域名前置(Domain Fronting)可用作绕过ISP(ISPs)和政府审查的工具。黑客也可以使用域前端从您那里获取他们想要的信息。(Domain Fronting)什么是域名前置?本文简要解释了域前置,并通过解释域前置的优点和危险,让您决定它是好是坏。
领域前沿解释
(Domain)简而言之,域前端正在使用加密中途改变互联网连接的目的地。如果您想浏览受限制的网站,您可以使用以下方法之一来访问它:
- 代理
- VPN
- 托尔
- 领域前沿
问题是许多政府正在禁止或限制不同ISP网络上的VPN和TOR流量。(TOR)ISP有来自这些政府的特定命令,以禁止一个或多个任何性质的网站。早在八到十年前,我们可以轻松使用代理并访问受限制的网站。技术(Technology)发生了变化,现在比以往任何时候都更容易检测使用代理的流量。不仅如此,现在还可以使用一些军用级技术破解TOR(洋葱路由器)。(The Onion Router)这两种方法不再是访问受限网站的可行方法。
因此,我们只剩下VPN和Domain Fronting。为了审查和关注其公民的行为,许多国家也禁止/限制VPN(VPNs)。他们不想要加密流量,以便他们知道发生了什么。ISP(ISPs)不能反抗任何限制或禁止VPN的国家/地区的政府。他们必须答应。
访问受限网站的最后一种方法是应用域前置。但是,作为用户,您不能应用域前置。您必须使用使用域前端的应用程序。Telegram就是一个这样的应用程序——被俄罗斯(Russia)和更多国家禁止的聊天应用程序。
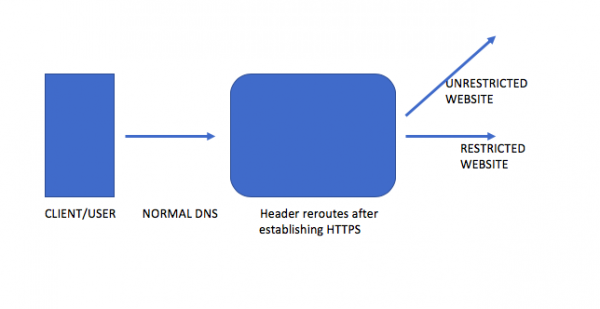
这些应用程序具有内置算法,允许用户访问受限制的网站或在用户所在的特定国家/地区被禁止的网站。这是通过更改主机网站标头中的代码来完成的。对于监考人员,它通常表明它正在连接到一个无辜的网站,可能也没有HTTPS。在网站和应用之间的握手过程中,应用首先建立一个加密连接(可以像HTTPS一样简单),然后切换到另一个网站的路由。该网站可能是被禁止或受限制的网站。
因此,有可能欺骗ISP和政府级别的监考人员联系受限制的网站,而互联网(Internet)警察认为您一直在与被禁止的网站通信时连接到其他网站。
域名前置(Domain Fronting)可用于规避任何类型的审查。这是好的部分。下一节将讨论域前置的危险。
领域前沿的危险
虽然域前端被用于让用户访问受限制的网站和服务,但黑客很有可能使用相同的技术来误导用户并挖掘他们想要的数据。
同名域和受限制的网站(或受感染的网站,如果是黑客)都托管在同一组服务器上。当一个人尝试连接到同名域时,其标头会发送另一个GET请求,该请求会为其提供受限制网站的地址。现在,这可能是一个简单的受政府限制的网站或被黑客感染的计算机。
取决于谁在使用域前端,它既有利又危险。虽然大多数情况下,私人消息应用程序都在使用该技术,但谷歌(Google)和亚马逊(Amazon)都抛弃了Telegram,称它们违反了他们的条款和条件(Conditions)。目前(Currently),Telegram正在寻找其他可以为他们提供领域前沿能力的云服务。
在其他几个案例中,领域前沿的使用是真实的——允许言论自由。但似乎世界各国政府正在关闭所有通往言论自由的途径。同时,我们可以说域名前端有其自身的危险,因为如果它可以取代目的地,它可能会导致您访问虚假网站,而您永远不会知道。
现在阅读(Now read):什么是冷启动攻击(Cold Boot Attack)?
Domain Fronting explained along with Dangers and
Domain Fronting can be used as a tool to bypass censorship by ISPs and governments. Domain Fronting can also be used by hackers to obtain the information they want from you. What is domain fronting? This article explains domain fronting in brief and lets you decide if it is good or bad by explaining both the advantage and dangers of domain fronting.

Domain Fronting explained
Domain fronting, in short, is changing the destination of an internet connection midway using encryption. If you want to browse a restricted website, you can use one of the following methods to reach it:
- Proxy
- VPN
- TOR
- Domain Fronting
The problem is that many governments are banning or restricting VPN and TOR traffic on different ISP networks. ISPs have specific orders from such governments to ban one or more website of any nature. Earlier, eight to ten years ago, we could easily use a proxy and reach the restricted website. Technology changed, and now it is easier than ever to detect traffic that is using a proxy. Not only that, but TOR (The Onion Router) can also be cracked now with some military grade techniques. Those two are no more viable methods to access restricted websites.
Thus, we are left with VPN and Domain Fronting. In an attempt to censor and to keep an eye on what its citizens are doing, many countries are banning/restricting VPNs too. They do not want encrypted traffic so that they know what is going on. The ISPs cannot rebel against the government of any country that restricts or bans VPN. They have to oblige.
The last method to access a restricted website is to apply domain fronting. You, as a user, cannot apply domain fronting though. You have to use an app that employs domain fronting. One such app is Telegram – the chatting app banned by Russia and many more countries.
These apps have built-in algorithms that allow users to access restricted websites or websites banned in that particular country where the user is located. This is done by altering the code in the header in the host websites. For invigilators, it generally shows that it is connecting to an innocent website, probably without HTTPS too. In the middle of the handshake between the website and app, the app first establishes an encrypted connection (could be as simple as HTTPS) and then switches route to another website. That website may be a banned or restricted website.
Thus, it is possible to cheat the invigilators at ISP and government levels to contact a restricted website while the Internet police think you are connected to some other website when all the time you were communicating with the banned website.
Domain Fronting can be used to circumvent any type of censorship. That’s the good part. The next section talks about the dangers of domain fronting.
Dangers of Domain Fronting
While domain fronting is being used to let users access restricted websites and services, there is a good chance that hackers might use the same technique to mislead users and mine the data they want.
Both the namesake domain and the restricted website (or infected website, in case of hackers) are hosted on the same set of servers. When one tries to connect to the namesake domain, its header sends another GET request that gives it the address of the restricted website. Now, this could be a simply restricted-by-government website or a computer infected by hackers.
Depending upon who is using domain fronting, it is both advantageous and dangerous. While mostly, private messaging apps were using the technique, both Google and Amazon dumped Telegram saying they are against their Terms and Conditions. Currently, Telegram is looking for other cloud service that would provide them with the ability of domain fronting.
There are several other cases where the use of domain fronting was genuine – to allow free speech. But it seems the world governments are closing all routes to freedom of expression. In the same breath, we can say domain fronting has its own dangers because if it can replace destination, it may lead you to fake sites, and you won’t ever know.
Now read: What is a Cold Boot Attack?

