有时,我们不是使用逻辑和推理理论,而是按照直觉本能地理解事物。黑客攻击(Hacking)就是可以遵循这一原则的一个例子。我们知道,黑客可以以令人惊讶的方式访问您的设备,并将自己表现为我们可能不知道的不同头像。IRC 客户端(Clients)、特洛伊木马(Trojans)、后门是一些用于入侵计算机的恶意程序。我们至少能做的是寻找一些可能的指标,表明我们可能已经被黑客入侵,然后寻找一些快速的行动来对付它。以下是您如何知道您的Windows 计算机是否已被黑客入侵(Windows computer has been hacked)的方法。

我怎么知道我的电脑是否被黑客入侵了?
如果您看到以下迹象,您就知道您的计算机已被黑客入侵和入侵:
- 您的在线密码或设置已更改
- 您计算机的本地帐户密码已更改,或者您看到新的用户(User)帐户
- 您会在社交信息流中看到“由您制作”的奇怪帖子。或者,您的“朋友(Friends)”可能收到了据称来自您的不当信息。
- 您的朋友报告收到来自您的奇怪垃圾邮件或电子邮件。
- 您发现您的计算机上安装了新的程序或工具栏。
- 您收到来自虚假防病毒软件或其他流氓软件的消息(rogue software)
- 您的网速(Internet)变得缓慢而缓慢
- 网络(Network)活动显着增加。
- 您的防火墙(Firewall)正忙于阻止几个向外的连接请求
- 您的安全软件已被禁用。
- 主页或默认浏览器搜索引擎已被劫持
- 您的鼠标会自动移动以进行选择
- 您开始接到来自银行(Bank)、信用卡(Credit Card)公司、在线商店(Online Store)的关于未付款、银行余额下降、意外未结余额或购买的电话。
让我们详细看看其中一些标志,没有特定的顺序。(Let us take a look at some of these signs in detail, in no specific order.)
更改在线密码
如果您发现您的一个或多个在线密码突然更改,则您很可能已被黑客入侵。在这里,通常发生的情况是受害者在不知不觉中回复了一封看似真实的网络钓鱼电子邮件(Phishing email),据称该电子邮件声称来自该服务,最终密码已更改。黑客收集登录信息、登录、更改密码,并使用该服务从受害者或受害者的熟人那里窃取金钱。了解如何避免网络钓鱼诈骗和攻击(avoid Phishing Scams and Attacks),并采取措施防止您的在线身份盗窃(Online Identity Theft)。
作为一项损害控制措施,您可以立即通知所有联系人有关帐户被盗的信息。其次(Second),立即联系在线服务报告被盗帐户。大多数在线服务都知道这种恶意行为,并具有必要的实力和专业知识来恢复正常,并使用新密码使帐户恢复到您的控制之下。您可以恢复被黑的微软帐户(Microsoft Accounts)、谷歌帐户(Google Accounts)、Facebook 帐户(Facebook account)、Twitter 帐户(Twitter account)等,使用他们适当制定的程序。
(Amount)您的银行账户中缺少的金额
万一发生不幸,如果黑客访问了您的个人信息(信用卡(Credit Card)、网上银行(Online Banking)详细信息等),您可能会损失所有金钱。为避免这种情况,请打开交易警报,以便在发生异常情况时向您发送文本警报。许多金融机构允许您设置交易金额的阈值,如果超过阈值或转到国外,您会收到警告。遵循这些网上银行提示(Online Banking Tips)将是一个好主意。
虚假的防病毒消息
虚假(Fake)的防病毒警告消息是您的系统已被入侵的最可靠迹象之一。单击否或取消以停止虚假病毒扫描不会产生任何好处,因为损坏已经造成。这些程序通常利用Java 运行时环境(Java Runtime Environment)等未打补丁的软件来利用您的系统。
频繁的随机弹出窗口
此问题主要与您的浏览器有关,表明您的计算机上安装了不需要的软件或恶意软件,因为网站通常不会生成有害的弹出窗口。
重定向的互联网(Internet)搜索或主页
众所周知,大多数黑客通过将您的浏览器重定向到您想要访问的地址以外的其他地方来谋生。这肯定是因为黑客通过让您的点击出现在其他人的网站上而获得报酬,通常是那些不知道对其网站的点击来自恶意重定向的人。
您通常可以通过在流行搜索引擎的搜索栏中输入一些相关的、非常常见的词并检查是否出现与您的搜索相关的结果来发现或查明此类恶意软件。在受感染的计算机与未受感染的计算机上发送和返回的流量总是截然不同。
您的 PC 是否充当僵尸网络节点?
僵尸网络是受感染计算机的网络,由远程攻击者控制以执行诸如发送垃圾邮件或攻击其他计算机等非法任务。也许您的计算机已被入侵并充当Node。
提示(TIP):在继续之前,您可能想阅读我们的帖子——为什么有人要入侵我的电脑(Why would someone want to hack my computer)?
如果你的电脑被黑了怎么办?
1] 如果您觉得您的 Windows PC 可能已被劫持,您应该断开与Internet的连接并启动到安全模式并运行您的(boot into Safe Mode)防病毒软件(antivirus software)的全面深度扫描。如果您的安全软件已被禁用,请使用良好的按需防病毒扫描程序(on-demand antivirus scanner)。并从外部磁盘或USB运行它。
2] 您还可以使用专门的工具,例如Norton Power Eraser、反黑客软件或这些Botnet Removal Tools之一。
2] 您可以使用优秀的Browser Hijacker Removal 软件(Browser Hijacker Removal software)从浏览器中删除虚假工具栏。
3]打开(Open)您的控制面板(Control Panel)并卸载本质上可能看起来可疑的程序。
4] 当您连接到Internet时,打开命令提示符(Command Prompt),键入以下命令,然后按 Enter(Enter):
netstat –ano
- -a 参数列出所有计算机的连接和监听端口
- -n 参数显示地址和端口号
- -o 参数输出负责连接的进程 ID。
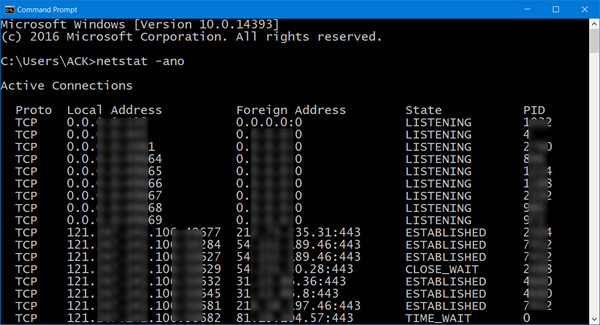
一目了然,IT 管理员将能够监视您打开的端口(Ports),以及系统中正在进行的网络活动。
检查(Check)任何可疑的连接。请记下任何显示“已建立”的连接和PID编号,并确保所有此类连接都是有效连接。如果需要,请按Ctrl+Shift+Esc调出任务管理器(Task Manager)。然后,将鼠标光标导航到“进程”选项卡并点击“查看”选项卡,选择列,然后检查进程标识符 PID(Process Identifier PID)列。立即显示完整的PID编号列表。在CMD(CMD)窗口中查找您刚才记下的数字。如果有疑问,请终止该过程。
5]安装带宽监控工具(bandwidth monitoring tool),以便您可以密切关注您的使用情况。使用数据包嗅探工具(Packet Sniffing Tools)拦截和记录网络流量。
随时更新您的操作系统和安装的软件,以关闭所有软件漏洞并使用良好的安全软件(security software)。让自己了解这些发展至关重要,因为在当今的威胁环境中,没有防病毒软件能让您 100% 安心。为了解决这个问题,应该使用监控程序行为的反恶意软件程序 -启发式(Heuristics)- 以捕获以前无法识别的恶意软件。其他使用虚拟化环境的程序、VPN、反黑客软件、网络流量检测软件也可以部署使用。
6]使用Detekt ,一款(Make)适用于(Detekt)Windows的免费反监视软件。
这里有一些技巧可以帮助您阻止黑客进入您的 Windows 计算机(tips that will help you keep Hackers out of your Windows computer)。(Here are some tips that will help you keep Hackers out of your Windows computer.)
如果您需要更多帮助,请阅读此恶意软件删除指南(Malware Removal Guide)。您可能还想阅读这篇标题为“如何判断您的计算机是否感染病毒(how do you tell if your computer has a virus)”的帖子。
How do I know if my Computer has been Hacked and what to do next
At timeѕ, rаther than using the theory of logic and reaѕoning, we follow our gut instinct to understand things instinctively. Hacking іs оne such instance where this principle may be followed. We know, hackers can get access to your devices in surprisіng ways and manifest thеmselves into different aνatars that we might not be aware of. IRC Clients, Trоjans, Backdoors are some of the malіcious programs that arе used to hack computers. The least we can do is look for some possible indicators suggesting we might have been hacked and then look for some quіck action against it. Here’s how you can know if your Windows computer has been hacked.

How do I know if my computer has been hacked?
You know that your computer has been hacked and compromised if you see the following signs:
- Your online passwords or settings have been changed
- Your computer’s local account passwords have been changed, or you see new User Accounts
- You see strange posts ‘made by you’ in your social feeds. Or maybe your ‘Friends’ are receiving inappropriate messages, allegedly from you.
- Your friends are reporting receiving strange spam or emails from you.
- You find that new programs or toolbars have been installed on your computer.
- You receive messages from fake antivirus or other rogue software
- Your Internet speed has become sluggish and slow
- There is a marked increase in Network activity.
- Your Firewall is busy blocking several outward connection requests
- Your security software has been disabled.
- The home page or default browser search engine has been hijacked
- Your mouse moves automatically to make selections
- You start getting calls from your Bank, Credit Card company, Online Store about non-payment, dip in the bank balance, unexpected outstanding balances or purchases.
Let us take a look at some of these signs in detail, in no specific order.
Change in online passwords
If you notice one or more of your online passwords have changed suddenly, you’ve more than likely been hacked. Here, usually what occurs is that the victim unknowingly responds to an authentic-looking Phishing email that purportedly claimed to be from the service ending up with the changed password. The hacker collects the log-on information, logs on, changes the password, and uses the service to steal money from the victim or the victim’s acquaintances. See how you can avoid Phishing Scams and Attacks and take steps to prevent your Online Identity Theft.
As a damage control action, you can immediately notify all your contacts about the account compromised. Second, immediately contact the online service to report the compromised account. Most online services are aware of this sort of maliciousness and have the requisite strength and expertise to restore things to normalcy and get the account back under your control with a new password. You can recover hacked Microsoft Accounts, Google Accounts, Facebook account, Twitter account, etc., using their properly laid down procedure.
Amount missing from your bank account
In the event of misfortune, you can lose all your money if a hacker gets access to your personal information (Credit Card, Online Banking details, etc.). To avoid this, turn on transaction alerts that send text alerts to you when something unusual is happening. Many financial institutions allow you to set thresholds on transaction amounts, and if the threshold is exceeded or it goes to a foreign country, you’ll be warned. It would be a good idea to follow these Online Banking Tips.
Fake antivirus messages
Fake antivirus warning messages are among the surest signs that your system has been compromised. Clicking No or Cancel to stop the fake virus scan yields no benefit since the damage is already done. These programs, often make use of unpatched software like the Java Runtime Environment to exploit your system.
Frequent random popups
This problem is mostly associated with your browsers and indicates you have unwanted software or malware installed on your computer since websites do not generally generate harmful pop-ups.
Redirected Internet searches or home page
It’s a well-known fact that most hackers make their living by redirecting your browser somewhere else than the address you would want to visit. That’s certainly because hacker gets paid by getting your clicks to appear on someone else’s website, often those who don’t know that the clicks to their site are from malicious redirection.
You can often spot or pinpoint this type of malware by simply typing a few related, very common words into the search bar of popular search engines and checking to see whether the results relevant to your search appear or not. The traffic sent and returned will always be distinctly different on a compromised computer vs. an uncompromised computer.
Is your PC acting as a Botnet Node?
Botnets are networks of compromised computers, controlled by remote attackers to perform such illicit tasks as sending spam or attacking other computers. Maybe your computer has been compromised and is acting as a Node.
TIP: Before you proceed, you might want to read our post – Why would someone want to hack my computer?
What to do if your computer has been hacked?

1] If you feel that your Windows PC may have been hijacked, you should disconnect from the Internet and boot into Safe Mode and run a full deep scan of your antivirus software. If your security software has been disabled, use a good on-demand antivirus scanner. and run it from an external disk or USB.
2] You may also use specialized tools like Norton Power Eraser, an anti-hacker software, or one of these Botnet Removal Tools.
2] You can remove bogus toolbars from the browser using a good Browser Hijacker Removal software.
3] Open your Control Panel and uninstall programs that may look suspicious in nature.
4] When you are connected to the Internet, open a Command Prompt, type the following command, and hit Enter:
netstat –ano
- -a parameter lists all the computer’s connections & listening ports
- -n parameter displays addresses & port numbers
- -o parameter outputs the process ID responsible for the connection.

With a glance, an IT administrator will be able to keep a watch on your open Ports, and the network activity which is going on in the system.
Check for any suspicious connection. Please note down that any connection that says – ‘Established’ and the PID number and ensure that all such connections are valid connections. If need be, press Ctrl+Shift+Esc to bring up the Task Manager. Then, navigate the mouse cursor to ‘Processes’ tab and hit the ‘View’ tab, select columns, and check the Process Identifier PID column. Instantly, the complete list of PID numbers will be displayed. Look for the number you noted down moments ago in the CMD window. If in doubt, terminate the process.
5] Install a bandwidth monitoring tool so that you can keep an eye on your usage. Use Packet Sniffing Tools intercept and log network traffic.
Keep your operating system and installed software updated at all times so as to close all software vulnerabilities and use a good security software. It is essential to keep yourself aware of these developments since, in today’s threatscape, no antivirus software offers 100% peace of mind. To combat this, antimalware programs that monitor program behaviors – Heuristics – to catch previously unrecognized malware should be used. Other programs that use virtualized environments, VPNs, anti-hacker software, and network traffic detection software can also be deployed for use.
6] Make use of Detekt, a free anti-surveillance software for Windows.
Here are some tips that will help you keep Hackers out of your Windows computer.
If you need more help, please go through this Malware Removal Guide. You may also like to read this post titled, how do you tell if your computer has a virus.



