Vice News、CNET、The Verge、Neowin等主要网站的读者自 2015 年以来一直面临安全风险,因为他们从PowerLinks 广告(PowerLinks advertising) 平台投放的广告使用(platform use)了过期的SSL证书。以下是正在发生的事情,您在阅读包含PowerLinks广告的出版物时会接触到的内容,以及您可以采取哪些措施来确保安全:
通过 PowerLink 投放的广告的SSL证书已于 2015 年10 月到期(October 2015)
在我的个人计算机上阅读多个网站时,我注意到我的安全解决方案(security solution)抱怨我的浏览器试图通过使用不受信任的证书加密的通道进行通信。我的防病毒软件无法保证建立加密连接的域的真实性,这给我带来了安全风险(security risk)。最初,我忽略了这个警告,只是继续阅读。但是,在几个大网站上看到之后,我开始关注并更详细地研究了一些东西。
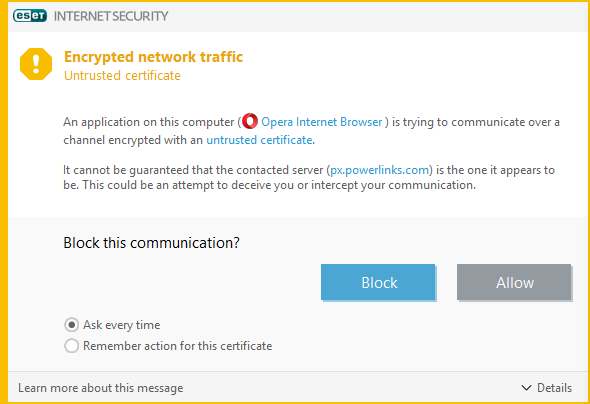
我惊讶地发现这个警告出现在大型在线出版物上,而且它总是由 pw.powerlinks.com 提供的广告引起的。他们都有一个在 2015 年10 月(October 2015)过期的SSL 证书(SSL certificate),如下所示。

为了仔细检查这是否属实而不是虚惊一场,我尝试了另一种一流的安全产品(security product),结果是一样的。我浏览了更多网站,并注意到出版界(publishing world)的一些大人物正在重复同样的问题。
PowerLinks 为(PowerLinks offer)出版商提供什么?
根据他们的官方网站,PowerLinks拥有全面的广告解决方案和服务组合。他们为其客户组合中的网站提供广告服务器、 (Ad Server)Ad Exchange 平台(Ad Exchange platform)、原生广告(文本内、视频内、图像内、信息流和展示广告)等。
为什么这是一个问题?当网站展示带有过期SSL(SSL)证书的广告时我们面临的问题
如果您没有安装好的安全解决方案(security solution),您可能永远不会注意到这个问题。但是,如果您使用实时扫描您的HTTP 流量的优秀防病毒软件,那么您将会对使用(HTTP traffic)PowerLinks提供的广告服务的几家大型媒体出版物上的安全提示(security prompt)感到恼火。
撇开烦人的因素(annoyance factor)不谈,我们向Catalin Patrascu(罗马尼亚国家计算机安全事件响应小组的(National Computer Security Incident Response Team)信息安全和监控部门负责(Information Security and Monitoring Department)人)询问了这些广告所涉及的安全风险,他陈述了以下内容:
“理论上,即使 SSL 证书过期,也可以进行验证。对于习惯了这种错误并且每次收到错误时不检查 SSL 证书的用户,存在被重定向到恶意的风险页面并成为中间人攻击的目标”("Theoretically, the verification of SSL certificates can be done even though they are expired. For the users that get used to this error and don't check the SSL certificate each time they get the error, there is the risk of getting redirected to malicious pages and becoming the target of man-in-the-middle attacks")。
另一个需要考虑的重要事情是,这些广告还会跟踪用户数据和用户行为。这些数据是通过不安全的渠道(insecure channel)发送的,容易被不受欢迎的人拦截。
受此问题影响的网站包括:The Verge、Vice News、CNET等
我们不知道受此问题影响的网站的确切列表。我们假设所有PowerLinks客户都处于危险之中。到目前为止,我们已经在 The Verge、Vice News、CNET、Neowin 等(Neowin and others)大型媒体出版物上发现了这个问题。这些网站每个月都有数以千万计的读者,自 2015 年10 月(October 2015)以来,他们每天投放PowerLinks广告,其受众的安全都面临风险。
这个问题是由PowerLink的疏忽造成的
我们在这里处理的是明显的疏忽。这些SSL证书在几天或一个月内没有过期。它们自 2015 年以来已过期,PowerLinks 没有尽其所能为在线出版物和这些出版物的读者提供安全的广告解决方案。他们的技术团队没有注意到他们的广告平台(advertising platform)使用了已经过期多年的SSL证书,并且没有采取任何措施来解决这个问题,同时让数百万读者处于危险之中。(SSL)恶意软件(Did malware)创建者是否利用了这个问题?这是一个很好的问题,我们不确定 PowerLinks 是否可以回答。最后,他们甚至没有处理到期日期等基本问题。
哪些安全(Which security)产品帮助我发现了这个问题?
我第一次发现这个问题是在我浏览前面提到的一些网站并使用ESET Smart Security作为我的防病毒软件时。
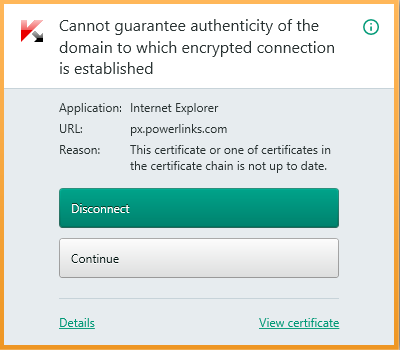
Kaspersky Total Security也确认了此问题,如下所示。
我们很高兴这些产品在通知我们并保护我们免受PowerLinks广告平台的安全漏洞的影响方面发挥了作用,并帮助我们解开了正在发生的事情。这进一步证明了您应该始终安装第三方防病毒产品(antivirus product)并停止不安全地浏览网页。如果您想了解更多有关在不受保护的情况下浏览网页所涉及的风险的信息,请阅读我们运行的这个实验:如何在免费浏览网页时感染您的Windows PC 。
我们做了什么来帮助受此安全问题(security issue)影响的读者和出版物?
首先(First),我们写这篇文章是为了告诉大家这件事。我们还要求PowerLinks发表官方评论。但是,他们的官方联系电子邮件不起作用,我们收到的只是一个 Delivery Status Notification Failure,您可以在下面看到。

我们使用他们的社交媒体渠道将这篇文章发送给我们发现的所有受影响的媒体出版物,以及PowerLinks 。我们希望他们不会忽视我们的信息,并会采取措施解决这个问题。
UPDATE (03/21/2017):我们终于设法将我们的消息发送到PowerLinks,我们收到了来自业务开发副总裁(VP Business Development)Branden Smythe的以下答复:
“我收到您联系 PowerLinks 的通知。我们将尽快解决您发布的问题。”("I received notice that you reached out to PowerLinks. We will address the concerns you posted shortly.")
今天,我们再次检查了发现我们描述的问题并且现在一切正常的网站。PowerLinks似乎已经采取了必要的措施来保护他们在所有网站上的广告投放(ad delivery),这很棒。希望(Hopefully)他们能从这个问题中吸取教训,并更好地处理安全基础知识,例如SSL证书的到期日期(expiration date)。
您可以做些什么来保护自己免受不安全的PowerLinks广告的侵害?
如果您的安全解决方案(security solution)抱怨PowerLinks广告使用的(PowerLinks)SSL证书过期,您应该阻止它们。如果您没有扫描实时HTTP 流量(HTTP traffic)的防病毒软件,那么您应该使用隐私浏览模式运行这些网站,这些模式也可以阻止不安全的广告或找到其他阻止它们的方法。我们不喜欢在我们提到的网站上屏蔽广告,因为广告是使这些出版物能够为每个人提供优质内容的原因。希望这个问题能很快得到解决,我们都可以安全地享受我们最喜欢的出版物,而不会阻止他们的广告并让他们从工作中获得收入。
PowerLinks ads put millions of readers at risk, from major publications like The Verge, Vice News and more
Readers of major websites like Vice News, CNET, The Verge, Neowin and more, hаve been exposed to security rіsks sincе 2015 bеcause the ads they run from the PowerLinks advertising plаtform use expired SSL certifiсates. Here's what is going on, what you are exposing yourself tо whеn reading publications that include PowerLinks аds and what you can do to stay safe:
The ads served through PowerLinks have SSL certificates that expired in October 2015
While reading several websites on my personal computer, I have noticed that my security solution was complaining that my browser is trying to communicate over a channel that is encrypted with an untrusted certificate. My antivirus could not guarantee the authenticity of the domain to which the encrypted connection was established, and this posed a security risk for me. Initially, I ignored this warning and just kept reading. However, after seeing it on several big websites, I started paying attention and studied things in more detail.
I was surprised to find that this warning is shown on large online publications and it is always caused by ads served from pw.powerlinks.com. All of them have an SSL certificate that expired in October 2015, as you can see below.

To double check whether this was true and not just a false alarm, I tried another top-notch security product, and the results were the same. I navigated more websites and noticed that the same problem was repeating for some big names in the publishing world.
What does PowerLinks offer publishers?
According to their official website, PowerLinks has a comprehensive portfolio of advertising solutions and services. They offer an Ad Server for the sites in their portfolio of clients, an Ad Exchange platform, native ads (in-text, in-video, in-image, in-feed and in-display ads) and more.
Why is this an issue? The problems we're exposed to when websites display ads with expired SSL certificates
If you don't have a good security solution installed, you might never notice this issue. However, if you use a good antivirus which scans your HTTP traffic in real-time, then you will be annoyed by a security prompt on several large media publications that use advertising services provided by PowerLinks.
Leaving the annoyance factor aside, we asked Catalin Patrascu (head of the Information Security and Monitoring Department at the Romanian National Computer Security Incident Response Team) about the security risks involved with these ads, and he stated the following:
"Theoretically, the verification of SSL certificates can be done even though they are expired. For the users that get used to this error and don't check the SSL certificate each time they get the error, there is the risk of getting redirected to malicious pages and becoming the target of man-in-the-middle attacks".
Another important thing to consider is that these ads also track user data and user behavior. This data is sent through an insecure channel, leaving it vulnerable to interception by unwanted parties.
The websites that are affected by this issue include: The Verge, Vice News, CNET, and more
We don't know the exact list of websites that are impacted by this issue. We assume that all PowerLinks customers are at risk. So far, we have identified this problem on large media publications like The Verge, Vice News, CNET, Neowin and others. These websites have dozens of millions of readers each month, and the security of their audience has been put at risk every day they have run PowerLinks ads, since October 2015.
This problem is caused by plain negligence on PowerLink's part
What we are dealing here is plain negligence. These SSL certificates have not been expired for a couple of days or a month. They have been expired since 2015 and PowerLinks are not doing their job of offering secure advertising solutions to both online publications and readers of those publications. Their technical team did not notice that their advertising platform uses SSL certificates that have been expired for years and did nothing to solve this problem while putting millions of readers at risk. Did malware creators exploit this issue? That's a good question, and we're not sure whether PowerLinks can answer. In the end, they did not even take care of basics like expiration dates.
Which security products helped me discover this issue?
The first time I found this problem was when I was navigating some of the websites I mentioned earlier and used ESET Smart Security as my antivirus.

This issue was also confirmed by Kaspersky Total Security, as you can see below.

We're pleased that these products did their job in informing us and keeping us safe from the security vulnerabilities of the PowerLinks ads platform and helps us unravel what is going on. It's further proof that you should always install a third-party antivirus product and stop browsing the web, unsecured. If you are curious to learn more about the risks involved with browsing the web unprotected, read this experiment that we have run: How to infect your Windows PC while browsing the web for free stuff.
What did we do to help readers and publications that are affected by this security issue?
First of all, we wrote this article to inform everyone on this matter. We also asked PowerLinks for an official comment. However, their official contact e-mail doesn't work, and all we received is a Delivery Status Notification Failure, which you can see below.

We sent this article to all the media publications that we've found that are affected, as well as to PowerLinks, using their social media channels. We hope that they won't ignore our message and will take measures to fix this problem.
UPDATE (03/21/2017): We finally managed to get our message sent to PowerLinks, and we received the following answer from Branden Smythe, VP Business Development:
"I received notice that you reached out to PowerLinks. We will address the concerns you posted shortly."
Today, we checked again the websites where we have found the issues that we described and things are now working well. It seems that PowerLinks has performed the necessary steps to secure their ad delivery on all websites, which is great. Hopefully, they will learn from this problem and take better care of security basics like the expiration date of SSL certificates.
What can you do to protect yourself from insecure PowerLinks ads?
If your security solution is complaining about the expired SSL certificates used by PowerLinks ads, you should block them. If you don't have an antivirus which scans your real-time HTTP traffic, then you should run these websites using private browsing modes that also block the insecure ads or find some other way of blocking them. We are not fans of blocking ads on the websites that we have mentioned because advertising is what keeps these publications able to provide everyone with great content. Hopefully, this problem will be solved soon, and we can all enjoy our favorite publications, safely, without blocking their advertising and allowing them to earn revenue from their work.




