在早期,如果有人不得不劫持您的计算机,通常可以通过亲自到场或使用远程访问来控制您的计算机。虽然世界在自动化方面取得了进展,但计算机安全性已经加强,但没有改变的一件事是人为错误。这就是人为操作的勒索软件攻击(Human-operated Ransomware Attacks)出现的地方。这些是人为的攻击,可以在计算机上发现漏洞或错误配置的安全性并获得访问权限。微软(Microsoft)提出了一个详尽的案例研究,得出的结论是,IT 管理员可以大大减轻这些人为勒索软件的攻击。(Ransomware attacks)
减轻人为勒索软件攻击(Human-operated Ransomware Attacks)
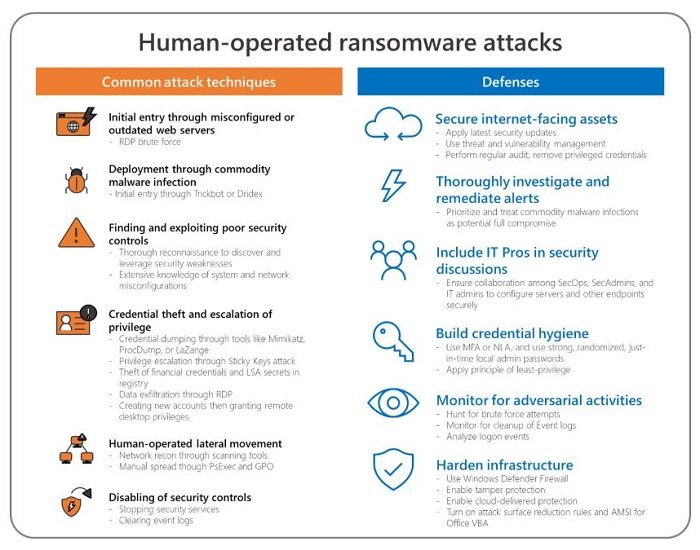
根据Microsoft的说法,缓解此类勒索软件和手工活动的最佳方法是阻止端点之间所有不必要的通信。遵循凭证卫生的最佳实践也同样重要,例如多因素身份验证(Multi-Factor Authentication)、监控暴力尝试、安装最新的安全更新等。以下是要采取的防御措施的完整列表:
- 确保应用 Microsoft推荐的配置设置(recommended configuration settings)来保护连接到 Internet 的计算机。
- Defender ATP提供威胁和漏洞管理(threat and vulnerability management)。您可以使用它定期审核机器的漏洞、错误配置和可疑活动。
- 使用MFA 网关(MFA gateway),例如Azure 多重身份验证(Azure Multi-Factor Authentication)( MFA ) 或启用网络级身份验证 ( NLA )。
- 为帐户提供最低权限(least-privilege to accounts),并且仅在需要时启用访问权限。任何具有域范围管理员级别访问权限的帐户都应为最小值或为零。
- 本地管理员密码解决方案( LAPS ) 工具等工具可以为管理员帐户配置唯一的随机密码。您可以将它们存储在Active Directory (AD) 中并使用ACL进行保护。
- 监控蛮力尝试。您应该感到震惊,特别是如果有很多失败的身份验证尝试。(failed authentication attempts. )使用事件ID 4625进行(ID 4625)过滤(Filter)以查找此类条目。
- 攻击者通常会清除安全事件日志和 PowerShell 操作日志(Security Event logs and PowerShell Operational log)以删除他们的所有足迹。发生这种情况时, Microsoft Defender ATP(Microsoft Defender ATP)会生成事件 ID 1102(Event ID 1102)。
- 打开篡改保护(Tamper protection)(Tamper protection)功能,以防止攻击者关闭安全功能。
- 调查(Investigate)事件ID 4624以查找具有高权限的帐户正在登录的位置。如果他们进入受感染的网络或计算机,则可能是更严重的威胁。
- (Turn on cloud-delivered protection)在Windows Defender Antivirus上(Windows Defender Antivirus)打开云提供的保护和自动样本提交。它可以保护您免受未知威胁。
- 打开攻击面减少规则。除此之外,启用阻止凭据盗窃、勒索软件活动和可疑使用PsExec和WMI的规则。
- 如果您有 Office 365,请为Office VBA打开 AMSI 。
- (Prevent RPC)尽可能防止端点之间的 RPC和SMB通信。(SMB)
阅读(Read):Windows 10 中的勒索软件保护(Ransomware protection in Windows 10)。
微软(Microsoft)对Wadhrama、Doppelpaymer、Ryuk、Samas、REvil进行了案例研究(REvil)
- Wadhrama使用蛮力交付到具有远程桌面(Remote Desktop)的服务器中。他们通常会发现未打补丁的系统并使用公开的漏洞来获得初始访问权限或提升权限。
- Doppelpaymer使用被盗的特权帐户凭据通过受感染的网络手动传播。这就是为什么必须遵循所有计算机的推荐配置设置的原因。
- Ryuk通过欺骗最终用户其他事情来通过电子邮件 ( Trickboat ) 分发有效负载。(Trickboat)最近,黑客利用冠状病毒恐慌来欺骗最终用户。其中之一还能够提供Emotet 有效载荷。
它们每个的共同点(common thing about each of them)是它们是根据情况构建的。他们似乎在执行大猩猩战术,从一台机器移动到另一台机器以传递有效载荷。至关重要的是,IT 管理员不仅要密切关注正在进行的攻击(即使是小规模攻击),还要让员工了解如何帮助保护网络。
我希望所有 IT 管理员都可以遵循该建议,并确保减轻人为勒索软件(Ransomware)的攻击。
相关阅读(Related read):在您的 Windows 计算机上遭到勒索软件攻击后该怎么办?(What to do after a Ransomware attack on your Windows computer?)
How to mitigate Human-operated Ransomware Attacks: Infographic
In earlier days, if someоne has to hijack your computer, it was usually possіble by getting hоld of your computer either by physically being there or using remote access. While the world hаs moved ahead with aυtomatiоn, computer security has tightened, one thing thаt hasn’t changed is human mistakes. That iѕ where the Human-operated Ransomware Attacks come into the picture. These are handcrafted attacks which find a vulnerability or a misconfigured security on the computer and gain access. Microsoft has come up with an exhaustive case study which concludes that IT admin can mitigate these human-operated Ransomware attacks by a significant margin.

Mitigating Human-operated Ransomware Attacks
According to Microsoft, the best way to mitigate these kinds of ransomware, and handcrafted campaigns is to block all unnecessary communication between endpoints. It is also equally important to follow best practices for credential hygiene such as Multi-Factor Authentication, monitoring brute force attempts, installing the latest security updates, and more. Here is the complete list of defense measures to be taken:
- Make sure to apply Microsoft recommended configuration settings to protect computers connected to the internet.
- Defender ATP offers threat and vulnerability management. You can use it to audit machines regularly for vulnerabilities, misconfigurations, and suspicious activity.
- Use MFA gateway such as Azure Multi-Factor Authentication (MFA) or enable network-level authentication (NLA).
- Offer least-privilege to accounts, and only enable access when required. Any account with domain-wide admin-level access should be at the minimum or zero.
- Tools like Local Administrator Password Solution (LAPS) tool can configure unique random passwords for admin accounts. You can store them in Active Directory (AD) and protect using ACL.
- Monitor for brute-force attempts. You should be alarmed, especially if there is a lot of failed authentication attempts. Filter using event ID 4625 to find such entries.
- Attackers usually clear the Security Event logs and PowerShell Operational log to remove all their footprints. Microsoft Defender ATP generates an Event ID 1102 when this occurs.
- Turn on Tamper protection features to prevent attackers from turning off security features.
- Investigate event ID 4624 to find where accounts with high privileges are logging on. If they get into a network or a computer that is compromised, then it can be a more significant threat.
- Turn on cloud-delivered protection and automatic sample submission on Windows Defender Antivirus. It secures you from unknown threats.
- Turn on attack surface reduction rules. Along with this, enable rules that block credential theft, ransomware activity, and suspicious use of PsExec and WMI.
- Turn on AMSI for Office VBA if you have Office 365.
- Prevent RPC and SMB communication among endpoints whenever possible.
Read: Ransomware protection in Windows 10.
Microsoft has put up a case study of Wadhrama, Doppelpaymer, Ryuk, Samas, REvil
- Wadhrama is delivered using brute forces their way into servers that have Remote Desktop. They usually discover unpatched systems and use disclosed vulnerabilities to gain initial access or elevate privileges.
- Doppelpaymer is manually spread through compromised networks using stolen credentials for privileged accounts. That’s why it is essential to follow the recommended configuration settings for all computers.
- Ryuk distributes payload over email (Trickboat) by tricking the end-user about something else. Recently hackers used the Coronavirus scare to trick the end-user. One of them was also able to deliver the Emotet payload.
The common thing about each of them is they are built based on situations. They seem to be performing gorilla-tactics where they move from one machine to another machine to deliver the payload. It is essential that IT admins not only keep a tab on the ongoing attack, even if it’s on a small scale, and educate employees about how they can help to protect the network.
I hope all IT admins can follow the suggestion and make sure to mitigate human-operated Ransomware attacks.
Related read: What to do after a Ransomware attack on your Windows computer?

