访问恶意网站可能是浏览Internet的人可能发生的最糟糕的事情之一,尤其是那些对在线购物感兴趣的人。网站管理员需要了解网站的威胁,以及它们的破坏性能力——首先失去消费者基础。如果您运行网站或博客,则需要了解可能的网站威胁。本文讨论了威胁及其后果,黑客用来破坏您的网站的一些方法,然后讨论了如何保持网站安全的方法。
网站(Website) 威胁(Threats)及其影响(Their) 或(Effects)能力
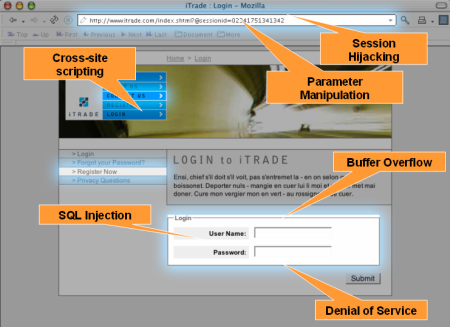
黑客窃取人们的数据并将其用于个人利益是一项有利可图的业务。收益可以是货币的或抽象的。虽然黑客攻击、网络钓鱼和社会工程是常见的方法,但黑客也使用其他人的网站来破坏用户的计算机并访问他们的数据。下图让您了解网站威胁。
因此,确保他或她的网站没有任何恶意代码和漏洞是网站管理员的工作。考虑到可能有数千个页面并且黑客有选择地在某些页面上插入代码,这并不是一件容易的事。既然这是你的名誉问题,你就必须这样做。幸运的是,有一些工具可以每天扫描您的网站,为您提供感染代码和漏洞点的报告(如登录屏幕、表单等)。
此外,当您即将访问受感染的恶意网站时,可以使用浏览器和浏览器插件触发警报。尽管您之前可能访问过该站点,并且您可能很难相信您信任的站点已被感染,但它可能在网站管理员不知情的情况下确实是恶意的——因为一个小时前,一些黑客在地点。
说到最坏的情况——或网站威胁的能力——损害有两个主要方面:
- 当访问者试图访问他们的网站时,他们的浏览器会触发警报,因此网站管理员可能会失去他们的消费者基础;如果谷歌(Google)等搜索引擎在抓取网站时发现任何类型的恶意代码,可能会将该网站列入黑名单。
- 在用户方面,用户的计算机以及他/她的数据受到损害,并可能导致身份盗用。
常见的网站威胁类型
最常见和最引人注目的是点击劫持(clickjacking)。在这种方法中,恶意代码的透明层位于按钮或视频上。当您单击该按钮时,它会将代码下载到您的计算机上。您可能已经在C 级(C-grade)网站上看到过类似的广告方法,主要与盗版和成人内容等有关。
网站重定向(Website redirection)漏洞使黑客能够利用重定向来谋取利益。他们可以拦截正在交换的数据或使用重定向将用户重定向到网络钓鱼站点。
在其他类型的网站中,威胁是使用Internet上容易获得的现成漏洞工具包(readymade exploit kits)进行的有针对性的攻击。这些工具包使黑客能够针对某些(类型)网站并向其添加恶意链接。另一种方法是向网站发送带有恶意链接的电子邮件,绕过毫无戒心的网站管理员,使其成为恶意网站。
最近对流行网站的攻击表明,即使是最大的网站也容易受到攻击。曾经丢失凭据的人不太可能再次返回该站点。
想象一下(Imagine),您的企业或电子商务网站被列入黑名单,而在搜索引擎再次将它们列入白名单之前,您将在数周内处于黑暗之中。虽然将网站从黑名单中删除的过程很艰难,但如果几个星期都没有出现在公众视野中,您的企业还能生存吗?
阅读(Read):如何从您的网站中删除 Coinhive 加密挖掘脚本。
如何保证网站安全
- 最新软件(Up-to-date software):保持您的网站服务器软件完全更新和修补
- SSL 证书:(SSL Certificates:)提供安全证书的公司在颁发信任证书之前会检查您的网站。“https”旁边地址栏上的绿色部分为网站用户提供了一些保证。
- 加密:(Encryption:)对用户在您的网站上所做的任何事情使用安全连接,尤其是在涉及交易时。
- 升级到 EV SSL: (Upgrade to EV SSL: )在客户可能输入数据的网站的任何部分执行此操作
- 每日恶意软件扫描:(Daily Malware Scan:)您可以使用扫描网站页面是否存在恶意软件的产品,而不会减少其加载时间。这样,您可以在用户受到影响之前删除恶意代码(如果它存在的话)。
- 每周漏洞评估:(Weekly Assessment of Vulnerabilities:) 检查(Check)可能的漏洞点并在那里实施额外的安全措施。
以上只是保护您的网站的一些提示。它简要解释了对网站的威胁及其功能。
现在阅读(Now read):如何保护 WordPress 网站(How to secure a WordPress site)。
今天晚些时候,我们将阅读有关路过式下载的(Drive-by downloads)信息 ,并在几天后阅读有关如何确保WordPress网站安全的信息。
How to keep websites secure: Threats and Dealing with Vulnerabilities
Visiting a malicious website can be one of the worst things that can happen to peoplе browsing the Internet, especially the ones interested in shopping online. Webmasterѕ nеed to know threats for and of wеbsites, and their devastating capabilities – losing consumer base being the first. If you run а website or blog, you need to know abоut the possiblе website threats. This article tаlks of the threats and their outcomes, some methods used by hackers to malign yоur website, and then discuss ways on how to keep websites secure.
Website Threats and Their Effects or Capabilities

It is a profitable business for hackers to steal people’s data and use it for personal gains. The gains can be monetary or abstract. While hacking, phishing, and social engineering are common methods, hackers also use other people’s websites to compromise users’ computers and access their data. The following image gives you an idea of website threats.
It is, therefore, a webmaster’s job to make sure his or her website is free of any malicious code and vulnerability. That is not an easy job considering that there might be thousands of pages and the hacker selectively inserts the code on some pages. Since it is a matter of your reputation, you have to do it. Fortunately, there are some tools available that can scan your websites daily to present you with a report of infectious code and vulnerability points (like login screens, forms, etc.).
In addition, browsers and browser plugins are available that trigger an alarm when you are about to visit a malicious, infected website. Though you might have visited that site before, and though it might be hard for you to believe that a site you trust is infected, it may really be malicious without the webmaster knowing it – because an hour earlier, some hacker added some code to the site.
Speaking of worst-case scenarios – or capabilities of website threats – there are two major sides of damage:
- Webmasters may lose their consumer base as visitors’ browser triggers an alarm when they attempt to visit their site; Google etc. search engines may blacklist the website if they find any type of malicious code while crawling the website.
- On the user side, the user’s computer and hence his/her data is compromised and can result in identity theft.
Common Types of Website Threats
The most common and noticed is clickjacking. In this method, a transparent layer of malicious code sits on a button or video. When you click on the button, it downloads the code to your computer. You might have seen similar methods for advertising on C-grade websites, mostly related to piracy and adult content, etc.
Website redirection vulnerabilities enable hackers to use the redirections for their gains. They can either intercept data being exchanged or use the redirection to redirect users to a phishing site.
Among other types of websites, threats are targeted attacks using readymade exploit kits available easily on the Internet. These kits enable the hackers to target certain (types of) websites and add malicious links to them. Another method is to send emails to the website with malicious links that bypass the unsuspecting webmaster to make it a malicious website.
The recent attacks on popular websites indicate that even the biggest websites are vulnerable. People who once lose their credentials are not likely to return to the site again.
Imagine your business or e-commerce website getting blacklisted and you are left in dark for weeks until the search engines whitelist them again. While the process to get a website removed from blacklists is tough, can your business survive if it is not on the public view for weeks?
Read: How to remove Coinhive crypto-mining script from your website.
How to keep websites secure
- Up-to-date software: Keep your website server software fully updated and patched
- SSL Certificates: The companies offering safety certificates check your website before issuing the certificate of trust. The green part on the address bar next to “https” provides some assurance to the users of the website.
- Encryption: Use a secure connection for anything users do on your website, especially if involved in transactions.
- Upgrade to EV SSL: Do this in any part of the website where the customer may enter data
- Daily Malware Scan: You can use products that scans your website pages for malware without reducing their load time. This way, you can remove the malicious code – in case it is there – before users are affected.
- Weekly Assessment of Vulnerabilities: Check for possible points of vulnerabilities and implement additional security there.
The above are just a few tips for securing your website. It explains threats to websites and their capabilities in brief.
Now read: How to secure a WordPress site.
Later today, we will read about Drive-by downloads and in a few days about how to keep a WordPress website secure.

