您是否曾经感到网络速度异常缓慢或某个网站意外不可用?有可能正在进行拒绝服务攻击。(Denial of Service attack)您可能熟悉“拒绝服务(Denial of Service)”这个术语,但实际上,很难区分真正的攻击和正常的网络活动。拒绝服务(或 DoS)(Denial of Service (or DoS))攻击,顾名思义,与拒绝服务直接相关,尤其是互联网(Internet)。
DoS攻击是一种吞噬用户资源并使网络瘫痪,从而阻止合法用户访问任何网站的攻击。DoS攻击一直是并且仍然是最复杂的攻击之一,没有潜在的预防策略。在这篇文章中,我们将阐明什么是DoS攻击以及如何更好地防止它以及在您知道自己受到攻击时该怎么做。
什么是DoS或(DoS)拒绝服务(Denial)攻击(Service Attack)
在DoS攻击中,具有恶意意图的攻击者会阻止用户访问服务。他通过针对您的计算机及其网络连接或您尝试使用的网站的计算机和网络来做到这一点。因此,他可以阻止您访问您的电子邮件或在线帐户。
想象一种情况,您正尝试登录您的网上银行(Internet Banking)帐户进行在线交易活动。然而,尽管看起来很奇怪,尽管您拥有快速的互联网连接,但您仍被拒绝访问银行的网站。现在可能有两种可能性 - 您的互联网服务提供商已关闭或您受到DoS攻击!
在DoS攻击中,攻击者向相关网站的主服务器发送大量多余的请求,这基本上会使其过载并在保留容量之前阻止任何进一步的请求。这会导致对本网站传入的合法请求的拒绝,因此,您是受害者( you’re the victim)。
但是,攻击方式可能会根据攻击者的动机而有所不同,但这是发起DoS攻击的最常见方式。其他攻击方式可能包括阻止特定人员访问某个网站,在服务器端阻塞两台机器之间的连接,从而中断服务等。
一些攻击者还对另一种DoS攻击采取行动——电子邮件轰炸(Email bombing),其中大量垃圾邮件被生成并涌入一个人的收件箱(Inbox),从而阻止对邮件服务器的任何进一步请求。这可能会广泛发生,即使是在您的雇主提供给您的电子邮件帐户上,更不用说雅虎、Outlook 等(Yahoo, Outlook, etc)公共邮件服务了。由于分配的存储配额将被填满,您甚至可能无法再接收任何合法电子邮件。由于他们的野心多种多样,攻击者的动机可能从“只是为了好玩”到财务上的成功再到报复。
相关(Related):浏览器卡在访问(Checking Your Browser Before Accessing)消息之前检查您的浏览器。
DoS 攻击的类型
根据攻击的性质和意图,有几种类型的程序可用于在您的网络上发起DoS攻击。请注意以下最常用的DoS攻击:
1] SYN洪水
SYN Flood过度利用了打开TCP连接的标准方法。当客户端想要打开与服务器开放端口的TCP连接时,它会发送一个SYN数据包。服务器接收数据包,对其进行处理,然后发回一个SYN-ACK数据包,其中包含存储在传输控制块 (TCB)(Transmission Control Block (TCB))表中的源客户端信息。在正常情况下,客户端会发回一个确认服务器响应的ACK数据包,从而打开TCP连接。然而,在潜在的SYN 洪水攻击下(SYN flood attack),攻击者使用模仿 IP 地址发出大量连接请求,目标机器将其视为合法请求。随后,它忙于处理其中的每一个,并尝试为所有这些恶意请求打开连接。
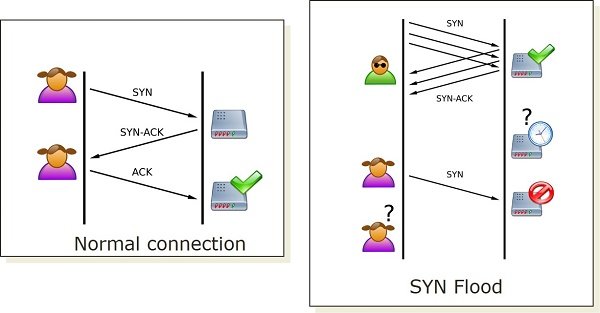
在正常情况下,客户端会发回一个确认服务器响应的ACK数据包,从而打开TCP连接。然而,在潜在的SYN洪水攻击下,攻击者使用模仿 IP 地址发出大量连接请求,目标计算机将其视为合法请求。随后,它忙于处理其中的每一个,并尝试为所有这些恶意请求打开连接。这导致服务器继续等待每个实际上从未到达的连接请求的ACK数据包。(ACK)这些请求很快填满了服务器的TCB表之前,它可以使任何连接超时,因此任何进一步的合法连接请求都被推入等待队列。
阅读(Read):什么是赎金拒绝服务(What is Ransom Denial of Service)?
2] HTTP洪水
这最常用于攻击 Web 服务和应用程序。这种攻击并没有过多强调高速网络流量,而是发出一个完整且看似有效的HTTP POST 请求(HTTP POST requests)。专门为耗尽目标服务器的资源而设计的,攻击者会发出许多这样的请求,以确保目标服务器在忙于处理虚假请求时不会拉过进一步的合法请求。然而如此简单,但很难将这些HTTP请求与有效请求区分开来,因为Header的内容在这两种情况下似乎都是可接受的。
3]分布式拒绝(Distributed Denial)服务攻击(Service Attack)(DDoS)

分布式拒绝服务(Distributed Denial of Service)或DDoS攻击就像这个团伙中的装饰人员。DDoS比普通DoS攻击要复杂得多,它通过不止一台计算机在目标机器上生成流量。攻击者同时控制多台受感染的计算机和其他设备,并分配使目标服务器充满流量的任务,从而严重消耗其资源和带宽。如果存在挥之不去的安全问题,攻击者还可以使用您的计算机对另一台计算机发起攻击。
现在,很明显,与DoS相比, (DoS)DDoS 攻击(DDoS attack)可以更加有效和真实 。一些可以轻松处理多个连接的网站可以通过同时发送大量垃圾邮件请求来轻松关闭。僵尸网络(Botnets)用于招募各种易受攻击的设备,这些设备的安全性可能会受到威胁,方法是向其中注入病毒并将其注册为僵尸军队(Zombie army),攻击者可以控制这些设备并将其用于DDoS攻击。因此(Hence),作为普通的计算机用户,您需要注意系统中和系统周围的安全漏洞,否则您可能最终会做某人的肮脏工作而永远不会知道它。
DoS 攻击预防
DoS攻击无法预先确定。您无法阻止成为DoS攻击的受害者。没有很多有效的方法。但是,您可以减少成为此类攻击的一部分的可能性,因为您的计算机可用于攻击另一台计算机。请注意以下要点,这些要点可以帮助您获得对您有利的机会。
- 如果尚未完成,请将防病毒(antivirus)程序和防火墙(firewall)部署到您的网络中。这有助于将带宽使用限制为仅经过身份验证的用户。
- 服务器配置(Server configuration)可以帮助减少被攻击的可能性。如果您是某家公司的网络管理员,请查看您的网络配置并强化防火墙策略以阻止未经身份验证的用户访问服务器资源。
- 一些第三方服务提供针对(third-party services)DoS攻击的指导和保护。这些可能很昂贵但也很有效。如果您有资金在您的网络中部署此类服务,那么最好开始。
DoS 攻击通常针对高知名度的组织(high-profile organizations),例如银行和金融部门的公司、贸易和商业存根等。人们应该充分意识到并保持警惕,以防止任何潜在的攻击。虽然这些攻击与机密信息的盗窃没有直接关系,但它可能会花费受害者大量的时间和金钱来解决这个问题。
有用的链接:(Useful links:)
- 防止拒绝(Denial)服务(MSDN)攻击(Service Attacks)– MSDN
- DoS/Denial服务攻击(Service Attacks)的最佳实践– MSDN
- 了解拒绝服务攻击(Denial-of-Service Attacks)– US-Cert.go v
- 保护Office 365 免受拒绝(Against Denial)服务攻击 - 阅读(Service Attacks – Read)Microsoft的更多信息
- 图片来源维基百科。
Denial of Service (DoS) Attack: What it is and how to prevent it
Have you ever felt an unusual slowness in your network speed or unexpected unavailability of a certain website? Chances could be that there сould be a Denial of Service attack in progress. You might be familiar with the term – Denial of Service but in reality, it can be difficult to distinguish between a real attack and normal network activity. Denial of Service (or DoS) attack, which, as the name suggests, directly relates to being denied a service, notably, the Internet.
A DoS attack is a kind of attack that eats upon the resources of a user and brings the network down to its knees, thereby preventing legitimate users from accessing any website. The DoS attack has been and remains one of the most sophisticated attacks to which one does not have a potential prevention policy. In this post, we’ll shed some light on what is a DoS attack and how to better prevent it and what to do in case you know that you’re attacked.
What is DoS or Denial of Service Attack
In a DoS attack, an attacker with malicious intent prevents users from accessing a service. He does so by either targeting your computer and its network connection, or the computers and network of the website that you are trying to use. He can thus prevent you from accessing your email or online accounts.
Imagine a situation, where you are trying to log into your Internet Banking account for online transaction activity. However, as strange as it may seem, you are denied access to the bank’s website, in spite of having a swift internet connection. Now there could be two possibilities – either your internet service provider is down or you’re under a DoS attack!
In a DoS attack, the attacker sends out a flood of superfluous requests to the main server of the website in question, which basically overloads it and blocks out any further requests before the capacity is retained back. This causes a denial of the incoming legitimate requests for this website and consequentially, you’re the victim.
However, the ways of attack may differ based on the motives of the attacker but this is the most common way to launch a DoS attack. Other ways of attacking may involve preventing a particular person from accessing a certain website, obstructing the connection between two machines at the server end, therefore, disrupting the service, etc.
Some attackers also act on another kind of DoS attack – Email bombing in which a lot of spam emails are generated and flooded into one’s Inbox so that any further request to the mail server is debarred. This can happen widely, even on the email account provided to you by your employers, not to mention the public mail services like Yahoo, Outlook, etc. You can even get deprived of receiving any further legitimate emails as your allotted storage quota will be filled up. With a great deal of variety in their ambitions, the motivation of attackers may range from ‘just-for-fun’ to financial clinch to revenge.
Related: Browser stuck at Checking Your Browser Before Accessing message.
Types of DoS Attacks
Based on the nature and intent of the attack, there are several types of programs that can be used to launch DoS attacks on your network. Take a note of the below most commonly used DoS attacks:
1] SYN Flood
SYN Flood takes undue advantage of the standard way to open a TCP connection. When a client wants to open a TCP connection with the server’s open port, it sends out a SYN packet. The server receives the packets, processes it, and then sends back a SYN-ACK packet which includes the source client’s information stored in Transmission Control Block (TCB) table. Under normal circumstances, the client would send back an ACK packet acknowledging the server’s response and hence opening a TCP connection. However, under a potential SYN flood attack, the attacker sends out an army of connection requests using a parody IP address which are treated as legitimate requests by the target machine. Subsequently, it gets busy processing each one of these and makes an attempt to open a connection for all of these malevolent requests.

Under normal circumstances, the client would send back an ACK packet acknowledging the server’s response and hence opening a TCP connection. However, under a potential SYN flood attack, the attacker sends out an army of connection requests using a parody IP address which are treated as legitimate requests by the target machine. Subsequently, it gets busy processing each one of these and makes an attempt to open a connection for all of these malevolent requests. This causes the server to keep waiting for an ACK packet for each connection request which actually never arrives. These requests quickly fill up the server’s TCB table before it can time any connection out and thus any further legitimate connection requests are pushed into the waiting queue.
Read: What is Ransom Denial of Service?
2] HTTP Flood
This is most commonly used for attacking web services and applications. Without putting much emphasis on high-rate network traffic, this attack sends out a complete and seemingly valid HTTP POST requests. Designed specifically to exhaust the target server’s resources, the attacker sends out a number of these requests to make sure the further legitimate requests are not pulled through by the target server while it is busy processing the fake requests. Yet so simple but it is very difficult to distinguish these HTTP requests from the valid ones as the content of the Header seems admissible in both the cases.
3] Distributed Denial of Service Attack (DDoS)

Distributed Denial of Service or DDoS attack is like the decorated officer in this gang. Much sophisticated by levels above normal DoS attack, DDoS generates the traffic on the target machine via more than one computer. The attacker controls several compromised computers and other devices at once and distributes the task of flooding the target server with traffic, heavily eating on its resources and bandwidth. The attacker can also use your computer to launch an attack on another computer if there are lingering security issues.
Now, as obvious as it is, a DDoS attack can be much more effective and real when comparing to DoS. Some websites which can easily handle multiple connections can be brought down easily by sending numerous simultaneous spam requests. Botnets are used to recruit all sorts of vulnerable devices whose security can be compromised by injecting a virus into them and signing them up for Zombie army which the attacker can control and use them for a DDoS attack. Hence, being a normal computer user, you need to be aware of security loopholes in and around your system otherwise you might end up doing somebody’s dirty work and never know about it.
DoS attack prevention
DoS attacks can not be pre-determined. You can’t prevent being a victim of the DoS attack. There are not many effective ways to that. However, you can reduce the prospect of being a part of such an attack where your computer can be used to attack another. Take note of below salient points which can help you get the odds in your favor.
- Deploy an antivirus program and firewall into your network if not already done. This helps in restricting the bandwidth usage to authenticated users only.
- Server configuration can help diminish the probability of being attacked. If you’re a network administrator at some firm, take a look at your network configurations and harden the firewall policies to block out unauthenticated users from addressing the server’s resources.
- Some third-party services offer guidance and protection against DoS attacks. These can be expensive but effective as well. If you have the capital to deploy such services in your network, better get going.
DoS attacks are generally targeted to high-profile organizations such as banking and financial sector companies, trade and commercial stubs, etc. One should be fully aware and keep looking over one’s shoulder to prevent any potential attacks. Although these attacks do not directly relate to the theft of confidential information, it can cost the victims a hefty sum of time and money to get rid of the problem.
Useful links:
- Preventing Denial of Service Attacks – MSDN
- Best Practices for Preventing DoS/Denial of Service Attacks – MSDN
- Understanding Denial-of-Service Attacks – US-Cert.gov
- Defending Office 365 Against Denial of Service Attacks – Read more at Microsoft
- Image source Wikipedia.


