加密劫持(Cryptojacking)或恶意加密挖掘(malicious cryptomining)是一种新技巧,用于在用户不知情的情况下在后台使用其CPU资源在用户计算机上挖掘加密货币。(Cryptocurrencies)通常,网络犯罪分子会将脚本加载到受害者的 Web 浏览器中,其中包含一个唯一的站点密钥,以强制用户丰富它们。
如果您正在为缓慢的 PC 或互联网连接而苦苦挣扎,请不要仅仅责怪供应商或服务提供商,因为您可能是黑客使用的一种称为浏览器Cryptojacking的新技巧的受害者。
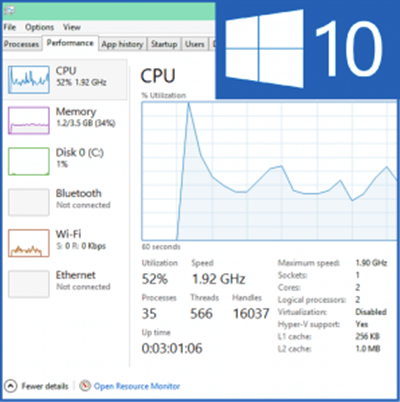
Cryptojacking的演变归因于过去几个月对加密货币(Cryptocurrencies)的兴趣飙升。看看过去几个月的比特币,它的价值已经上涨了 1000% 以上。(Bitcoin)这也引起了黑客的注意,因此催生了诸如Crytptojacking 之(Crytptojacking)类的危险做法。
什么是加密劫持
紧急情况(Emergence)
在我们了解Cryptojacking是什么之前,首先让我们了解Cryptomining。
Cryptomining或Cryptocurrency Mining是使用区块链技术产生加密货币的过程。Cryptomining还可以让新的加密货币硬币在市场上发布。挖矿(Mining)是由加密货币网络的某些对等方进行的,他们(个人或团体)竞争解决一个困难的数学问题,称为工作量证明
2017 年 9 月,Coinhive在市场上首次亮相,提供挖掘名为Monero ( XMR ) 的加密货币。Coinhive基本上提供了一段用JavaScript编写的代码,网站所有者可以简单地将其嵌入到他们的网站上。Coinhive为网站引入了一种新的商业模式,声称网站所有者可以从他们的网站上删除广告,然后加载Coinhive。
当用户访问嵌入了Coinhive的网站时, (Coinhive)Coinhive通过使用用户系统资源代表网站所有者启动加密挖掘过程(这就是 PC 经常变慢的原因)。网站的访问者代表进行密集计算工作以解决数学问题的节点组。但是,在解决挑战时,他们并没有收到奖励,而是网站所有者收到了奖励。因此(Hence),网站所有者据说仍然可以获利并支持他们的业务,而不会用广告打扰他们的访问者。
尽管Coinhive本来是合法的,但它的概念导致了类似软件的出现,现在网络犯罪分子将其用于Cryptomining 滥用(Cryptomining abuse )或Cryptojacking。
简而言之,Cryptojacking 是在未经用户同意的情况下劫持浏览器以挖掘加密货币的技术。通过恶意软件提供加密货币矿工是众所周知的事实,但在访问网页时挖掘加密货币是新事物,并导致攻击者滥用个人利益。(In short, Cryptojacking is the technique of hijacking browsers for mining cryptocurrency, without user consent. Delivering cryptocurrency miners through malware is a known fact, but mining cryptocurrency when accessing a webpage is new and has led to the attackers abusing for personal gains.)
Cryptojacking 不是传统的恶意软件
Cryptojacking 不会像传统的恶意软件或勒索(ransomware)软件行为那样损害您的 PC。它也不会在硬盘驱动器上存储或锁定任何内容。因此(Hence),它本身并不是恶意软件,但它肯定可以使用恶意软件引入您的系统。
Cryptojacking类似于恶意软件,在未经您许可的情况下使用您的 PC 资源。它可能会导致 PC 和浏览器工作极其缓慢、耗尽电池并提高电费,而您甚至没有意识到这一点。
加密劫持的后果
Cryptojacking会影响Windows 操作系统(Windows OS)以及Mac OSX和Android。最近报道了许多Cryptojacking的案例。(Cryptojacking)一些常见的类型包括:
故意使用 Coinhive 的网站(Websites using Coinhive deliberately)
Pirates Bay是第一个故意使用Coinhive的主要玩家之一。问题是它是透明地完成的,没有经过参观者的同意。一旦发现了加密挖掘脚本,海盗湾(Pirate Bay)就发表了一份声明,提到它正在测试该解决方案作为替代收入来源。研究人员担心有许多这样的网站已经在未经访问者同意的情况下使用Coinhive 。
Coinhive 注入受感染的网站(Coinhive injected into compromised websites)
研究人员确定了受到感染的WordPress和Magento网站,其中注入了Coinhive或类似的基于 JavaScript 的矿工。
阅读(Read):如果 Coinhive 加密挖掘脚本感染您的网站该怎么办。
使用浏览器扩展进行加密劫持(Cryptojacking using browser extensions)
浏览器(In-browser)内加密劫持使用网页上的JavaScript来挖掘加密货币。(JavaScript)JavaScript几乎在您访问的每个网站上运行,因此无需安装负责浏览器内挖掘的JavaScript代码。(JavaScript)加载页面后,浏览器内的挖掘代码就会运行。
在某些情况下,嵌入Coinhive的网络浏览器扩展程序在后台运行加密软件,并在浏览器运行时挖掘“门罗币”——而不仅仅是在访问特定网站时。
使用恶意软件进行加密劫持(Cryptojacking with malware)
这是另一种滥用行为,其中Coinhive通过虚假的Java更新与恶意软件一起部署。
Android 设备中的加密劫持(Cryptojacking in Android devices)
已检测到针对俄罗斯用户的Coinhive的Android变体。这一趋势表明Cryptojacking也正在扩展到移动应用程序。
嵌入 Coinhive 的域名仿冒域名(Typosquatted domains embedding Coinhive)
有人注册了“twitter.com.com”域名并将Coinhive加载到其中。本质上,输入错误的 Twitter URL并登陆该网页的用户只要留在该网页上,就会为域名所有者挖掘门罗币。(Monero)
通过云服务进行加密劫持(Cryptojacking through cloud services)
网络犯罪分子正在劫持不安全的云(Cloud)平台并使用它们来挖掘加密货币。
微软已通知在野外发现了 Coinhive 的变体。这样的发展表明,Coinhive 的成功促使其他想加入这个市场的各方涌现出类似的软件。(Microsoft has notified of variations of Coinhive being spotted in the wild. Such a development indicates that Coinhive’s success has motivated the emergence of similar software by other parties that want to join this market.)
Minr – Coinhive(A Coinhive)替代品出现
由于自推出以来一直不受欢迎,合法用户对Coinhive(Coinhive)的使用总体上一直在下降。Coinhive也很容易追踪,这是另一个事实,它的潜在崇拜者没有在他们的网站上使用它。
因此,作为替代方案,Minr的团队开发了一种“混淆(obfuscation)”选项,这使得追踪矿工变得更加困难。这有利于工具的隐藏使用。此功能非常有效,甚至可以隐藏(hides the code)流行的反恶意软件工具Malwarebytes的代码。
如何防止加密劫持
加密货币和区块链技术正在占领世界。它正在对全球经济产生影响,并导致技术中断。每个人都开始关注这样一个利润丰厚的市场——这也包括网站黑客。随着回报的增加,我们应该预料到这些技术会被滥用。
如果您想远离 Cryptojacking 欺诈,在浏览时保持观察是您必须经常练习的事情。如果您发现您的 PC 上的内存使用量突然激增并且性能缓慢,那么您就是在一个受感染的网站上。最好的做法是通过退出网站来停止该过程,并且不再访问它。
您还应该安装一个好的安全软件(good security software)并保持更新,以及打开防火墙并且在浏览时不要点击可疑链接(not click on suspicious links while browsing)。
您可以使用Anti-WebMiner程序作为预防措施之一。
使用阻止网站使用您的 CPU 进行加密挖掘的浏览器扩展程序。如果您使用Chrome浏览器,请安装(Install)minerBlock 扩展程序。它是Chrome浏览器的一个有用扩展,可以阻止整个网络上的基于网络的加密货币矿工。除了CoinHive,它甚至会阻止Minr。
另一个必要的预防措施是更新您的Hosts 文件(Hosts file)以阻止 coinhive.com 和其他已知会启用未经授权的挖掘的域。请记住(Remember),随着越来越多的人使用加密货币, Cryptojacking仍在增长,因此您的黑名单必须定期更新。
防止 CoinHive(Prevent CoinHive)感染您的网站
- 不要在您的网站/论坛上使用任何NULL模板或插件。(NULL)
- 将您的CMS更新到最新版本。
- 定期更新您的托管软件(PHP、数据库(Database)等)。
- (Secure your website)使用Sucuri(Sucuri)、Cloudflare、Wordfence等网络安全提供商保护您的网站。
- 采取基本的预防措施来保护您的博客(precautions to secure your blog)。
Stay alert, stay safe!
Cryptojacking the new browser mining threat you need to know about
Cryptojacking or malicious cryptomining is a new trick used to mine Cryptocurrencies on a user’s computer using their CPU resources in the background without their knowledge. Typically, the cybercriminal loads a script into the victim’s web browser which contains a unique site key to force the user to enrich them.
If you are struggling with a slow PC or internet connection, do not just blame the vendor or service provider yet because you may be a victim of a new trick used by the hackers called as browser Cryptojacking.

The evolution of Cryptojacking is attributed to the soaring interest in Cryptocurrencies for the past few months. Look at Bitcoin for the past few months or so, and its value has gone up by more than 1,000%. This has attracted attention from hackers as well and so has given birth to dangerous practices such as Crytptojacking.
What is Cryptojacking
Emergence
Before we understand what Cryptojacking is, first let us know about Cryptomining.
Cryptomining or Cryptocurrency Mining is the process by which a cryptocurrency comes into existence, using the blockchain technology. Cryptomining also lets new cryptocurrency coins get released on the market. Mining is carried out by certain peers of the cryptocurrency network who compete (individually or in groups) in solving a difficult mathematical problem, called proof-of-work
In September 2017, Coinhive debuted in the market, offering to mine the cryptocurrency called Monero (XMR). Coinhive basically offers a piece of code written in JavaScript which website owners can simply embed it on their website. Coinhive introduced a new business model for website claiming that website owners can remove ads from their websites, and load Coinhive instead.
When users access a website with Coinhive embedded, Coinhive initiates the process of crypto mining on behalf of the website owner by using user system resources (that is why PC’s often become slow). The visitors to the website represent the group of nodes doing the intensive computational work to solve the mathematical problem. However, instead of them receiving the reward when solving the challenge, the website owner receives it. Hence, website owners can supposedly still make a profit and support their businesses, without supposedly bothering their visitors with advertisements.
Although Coinhive was meant to be legitimate, its concept led to the emergence of similar software, which is now used by cyber criminals for Cryptomining abuse or Cryptojacking.
In short, Cryptojacking is the technique of hijacking browsers for mining cryptocurrency, without user consent. Delivering cryptocurrency miners through malware is a known fact, but mining cryptocurrency when accessing a webpage is new and has led to the attackers abusing for personal gains.
Cryptojacking is not a traditional malware
Cryptojacking does not harm your PC like traditional malware or ransomware act. Neither does it store or lock down anything on the hard drive. Hence, it in itself is not a malware as such, but it can certainly be introduced into your system using malware.
Cryptojacking, similar to malware, uses your PC resources without your permission. It can cause the PC and browsers to work extremely sluggish, drain the battery and raise the electricity bills without you even realizing the same.
Consequences of Cryptojacking
Cryptojacking can affect Windows OS as well as Mac OSX & Android. There have been numerous cases of Cryptojacking reported recently. Some of the common types include the following:
Websites using Coinhive deliberately
Pirates Bay was one of the first major player guilty of using Coinhive deliberately. The issue was that it was done transparently, without the visitors’ consent. Once the crypto mining script was discovered, Pirate Bay issued a statement mentioning that it was testing this solution as an alternative revenue source. Researchers fear that there are many such websites which are already using Coinhive without visitor’s consent.
Coinhive injected into compromised websites
Researchers identified compromised WordPress and Magento websites that had Coinhive, or a similar JavaScript-based miner injected into them.
Read: What to do if Coinhive crypto-mining script infects your website.
Cryptojacking using browser extensions
In-browser cryptojacking uses JavaScript on a web page to mine for cryptocurrencies. JavaScript runs on just about every website you visit, so the JavaScript code responsible for in-browser mining does not need to be installed. As soon as you load the page, and the in-browser mining code just runs.
There are cases of web browser extensions embedding Coinhive where cryptomining software run in the background and mined “Monero” while the browser was running -and not only when visiting a specific website.
Cryptojacking with malware
This is another type of abuse where Coinhive is being deployed alongside malware through a fake Java update.
Cryptojacking in Android devices
An Android variant of Coinhive has been detected targeting Russian users. This trend suggests that Cryptojacking is expanding to mobile applications as well.
Typosquatted domains embedding Coinhive
Someone registered the “twitter.com.com” domain and loaded Coinhive to it. Essentially, users who mistyped Twitter’s URL and landed on that webpage would mine Monero for the domain owner for as long as they remained at the webpage.
Cryptojacking through cloud services
Cybercriminals are hijacking unsecured Cloud platforms and using them to mine cryptocurrency.
Microsoft has notified of variations of Coinhive being spotted in the wild. Such a development indicates that Coinhive’s success has motivated the emergence of similar software by other parties that want to join this market.
Minr – A Coinhive alternative emerges
The use of Coinhive by legitimate users has in general been on decline owing to the unpopularity that it has been receiving since its launch. Coinhive is also easily traceable which is another fact that its prospective admirers are not using it on their website.

So, as an alternative, the team of Minr, has developed an option of “obfuscation”, which makes it much more difficult to track the miner. This facilitates the hidden use of the tool. This feature is so effective that it hides the code even for the popular anti-malware tool Malwarebytes.
How to stay protected from Cryptojacking
Cryptocurrencies & Blockchain technology is taking over the world. It is creating an impact on the global economy and causing technology disruptions as well. Everyone has started focusing on such a lucrative market – and this includes website hackers too. As returns increase, we should expect that such technologies will be misused.
Being observant while browsing is something that you have to practice regularly if you want to stay away from Cryptojacking frauds. You are on a compromised website if you see a sudden spike in memory usage and sluggish performance on your PC. The best action here is to stop the process by exiting the website, and not visit it again.
You should also install a good security software and keep it updated, as well as turn on firewalls and not click on suspicious links while browsing.
You can use Anti-WebMiner programs as one of the precautions.
Use a browser extension that blocks websites from using your CPU for crypto mining. If you use Chrome browser, then Install minerBlock extension. It is a useful extension for Chrome browser to block web-based cryptocurrency miners all over the web. Apart from CoinHive it even blocks Minr.
Another necessary precaution is to update your Hosts file to block coinhive.com and other domains that are known to enable unauthorized mining. Remember, Cryptojacking is still growing with more and more people drawing towards Cryptocurrencies, so your blocklists will have to be regularly updated.
Prevent CoinHive from infecting your website
- Don’t use any NULL templates or plugins on your website/forum.
- Keep your CMS updated to the latest version.
- Update your hosting software regularly (PHP, Database, etc.).
- Secure your website with web security providers like Sucuri, Cloudflare, Wordfence, etc.
- Take basic precautions to secure your blog.
Stay alert, stay safe!


