LDAP 签名(LDAP signing)是Windows Server中的一种身份验证方法,可以提高目录服务器的安全性。一旦启用,它将拒绝任何不要求签名或请求使用非 SSL/TLS 加密的请求。在这篇文章中,我们将分享如何在Windows Server和客户端计算机中启用LDAP签名。LDAP代表 轻量级目录访问协议(Lightweight Directory Access Protocol)(LDAP)。
如何在Windows计算机中启用LDAP签名
为了确保攻击者不使用伪造的LDAP客户端来更改服务器配置和数据,启用(LDAP)LDAP签名至关重要。在客户端机器上启用它同样重要。
- 设置(Set)服务器LDAP签名要求
- (Set)使用本地(Local)计算机策略设置客户端LDAP签名要求(LDAP)
- (Set)使用域组策略对象(Domain Group Policy Object)设置客户端LDAP签名要求(LDAP)
- (Set)使用注册表(Registry)项设置客户端LDAP签名要求(LDAP)
- 如何验证配置更改
- 如何找到不使用“需要(Require)签名”选项的客户
最后一部分帮助您找出未在计算机上启用“要求签名”的客户端。(do not have Require signing enabled)它是 IT 管理员隔离这些计算机并在计算机上启用安全设置的有用工具。
1]设置(Set)服务器LDAP签名要求
- 打开Microsoft 管理控制台(Microsoft Management Console)(mmc.exe)
- 选择文件 > 添加(Add)/删除管理单元 > 选择 组策略对象编辑器(Group Policy Object Editor),然后选择 添加(Add)。
- 它将打开组策略向导(Group Policy Wizard)。单击(Click)浏览按钮,然后选择 默认(Browse)域策略(Default Domain Policy)而不是本地计算机
- 单击(Click)确定按钮,然后单击完成(Finish)按钮,然后将其关闭。
- 选择 Default Domain Policy > Computer Configuration > Windows Settings > Security Settings > Local Policies,然后选择安全选项。
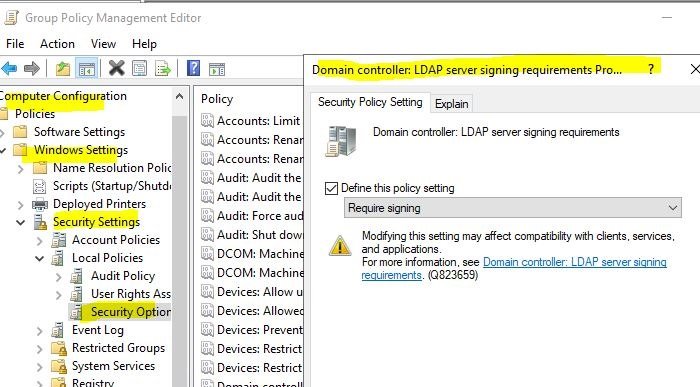
- 右键单击 域控制器:LDAP 服务器签名要求(Domain controller: LDAP server signing requirements),然后选择属性。
- 在 域(Domain)控制器:LDAP服务器签名要求属性(Properties) 对话框中,启用 定义(Define)此策略设置, 在定义此策略设置列表中选择要求签名,(Require signing in the Define this policy setting list,)然后选择确定。
- 重新检查设置并应用它们。
2]使用本地计算机策略设置(Set)客户端LDAP签名要求(LDAP)
- 打开运行(Run)提示,输入 gpedit.msc,然后按Enter键。
- 在组策略编辑器中,导航到 Local Computer Policy > Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies,然后选择 安全选项。(Security Options.)
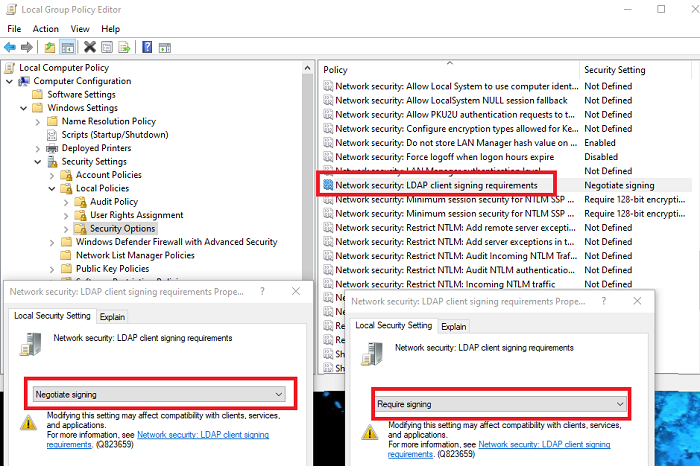
- 右键单击网络安全:LDAP 客户端签名要求(Network security: LDAP client signing requirements),然后选择属性。
- 在 网络(Network)安全:LDAP客户端签名要求属性(Properties) 对话框中,选择 列表中的要求签名(Require signing),然后选择确定。
- 确认更改并应用它们。
3]使用域组策略对象(Group Policy Object)设置(Set)客户端LDAP签名要求(LDAP)
- 打开 Microsoft 管理控制台 (mmc.exe)(Open Microsoft Management Console (mmc.exe))
- 选择 文件(File) > Add/Remove Snap-in > 选择 组策略对象编辑器(Group Policy Object Editor),然后选择 添加(Add)。
- 它将打开组策略向导(Group Policy Wizard)。单击(Click)浏览按钮,然后选择 默认(Browse)域策略(Default Domain Policy)而不是本地计算机
- 单击(Click)确定按钮,然后单击完成(Finish)按钮,然后将其关闭。
- 选择 默认域策略(Default Domain Policy) > 计算机配置(Computer Configuration) > Windows 设置(Windows Settings) > 安全设置(Security Settings) > 本地策略(Local Policies),然后选择 安全选项(Security Options)。
- 在 网络安全:LDAP 客户端签名要求属性 (Network security: LDAP client signing requirements Properties )对话框中,选择 列表中的要求签名 (Require signing ),然后选择 确定(OK)。
- 确认(Confirm)更改并应用设置。
4]使用注册表项设置(Set)客户端LDAP签名要求(LDAP)
首先要做的就是备份您的注册表
- 打开注册表编辑器
- 导航到HKEY_LOCAL_MACHINE \ SYSTEM \ CurrentControlSet \ Services \ <InstanceName> \Parameters
- 右键单击(Right-click)右侧窗格,然后创建一个名为LDAPServerIntegrity的新(LDAPServerIntegrity)DWORD
- 将其保留为默认值。
<InstanceName >:要更改的AD LDS实例的名称。(AD LDS)
5]如何(How)验证配置更改现在是否需要登录
为了确保安全策略在这里起作用是如何检查其完整性。
- 登录到安装了AD DS 管理工具(AD DS Admin Tools)的计算机。
- 打开运行(Run)提示符,键入 ldp.exe,然后按Enter键。它是用于在Active Directory(Active Directory)命名空间中导航的 UI
- 选择连接 > 连接。
- 在 服务器(Server) 和 端口(Port)中,键入目录服务器的服务器名称和非 SSL/TLS 端口,然后选择确定。
- 建立连接后,选择连接 > 绑定。
- 在 绑定(Bind)类型下,选择 简单(Simple)绑定。
- 键入用户名和密码,然后选择确定。
如果您收到一条错误消息说 Ldap_simple_bind_s() failed: Strong Authentication Required,那么您已经成功配置了目录服务器。
6]如何(How)找到不使用“要求(Require)签名”选项的客户
每次客户端计算机使用不安全的连接协议连接到服务器时,它都会生成事件 ID 2889(Event ID 2889)。日志条目还将包含客户端的 IP 地址。您需要通过将16 LDAP Interface Events 诊断设置设置为 2(基本)来启用此功能。(2 (Basic). )在 Microsoft(here at Microsoft)了解如何配置 AD 和LDS诊断事件日志记录。
LDAP 签名(LDAP Signing)至关重要,我希望能够帮助您清楚地了解如何在Windows Server和客户端计算机上启用LDAP签名。
How to enable LDAP signing in Windows Server & Client Machines
LDAP signing is an authentication method in Windows Server that can improve the security of a directory server. Once enabled, it will reject any request that doesn’t ask for signing or if the request is using non-SSL/TLS-encrypted. In this post, we will share how you can enable LDAP signing in Windows Server and client machines. LDAP stands for Lightweight Directory Access Protocol (LDAP).
How to enable LDAP signing in Windows computers
To make sure that the attacker doesn’t use a forged LDAP client to change server configuration and data, it is essential to enabling LDAP signing. It is equally important to enable it on the client machines.
- Set the server LDAP signing requirement
- Set the client LDAP signing requirement by using Local computer policy
- Set the client LDAP signing requirement by using the Domain Group Policy Object
- Set the client LDAP signing requirement by using Registry keys
- How to verify configuration changes
- How to find clients that do not use the “Require signing” option
The last section helps you to figure out clients that do not have Require signing enabled on the computer. It is a useful tool for IT admins to isolate those computers, and enable the security settings on the computers.
1] Set the server LDAP signing requirement

- Open Microsoft Management Console (mmc.exe)
- Select File > Add/Remove Snap-in > select Group Policy Object Editor, and then select Add.
- It will open the Group Policy Wizard. Click on the Browse button, and select Default Domain Policy instead of Local Computer
- Click on the OK button, and then on the Finish button, and close it.
- Select Default Domain Policy > Computer Configuration > Windows Settings > Security Settings > Local Policies, and then select Security Options.
- Right-click Domain controller: LDAP server signing requirements, and then select Properties.
- In the Domain controller: LDAP server signing requirements Properties dialog box, enable Define this policy setting, select Require signing in the Define this policy setting list, and then select OK.
- Recheck the settings and apply them.
2] Set the client LDAP signing requirement by using local computer policy

- Open Run prompt, and type gpedit.msc, and press the Enter key.
- In the group policy editor, navigate to Local Computer Policy > Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies, and then select Security Options.
- Right-click on Network security: LDAP client signing requirements, and then select Properties.
- In the Network security: LDAP client signing requirements Properties dialog box, select Require signing in the list and then choose OK.
- Confirm changes and apply them.
3] Set the client LDAP signing requirement by using a domain Group Policy Object
- Open Microsoft Management Console (mmc.exe)
- Select File > Add/Remove Snap-in > select Group Policy Object Editor, and then select Add.
- It will open the Group Policy Wizard. Click on the Browse button, and select Default Domain Policy instead of Local Computer
- Click on the OK button, and then on the Finish button, and close it.
- Select Default Domain Policy > Computer Configuration > Windows Settings > Security Settings > Local Policies, and then select Security Options.
- In the Network security: LDAP client signing requirements Properties dialog box, select Require signing in the list and then choose OK.
- Confirm changes and apply the settings.
4] Set the client LDAP signing requirement by using registry keys
The first and foremost thing to do is take a backup of your registry
- Open Registry Editor
- Navigate to HKEY_LOCAL_MACHINE \ SYSTEM \ CurrentControlSet \ Services \ <InstanceName> \Parameters
- Right-click on the right pane, and create a new DWORD with name LDAPServerIntegrity
- Leave it to its default value.
<InstanceName>: Name of the AD LDS instance that you want to change.
5] How to verify if configuration changes now require sign-in
To make sure the security policy is working here is how to check its integrity.
- Sign in to a computer that has the AD DS Admin Tools installed.
- Open Run prompt, and type ldp.exe, and press the Enter key. It is a UI used for navigating through the Active Directory namespace
- Select Connection > Connect.
- In Server and Port, type the server name and the non-SSL/TLS port of your directory server, and then select OK.
- After a connection is established, select Connection > Bind.
- Under Bind type, select Simple bind.
- Type the user name and password, and then select OK.
If you receive an error message saying Ldap_simple_bind_s() failed: Strong Authentication Required, then you have successfully configured your directory server.
6] How to find clients that do not use the “Require signing” option
Every time a client machine connects to the server using an insecure connection protocol, it generates Event ID 2889. The log entry will also contain the IP addresses of the clients. You will need to enable this by setting the 16 LDAP Interface Events diagnostic setting to 2 (Basic). Learn how to configure AD and LDS diagnostic event logging here at Microsoft.
LDAP Signing is crucial, and I hope the was able to help you clearly understand how you can enable LDAP signing in Windows Server, and on the client machines.


