如果您是系统管理员,那么密切关注员工的电子邮件和 PC 使用情况是一项相当常见的任务,可让您监控生产力,并确保没有危险文件进入您的网络。这同样适用于父母(applies to parents)和老师,他们可能希望密切关注孩子的 PC 使用情况以确保他们的安全。
不幸的是,有时监控软件不受欢迎或不受欢迎。黑客、窥探者或过度扩张的 IT 管理员都可能将界限推得太远。如果您担心自己的隐私(worried about your privacy),可以按照以下步骤学习检测计算机和电子邮件监控或间谍软件。

在家、学校或工作场所进行监控(Monitoring at Home, School, or Work)
在您开始研究如何检测某些类型的计算机和电子邮件监控之前,您可能需要确定您的权利。作为一名员工,您对网络、电子邮件或一般 PC 使用的未经过滤访问的权利可能要低得多,但这并不意味着没有不能跨越的界限(boundaries that can’t be crossed)。
您可能不拥有这些设备,并且根据您的合同,您的雇主或学校可能有权记录有关您的 PC 使用情况的任何数据。虽然有一些方法可以监控这一点,但您可能无法停止或解决它。这同样适用于教育环境,可能对 PC 和网络使用进行严格控制。

然而,对于家庭网络上的个人 PC 来说,情况完全不同。你的电脑,你的规则——除非它不是你的设备。例如,父母可能会放置监控软件来保护孩子的安全,但虐待伙伴或数千英里外的恶意黑客也可能如此。
无论是在家里、学校还是在办公室,您都可以通过多种方式检查可能发生的典型计算机或电子邮件监控。
检查电子邮件监控软件(Checking for Email Monitoring Software)
如果您想检查电子邮件监控,请首先考虑您使用的是个人、公司还是教育电子邮件帐户。对于企业或教育帐户,系统管理员可能有权随时访问您的电子邮件,所有电子邮件都通过他们也可以控制的安全服务器路由。

如果是这种情况,您应该始终(always)假设您的电子邮件以某种方式受到监控。它可能会受到主动监控,检查和记录每封电子邮件,或者监控可能不太具体,分别记录您何时发送和接收电子邮件(以及收件人或发件人)的信息。
即使监控较少,企业或教育电子邮件帐户的管理员仍然可以随时重置您的密码以访问您的电子邮件。
检查电子邮件标题(Checking Email Headers)
您通常可以通过查看您收到的电子邮件的标题来(headers for emails)确定您的电子邮件是否通过公司电子邮件服务器进行路由。例如,在Gmail中,您可以通过打开电子邮件并选择右上角的三点菜单图标(three-dots menu icon )来查找标题。从选项中,选择显示原始(Show Original )选项。

查看标头,已接收(Received)标头将显示电子邮件的来源和正在使用的电子邮件服务器。如果电子邮件通过公司服务器路由或被过滤器扫描,您可以假设电子邮件正在(或可以)被记录和监控。

使用代理服务器(Using Proxy Servers)
如果您使用的是Microsoft Outlook等桌面电子邮件客户端,则您的电子邮件可能正在通过代理服务器进行监控。代理服务器可用于记录某些数据,以及将其转发到其他服务器。
您可以在Windows 设置菜单中检查您在(Windows Settings)Windows 10上的代理设置(如果您有权访问)。
- 要开始,请右键单击“开始(Start)”菜单并选择“设置”(Settings)选项。

- 在 Windows 设置中,选择网络和 Internet(Network & Internet) >代理( Proxy)。如果您使用的是代理服务器,这将在使用代理服务器(Use a proxy server)部分中列出。

您的Outlook邮箱设置也可能设计为通过特定代理通过电子邮件服务器进行路由。这是在将您的帐户邮箱添加到Outlook时设置的,对于公司设备,可能会自动为您配置。
不幸的是,测试这一点的唯一方法(您自己没有管理员访问权限)是在个人帐户和您怀疑被监控的帐户之间发送和接收电子邮件。监视电子邮件标头,您可以通过Received或X-Forwarded-For标头发现是否使用了代理服务器。
检查监控软件(Checking for Monitoring Software)
一种更典型的数字监控方法是通过安装在您的 PC 上的软件,跟踪您的网络活动、您使用的软件,甚至您的麦克风、网络摄像头和键盘的使用情况。您在 PC 上所做的几乎所有事情都可以使用正确的软件进行记录。
然而,寻找你被监视的迹象可能会有点困难。Windows任务栏中并不总是有一个方便的图标可供查找,因此您需要更深入地挖掘。
检查 Windows 任务管理器(Checking Windows Task Manager)
如果您怀疑 Windows PC 上有软件正在记录您的活动,您可能需要先使用任务管理器(Task Manager)检查正在运行的进程列表。您可以在其中找到 PC 上所有正在运行的软件的列表。
- 要打开任务管理器,请右键单击开始(Start)菜单并选择任务管理器(Task Manager)选项。

- 在任务管理器(Task Manager)窗口中,您将看到正在运行的应用程序和服务的列表。或者,切换到详细信息选项卡以获得所有正在运行的(Details)可执行文件(executable files)的更清晰列表。

运行具有非描述名称的进程应该引起您的怀疑(尽管并非总是如此)。虽然这可能很耗时,但您应该使用搜索引擎依次调查每个正在运行的进程。
例如,ntoskrnl.exe是一个完全合法(且必不可少)的 Windows 进程。但是,如果您在列表中发现了student.exe(LanSchool学校监控服务的监控应用程序),您可以假设您正在被监控。

您还应该寻找常见的远程桌面连接软件,例如VNC、LogMeIn或TeamViewer。这些屏幕共享应用程序(screen sharing apps)允许远程用户控制您的 PC,使他们能够打开应用程序、执行任务、记录您的屏幕使用情况等。
Windows 也有自己的远程桌面服务(own remote desktop service),允许其他Windows PC 来查看和控制您的 PC。好消息是RDP连接通常只允许一个人同时查看一个屏幕。只要您登录,其他用户就不能查看或控制您的 PC。
查看活动网络连接(Looking at Active Network Connections)
进程管理器是检查活动监控软件的好方法,但这仅在软件当前处于活动状态时才有效。在某些设置(例如学校环境)中,您可能无权打开任务管理器(Task Manager)首先查看。
大多数日志软件通常通过在本地记录数据并将其发送到其他地方的服务器或管理员来工作。这可以是本地的(在您自己的网络上)或基于 Internet 的服务器。为此,您需要查看 PC 上的活动网络连接。
一种方法是使用内置的Resource Monitor。这个鲜为人知的Windows应用程序允许您从您的 PC 查看任何活动的通信,包括传入和传出。它也是一个经常在企业和教育 PC 上可用的应用程序。
- 要打开资源监视器(Resource Monitor),请右键单击开始(Start)菜单并选择运行(Run)。

- 在“运行”(Run)框中,键入resmon并选择“确定(OK)” 。

- 在资源监视器(Resource Monitor )窗口中选择网络(Network)选项卡。从这里,您将看到活动连接列表。在具有网络活动的进程(Processes with Network Activity )框中,您将看到正在本地或基于 Internet 的服务发送和接收数据的进程。在“网络活动(Network Activity )”框中,您将再次看到这些进程列出,但列出了活动连接(带有 IP 地址)。如果您想知道用于建立连接的端口,或在您的 PC 上打开(open ports on your PC)进程正在主动侦听连接的端口,请查看TCP 连接(TCP Connections )和侦听端口(Listening Ports)框。

与保留 IP 范围内的其他设备的任何连接(例如 10.0.0.1 到 10.255.255.255 或 192.168.0.1 到 192.168.255.255)意味着数据正在通过您的网络共享,但与其他范围的连接指向基于 Internet 的管理服务器.
您可能需要研究此处列出的一些流程以确定可能的应用程序。例如,如果您发现一个您无法识别的进程,其中包含多个活动连接、发送和接收大量数据或使用不常见的端口(通常是 5 位数字),请使用搜索引擎对其进行研究更远。
发现键盘、网络摄像头和麦克风记录(Spotting Keyboard, Webcam, and Microphone Logging)
PC 监控软件不仅仅是记录您的网络使用情况——它可以证明是更加个人化的。在可能的情况下,此类应用程序可以(并且可能)监控您的网络摄像头并监控使用情况,或记录您所做的所有活动按键。您在 PC 上键入、说或执行的所有操作都可以被记录下来并在以后进行检查。
如果发生这种情况,您需要尝试发现这些迹象。大多数内置和外部网络摄像头(external webcams)都会显示一个指示灯(通常为绿色或白色LED),以表明网络摄像头处于活动状态。麦克风(Microphone)的使用很难发现,但您可以在声音(Sound)设置菜单中检查麦克风检测到的声音。
- 为此,请右键单击任务栏快速访问区域中的声音图标。从选项中,选择打开声音设置(Open Sound settings)。

- 在“声音(Sound)”菜单中,“测试麦克风(Test your microphone )”滑块将随着麦克风拾取的声音上下移动。

如果您有权这样做,您可以在 Windows 设置菜单中阻止对麦克风或摄像头的访问。(block access to your mic or camera)
- 要访问此菜单,请右键单击“开始(Start)”菜单并选择“设置”。(Settings.)

- 在“设置”(Settings )菜单中,选择“隐私(Privacy )”选项。在麦克风(Microphone )部分,禁用允许应用程序访问您的麦克风(Allow apps to access your microphone )和允许桌面应用程序访问您的麦克风(Allow desktop apps to access your microphone )滑块以停止所有麦克风访问。或者,您可以通过选择每个应用条目旁边的滑块来阻止单个应用。
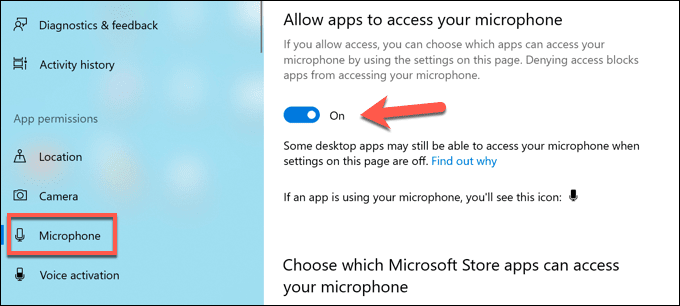
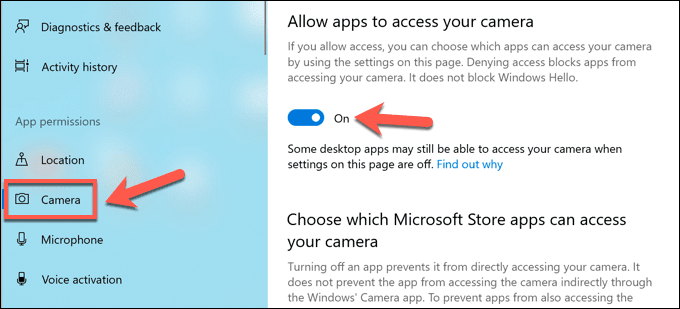
- 在相机部分,您可以通过选择(Camera )允许应用访问您的相机(Allow apps to access your camera )和允许桌面应用访问您的相机(Allow desktop apps to access your camera)滑块来禁用相机访问。您还可以通过选择每个条目旁边的滑块来停止单个应用程序。
上述步骤应该可以帮助您限制某人可以看到或听到的内容,但您可能需要采取其他步骤来阻止键盘记录尝试(block keylogging attempts)。
防止政府监控(Protecting Against Government Monitoring)
我们上面概述的方法可以很好地发现您可以在家中或工作场所进行的监控,但它们不太可能用于发现政府监控。在世界的某些地区,您的数字活动可能会被记录和审查。

防止这种在线计算机监控可能很困难,但这并非不可能。一些最好的虚拟专用网络(best virtual private networks)可以在互联网审查普遍的地区工作,但您也可以使用 Tor(use Tor)绕过限制并保护您的隐私。
不幸的是,真正阻止政府代理人监控您的数字使用的唯一方法是切换到加密平台进行通信。存在许多支持端到端加密的加密聊天平台(encrypted chat platforms),例如Signal ,让您可以自由聊天而不必担心审查。(Signal)
保护自己免受窥探者(Protect Yourself Against Snoopers)
如上述步骤所示,公司管理员、霸道的父母、心怀不满的前任、恶意黑客甚至政府间谍可以通过多种方式监控您的 PC 使用情况。这并不总是您可以控制的,特别是如果您是使用公司网络的员工。
但是,如果您使用的是个人 PC,则可以采取一些步骤来保护您的 PC。使用虚拟专用网络(virtual private network)是隐藏您的互联网使用情况的好方法,但它也可以阻止传出尝试连接到您的 PC。您还可以考虑使用第三方防火墙(third-party firewall)来增强您的 PC 以阻止不必要的访问。
如果您真的担心您的网络安全(network security),您可以查看其他方法来隔离您的 PC 使用。您可以切换到Linux 发行版(Linux distribution),提供比典型Windows PC 更高的安全性。如果你想变成白帽,你甚至可以考虑一个用于黑客攻击的 Linux 发行版(Linux distro for hacking),允许你测试你的网络是否存在安全漏洞。
How to Detect Computer & Email Monitoring or Spying Software
If yoυ’re a system administrator, then keeping an eye on yoυr employees’ email and PC usage is a fairly common task, allowing you to monitоr productіvity, as well as ensure no dangеrous files enter your network. Thе same applies to parents and teachers, too, who might wish to keep an eye on a child’s PC usage for their safety.
Unfortunately, there are times where monitoring software isn’t welcomed or appreciated. Hackers, snoopers, or overreaching IT admins can all push the boundaries too far. If you’re worried about your privacy, you can learn to detect computer and email monitoring or spying software by following these steps.

Monitoring at Home, School, or Work
Before you begin to look at how to detect certain types of computer and email monitoring, you may need to determine your rights. As an employee, your rights to unfiltered access to the web, email, or general PC usage could be much lower, although that doesn’t mean that there aren’t boundaries that can’t be crossed.
You may not own the equipment, and depending on your contract, your employer or school may hold the right to log any data on your PC usage. While there are ways to monitor this, you might not be able to stop or work around it. The same applies in an educational setting, where strict controls on PC and web usage are likely.

It’s a different scenario entirely for a personal PC on a home network, however. Your PC, your rules – unless it isn’t your equipment. Parents, for instance, may place monitoring software to keep their children safe, but so too may abusive partners, or malicious hackers thousands of miles away.
Whether it’s at home, school, or at the office, there are a number of ways you can check for the typical kind of computer or email monitoring that can take place.
Checking for Email Monitoring Software
If you want to check for email monitoring, consider first whether you’re using a personal, corporate, or educational email account. For corporate or educational accounts, a system administrator likely has the power to access your emails at any point, with all emails routed through a secure server that they may also control.

If that’s the case, you should always assume that your emails are monitored in some way. It might be actively monitored, where each email is checked and logged, or the monitoring could be less specific, with information on when you send and receive emails (as well as the recipients or senders) logged separately.
Even with less active monitoring, an administrator over a corporate or educational email account can still reset your password to access your emails at any point.
Checking Email Headers
You can usually determine if your emails are being routed through a corporate email server by looking at the headers for emails you receive. For instance, in Gmail, you can look up the headers by opening an email and selecting the three-dots menu icon in the top-right. From the options, select the Show Original option.

Looking at the headers, the Received header will show where the email originated from and the email server being used. If the email is routed through a corporate server or is scanned by a filter, you can assume that the email is being (or can be) logged and monitored.

Using Proxy Servers
If you’re using a desktop email client like Microsoft Outlook, it’s possible that your emails are being monitored through a proxy server. A proxy server can be used to log certain data, as well as forward it to other servers.
You can check your proxy settings on Windows 10 in the Windows Settings menu (if you have access to this).
- To start, right-click the Start menu and select the Settings option.

- In Windows Settings, select Network & Internet > Proxy. If you’re using a proxy server, this will be listed in the Use a proxy server section.

It’s also possible that your Outlook mailbox settings are designed to route through an email server over a specific proxy. This is set up when your account mailbox is added to Outlook which, for corporate devices, is likely configured for you automatically.
Unfortunately, the only way to test this (without administrator access yourself) is to send and receive emails between a personal account and an account you suspect is monitored. Monitoring the email headers, you may be able to spot if a proxy server is used using the Received or X-Forwarded-For headers.
Checking for Monitoring Software
A more typical method of digital monitoring is through software installed on your PC, tracking your web activity, the software you use, and even your microphone, webcam, and keyboard usage. Almost everything you do on your PC is loggable with the right software.
Looking for the signs that you’re being monitored, however, can be a little harder. There isn’t always a handy icon in the Windows taskbar to look for, so you’ll need to dig a little deeper.
Checking Windows Task Manager
If you suspect there’s software on your Windows PC that’s recording your activity, you might want to check your list of running processes first using Task Manager. There is where you’ll find a list of all the running software on your PC.
- To open the task manager, right-click the Start menu and select the Task Manager option.

- In the Task Manager window, you’ll see a list of running apps and services. Alternatively, switch to the Details tab for a clearer list of all running executable files.

Running processes with non-descript names should raise your suspicions (although not always). While it may prove time consuming, you should use a search engine to investigate each running process in turn.
For instance, ntoskrnl.exe is a perfectly legitimate (and essential) Windows process. If you spotted student.exe (the monitoring app for the LanSchool monitoring service for schools) in the list, however, you can assume you’re being monitored.

You should also look for common remote desktop connection software, such as VNC, LogMeIn, or TeamViewer. These screen sharing apps allow a remote user to take control of your PC, giving them the ability to open apps, perform tasks, record your screen usage, and more.
Windows also has its own remote desktop service, allowing other Windows PCs to view and control your PC. The good news is that RDP connections typically only allow one person to view a screen at the same time. As long as you’re logged in, another user shouldn’t be able to view or control your PC.
Looking at Active Network Connections
The process manager is a good way to check for active monitoring software, but this only works if the software is currently active. In certain settings (such as a school environment), you may not have permission to open the Task Manager to look in the first place.
Most logging software usually works by recording data locally and sending it to a server or administrator elsewhere. This could be locally (on your own network) or to an internet-based server. To do this, you’ll need to look at the active network connections on your PC.
One way to do this is to use the built-in Resource Monitor. This little-known Windows app allows you to view any active communications, both ingoing and outgoing, from your PC. It’s also an app that often remains available on corporate and educational PCs.
- To open Resource Monitor, right-click the Start menu and select Run.

- In the Run box, type resmon and select OK.

- Select the Network tab in the Resource Monitor window. From here, you’ll see a list of active connections. In the Processes with Network Activity box, you’ll see processes that are sending and receiving data, either locally or to internet-based services.
In the Network Activity box, you’ll see these processes listed again, but with the active connections (with IP addresses) listed. If you want to know the ports being used to make the connections, or open ports on your PC that processes are actively listening on for connections, view the TCP Connections and Listening Ports boxes.

Any connections to other devices in reserved IP ranges (eg. 10.0.0.1 to 10.255.255.255 or 192.168.0.1 to 192.168.255.255) means data is being shared over your network, but connections to other ranges points to an internet-based administration server.
You may need to research some of the processes listed here to identify possible apps. For instance, if you spot a process that you don’t recognize with a number of active connections, sending and receiving a lot of data, or using an uncommon port (typically a 5-digit number), use a search engine to research it further.
Spotting Keyboard, Webcam, and Microphone Logging
PC monitoring software isn’t just about recording your web usage—it can prove to be a lot more personal. Where possible, apps like these can (and may) monitor your webcam and monitor usage, or record all active keypresses you make. Everything you type, say, or do on your PC could be recorded and examined later.
If this is happening, you’ll need to try and spot the signs. Most built-in and external webcams display a light (usually a green or white LED) to show that a webcam is active. Microphone usage is trickier to spot, but you can check what sounds a microphone is detecting in the Sound settings menu.
- To do this, right-click the sound icon in the quick access area of the task bar. From the options, select Open Sound settings.

- In the Sound menu, the Test your microphone slider will move up and down with sounds picked up by your mic.

If you have permissions to do so, you can block access to your mic or camera in the Windows Settings menu.
- To access this menu, right-click the Start menu and select Settings.

- In the Settings menu, select the Privacy option. In the Microphone section, disable the Allow apps to access your microphone and Allow desktop apps to access your microphone sliders to stop all mic access. Alternatively, you can block individual apps by selecting the slider next to each app entry.

- In the Camera section, you can disable camera access by selecting the Allow apps to access your camera and Allow desktop apps to access your camera sliders. You can also stop individual apps by selecting the slider next to each entry.

The steps above should help you to limit what somebody can see or hear, but you may need to take additional steps to block keylogging attempts.
Protecting Against Government Monitoring
The methods we’ve outlined above work well to spot the kind of monitoring you can expect at home or at work, but they’re less likely to work to spot government monitoring. In certain areas of the world, your digital activity is likely to be recorded and censored.

Protecting against this kind of computer monitoring online can be difficult, but it isn’t impossible. Some of the best virtual private networks can work in areas of the world where internet censorship is common, but you can also use Tor to bypass restrictions and protect your privacy instead.
Unfortunately, the only way to truly prevent government agents from monitoring your digital usage is to switch to encrypted platforms for communication. A number of encrypted chat platforms exist, such as Signal, that support end-to-end encryption, allowing you to chat freely without fear of censorship.
Protect Yourself Against Snoopers
As the steps above show, there are a number of ways that corporate administrators, overbearing parents, disgruntled exes, malicious hackers, and even government spies can monitor your PC usage. This isn’t always something you can control, especially if you’re an employee using a corporate network.
If you’re using a personal PC, however, there are steps you can take to protect your PC. Using a virtual private network is a great way to hide your internet usage, but it can also block outgoing attempts to connect to your PC. You could also think about beefing up your PC with a third-party firewall to stop unnecessary access.
If you’re really worried about your network security, you can look at other ways to isolate your PC usage. You could switch to a Linux distribution, offering more security than a typical Windows PC. If you want to turn white-hat, you can even think about a Linux distro for hacking, allowing you to test your network for security holes.



















