Windows 10/8 包含一项名为Secure Boot的新安全功能,该功能可保护Windows启动配置和组件,并加载Early Launch Anti-malware ( ELAM ) 驱动程序。此驱动程序在其他引导启动驱动程序之前启动,并启用对这些驱动程序的评估,并帮助Windows 内核(Windows kernel)决定是否应初始化它们。通过内核首先启动,ELAM确保它在任何其他第三方软件之前启动。因此,它能够在启动过程中检测恶意软件并阻止其加载或初始化。
早期启动反恶意软件(Launch Anti-Malware)保护
Windows Defender利用 Early-Launch Anti-Malware,因此您会看到它在启动过程完成后不再加载,而是在启动过程的早期加载。
第三方防病毒软件也能够利用ELAM技术。为此,他们必须在其软件中集成相同的早期启动反恶意软件(Early Launch Anti-Malware)( ELAM ) 功能。为了帮助安全软件供应商入门,Microsoft发布了一份白皮书(whitepaper) ,其中提供了有关为Windows开发 Early Launch (Windows)Anti-Malware ( ELAM ) 驱动程序的信息操作系统。它为反恶意软件开发人员开发在其他引导启动驱动程序之前初始化的反恶意软件驱动程序提供了指导,并确保这些后续驱动程序不包含恶意软件。已经发布了针对Windows(Windows)的更新解决方案的几家防病毒公司已经采用了这项技术。
Early Launch Antimalware boot-start 驱动程序将驱动程序分类如下:
- Good : 驱动已签名,未被篡改。
- 坏(Bad):驱动程序已被识别为恶意软件。建议您不要让已知的坏驱动程序被初始化。
- Bad, but required for boot : 驱动程序已被识别为恶意软件,但如果不加载此驱动程序,计算机将无法成功启动。
- 未知(Unknown):此驱动程序尚未被您的恶意软件检测应用程序证明,也未被 Early Launch Antimalware启动驱动程序分类。
默认情况下,Windows 10 会加载那些分类为Good、Unknown和Bad but Boot Critical的驱动程序;即上面的1、3和4。不加载错误的驱动程序。(Bad)
使用组策略编辑器(Group Policy Editor)配置引导启动驱动程序初始化策略(Boot-Start Driver Initialization Policy)
虽然最好将此设置保留为默认值,但如果您愿意,可以通过组策略编辑器(Group Policy Editor)更改此设置。为此,请打开WinX菜单> Run > gpedit.msc > Hit Enter。导航(Navigate)到以下策略设置:
Computer Configuration > Administrative Templates > System > Early Launch Antimalware
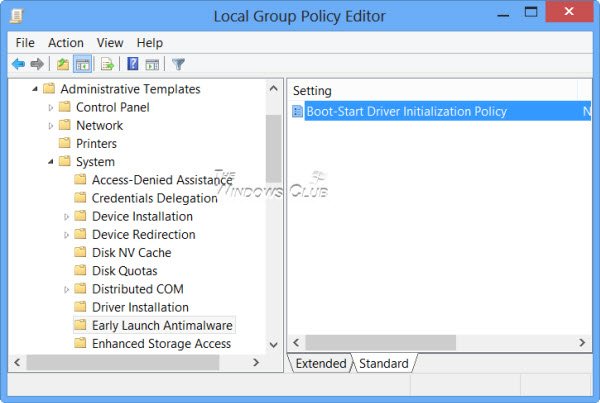
在右侧窗格中,双击 Boot-Start Driver Initialization Policy进行配置。
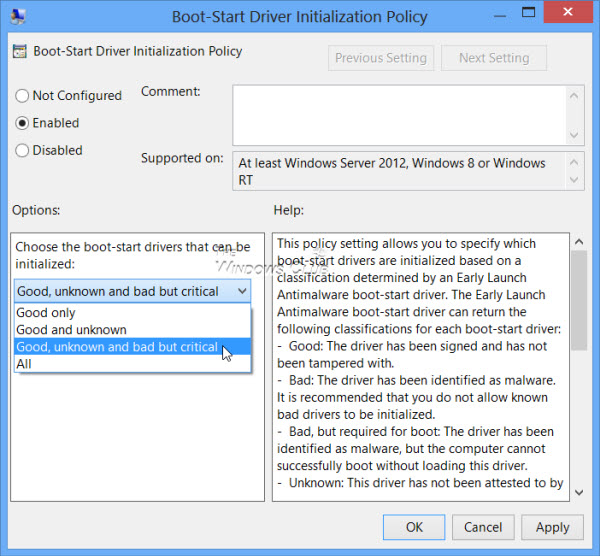
您将看到未配置的默认配置(Not Configured)。如果您禁用或未配置此策略设置,则会初始化确定为 Good、Unknown或Bad但Boot Critical的引导启动驱动程序,并跳过确定为Bad的驱动程序的初始化。
如果启用(Enable)此策略设置,您将能够选择下次启动计算机时要初始化哪些引导启动驱动程序。
如果您使用的是Windows 10/8,则需要检查您的反恶意软件是否包含 Early Launch Antimalware启动驱动程序。否则,所有引导启动驱动程序都将被初始化,您将无法利用这项新的ELAM技术。
Early Launch Anti-Malware (ELAM) protection technology in Windows 10
Windows 10/8 includes a new security feature called Secure Boot, which protects the Windows boot configuratіon and components, and lоads аn Early Launch Anti-malware (ELAM) driver. This driver starts before other boot-start drivers and enables the evaluation of those drivers and helps the Windows kernel decide whether they should be initialized. By being launched first by the kernel, ELAM is ensured that it is launched before any other third-party software. It is, therefore, able to detect malware in the boot process itself and prevent it from loading or initializing.
Early Launch Anti-Malware protection
Windows Defender takes advantage of Early-Launch Anti-Malware, and you, therefore, see that it no longer loads after the start-up process is complete, but early on during the boot process.
Third-party antivirus software too, is able to take advantage of the ELAM technology. To do so, they will have to integrate the same Early Launch Anti-Malware (ELAM) capability in their software. To help security software vendors get started, Microsoft has released a whitepaper that provides information about developing Early Launch Anti-Malware (ELAM) drivers for Windows operating systems. It provides guidelines for anti-malware developers to develop anti-malware drivers that are initialized before other boot-start drivers, and ensure that those subsequent drivers do not contain malware. Several antivirus companies, who have released their updated solutions for Windows already incorporate this technology.
The Early Launch Antimalware boot-start driver has classified the drivers as follows:
- Good: The driver has been signed and has not been tampered with.
- Bad: The driver has been identified as malware. It is recommended that you do not allow known bad drivers to be initialized.
- Bad, but required for boot: The driver has been identified as malware, but the computer cannot successfully boot without loading this driver.
- Unknown: This driver has not been attested to by your malware detection application and has not been classified by the Early Launch Antimalware boot-start driver.
By default, Windows 10 loads those drivers which have been classified as Good, Unknown, and Bad but Boot Critical; ie 1, 3 and 4 above. Bad drivers are not loaded.
Configure Boot-Start Driver Initialization Policy using Group Policy Editor
While this setting is best left at its default value, if you wish, you can change this setting via your Group Policy Editor. To do so, open the WinX menu > Run > gpedit.msc > Hit Enter. Navigate to the following policy setting:
Computer Configuration > Administrative Templates > System > Early Launch Antimalware

In the right pane, double-click on Boot-Start Driver Initialization Policy to configure it.

You will see the default configuration of Not Configured. If you disable or do not configure this policy setting, the boot-start drivers determined to be Good, Unknown or Bad but Boot Critical are initialized, and the initialization of drivers determined to be Bad is skipped.
If you Enable this policy setting, you will be able to choose which boot-start drivers to initialize the next time the computer is started.
If you are using Windows 10/8, you want to check if your anti-malware software includes an Early Launch Antimalware boot-start driver. If it doesn’t, all boot-start drivers will be initialized, and you will not be able to take advantage of this new ELAM technology.


