Tor是代表洋葱路由器(The Onion Router)的首字母缩写词。虽然名字暗示它是一个路由器,但它实际上是一个浏览器。Tor是(Tor)互联网(Internet)上代表匿名和隐私的浏览器。这篇关于 Tor 的评论讨论(Tor)了Tor的工作原理以及在您浏览Internet时它如何提供匿名性。
Tor 浏览器评论
Tor 与其他浏览器
虽然Microsoft Edge、Mozilla Firefox和Google Chrome提供了可以匿名浏览的功能(InPrivate和InCognito模式),但当中介位于网络流量的来源和目的地之间时,它们仍然落后。当您浏览网页、发送电子邮件或下载音频/视频或任何内容时,数据以数据包的形式发送。
每个数据包都有一个标头,用于说明数据包的来源和目的地。即使您使用的是加密连接,数据包标头也容易受到攻击。位于源和目标之间的任何人都可以读取数据包标头以了解您和您的浏览习惯。窥探的人包括您的ISP(ISPs)、广告代理商,有时甚至是政府机构。因此,您的浏览和您在Internet上看到的内容会受到其他人收集的关于您的信息的影响。
为什么需要 Tor
Tor的开发完全专注于用户的隐私。人们使用Tor发送机密电子邮件。Tor的高级安全性使黑客无法知道电子邮件的来源,从而知道发件人的位置。以下是Tor的一些用途,它们清楚地表明谁都需要地球上最安全的浏览器:
- 您可以匿名发送数据。
- 您可以在网上冲浪而不会留下任何痕迹,因为一旦数据从一个中继转发到另一个中继,痕迹就会被删除。我稍后会谈到接力 - 在下一节中。
- 您可以查看在您所在国家/地区受到审查的网站——因为ISP(ISPs)不会知道您要访问的内容。
- 您可以托管难以审查的网站,因为没有人知道谁在托管该网站。
Tor有很多用途——尤其是在用户隐私一直受到不同广告机构、社交网络和政府机构窥探的世界中。此外,您的ISP(ISPs)会在您实际连接到网站之前拦截您的连接请求。使用Tor,您不会为此类机构留下任何数据。
Tor 中继网络——Tor(Tor Relay Network – How Tor Works)的工作原理
Tor Network在一个由自愿参与该项目的人组成的中继网络上工作。与其他浏览器具有固定路由器接收数据包以将其转发到目的地不同,Tor浏览器使用许多中继。为了更清楚,这里是过程:
- 当您在Tor地址栏中输入URL时,会使用(URL)Tor网络中的中继计算机形成随机路由。(a random route is formed)
- 网络中的每台中继计算机都充当路由器。它接收数据包,在删除有关前一个路由器的信息后,将其转发给网络中的下一个中继计算机。
- 一旦数据包离开中继计算机,有关数据包的任何信息都会从中继计算机中删除。
- 大约每十分钟左右,就会设置一个新的中继,以进一步保护您的隐私。
下图显示了 Tor 的工作原理:
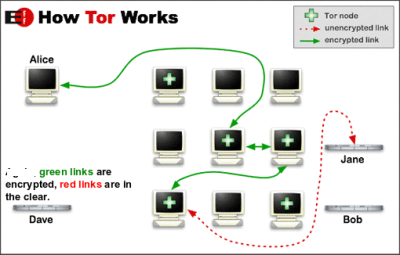
目标很明确——创建一个中继迷宫,使有关原始来源的所有信息都丢失在网络中。这使得目标网站上的脚本无法跟踪谁发送了请求/数据以及从何处发送。
什么是 Tor 捆绑包
当您下载Tor捆绑包时,您将获得三个基本程序:
- Vidalia 图形界面
- Tor 浏览器
- Tor 按钮
当你第一次下载Tor包时,你需要解压文件。您不需要任何类型的安装。这意味着您可以在USB(USB)驱动器上携带提取的文件,以便与运行任何类型操作系统的任何计算机一起使用。
阅读(Read):适用于 Windows PC 的最佳隐私浏览器(Best Privacy browsers for Windows PC)。
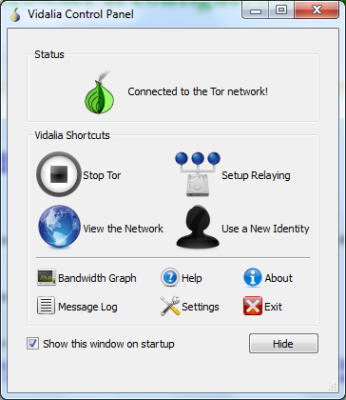
解压Tor Browser包后,您会找到一个可执行文件,上面写着“ Start Tor Browser.Exe ”。当您双击此文件时,它会启动Vidalia图形界面。除了在创建Tor中继网络后启动(Tor)Tor,图形界面还允许您:
- 更改Tor(Tor)浏览器的默认设置
- 查看Tor(Tor)网络中充当中继的计算机
- 查看带宽
- 启动(Start)和停止Tor浏览器(连接和断开Tor连接)
- 查看帮助文件和关于
设置中继后,您将获得Tor浏览器,如上一节中的第一张图片所示。Tor按钮位于地址栏之前,它允许您允许/阻止 cookie 在您正在访问的网页上运行。您还可以使用Tor按钮更改您的偏好。如果您愿意,您可以使用Tor(Tor)按钮开始一个新会话(新的中继) 。
请注意,您需要使用Tor包下载所有组件。您不能也不应该尝试下载和使用单个组件,因为您的计算机可能会变得不稳定。
阅读(Read):适用于 Windows PC的免费代理软件列表。(free Proxy software)
如何使用 Tor 浏览器
与任何浏览器一样,您只需在地址栏中输入URL ,然后按 Enter 即可访问您想要的网站。(URL)地址栏旁边的栏是快速搜索栏。它允许您选择Google、Amazon、Bing、Twitter、Wikipedia等网站。选择您要搜索的网站后,输入搜索词并按Enter键。
您可以单击Tor按钮( (Tor)Tor浏览器左侧的洋葱图标)来设置Tor cookie 和其他首选项。
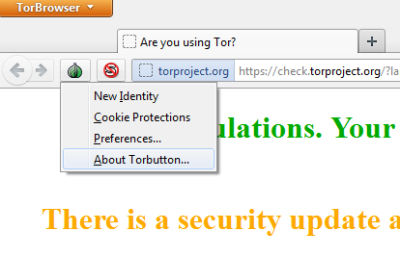
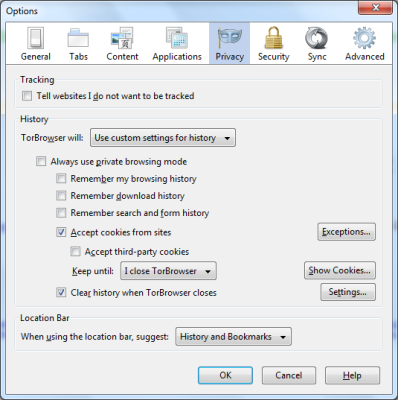
您可以通过选择Tor在InCognito浏览时的行为来进一步自定义您的隐私偏好。单击(Click)Tor 浏览器(Tor Browser)标题栏上的 Tor 浏览器按钮,然后在(Tor Browser)出现的子菜单中单击选项(Options),然后再次单击选项(Options)。在出现的对话框中,单击隐私(Privacy)选项卡。在此选项卡中,您可以设置是否要保存 cookie、下载历史记录、密码等。您还可以设置Tor模式,“网站不应尝试跟踪您”(websites should not try to track you)”(尽管这不是很可靠,因为广告机构,尤其是政府机构会继续跟踪您,而不管您的意愿如何)。
您可以使用 TOR 浏览器访问暗网(access the Dark Web using the TOR browser)。
Tor 浏览器的缺点
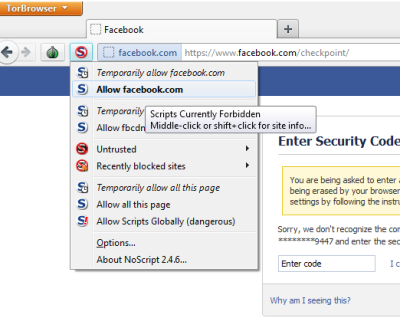
只有一个——浏览器有时会变慢。这是因为数据包通过Tor浏览器中的大量中继点进行路由。使用Tor(Tor)浏览时,我找不到任何其他负面影响。此外,在某些网站上,您可能必须允许脚本在地址栏前使用S图标。(S)Facebook和Twitter等网站大量使用脚本,因此如果在脚本被阻止的情况下运行 Tor,您可能会遇到问题。您可以使用S(S)按钮切换阻止/允许脚本。
Tor 浏览器下载
上面对Tor(Tor)的评论只涵盖了浏览器最重要的功能。您可以在Tor 网站(Tor website.)上下载或获取更多详细信息。如果您有什么要补充的,请在下方留言。
相关(Related):TOR 浏览器无法在 Windows 中打开或工作。
如何卸载 Tor 浏览器
您可能在控制面板(Control Panel)或设置(Settings)中看不到Tor浏览器条目。从您的系统中删除Tor 浏览器(Tor Browser)很简单:
- 使用开始搜索(Start Search)搜索Tor
- 找到您的Tor 浏览器(Tor Browser)文件夹或应用程序
- 删除(Delete)Tor 浏览器(Tor Browser)文件夹或应用程序
- 清空垃圾箱
- 就是这样!
Browzar是另一种注重隐私的Windows浏览器,您可能也会感兴趣。您可能还想查看此链接,其中讨论了适用于您的Windows计算机的(Windows)备用 Web 浏览器(alternate web browsers ),每个都提供一组不同的功能,或者这个关于便携式浏览器(portable browsers)的功能。您可能还想查看Epic Privacy Browser。
Tor Browser Review Download: Protect Your Privacy and Surf Web Safely
Tor is an acronym that stands for The Onion Router. While the name suggests it is a router, it is actually a browser. Tor is the browser that stands for anonymity and privacy on the Internet. This review of Tor talks about how Tor works and how it provides anonymity when you are browsing the Internet.
Tor Browser Review

Tor vs. Other Browsers
While Microsoft Edge, Mozilla Firefox and Google Chrome offer the feature where you can browse anonymously (InPrivate and InCognito modes), they still lag behind when intermediaries are sitting between the source and destination of web traffic. When you browse the web, send an email or download audio/video or anything, data is sent in the form of packets.
Each data packet has a header that tells about the source and destination of the data packet. Even if you are using an encrypted connection, the packet headers are vulnerable. Anyone sitting between the source and destination can read the packet header to know about you and your browsing habits. The people snooping include your ISPs, ad agencies and sometimes even the government agencies. As such, your browsing and what you see on the Internet is affected by the information others have gathered about you.
Why do you need Tor

Tor has been developed with a total concentration on the privacy of users. People use Tor to send confidential emails. The high-level security of Tor makes it impossible for hackers to know the origination of emails and thereby the location of the sender. Following are some uses of Tor that make it clear as to who all need the safest browser available on the planet:
- You can send data anonymously.
- You can surf the web without leaving any traces as the traces are deleted as soon as data is forwarded from one relay to another. I will come to relays in a moment – in the next section.
- You can view the websites that are otherwise censored in your country – because the ISPs won’t know what you are trying to access.
- You can host websites that will be difficult to censor because nobody knows who is hosting the website.
There are many uses of Tor – especially in a world where user privacy has been under the prying eyes of different ad agencies, social networks, and government agencies. Also, your ISPs intercept your connection requests before you actually connect to a website. Using Tor, you won’t leave any data for such agencies.
The Tor Relay Network – How Tor Works
Tor Network works on a network of relays formed by people who have volunteered for the project. Unlike other browsers that have fixed routers that receive data packets to forward them to their destinations, Tor browser uses a number of relays. To be clearer, here is the procedure:
- When you enter a URL in Tor address bar, a random route is formed using the relay computers in the Tor network.
- Each relay computer in the network works as a router. It receives data packets, forwards it to the next relay computer in the network after deleting information about the previous router.
- Once the data packet leaves the relay computer, any information about the data packet is removed from the relay computer.
- Approximately every ten minutes or so, a new relay is set up to further protect your privacy.
The below figure shows how Tor works:

The aim is clear – to create a maze of relays so that all the information about the original source is lost in the network. This makes it impossible for the scripts on the destination website to track who sent the request/data and from where.
What Is The Tor Bundle
When you download the Tor bundle, you get three essential programs:
- Vidalia graphical Interface
- Tor Browser
- Tor Button
When you first download the Tor bundle, you are required to extract the files. You do not need any kind of installations. This means you can carry the extracted files on a USB drive for use with any computer running any kind of operating system.
Read: Best Privacy browsers for Windows PC.
Once you have extracted the Tor Browser bundle, you find an executable that says “Start Tor Browser.Exe”. When you double-click this file, it launches Vidalia graphical interface. Other than launching Tor after creating a Tor relay network, the graphical interface lets you:
- Change the default settings for Tor browser
- View the computers acting as a relay in the Tor network
- Check out the bandwidth
- Start and stop Tor browser (connect and disconnect the Tor connection)
- Check out the help files and About

Once the relay is set up, you get the Tor browser as shown in the first image in the above section. The Tor button is located before the address bar and it allows you to allow/block cookies from running on the webpage you are visiting. You can also change your preferences using the Tor button. If you wish, you can start a new session (a new relay) using the Tor button.
Note that you need to download all the components using the Tor bundle. You cannot and should not try to download and use individual components as your computer may become unstable.
Read: List of free Proxy software for Windows PC.
How To Use Tor Browser
As with any browser, you just enter the URL in the address bar and hit enter to visit the website you want. The bar next to the address bar is a Quick search bar. It allows you to select websites such as Google, Amazon, Bing, Twitter, Wikipedia and more. After selecting the website that you wish to search, enter the search term and hit the Enter key.

You can click on the Tor button (onion icon towards the left of the Tor browser) to set up Tor cookies and other preferences.

You can further customize your preferences about privacy by selecting the behavior of Tor when it comes to InCognito browsing. Click on the Tor Browser button on the title bar of Tor Browser and in the resulting sub-menu, click on Options and again on Options. In the resulting dialog box, click the Privacy tab. In this tab, you can set whether you want to save cookies, download history, passwords, etc. You can also set Tor mode where “websites should not try to track you” (Though this is not very reliable as ad agencies and especially government agencies will continue to track you irrespective of your will).

You can access the Dark Web using the TOR browser.
Drawbacks Of Tor Browser
There is only one – the browser gets slower at times. This is because of the fact that the data packets are routed through a good number of relay points in the Tor browser. I could not find any other negatives while browsing with Tor. Also, on some sites, you may have to allow scripts using the S icon just before the address bar. Sites such as Facebook and Twitter make extensive use of scripts so you may face problems if you run Tor with scripts blocked. You can toggle blocking/allowing scripts using the S button.

Tor Browser Download
The above review of Tor covers just the most important features of the browser. You can download it or get more details on the Tor website. If you have anything to add, please leave a comment below.
Related: TOR browser not opening or working in Windows.
How to uninstall Tor browser
You may not see the Tor browser entry in the Control Panel or Settings. Removing Tor Browser from your system is simple:
- Search for Tor using the Start Search
- Locate your Tor Browser folder or application
- Delete the Tor Browser folder or application
- Empty your Trash
- That’s it!
Browzar, another privacy-minded browser for Windows may also interest you. You might want also to check out this link which talks of alternate web browsers for your Windows computer, each offering a different set of features or this one about portable browsers. You might want to also check out Epic Privacy Browser.








