语音助手可以帮助您处理日常琐事——无论是与客户预约播放音乐等等。与语音助手相关的市场充满了选择:Google、Siri、Alexa和Bixby。这些助手使用语音命令激活并完成工作。例如,您可以要求Alexa播放您选择的一些歌曲。这些设备可以被劫持并用来对付设备的所有者。今天,我们将了解使用超声波进行(Ultrasound)冲浪攻击(Surfing Attacks)及其带来的潜在问题。
什么是冲浪攻击?
智能设备配备了语音助手,例如Google Home Assistant、亚马逊的(Amazon)Alexa、苹果(Apple)的Siri,以及一些不太流行的语音助手。我在互联网(Internet)上的任何地方都找不到任何定义,所以我定义如下:
“Surfing attacks refer to hijacking of voice assistants using inaudible sounds such as Ultrasound waves, with an intention to access device owners’ data without the knowledge of owner”.
您可能已经知道,人耳只能感知一定频率范围(20 Hz 到 20KHz)之间的声音。如果有人发送超出人耳音频频谱的音频信号,则该人听不到它们。与超声波(Ultrasounds)相同。频率为超出了人耳的感知范围。
坏人开始使用超声波(Ultrasound)劫持智能手机和智能家居等使用语音命令的设备。这些以超声波(Ultrasound)频率发出的语音命令超出了人类的感知范围。这允许黑客在声音助手的帮助下获取他们想要的信息(存储在声控智能设备中)。为此,他们使用听不见的声音。
对于冲浪攻击,黑客无需在智能设备的视线范围内即可使用语音助手对其进行控制。例如,如果将 iPhone 放在桌子上,人们会认为语音可以在空中四处走动,因此如果语音命令通过空中传来,他们就会注意到黑客。但事实并非如此,因为声波只需要一个导体来传播。
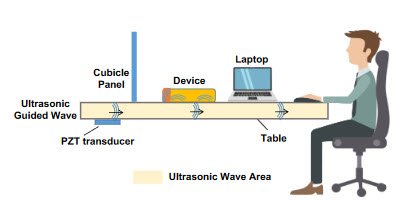
要知道(Know),只要可以振动,实体文物也可以帮助声音传播。木头制成的桌子仍然可以通过木头传递声波。这些是超声波(Ultrasound)被用作命令,在目标用户的智能手机或其他使用语音助手(如Google Home或Alexa )的智能设备上非法完成任务。
阅读(Read):什么是密码喷射攻击(Password Spray Attack)?
冲浪攻击如何运作?
使用可以穿过放置机器的表面的听不见的超声波。例如,如果手机在一张木桌上,他们只需要在桌子上安装一台可以发送超声波进行冲浪攻击的机器。
实际上,一个设备连接到受害者的桌子或他或她用来放置语音助手的任何表面上。该设备首先会调低智能助手的音量,以便受害者不会怀疑任何事情。命令来自连接到桌子的设备,对命令的响应也由同一台机器或其他可能位于远程位置的机器收集。
例如,可能会给出一个命令,“ Alexa,请阅读我刚刚收到的短信”。(SMS)房间里的人听不见这个命令。Alexa以极低的声音读出包含OTP(一次性密码)的SMS 。该响应再次被劫持设备捕获并发送到黑客想要的任何地方。
这种攻击称为冲浪攻击(Attacks)。我试图从文章中删除所有技术词汇,以便即使是非技术人员也能理解这个问题。对于高级阅读,这里是一篇研究论文的链接(a link to a research paper),可以更好地解释它。
阅读下一篇(Read next):什么是离地攻击(What are Living Off The Land attacks)?
Surfing Attacks: Hijack Siri, Alexa, Google, Bixby with Ultrasound Waves
Voice Assistants help you with daily chores – be it making an appointment with a client to playing music and more. The market related to voice assistantѕ is full of options: Google, Sirі, Alexa, and Bixby. Τhese assistantѕ are activated using voice commаnds аnd get things done. For еxample, you can ask Alexa to play some songs of your choicе. These devicеs can be hijacked and uѕed аgainst the owner of the device. Today, we will learn about Surfing Attacks using Ultrasound waves and the potential problems it poses.
What is a Surfing Attack?

Smart devices are equipped with voice assistants such as Google Home Assistant, Alexa from Amazon, Siri from Apple, and some not-so-popular voice assistants. I could not find any definition anywhere on the Internet, so I define it as follows:
“Surfing attacks refer to hijacking of voice assistants using inaudible sounds such as Ultrasound waves, with an intention to access device owners’ data without the knowledge of owner”.
You might already know that human ears can perceive sounds only between a range of frequencies (20 Hz to 20KHz. If anyone sends audio signals that fall outside the audio spectrum of human ears, the person cannot hear them. Same with Ultrasounds. The frequency is beyond the perception of human ears.
The bad guys started using Ultrasound waves to hijack devices such as smartphones and smart homes, that use voice commands. These voice commands at the frequency of Ultrasound waves are beyond human perception. That allows hackers to obtain the information they want (which is stored in the voice-activated smart devices), with the help of the sound assistants. They use inaudible sounds for this end.
For surfing attacks, hackers need not be in the line of sight of the smart device to control it using voice assistants. For example, if an iPhone is set on the table, people assume that voice can move around in the air so if voice command comes through the air, they can notice the hackers. But it is not so because voice waves need just a conductor to propagate.
Know that solid artifacts too can help voice propagate as long as they can vibrate. A table made up of wood can still pass voice waves through the wood. These are the Ultrasound waves being used as commands to get things done illegally on the target users’ smartphones or other smart devices that make use of voice assistants such as Google Home or Alexa.
Read: What is a Password Spray Attack?
How do Surfing Attacks work?
Using inaudible ultrasound waves that can travel through the surface where the machines are kept. For example, if the phone is on a wooden table, all they need to do is to attach a machine to the table that can send ultrasound waves for surfing attack.
Actually, a device is attached to the victim’s table or whatever surface he or she is using to rest the voice assistant on. This device first turns down the volume of smart assistants so that the victims don’t suspect anything. The command comes via the device attached to the table and the response to command too is collected by the same machine or something else that may be at a remote place.
For example, a command may be given saying, “Alexa, please read the SMS I just got”. This command is inaudible to people in the room. Alexa reads out the SMS containing OTP (one-time password) in an extremely low voice. This response is again captured by the hijacking device and sent to wherever the hackers want.
Such attacks are called Surfing Attacks. I have tried to remove all technical words from the article so that even a non-techie can understand this problem. For advanced reading, here is a link to a research paper that explains it better.
Read next: What are Living Off The Land attacks?

