Windows中的多用户功能使我们能够在学校、学院、办公室等公共场所方便地使用它。在这些地方,通常有一个管理员,他设法密切关注在其中工作的用户的活动。有时,用户会超出其限制并修改在工作组(Workgroup)模式下配置的帐户。这可能会产生安全影响,因此我们应该配置Windows以跟踪用户活动。
通过配置Windows来监控用户活动,我们可以提高管理的安全性,还可以通过观察受害者的记录来惩罚受害用户,以防万一。在本文中,我们将告诉您使用审核策略在Windows 11/10/8.1/8/7方法如下:
(Track User Activity)在工作组模式下(WorkGroup Mode)使用审核策略跟踪用户活动
1.按Windows Key + R组合,在运行(Run) 对话框中键入 put secpol.msc ,然后(secpol.msc)按 Enter(Enter)打开本地安全策略(Local Security Policy)。
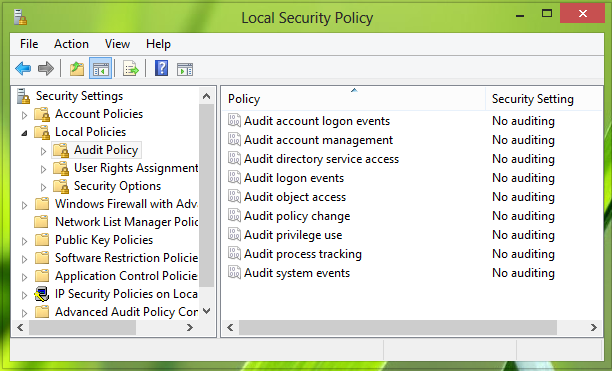
2.在本地安全策略(Local Security Policy)窗口中,展开安全设置(Security Settings)>本地策略(Local Policies)>审核策略(Audit Policy)。现在你应该让你的窗口与这个类似:
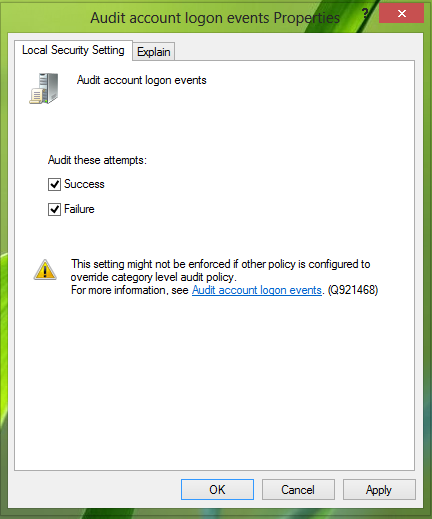
3.在右侧窗格中,您可以看到9 Audit...[]策略将无审核(No auditing)作为预定义的(pre-defined)安全设置。逐一单击(Click one)所有策略并选择成功(Success)和失败(Failure),单击应用( Apply),然后为每个策略单击确定(OK)。
通过这种方式,我们将配置Windows以跟踪用户活动。
按照以下步骤获取跟踪记录:
使用事件查看器跟踪用户活动(Trace User Activity Using Event Viewer)
1.按Windows Key + R组合,在运行(Run) 对话框中输入put eventvwr并按(eventvwr)Enter打开事件查看器(Event Viewer)。
2.现在,在事件查看(Event Viewe)器窗口的左窗格中,选择Windows 日志(Windows Logs)>安全性(Security)。在这里,Windows 会记录有关安全的每个事件。
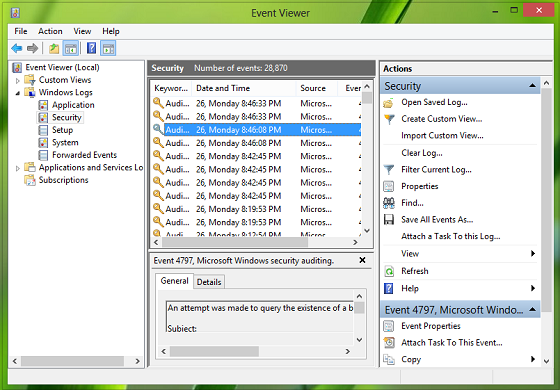
3.从中心窗格中,单击任何事件以获取其信息:
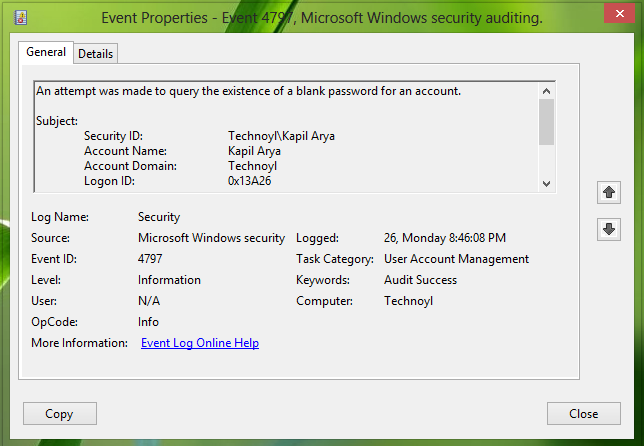
现在,这里是涵盖工作组模式中帐户的用户活动的事件ID列表:(IDs)
1.创建用户:(Create User:)以下是创建用户时记录的事件 ID(Event IDs)。
- 事件 ID:(Event ID: ) 4728 | 类型:(Type: )审核成功 | 类别:(Category: )安全组管理 | 说明:(Description: )已将成员添加到启用安全性的全局组中。
- 事件 ID:(Event ID: ) 4720 | 类型:(Type: )审核成功 | 类别:(Category: )用户帐户管理 | 描述:(Description: )创建了一个用户帐户。
- 事件 ID:(Event ID: ) 4722 | 类型:(Type: )审核成功 | 类别:(Category: )用户帐户管理 | 说明:(Description: )已启用用户帐户。
- 事件 ID:(Event ID: ) 4738 | 类型:(Type: )成功审计 | 类别:(Category: )用户帐户管理 | 说明:(Description: )用户帐户已更改。
- 事件 ID:(Event ID: ) 4732 | 类型:(Type: )成功审计 | 类别: (Category: )安全组管理 | 说明:(Description: )成员已添加到启用安全性的本地组。
2.删除用户:(Delete User: )以下是删除用户时记录的事件 ID(Event IDs)。
- 事件 ID:(Event ID: ) 4733 | 类型:(Type: )成功审计 | 类别: (Category: )安全组管理 | 说明:(Description: )已从启用安全性的本地组中删除成员。
- 事件 ID:(Event ID: ) 4729 | 类型:(Type: )成功审计 | 类别: (Category: )安全组管理 | 说明:(Description: )已将成员添加到启用安全性的全局组中。
- 事件 ID:(Event ID: ) 4726 | 类型:( Type: )成功审计 | 类别: (Category: )用户帐户管理 | 描述:(Description: )用户帐户已被删除。
3.禁用用户帐户:(User Account Disabled: )以下是禁用用户时记录的事件 ID(Event IDs)。
- 事件 ID:(Event ID: ) 4725 | 类型:(Type: )成功审计 | 类别: (Category: )用户帐户管理 | 说明:(Description: )用户帐户被禁用。
- 事件 ID:(Event ID: ) 4738 | 类型:(Type: )成功审计 | 类别: (Category: )用户帐户管理 | 说明:(Description: )用户帐户已更改。
4.启用用户帐户:(User Account Enabled: )以下是启用用户时记录的事件 ID(Event IDs)。
- 事件 ID:(Event ID: ) 4722 | 类型:(Type: )成功审计 | 类别: (Category: )用户帐户管理 | 说明:(Description: )已启用用户帐户。
- 事件 ID:(Event ID: ) 4738 | 类型:(Type: )成功审计 | 类别: (Category: )用户帐户管理 | 说明:(Description: )用户帐户已更改。
5.用户帐户密码重置:(User Account Password Reset: )以下是用户(User Account Password)帐户密码重置时记录的事件 ID(Event IDs)。
- 事件 ID:(Event ID: ) 4738 | 类型:(Type: )成功审计 | 类别: (Category: )用户帐户管理 | 说明:(Description: )用户帐户已更改。
- 事件 ID:(Event ID: ) 4724 | 类型:(Type: )成功审计 | 类别: (Category: )用户帐户管理 | 描述:(Description: )试图重置帐户的密码。
6.用户帐户配置文件路径集:(User Account Profile Path Set: )以下(Below)是为用户帐户设置配置文件路径(Profile Path)时记录的事件 ID(Event ID)。
- 事件 ID:(Event ID: ) 4738 | 类型:(Type: )成功审计 | 类别: (Category: )用户帐户管理 | 说明:(Description: )用户帐户已更改。
7.用户帐户重命名:(User Account Rename: )以下是用户(User Account)帐户重命名时记录的事件 ID(Event IDs)。
- 事件 ID:(Event ID: ) 4781 | 类型:(Type: )成功审计 | 类别: (Category: )用户帐户管理 | 描述:(Description: )帐户名称已更改。
- 事件 ID:(Event ID: ) 4738 | Type: 成功审计 | 类别: (Category: )用户帐户管理 | 说明:(Description: )用户帐户已更改。
8.创建本地组:(Create Local Group: )以下是创建本地(Local Group)组时记录的事件 ID(Event IDs)。
- 事件 ID:(Event ID: ) 4731 | 类型:(Type: )成功审计 | 类别: (Category: )安全组管理 | 说明:(Description: )已创建启用安全性的本地组
- 事件 ID:(Event ID: ) 4735 | 类型:(Type: )成功审计 | 类别: (Category: )安全组管理 | 说明:(Description: )已更改启用安全性的本地组
9.将用户添加到本地组:(Add User to Local Group: )以下(Below)是将用户添加到本地(Local)组时记录的事件 ID(Event ID)。
- 事件 ID:(Event ID: ) 4732 | 类型:(Type: )成功审计 | 类别: (Category: )安全组管理 | 说明:(Description: )已将成员添加到启用安全性的本地组
10.从本地组中删除用户:(Remove User from Local Group: )以下(Below)是 从本地(Local)组中删除用户时记录的事件 ID(Event ID)。
- 事件 ID:(Event ID: ) 4733 | 类型:(Type:)成功审计 | 类别:(Category:) 安全组管理 | 说明:(Description:)已从启用安全性的本地组中删除成员
11.删除本地组:(Delete Local Group: )以下(Below)是删除本地(Local Group)组时记录的事件 ID(Event ID)。
- 事件 ID:(Event ID: ) 4734 | 类型:(Type: )成功审计 | 类别: (Category: )安全组管理 | 说明:(Description: )已删除启用安全性的本地组
12.重命名本地组:(Rename Local Group: )以下是重命名本地组(Local Group)时记录的事件 ID(Event IDs)。
- 事件 ID:(Event ID: ) 4781 | 类型:(Type: )成功审计 | 类别: (Category: )用户帐户管理 | 描述:(Description: )帐户名称已更改
- 事件 ID:(Event ID: ) 4735 | 类型:(Type: )成功审计 | 类别: (Category: )安全组管理 | 说明:(Description: )已更改启用安全性的本地组
通过这种方式,您可以跟踪用户的活动。本文适用于工作组模式下的(Workgroup Mode)Windows 11/10/8.1。对于 Active Directory 域(Directory Domain),过程会有所不同。
How to track User Activity in WorkGroup Mode on Windows 11/10
Multi-user functionality in Windows has enabled us to use it conveniently in public places like schools, colleges, offices, etc. At these places, there is generally an administrator, who manages to keep an eye on the activities of users working therein. Sometimes, users go beyond their limits and modify accounts configured in Workgroup mode. This can have security repercussions, and thus we should configure Windows to track down user activities.
By configuring Windows for monitoring user activities, we can increase the security of the administration and can also punish the victim users by observing their records in case of an offense. In this article, we’ll tell you the way to track user activities in Windows 11/10/8.1/8/7 using Audit Policy. Here is how:
Track User Activity using Audit Policy in WorkGroup Mode
1. Press Windows Key + R combination, type put secpol.msc in Run dialog box and hit Enter to open the Local Security Policy.

2. In the Local Security Policy window, expand Security Settings > Local Policies > Audit Policy. Now you should get your window resembled with this one:

3. In the right pane, you can see 9 Audit…[] policies have No auditing as pre-defined security setting. Click one by one all the policies and make the selection to Success and Failure, click Apply followed by OK for each policy.

In this way, we will have configured Windows to track down user activity.
Follow these steps to get the traced records:
Trace User Activity Using Event Viewer
1. Press Windows Key + R combination, type put eventvwr in Run dialog box and hit Enter to open the Event Viewer.

2. Now, in the Event Viewer window, from the left pane, select Windows Logs > Security. Here Windows keeps a record of every event concerning security.

3. From the center pane, click any event to get its info:

Now, here is the list of the event IDs which covers the user activities for the accounts in the workgroup mode:
1. Create User: Below are the Event IDs that get logged when the user is created.
- Event ID: 4728 | Type: Audit Success | Category: Security Group Management | Description: A member was added to a Security-enabled global group.
- Event ID: 4720 | Type: Audit Success | Category: User Account Management | Description: A User account was created.
- Event ID: 4722 | Type: Audit Success | Category: User Account Management | Description: A User account was enabled.
- Event ID: 4738 | Type: Success Audit | Category: User Account Management | Description: A User account was changed.
- Event ID: 4732 | Type: Success Audit | Category: Security Group Management | Description: A member was added to a Security-enabled local group.
2. Delete User: Below are the Event IDs that get logged when the user is deleted.
- Event ID: 4733 | Type: Success Audit | Category: Security Group Management | Description: A member was removed from a Security-enabled local group.
- Event ID: 4729 | Type: Success Audit | Category: Security Group Management | Description: A member was added to a Security-enabled global group.
- Event ID: 4726 | Type: Success Audit | Category: User Account Management | Description: A User account was deleted.
3. User Account Disabled: Below are the Event IDs that get logged when the user is disabled.
- Event ID: 4725 | Type: Success Audit | Category: User Account Management | Description: A User account was disabled.
- Event ID: 4738 | Type: Success Audit | Category: User Account Management | Description: A User account was changed.
4. User Account Enabled: Below are the Event IDs that get logged when the user is enabled.
- Event ID: 4722 | Type: Success Audit | Category: User Account Management | Description: A User account was enabled.
- Event ID: 4738 | Type: Success Audit | Category: User Account Management | Description: A User account was changed.
5. User Account Password Reset: Below are the Event IDs that get logged when the User Account Password gets reset.
- Event ID: 4738 | Type: Success Audit | Category: User Account Management | Description: A User account was changed.
- Event ID: 4724 | Type: Success Audit | Category: User Account Management | Description: An attempt was made to reset an account’s password.
6. User Account Profile Path Set: Below is the Event ID that gets logged when Profile Path gets set for a user account.
- Event ID: 4738 | Type: Success Audit | Category: User Account Management | Description: A User account was changed.
7. User Account Rename: Below are the Event IDs that get logged when the User Account is renamed.
- Event ID: 4781 | Type: Success Audit | Category: User Account Management | Description: The name of an account was changed.
- Event ID: 4738 | Type: Success Audit | Category: User Account Management | Description: A User Account was changed.
8. Create Local Group: Below are the Event IDs that get logged when the Local Group is created.
- Event ID: 4731 | Type: Success Audit | Category: Security Group Management | Description: A Security-enabled local group was created
- Event ID: 4735 | Type: Success Audit | Category: Security Group Management | Description: A Security-enabled local group was changed
9. Add User to Local Group: Below is the Event ID that gets logged when the user gets added to the Local group.
- Event ID: 4732 | Type: Success Audit | Category: Security Group Management | Description: A member was added to a Security-enabled local group
10. Remove User from Local Group: Below is the Event ID that gets logged when the user is removed from the Local group.
- Event ID: 4733 | Type: Success Audit | Category: Security Group Management | Description: A member was removed from a Security-enabled local group
11. Delete Local Group: Below is the Event ID that gets logged when the Local Group is deleted.
- Event ID: 4734 | Type: Success Audit | Category: Security Group Management | Description: A Security-enabled local group was deleted
12. Rename Local Group: Below are the Event IDs that get logged when the Local Group is renamed.
- Event ID: 4781 | Type: Success Audit | Category: User Account Management | Description: A name of an account was changed
- Event ID: 4735 | Type: Success Audit | Category: Security Group Management | Description: A Security-enabled local group was changed
In this way, you can trace users with their activities. This article is applicable for Windows 11/10/8.1 in Workgroup Mode. For Active Directory Domain, the procedure will be different.






