近年来,一种新的安全概念(security concept)成为头条新闻——两步验证或两因素身份验证(verification or two-factor authentication)(2FA)。这一切都始于谷歌(Google)为其用户启用它,从那时起,许多公司效仿他们的榜样,包括微软(Microsoft)、苹果(Apple)和Facebook。甚至游戏公司也加入了这一趋势。如果您想了解什么是双因素身份验证(two-factor authentication)、它是如何工作的、为什么要启用它以及在哪里阅读本文:
什么是两步验证或验证(authentication or verification)?
双因素身份验证是一个安全过程(security process),涉及两个阶段,用于验证尝试访问任何类型服务(电子邮件、社交网络、银行等)的个人或实体的身份。(person or entity)这个概念也被称为两步验证,它需要这三个认证因素中的两个或多个:知识因素(knowledge factor)、拥有因素(possession factor)和固有因素(inherence factor)。
传统的身份验证只涉及前面提到的三个因素中的一个或两个。例如,如果您想使用电子邮件等服务,传统的身份验证需要知道用户名和密码。知识(Knowledge)可以通过多种方式被窃取,人们可以找到您的用户名和密码(username and password),然后使用该信息冒充您,或窃取可用于伤害您的有价值信息。
在现实世界中,传统的验证可能涉及知识因素(knowledge factor)和占有因素(possession factor)。例如,当您去ATM 取款(ATM)时,您使用借记卡或信用卡(debit or credit card)(拥有因素(possession factor))和PIN(知识因素(knowledge factor))。但是,您的信用卡上的(credit card)PIN或信息都可能以各种方式被盗,未经授权的人可以使用您的钱进行在线交易。这就是开发3D Secure概念的原因,旨在为在线信用卡和借记卡交易提供额外的安全层。(security layer)
在数字世界中使用两步验证时,会添加第三个因素:拥有因素(possession factor)- 通常是您的智能手机或手机。该设备用于验证您身份的第二阶段。例如,当您登录您的电子邮件帐户(email account)时,您首先需要提供您的用户名和密码(username and password)。然后,系统会要求您提供一个基于时间的密码,该密码会在几秒钟后过期。此密码可以发送到您的电子邮件帐户(email account)、您的智能手机,也可以由Google Authenticator或Microsoft Authenticator等验证器应用程序(authenticator app)生成。

一些公司和服务还提供物理验证设备,这些设备会不断生成您需要用来完成验证过程(verification process)的代码。例如,很多银行都提供了两步验证的实体设备,这样你就可以在线访问你的银行账户(bank account online)。此外,PayPal为包括(PayPal)美国(USA)在内的许多国家/地区执行此操作。
双重身份验证如何工作(authentication work)?
两步认证的实现有很多,这里就不一一赘述了,因为这篇文章会很长。
最流行的实现是Google基于TOTP-Time-based One-time Password 算法(TOTP - Time-based One-time Password Algorithm)的方法。为您的帐户启用两步验证后,一个特殊的服务器会每隔几秒钟生成一个新密码/代码。与您共享密码的设备需要与服务器同步,以便您在第二步验证步骤(authentication step)中输入的密码与服务器上的密码匹配。如果共享密码的设备不同步,您将无法完成身份验证。
该算法是网上最流行的算法。许多公司都在使用它,包括Google、Microsoft、Apple、Facebook、Evernote、Dropbox、WordPress、MailChimp和LastPass。
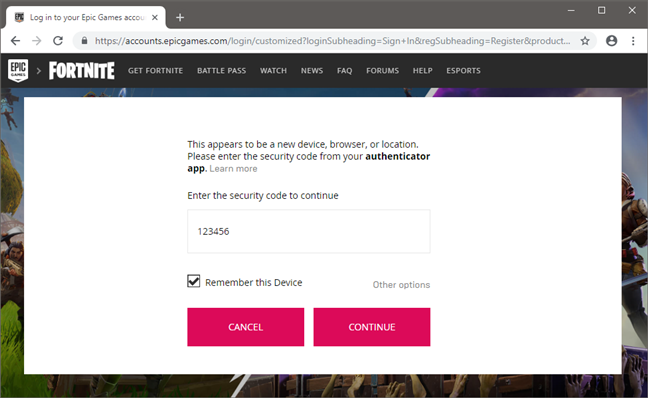
为了让您更容易理解双因素身份验证的工作原理,我们以Fortnite 为例(Fortnite),这是一款很多人都玩的流行在线游戏。(online game)一旦您为您的Epic (Epic) Games帐户(Fortnite的创建者)配置了双重身份验证 (2FA),仅提供您的用户名和密码(username and password)来登录是不够的。您还必须提供辅助密码才能能够要做到这一点。
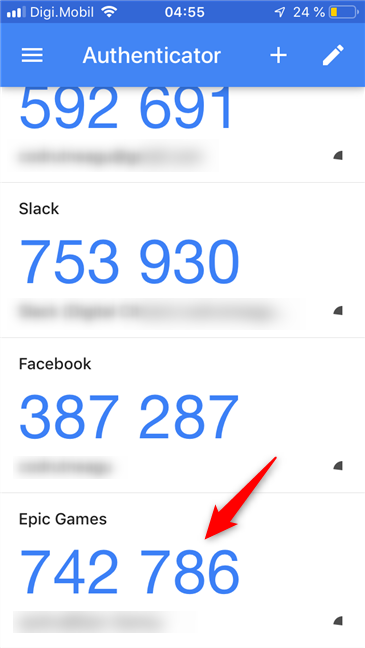
附加密码是临时的,只有您知道。其他人应该找不到它,因为您只能从身份验证器应用程序(authenticator app)(例如Google Authenticator )或从(Google Authenticator)Epic Games收到的电子邮件中获取此代码。两因素身份验证代码每隔几秒钟就会更改一次,因此几乎不可能猜到它们。
如果您提供正确的双因素身份验证代码(authentication code),您将登录到您的Fortnite 帐户(Fortnite account)。在接下来的 30 天内,您不必在已登录的设备上提供 2FA 代码。但是,在 30 天结束时,或者如果您尝试从新设备登录,则必须提供再次有效的 2FA 密码。
银行业(banking sector)的双因素认证
另一种流行的方法是银行和信用卡(credit card)提供商使用的方法。它被命名为3-D Secure,用于批准在线进行的金融交易。这种两步验证方法涉及三个实体:支付款项的商家或银行的域、正在使用的发卡银行的域以及支持 3-D 协议的基础设施。

该协议仅使用安全的SSL连接进行在线交易,并且要批准交易,您需要一个特殊密码以及您的姓名和信用卡详细信息(name and credit card details)。此密码可能是临时的和基于时间的,也可能是永久的并由您(用户)设置。另一个重要方面是,该密码不是由商家或支付款项的银行存储的。只有为 3-D 协议提供基础设施的服务器才知道密码。因此,如果商家被黑客入侵,黑客将无法获取您的 3-D Secure 密码(Secure password)。
为什么需要双重身份验证?
您应该使用两步验证的主要原因是为了保护自己。通过使用这一额外的保护层,您可以让不受欢迎的人更难在线访问您的身份(identity online)并窃取个人或财务数据。
使用 3-D Secure 进行金融交易时,黑客更难窃取您的资金。他们很容易复制您的卡详细信息,但他们很难获得您的 3-D安全密码(Secure password)。
什么时候应该使用双重身份验证?
添加辅助身份验证步骤(authentication step)对每个人来说都很烦人,但对我们的帐户和数据保密是必要的。我们强烈建议您至少为以下类型的服务启用和使用两步验证:
- 电子邮件(E-mail)- 您的收件箱(Inbox)存储了您所有在线帐户中最多的个人数据。人们可以监视您的电子邮件历史记录,了解您的银行帐户和 PayPal 帐户(banking and PayPal accounts)的用户名,了解有关您的工作、人际关系和许多其他重要细节的更多信息。保护您的收件箱是您应该做的第一件事。
- 网上银行和金融交易(Online banking & financial transactions)- 如果您进行网上银行,如果您从亚马逊(Amazon)、eBay 或其他网上商店购买东西,您必须确保您的信用卡或借记卡安全。向您的银行询问他们提供的 3-D 安全和两步验证选项,启用它们并使用它们。
- 存储您的密码(Storing your passwords)- 许多有安全意识的人使用LastPass、Roboform 或 KeePass(Roboform or KeePass)等服务。保护它们至关重要。如果您的帐户密码(account password)被盗,未经授权的人可以访问您的所有密码,并对您造成很大伤害。
- 社交网络——我们都在(Social Networking)Facebook、Twitter或Instagram等社交网络上存储大量个人数据。如果其他人可以访问您的数据,他们可能会发现许多您宁愿保密的事情。例如,如果您有一个嫉妒的伴侣,他们可能已经知道您的Facebook 密码(Facebook password)并密切关注您的行为。保护自己并启用双重身份验证。

如何为您最重要的帐户启用双重身份验证
通常,启用双重身份验证意味着您必须登录您的在线帐户并(account and head)前往您的密码和安全设置(password and security settings)。然后,如果您可以为您的帐户使用双重身份验证,您应该找到一个选项。如果 2FA 可用,启用它意味着按照几个步骤选择您喜欢的方法(通常是通过电子邮件或(email or authenticator app)智能手机上的身份验证器应用程序进行身份验证)。为了帮助您启用和使用双重身份验证,我们发布了一些指南,涵盖了一些最流行的在线服务:
- 如何为您的Google 帐户(Google account)启用或禁用两步验证
- (Approve)使用Android批准或拒绝对您的Microsoft 帐户的登录请求(Microsoft account)
- 如何在iPhone 或 iPad(iPhone or iPad)上为您的Apple ID激活两步验证
- (Set)使用Google Authenticator为您的(Google Authenticator)Microsoft 帐户(Microsoft account)设置两步验证
- 如何启用和使用Fortnite的 2FA(双因素身份验证)
- 为您的暴雪帐户(Blizzard account)启用和使用双重身份验证 (2FA)
此外,如果您正在寻找一种在您自己的公司中实施双重身份验证的简单方法,这里有一篇关于此类优秀解决方案的好处的简短文章:您可以使用ESET 安全身份验证(ESET Secure Authentication)做的 7 件事。
您是否对所有帐户启用了双重身份验证?
我们希望您发现本指南对您有用。如果您对了解两步验证的工作原理有任何疑问或问题,请随时在下方发表评论。
Simple questions: What is two-factor authentication or two-step verification?
In recent years a new security concept hаs made the headlines - two-step verification or two-factor authentication (2FA). It all started with Google enabling it for its users, and sіnсe then, many companies followed their example, including Microsoft, Apple, and Facebook. Even gaming companies joined this trend. If you would like to undеrstand what two-faсtor authentіcation is, how it works, why you should enable it and where read this article:
What is two-step authentication or verification?
Two-factor authentication is a security process that involves two stages for verifying the identity of a person or entity that is trying to access a service of any kind (e-mail, social networking, banking, etc.). This concept is also named two-step verification, and it requires two or more of these three authentication factors: a knowledge factor, a possession factor, and an inherence factor.
Traditional authentication involves only one or two of the three factors mentioned earlier. For example, if you want to use a service like e-mail, traditional authentication involves knowing a username and its password. Knowledge can be stolen in a variety of ways and people can find out both your username and password, and then use that information to pose as you, or steal valuable information that can be used to harm you.

In the real world, traditional verification may involve the knowledge factor and the possession factor. For example, when you go to an ATM to get cash, you use your debit or credit card (possession factor) and the PIN (a knowledge factor). However, both the PIN or the information on your credit card can be stolen in various ways, and unauthorized parties can make online transactions using your money. That's why the 3D Secure concept has been developed to provide an additional security layer for online credit and debit card transactions.
When using two-step verification in the digital world, a third factor is added: the possession factor - usually your smartphone or mobile phone. This device is used for the second stage of verifying your identity. For example, when you sign-in to your email account, you first provide your username and password. Then, you are asked to provide a time-based password that expires in a couple of seconds. This password can be sent to your email account, to your smartphone, or it can be generated by an authenticator app such as Google Authenticator or Microsoft Authenticator.

Some companies and services also provide physical authentication devices that continuously generate the codes you need to use to finalize the verification process. For example, many banks provide physical devices for two-step verification, so that you can access your bank account online. Also, PayPal does this for a number of countries, including the USA.
How does two-factor authentication work?
The implementations for two-step authentication are many, and we do not go into details about all of them because this article would become very long.
The most popular implementation is Google's approach based on the TOTP - Time-based One-time Password Algorithm. When two-step verification is enabled for your account, a special server generates a new password/code once every couple of seconds. The device sharing the password with you needs to be synchronized with the server so that the code you enter during the second authentication step matches the one on the server. If the device sharing the password is out of sync, you cannot complete the verification of your identity.
This algorithm is the most popular one found online. Many companies use it, including Google, Microsoft, Apple, Facebook, Evernote, Dropbox, WordPress, MailChimp, and LastPass.
To make it easier for you to understand how two-factor authentication works, let's take for example Fortnite, a popular online game that many people play. Once you have configured two-factor authentication (2FA) for your Epic Games account (the creators of Fortnite), it is no longer enough just to provide your username and password to log in. You also have to provide a secondary passcode to be able to do that.

The additional passcode is temporary, and you are the only one who knows it. No one else should be able to find it, as you can only get this code from an authenticator app (such as Google Authenticator) or from an email message you receive from Epic Games. The two-factor authentication codes change every couple of seconds, so they should be almost impossible to guess.

If you provide the correct two-factor authentication code, you are signed into your Fortnite account. For the next 30 days, you do not have to provide 2FA codes on the device on which you already signed in. However, at the end of the 30 days or if you try to log in from a new device, you have to provide a valid 2FA passcode again.
Two-factor authentication in the banking sector
Another popular approach is the one used by banks and credit card providers. It is named 3-D Secure, and it is used for approving financial transactions that are made online. This method of two-step verification involves three entities: the domain of the merchant or the bank to which the money is being paid, the domain of the bank which issues the card being used and the infrastructure that supports the 3-D protocol.

This protocol uses only secure SSL connections for making online transactions and, for a transaction to be approved, you need a special password, alongside your name and credit card details. This password may be temporary and time-based, or it may be permanent and set by you, the user. Another important aspect is that this password is not stored by the merchant or the bank to which money is being paid. The password is known only by the servers providing the infrastructure for the 3-D protocol. Therefore, if the merchant is hacked, hackers cannot get your 3-D Secure password.
Why do you need two-factor authentication?
The main reason why you should use two-step verification is to protect yourself. By using this additional layer of protection, you make it harder for unwanted parties to access your identity online and steal personal or financial data.
When using 3-D Secure for financial transactions, you make it harder for hackers to steal your money. It is easy for them to copy your card details but they are going to have a hard time getting your 3-D Secure password.
When should you use two-factor authentication?
Adding a secondary authentication step is annoying for everyone but necessary to keep our accounts and data private. We highly recommend that you enable and use two-step verification at least for the following types of services:
- E-mail - your Inbox stores the biggest amount of personal data out of all your online accounts. People can spy on your email history, learn the username for your banking and PayPal accounts, learn more about your work, your relationships, and many other important details. Securing your inbox is the first thing you should do.
- Online banking & financial transactions - if you do online banking, if you purchase stuff from Amazon, eBay or other online shops, you must secure your credit or debit card. Ask your bank about 3-D secure and the two-step verification options they offer, enable them and use them.
- Storing your passwords - many security conscious people use services like LastPass, Roboform or KeePass. Securing them is crucial. If your account password is stolen, unauthorized parties have access to all your passwords and can do a lot of harm to you.
- Social Networking - we all store lots of personal data on social networks such as Facebook, Twitter, or Instagram. If others get access to your data, they might find many things you would rather keep private. For example, if you have a jealous partner, they may already know your Facebook password and keep an eye on what you do. Protect yourself and enable two-factor authentication.

How to enable two-factor authentication for your most important accounts
In general, enabling two-factor authentication means that you have to log in to your online account and head to your password and security settings. Then, if you can use two-factor authentication for your account, you should find an option for it. If 2FA is available, enabling it means following a couple of steps in which you choose the method you prefer (usually, that is authentication via email or authenticator app on a smartphone). To help you out in enabling and using two-factor authentication, we have published a few guides that cover some of the most popular online services:
Also, if you are looking for an easy way to implement two-factor authentication in your own company, here is a short article about the benefits of an excellent solution of this kind: 7 things you can do with ESET Secure Authentication.
Have you enabled two-factor authentication on all your accounts?
We hope that you found this guide useful. If you have any questions or issues with understanding how two-step verification works, do not hesitate to leave a comment below.






