Thunderbolt是Intel开发的硬件品牌接口。它充当计算机和外部设备之间的接口。虽然大多数Windows计算机都带有各种端口,但许多公司使用Thunderbolt连接到各种类型的设备。它使连接变得容易,但根据埃因霍温(Eindhoven University)科技(Technology)大学的研究, Thunderbolt背后的安全性可以使用一种技术——Thunderspy 来破坏(Thunderspy)。在这篇文章中,我们将分享您可以遵循的提示,以保护您的计算机免受Thunderspy攻击。
什么是Tunderspy?它是如何工作的?
它是一种隐形攻击,允许攻击者访问直接内存访问 ( DMA ) 功能来破坏设备。最大的问题是没有任何痕迹,因为它在没有部署任何恶意软件或链接诱饵的情况下工作。它可以绕过最佳安全实践并锁定计算机。那么它是怎样工作的?攻击者需要直接访问计算机。根据研究,使用正确的工具只需不到 5 分钟。
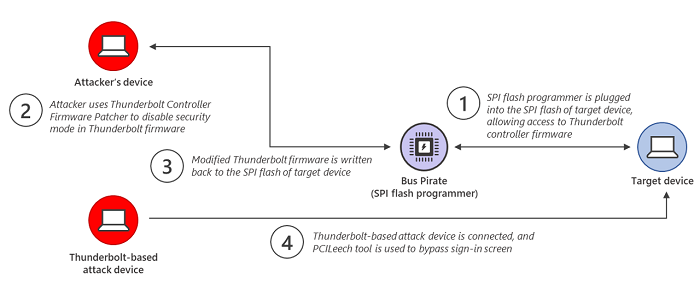
攻击者将源设备的Thunderbolt 控制器固件(Thunderbolt Controller Firmware)复制到他的设备。然后,它使用固件修补程序 ( TCFP ) 禁用Thunderbolt固件中强制执行的安全模式。使用Bus Pirate(Bus Pirate)设备将修改后的版本复制回目标计算机。然后基于Thunderbolt的攻击设备连接到被攻击的设备。然后,它使用PCILeech工具加载绕过Windows登录屏幕的内核模块。
因此,即使计算机具有安全启动(Secure Boot)、强大的BIOS和操作系统帐户密码等安全功能,并启用了全盘加密,它仍然会绕过一切。
提示(TIP):Spycheck 将检查您的 PC 是否容易受到 Thunderspy 攻击。
防范 Thunderspy 的提示
Microsoft推荐(recommends)了三种方法来防御现代威胁。可以利用 Windows 中内置的一些功能,而应该启用一些功能来缓解攻击。
- 安全核心 PC 保护
- 内核 DMA 保护
- 受管理程序保护的代码完整性 ( HVCI )
也就是说,这一切都可以在 Secured-core PC 上实现。您根本无法在普通 PC 上应用此功能,因为没有可用的硬件来保护它免受攻击。确定您的 PC 是否支持它的最佳方法是检查Windows 安全(Windows Security)应用程序的设备安全(Devic Security)部分。
1] 安全核心 PC 保护
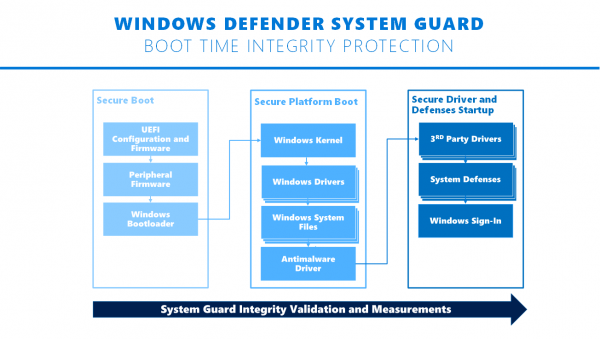
Windows Security是 Microsoft 的内部安全软件,提供Windows Defender System Guard和基于虚拟化的安全性。但是,您需要一台使用Secured-core PC(Secured-core PCs)的设备。它使用现代CPU中的根深蒂固的硬件安全性将系统启动到受信任状态。它有助于减轻恶意软件在固件级别的尝试。
2]内核DMA保护
在Windows 10 v1803中引入的内核 DMA(Kernel DMA)保护可确保阻止外部外围设备使用PCI热插拔设备(如Thunderbolt )进行直接(Thunderbolt)内存访问(Memory Access)( DMA ) 攻击。这意味着如果有人试图将恶意的Thunderbolt固件复制到机器上,它将通过Thunderbolt端口被阻止。但是,如果用户有用户名和密码,他将能够绕过它。
3]使用Hypervisor 保护的(Hypervisor-protected)代码完整性 ( HVCI )强化保护(Hardening)
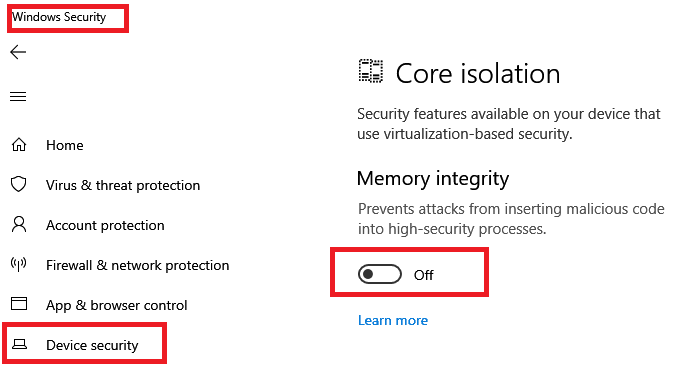
应在Windows 10上启用受 Hypervisor 保护的代码完整性或HVCI。它隔离代码完整性子系统并验证内核(Kernel)代码没有经过Microsoft验证和签名。它还确保内核代码不能既可写又可执行,以确保未验证的代码不会执行。
Thunderspy使用PCILeech工具加载绕过Windows登录屏幕的内核模块。使用HVCI将确保防止这种情况发生,因为它不允许它执行代码。
在购买计算机时,安全性应始终放在首位。如果您处理重要的数据,尤其是业务数据,建议购买Secured-core PC设备。这是微软网站上此类设备的官方页面。(such devices)
Tips to protect your computer against Thunderspy attack
Thunderbolt is the hardware brand interface developed by Intel. It acts as an interface between computer and external devices. While most of the Windows computers come with all sorts of ports, many companies use Thunderbolt to connect to various types of devices. It makes connecting easy, but according to research at the Eindhoven University of Technology, the security behind Thunderbolt can be breached using a technique — Thunderspy. In this post, we will share tips you can follow to protect your computer against Thunderspy.
What is Tunderspy? How does it work?
Its a stealth attack that allows an attacker to access direct memory access (DMA) functionality to compromise devices. The biggest problem is that there is no trace left as it works without deploying any mind of malware or link bait. It can bypass the best security practices and lock the computer. So how does it work? The attacker needs direct access to the computer. According to the research, it takes less than5 minutes with the right tools.

The attacker copies the Thunderbolt Controller Firmware of the source device to his device. It then uses a firmware patcher (TCFP) to disable the security mode enforced in the Thunderbolt firmware. The modified version is copied back to the target computer using the Bus Pirate device. Then a Thunderbolt-based attack device is connected to the device being attacked. It then uses the PCILeech tool to load a kernel module that bypasses the Windows sign-in screen.
So even if the computer has security features like Secure Boot, strong BIOS, and operating system account passwords, and enabled full disk encryption, enabled, it will still bypass everything.
TIP: Spycheck will check if your PC is vulnerable to the Thunderspy attack.
Tips to protect against Thunderspy
Microsoft recommends three ways to protect against the modern threat. Some of these features that are built into Windows can be leveraged while some should be enabled to mitigate the attacks.
- Secured-core PC protections
- Kernel DMA protection
- Hypervisor-protected code integrity (HVCI)
That said, all this is possible on a Secured-core PC. You simply cannot apply this on a regular PC because the hardware is not available that can secure it from the attack. The best way to find out if your PC supports it is by checking the Devic Security section of the Windows Security app.
1] Secured-core PC protections

Windows Security, Microsoft’s in-house security software, offers Windows Defender System Guard and virtualization-based security. However, you need a device that uses Secured-core PCs. It uses rooted hardware security in the modern CPU to launch the system into a trusted state. It helps mitigate attempts made by malware at the firmware level.
2] Kernel DMA protection
Introduced in Windows 10 v1803, Kernel DMA protection makes sure to block external peripherals from Direct Memory Access (DMA) attacks using PCI hotplug devices such as Thunderbolt. It means if someone tries to copy malicious Thunderbolt firmware to a machine, it will be blocked over the Thunderbolt port. However, if the user has the username and password, he will be able to bypass it.
3] Hardening protection with Hypervisor-protected code integrity (HVCI)

Hypervisor-protected code integrity or HVCI should be enabled on Windows 10. It isolates the code integrity subsystem and verified that there Kernel code is not verified and signed by Microsoft. It also ensures that kernel code cannot be both writable and executable to make sure unverified code does not execute.
Thunderspy uses the PCILeech tool to load a kernel module that bypasses the Windows sign-in screen. Using HVCI will make sure to prevent this as it will not allow it to execute the code.
Security should always be at the top when it comes to buying computers. If you deal with data that is important, especially with business, it is recommended to purchase Secured-core PC devices. Here is the official page of such devices on the Microsoft website.



