Windows Applocker是在 Windows 7 中引入的,并在Windows 11/10/8中包含一些新功能。使用AppLocker,管理员可以阻止或允许某些用户或用户组安装或使用某些应用程序。您可以使用黑名单规则或白名单规则来实现此结果。AppLocker帮助管理员控制用户可以运行哪些应用程序和文件。其中包括可执行文件、脚本、Windows 安装程序(Windows Installer)文件、DLL(DLLs)、打包(Packaged)应用程序和打包(Packaged)应用程序安装程序。
Windows AppLocker阻止用户安装或运行应用程序
在Windows 10和Windows 8.1中,Applocker已经发展并允许您阻止旧版以及 Windows 应用商店(Windows Store)应用程序。
如何在Windows 11/10AppLocker
要防止用户在 Windows 中使用AppLocker安装或运行(AppLocker in Windows)Windows 应用商店应用程序(Windows Store Apps),请在运行(Run)中键入secpol.msc并按Enter以打开本地安全策略编辑器(Local Security Policy Editor)。
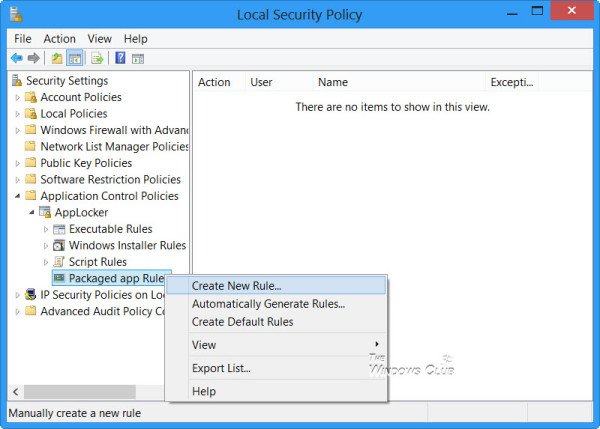
在控制台树中,导航到Security Settings > Application Control Policies > AppLocker。
选择(Select)要创建规则的位置。这可能适用于 Executable、Windows Installer、Scripts或在Windows 10的情况下,Windows Store打包应用程序。
假设您要为打包(Packaged)应用创建规则。右键单击打包(Packaged)的应用程序并选择创建规则(Create Rule)。您将看到“开始之前”页面(Before You Begin page)。
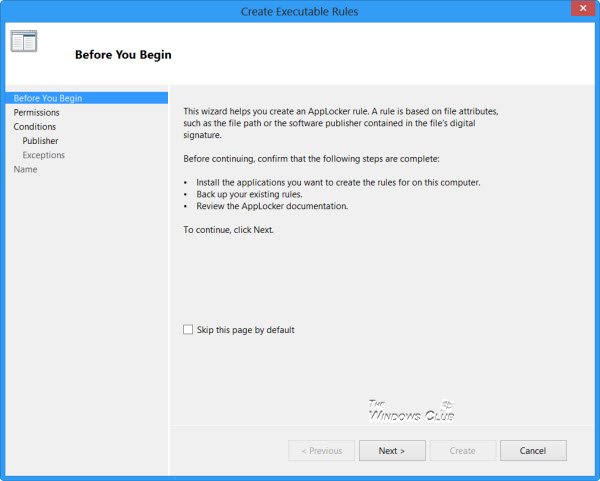
单击“下一步”进入“权限”页面(Permissions page)。
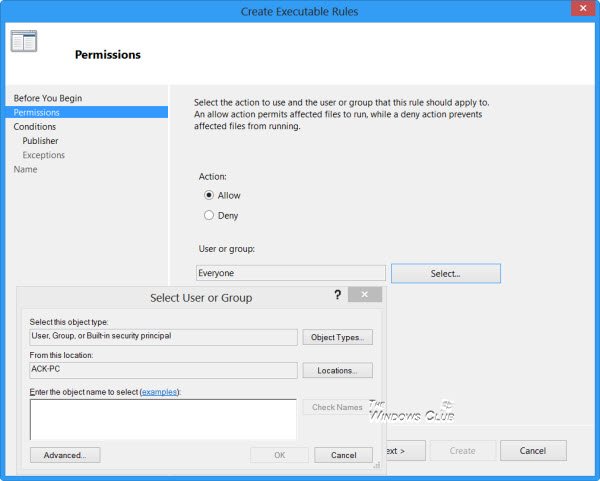
在此页面上,选择操作即。允许或拒绝(Deny)以及您希望规则应用的用户(User)或用户组。(User Group)单击下一步(Click Next)进入条件页面(Conditions page)。
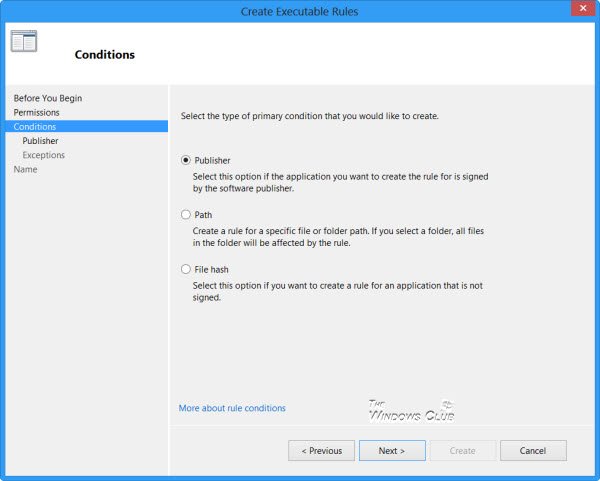
选择您希望如何创建规则 - 基于 Publishers、File Path或Has。我选择了 Publishers,这是默认设置。
单击“下一步”进入“发布者”页面(Publisher page)。
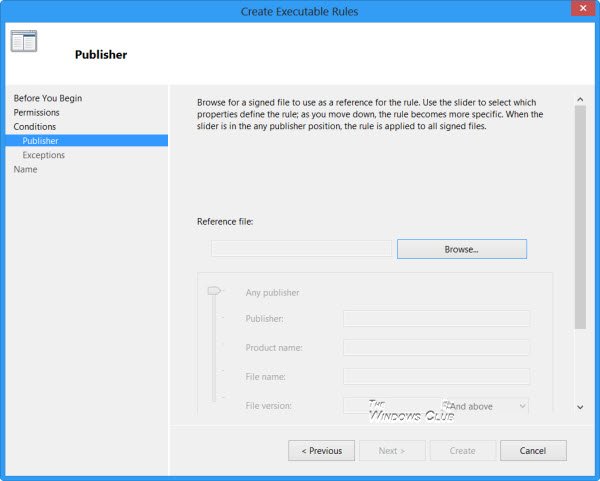
您可以在此处浏览并选择打包应用程序的参考(Reference)并设置规则的范围(Scope)。
范围设置包括:(Settings for Scope include:)
- 适用于任何出版商
- 适用于特定发布者
- 适用于包名称
- 适用于包版本
- 将自定义值应用于规则
参考选项包括:(The options for Reference include:)
- 使用(Use)已安装的打包应用程序作为参考
- 使用打包的应用安装程序作为参考
做出选择后,再次单击下一步(Next)。
如果您愿意,可以在Exceptions 页面上(Exceptions page)指定排除规则的条件,在Name and Description 页面上(Name and Description page),您可以接受自动生成的规则名称或键入新的规则名称,然后单击Create。您可以在Technet上阅读有关为打包的 Windows 应用商店(Packaged Windows Store)应用程序创建规则的更多信息。
请注意,要让AppLocker在您的系统上运行,应用程序身份服务(Application Identity service)必须在您的计算机上运行。此外,运行AppLOcker所需的组策略客户端服务gpsvc 在(Group Policy Client service)Windows RT上默认禁用,因此您可能必须通过 services.msc 启用它。
Windows 11/10和Windows 7中的AppLocker之间的区别
Windows 10中的AppLocker还允许您为打包的 Windows 应用商店(Packaged Windows Store)应用创建规则。此外,Windows 10/8AppLocker规则还可以额外控制.mst 和.appx文件格式。
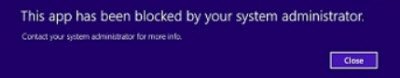
此应用已被您的系统管理员屏蔽
如果作为用户,您发现当您启动任何Windows 应用商店(Windows Store)应用程序(或传统软件)时,您会收到消息:此应用程序已被系统管理员阻止(This app has been blocked by your system administrator),您必须联系您的管理员(Administrator)并要求他创建规则以允许您使用(或安装)软件。
要创建和实施AppLocker规则,计算机必须运行Windows 11/10 /10 、Windows 8 Enterprise、Windows 7 Ultimate、Windows 7 Enterprise、Windows Server 2008 R2 或Windows Server 2012。
您还可以使用注册表(Registry)或组策略(Group Policy)阻止用户安装或运行程序。
PS: Windows Program Blocker是一款免费的App或Application Blocker 软件,用于阻止软件在Windows 10/8/7上运行。
Windows AppLocker prevents users from installing or running applications
Windows Applocker was introduced in Windows 7 and includes some new features in Windows 11/10/8. With AppLocker, an administrator can block or allow certain users or user groups from installing or using certain applications. You can use blacklisting rules or whitelisting rules to achieve this result. AppLocker helps administrators control which applications and files users can run. These include executable files, scripts, Windows Installer files, DLLs, Packaged apps, and Packaged app installers.
Windows AppLocker prevents users from installing or running applications
In Windows 10 and Windows 8.1, Applocker has evolved and lets you block legacy as well as Windows Store apps.
How to use AppLocker in Windows 11/10
To prevent users from installing or running Windows Store Apps with AppLocker in Windows, type secpol.msc in Run and hit Enter to open the Local Security Policy Editor.

In the console tree, navigate to Security Settings > Application Control Policies > AppLocker.
Select where you want to create the rule. This could be for an Executable, Windows Installer, Scripts or in the case of Windows 10, a Windows Store packaged app.
Let us say you want to create a rule for Packaged apps. Right-click on Packaged apps and select Create Rule. You will see a Before You Begin page.

Click Next to reach the Permissions page.

On this page, select the action viz. Allow or Deny and the User or User Group you want the rule to apply. Click Next to reach the Conditions page.

Select how you want to create the rules – base on Publishers, File Path, or Has. I have selected Publishers, which is the default.
Click Next to reach the Publisher page.

Here you can browse for and select a Reference for the Packaged app and set the Scope for the rule.
Settings for Scope include:
- Applies to Any publisher
- Applies to a specific Publisher
- Applies to a Package name
- Applies to a Package version
- Applying custom values to the rule
The options for Reference include:
- Use an installed packaged app as a reference
- Use a packaged app installer as a reference
After making your selections, click Next again.
If you wish, on the Exceptions page you may specify conditions when to exclude the rules, and on the Name and Description page, you can accept the automatically generated rule name or type a new rule name, and click Create. You can read more about creating rules for Packaged Windows Store apps here at Technet.
Do note that for the AppLocker to work on your system, the Application Identity service must be running on your computer. Also, the Group Policy Client service, gpsvc, required for running AppLOcker, is disabled by default on Windows RT, so you may have to enable it via services.msc.
Difference between AppLocker in Windows 11/10 & Windows 7
The AppLocker in Windows 10 allows you to also create rules for Packaged Windows Store apps. Moreover, the Windows 10/8 AppLocker rules can also additionally control the .mst and .appx file formats.
This app has been blocked by your system administrator
If as a user, you find that when you start any Windows Store app (or traditional software) you receive the message: This app has been blocked by your system administrator, you will have to contact your Administrator and ask him to create rules to allow you to use (or install) the software.

To create and enforce AppLocker rules, the computer must be running Windows 11/10, Windows 8 Enterprise, Windows 7 Ultimate, Windows 7 Enterprise, Windows Server 2008 R2 or Windows Server 2012.
You can also block users from installing or running programs using the Registry or Group Policy.
PS: Windows Program Blocker is a free App or Application blocker software to block software from running on Windows 10/8/7.






