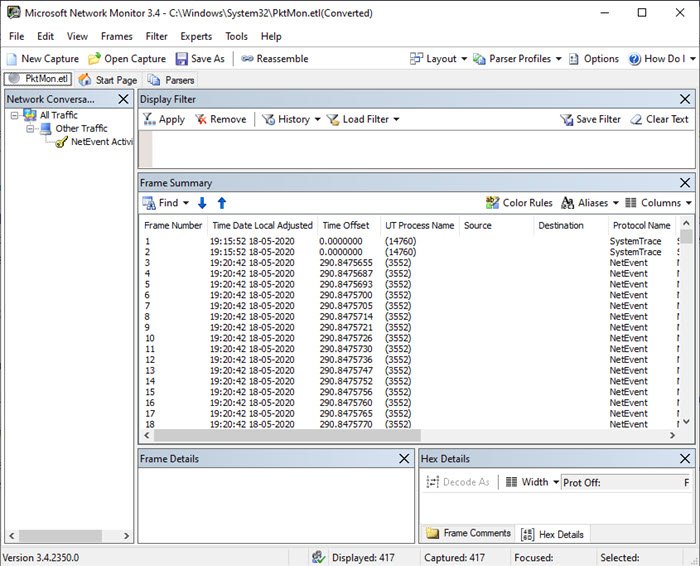
日志文件保存到PktMon.ETL文件中,可以使用以下命令将其转换为人类可读的格式
pktmon format PktMon.etl -o port-monitor-1088.txt
完成此操作后,当您在记事本中打开文件并阅读它时,为了有意义,您将不得不使用Microsoft 网络监视器。 它可以直接读取ETL文件。
也就是说,微软(Microsoft)预计将开始推出对实时监控的支持,这在Windows 10 2004 中是预期的——但我还没有看到那个选项。
相关阅读(Related read):适用于 Windows 10 的免费数据包嗅探工具(Free Packet Sniffing Tools)。
How to use Network Sniffer Tool PktMon.exe in Windows 10
Windows 10 offers an inbuilt Network Sniffer Tool — PktMon.exe — to monitor internal packet propagation and packet drop reports. This tool can help you snoop around. The network and help you resolve the cause of network latency, identify impacted applications, and, when used with an additional set of tools, can provide insight into top metrics. In this post, we will show how you can use the new Network Sniffer Tool (PktMon.exe) in Windows 10.
Network Sniffer Tool pktmon.exe in Windows 10
PktMon.exe or Packet Monitor is the new network sniffer or network diagnostic and packet monitoring tool. It is located in the Systems folder, which means you can invoke it from the Run or Command Prompt or PowerShell.
If the program reminds you about Netsh Trace Command, then you are right. Netsh Trace command helps you to enable and configure network tracing to assist you when troubleshooting network connectivity problems.

What can PktMon can do?
If you run PktMon.exe Help on the command prompt. Here is what you get:
- filter: Manage packet filters.
- comp: Manage registered components.
- reset: Reset counters to zero.
- start: Start packet monitoring.
- stop: Stop monitoring.
- format: Convert log file to text.
- unload: Unload PktMon driver.
And if you want further help on a specific command, then you can run help against that command. Here is how it looks like:
pktmon filter help
pktmon filter { list | add | remove } [OPTIONS | help]
Commands
list Display active packet filters.
add Add a filter to control which packets are reported.
remove Removes all filters.
PktMon.exe also comes with real-time monitoring and support for the PCAPNG file format.
Read: How to enable and test DNS over HTTPS in Windows 10.
How to use PktMon to monitor network traffic
Here is an example of how to use it with a simple example.
- Create a Filter to monitor a port
- Start Monitoring
- Export Log into a readable format
This example is assuming that you want to monitor a port number on the computer, which might be having issues often.
1. Create a Filter
The primary option which allows you to monitor traffic is —filter. Using this option, you can create a filter to control which packets are reported based on Ethernet Frame, IP header, TCP header, and Encapsulation. If you run the below-mentioned program, you will get full details on what you can do with the filter.
pktmon filter add help
So coming back to our topic, let’s assume that we are going to monitor TCP port no 1088. It can be a port used by your custom application, which is crashing, and PktMon can help you figure out if the network is the problem.
Open Command Prompt or PowerShell with admin privileges
Create a packet filter using the command: “pktmon filter add -p [port]”
pktmon filter add -p 1088
You can then run the command “pktmon filter list” to see a list of added filters.

To remove all the filters run the command “pktmon filter remove”
2. Start Monitoring
Since this is not an automated program running in the background but works on-demand, you need to start monitoring manually. Run the following command to start monitoring packets
pktmon start --etw - p 0
It will start the monitoring and created a log file at the mentioned location. You will have to manually stop using the “stop” argument to stop the logging, or it will end when the computer shuts down. If you run the command with “-p 0” then it will only capture 128 bytes of a packet.
Log filename: C:\Windows\system32\PktMon.etl
Logging mode: Circular
Maximum file size: 512 MB
3. Export Log into a readable format

The log file is saved into PktMon.ETL file which can be converted into a human-readable format using the following command
pktmon format PktMon.etl -o port-monitor-1088.txt
Having done that, while you open the file in notepad, and read it, to make sense, you will have to use the Microsoft Network Monitor. It can directly read the ETL file.
That said, Microsoft is expected to start rolling out support for real-time monitoring, which was expected in Windows 10 2004 – but I do not see that that option yet.
Related read: Free Packet Sniffing Tools for Windows 10.



