网络攻击(Cyber Attack)是从一台计算机对另一台计算机或网站发起的攻击,旨在损害目标及其中存储的信息的完整性、机密性或可用性。本文解释了什么是网络攻击(Cyber Attacks)、其定义、类型,并讨论了如何防止它们以及在发生网络攻击时应采取的措施。网络攻击(Cyber Attacks)在某种程度上可以被广泛认为是网络犯罪(Cyber Crime)的一部分。实施 网络犯罪(Cyber Crime)的攻击可以称为网络攻击!
网络攻击定义
根据 hklaw.com 的Practical Law (hklaw.com)Company(Practical Law Company)网络攻击(Cyber Attacks)白皮书(Whitepaper),网络攻击(Cyber Attacks)的定义如下:
A Cyber Attack is an attack initiated from a computer against a website, computer system or individual computer (collectively, a computer) that compromises the confidentiality, integrity or availability of the computer or information stored on it.
该定义具有三个不同的因素: [1 ] 攻击(] Attack)或非法企图 [2] 从 [3] 计算机系统获得某些东西。一般而言,系统是为实现共同目标而共同工作的单元的集合。因此,无论是单台计算机还是一组计算机——离线或在线(网站/内联网),它都是一个系统,因为它们可以促进某事或其他事。即使是一台计算机也有许多组件为了一个共同的目标而协同工作,因此被称为计算机系统。
主要因素是非法访问(illegal access)此类系统。第二个因素是目标系统(target system)。最后一个因素是攻击者(attacker)的收益。需要注意的是,非法访问必须有破坏目标系统的动机,以某种方式使攻击者获得某些东西,例如存储在系统中的信息,或者对系统的完全控制权。
阅读:(Read:) 为什么网站被黑客入侵?
网络攻击的类型
网络攻击(Cyber Attacks)的方法有很多种,从恶意软件注入到网络钓鱼到社会工程再到内部数据窃取。其他高级但常见的形式是DDoS 攻击(DDoS Attacks)、蛮力攻击、黑客攻击、使用直接黑客攻击或勒索(Brute Force attacks)软件(Ransomware)持有计算机系统(或网站)以勒索。
其中一些已在下面列出:
- 获得或试图获得对计算机系统或其数据的未经授权的访问。
- 中断或拒绝服务攻击 ( DDoS )
- 入侵网站或恶意攻击该网站
- 病毒或恶意软件安装
- 未经授权使用计算机处理数据
- (Inappropriate)公司员工以损害公司的方式不当使用计算机或应用程序。
最后一个——员工不当使用计算机或应用程序——可能是故意的,也可能是由于缺乏知识。例如,必须找出员工试图输入错误数据或访问他或她无权更改的特定数据记录的真正原因。
社会工程(Social engineering)也可能是员工故意尝试侵入数据库的原因——只是为了帮助朋友!也就是说,该员工与一名罪犯结识,并在情感上被迫为新朋友获取一些无辜的数据。
当我们在这里时,还建议向员工宣传公共 WiFi 的危险(dangers of public WiFi)以及为什么他们不应该使用公共 WiFi 进行办公室工作。(While we are here, it is also advisable to teach the employees about the dangers of public WiFi and why they should not use public WiFi for office work.)
阅读(Read):什么是蜜罐以及它们如何保护计算机系统。
网络攻击响应
预防总是胜于治疗。你一定听过很多次了。在保护网络攻击(Cyber Attacks)方面,这同样适用于 IT 领域。但是,假设您的计算机或网站受到攻击,即使在采取了所有预防措施之后,仍会制定一些常见的一般响应步骤:
- 袭击真的(Did)发生了还是有人打电话来恶作剧?
- 如果您仍然可以访问您的数据,请将其备份;
- 如果您无法访问您的数据,并且黑客要求赎金,您可能需要考虑与法律机构联系
- 与黑客谈判并重新获得数据
- 在社会工程和员工滥用特权的情况下,应进行检查以确定员工是否无辜或故意行为
- 在DDoS攻击的情况下,应将负载减轻到其他服务器,以便网站尽快恢复在线。您可以租用一段时间的服务器或使用云应用程序,以便将成本降至最低。
有关以法律方式回应的准确和详细信息,请阅读参考(References)部分下提到的白皮书。
阅读(Read):为什么有人想破解我的电脑?(Why would someone want to hack my computer?)
预防网络攻击
您可能已经知道没有 100% 万无一失的方法来应对网络犯罪和网络攻击,但您仍然必须采取尽可能多的预防措施来保护您的计算机。
首先要做的是使用好的安全软件,它不仅可以扫描病毒,还可以寻找不同类型的恶意软件,包括但不限于勒索软件,并阻止它进入计算机。大多数情况下,这些恶意代码是通过访问或从不知名网站下载内容、路过(Mostly)式下载(Drive-by downloads)、显示恶意广告的受感染网站(也称为恶意广告)而(Malvertising)注入您的计算机的。
除了防病毒软件,您还应该使用良好的防火墙。Windows 10/8/7中的内置防火墙很好,但您可以使用您认为比默认Windows 防火墙(Windows Firewall)更强大的第三方防火墙。
阅读(Read):恶意软件跟踪器地图,可让您实时查看网络攻击。(Cyber Attacks)
如果是公司计算机网络,请确保任何用户计算机都没有即插即用支持(Play)。也就是说,员工不应该能够将闪存(Flash)驱动器或他们自己的互联网(Internet)加密狗插入USB。公司的 IT 部门还应密切关注所有网络流量。使用良好的网络流量分析器有助于及时处理任何终端(员工计算机)引起的奇怪行为。
阅读(Read):小型企业的最佳网络安全实践(Best Cybersecurity Practices for Small Business)。
为了防止DDoS攻击,网站最好缓解到不同的服务器上,而不是简单地托管在单个服务器上。最好的方法是使用云服务不断启动镜像。这将大大降低DDoS成功的机会——至少不会持续很长时间。使用像Sucuri这样好的防火墙并采取一些基本步骤来保护和保护您的网站。
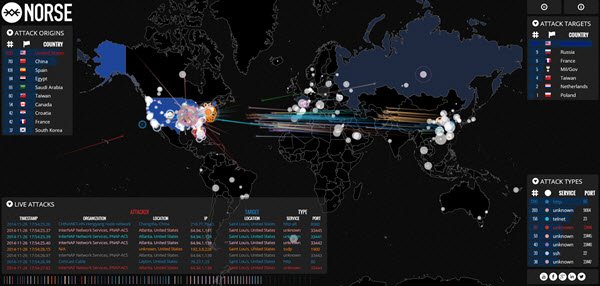
以下是一些显示实时数字黑客攻击地图的有用链接:(Here are a few useful links that display real-time digital hack attack maps:)
- ipviking.com
- digitalattackmap.com
- 火眼网
- norsecorp.com
- 蜜网.org。
看看他们。他们很有趣!
如果您有什么要补充的,请分享。(If you have anything to add, please do share.)
阅读下一篇(Read next):密码喷射攻击(Password Spray Attacks)| 蛮力攻击(Brute Force Attacks)| 生活在土地攻击(Living Off The Land attacks)| 冲浪攻击(Surfing Attacks)| 凭据填充攻击| 领域前沿(Domain Fronting)| 冷启动攻击(Cold Boot Attacks)。
Cyber Attacks - Definition, Types, Prevention
A Cуber Attaсk is an attack іnitiated from a computer against another computer or a websitе, with a view to compromising the integrity, confidentiality or availability of target and the informаtion stored in it. This article explains what are Cyber Attacks, its definition, types and talks about how to prevent them and the course to take in the event of a cyber attack. Cyber Attacks, in a way, can be broadly considered to be a part of Cyber Crime. An attack to commit a Cyber Crime can be called as a Cyber Attack!

Cyber Attacks Definition
According to the Practical Law Company, Whitepaper on Cyber Attacks, conducted by hklaw.com, the definition of Cyber Attacks is as follows:
A Cyber Attack is an attack initiated from a computer against a website, computer system or individual computer (collectively, a computer) that compromises the confidentiality, integrity or availability of the computer or information stored on it.
The definition has three distinct factors: [1] Attack or an illegal attempt to [2] gain something from a [3] computer system. Generally speaking, a system is a collection of units that work collectively towards a common goal. Thus, whether it is a single or a collection of computers – offline or online (websites/intranets), it is a system as they work to facilitate something or the other. Even a single computer has many components that work together for a common goal and hence is called a computer system.
The main factor is illegal access to such a system. The second factor is the target system. The final factor is gains to the attacker. It should be noted that illegal access must have a motive to compromise the target system, in a way that the attacker gains something, such as information stored in the system, or the total control of the system.
Read: Why are websites hacked?
Types of Cyber Attacks
There are many methods of Cyber Attacks from malware injection to phishing to social engineering to the internal stealing of data. Other advanced but common forms are DDoS Attacks, Brute Force attacks, hacking, holding a computer system (or a website) for ransom using direct hack or Ransomware.
Some of them have been listed below:
- Gaining, or attempting to gain, unauthorized access to a computer system or its data.
- Disruption or denial of service attacks (DDoS)
- Hacking a website or mal-facing the site
- Virus or malware installation
- Unauthorized use of a computer for processing of data
- Inappropriate use of computers or applications by employees of a company, in a way that it harms the company.
The last one – the inappropriate use of computers or apps by employees – could be deliberate or due to lack of knowledge. One has to figure out the real reason why an employee, for example, tried to enter the wrong data or accesses a particular data record which he or she was not authorized to change.
Social engineering could also be a cause whereby an employee deliberately tries to hack into the database – just to help a friend! That is, the employee was befriended by a criminal and is emotionally forced to obtain some innocent data for the new friend.
While we are here, it is also advisable to teach the employees about the dangers of public WiFi and why they should not use public WiFi for office work.
Read: What are Honeypots and how can they secure computer systems.
Cyber Attacks Response
Prevention is always better than the cure. You must have heard this a number of times. The same applies to the field of IT when it comes to protection against Cyber Attacks. However, assuming that your computer(s) or website(s) were attacked, even after taking all the precautions, there are certain common general response steps laid down:
- Did the attack really happened or is someone calling in to play a prank;
- If you still have access to your data, back it up;
- If you cannot access your data, and the hacker is demanding ransom, you may want to consider approaching the legal authorities
- Negotiate with the hacker and regain the data
- In the case of social engineering and employees misusing their privileges, checks should be conducted to determine if the employee was innocent or acted deliberately
- In the case of DDoS attacks, the load should be mitigated to other servers, so that the website comes back online as soon as possible. You may rent out servers for a while or use a cloud app so that costs are minimal.
For exact and detailed information on responding the legal way, please read the whitepaper mentioned under the References section.
Read: Why would someone want to hack my computer?
Prevention of Cyber Attacks
You might already know that there is no 100% foolproof method to counter cyber crime and cyber attacks, but still, you have to take as many precautions to protect your computers.
The primary things to be done are to use good security software, that not only scans for virus, but also looks for different types of malware, including but not limited to ransomware, and stops it from entering the computer. Mostly these malicious codes are injected into your computers by visiting or downloading things from non-reputed websites, Drive-by downloads, compromised websites that display malicious advertisings also known as Malvertising.
Along with the antivirus, you should use a good firewall. While the built-in firewall in Windows 10/8/7 is good, you can use third-party firewalls that you feel are stronger than the default Windows Firewall.
Read: Malware Tracker Maps that let you view Cyber Attacks in real-time.
If it is a corporate computer network, make sure there is no Plug and Play support in any of the user computers. That is, employees should not be able to plug in Flash drives or their own Internet dongles into the USB. The IT department of the company should also keep a watch on all the network traffic. Using a good network traffic analyzer helps in prompt attendance to strange behaviors arising out of any terminal (employee computer).
Read: Best Cybersecurity Practices for Small Business.
For protection against DDoS attacks, the website is better mitigated to different servers, instead of being hosted simply on a single server. The best method would be to have a mirror constantly up using a cloud service. That will greatly reduce the chances of a DDoS being successful – not for a long time at least. Use a good firewall like Sucuri and take some basic steps to protect and secure your website.
Here are a few useful links that display real-time digital hack attack maps:
- ipviking.com
- digitalattackmap.com
- fireeye.com
- norsecorp.com
- honeynet.org.
Have a look at them. They are pretty interesting!
If you have anything to add, please do share.
Read next: Password Spray Attacks | Brute Force Attacks | Living Off The Land attacks | Surfing Attacks | Credential Stuffing attacks | Domain Fronting | Cold Boot Attacks.

