无论您是对网络安全职业感兴趣,还是只想了解更多关于Linux和计算机的信息,Kali都是一个很好的 Linux 发行版(good Linux distribution to use)。它是免费的,来自著名的网络安全公司Offensive Security,并且预装了人们需要的大多数安全研究工具。让我们学习如何安装和使用Kali Linux。
Kali Linux安装在Raspberry Pi等(Raspberry Pi)ARM设备、 VMWare和VirtualBox等虚拟机主机上,或者直接安装在笔记本电脑或 PC 等硬件上。Kali Linux在VMWare、VirtualBox、Raspberry Pi上的安装大致相同,或者作为笔记本电脑或台式计算机的主要操作系统。

在笔记本电脑或台式计算机上安装 Kali Linux(Installing Kali Linux On a Laptop or Desktop Computer)
ISO是一个文件,它是您可以在安装 DVD 上找到的数据的副本,包括(DVD)文件系统。所以,如果你有一个磁盘来安装Kali Linux并制作了一个可以用来安装它的副本,那么该副本将是一个ISO文件。

有几种方法可以从ISO安装(ISO)Kali。您可以制作可启动的 USB 驱动器(bootable USB drive)或DVD,然后将其安装在笔记本电脑或 PC 等硬件上。使用我们的文章如何免费创建、装载和刻录 ISO 映像文件(How to Create, Mount, and Burn ISO Image Files for Free)来提供帮助。或者您可以使用它来创建虚拟机 (VM)。
- 转到 Offensive Security 的Kali Linux 下载(Kali Linux Downloads)页面并为您选择正确的下载。我们将使用Kali Linux 64-Bit Installer。您可以直接下载或使用他们的Torrent链接。

使用ISO创建可启动的USB驱动器或DVD,或将其用作 VM 的安装盘。
- 启动要安装Kali Linux的设备。如果您制作了可启动的 USB 或DVD,请确保先插入。片刻之后,就会出现Kali Linux 安装程序(Kali Linux Installer)。对于初学者,请选择图形安装(Graphical install)。

可能会出现看起来像失败的错误消息。让它继续。

- 选择一种语言,然后继续(Continue)。

- 选择您的位置。如果您要使用的时区不在该位置,请不要选择它。加拿大人(Canadians)只使用美国(United) 是很常见的(States)。如果他们这样做,他们会错过一些时区,比如大西洋(Atlantic)( UTC -4 )。选择继续(Continue)。

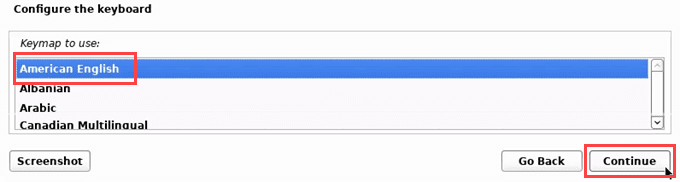
- 选择与键盘一起使用的键盘映射,有很多可供选择。
选择继续(Continue ),它将检测并安装ISO。一旦找到它,它将执行一些自动程序。

- 要将Kali Linux机器放到网络上,请设置一个 hostname(set a hostname)。

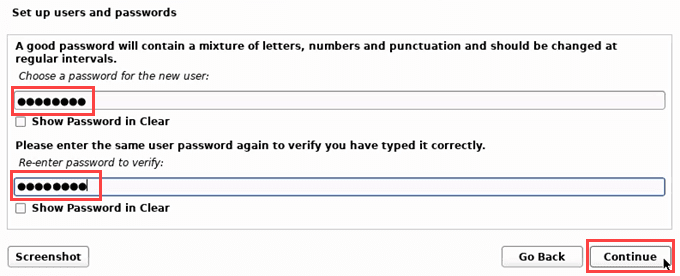
- 现在设置用户和密码。这些不是针对管理用户的,而是针对普通用户的。

- 创建一个安全密码(secure password)。
- 选择您的时区。

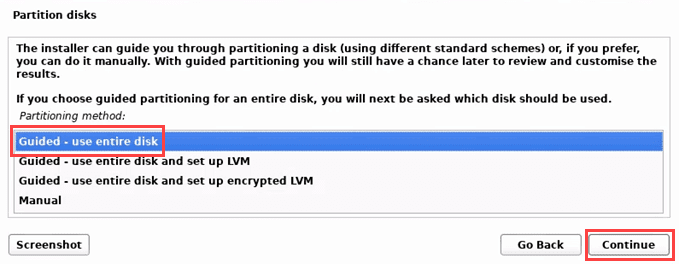
- 现在Linux Kali安装将带您完成磁盘分区(disk partitioning)。如果您仅将设备用于Kali,请选择Guided – use the entire disk。
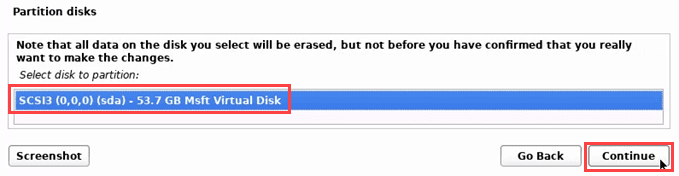
- 磁盘可以分区,但基本安装不需要这样做。
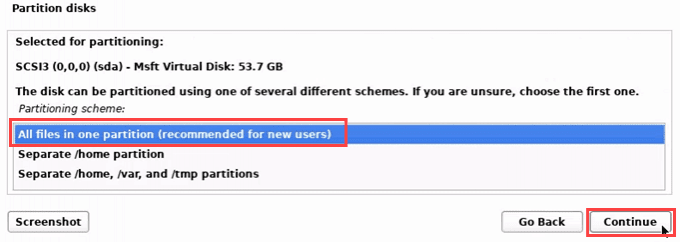
- 选择分区类型。对于新用户,选择All files in one partition。
- 因为它没有被分区,所以选择完成分区(Finish partitioning)并将更改写入磁盘。

- 它会询问您是否确定。选择是(Yes )并继续(Continue)。

Linux Kali 现在将安装。

- 现在您可以选择要安装的工具。如果您不确定,请使用默认值。这将为您提供出色的学习工具选择。

工具将安装。

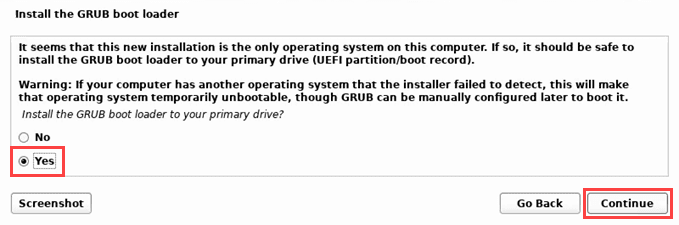
- 现在Kali Linux会询问是否安装GRUB引导程序。是(Yes )是默认值。
它将询问在什么设备上安装GRUB。只有一个,所以选择它。


- 安装完成后,请确保弹出USB驱动器或DVD。选择继续(Continue )以完成它。

安装将开始完成。是的,安装中的措辞很奇怪。

黑色背景上的一些白色文本可能会滚动。等一下(Just)。
Kali Linux将启动并提供启动到Kali GNU/Linux或Kali GNU/LinuxAdvanced options for Kali GNU/Linux。第一个是默认设置,如果您不选择,将自动选择。

- 登录到 Kali Linux 并享受。

将 Kali Linux 安装为虚拟机(Installing Kali Linux As a Virtual Machine)
自定义 VM 映像是创建Kali Linux虚拟机的最快方法。Offensive Security提供在VirtualBox或VMWare上使用的图像。我们将使用VirtualBox进行此安装,并假设您已经安装了 VirtualBox(VirtualBox already installed)。
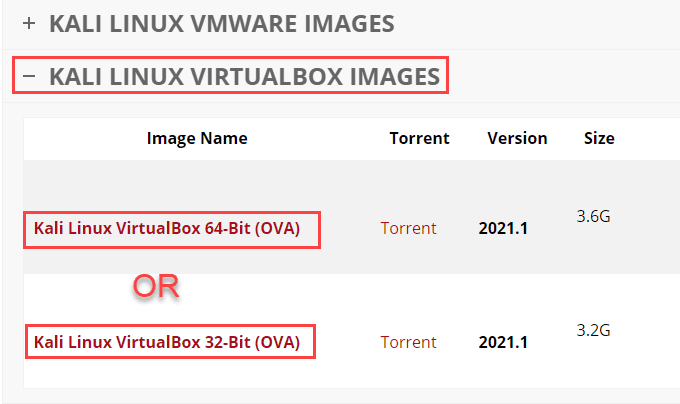
通过从 Offensive Security 的站点下载 Kali Linux 映像(downloading the Kali Linux image)进行准备。请注意,所有图像都已设置用户名kali和密码kali。首次登录时更改它。
- 在Oracle VM VirtualBox Manager中,选择Import。

- Source默认为Local File System。保持原状。选择黄色文件夹图标以导航到下载的图像。然后选择下一步(Next)。

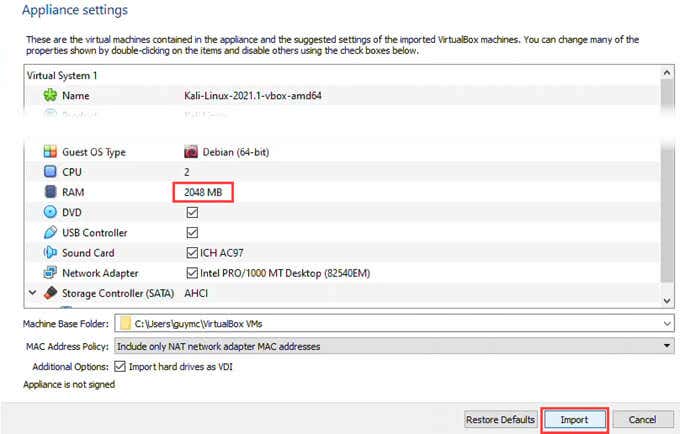
- 默认的设备设置(Appliance settings)几乎不会起作用。如果可以的话,增加RAM和CPU 。选择导入(Import)。
- 阅读软件许可协议(Software License Agreement)后,选择同意(Agree)继续。

将开始导入。这可以在 10 分钟内完成。

- 导入完成后,您将在VirtualBox中看到(VirtualBox)Kali Linux安装。选择它,然后选择开始(Start)。

- 它将简要地为您提供启动到Kali Gnu/Linux或Kali Gnu/LinuxAdvanced options for Kali Gnu/Linux。它将默认为第一个选项。
(Log)使用用户名kali和密码kali登录到新的Kali Linux VM。请记住(Remember)立即更改它们。

你可以用 Kali Linux 做什么?(What Can You Do With Kali Linux?)
Kali本质上是一个普通的Linux,已经安装了一堆安全工具并可以使用。您还可以轻松地向 Kali 添加更多工具。(add more tools to Kali)有些是免费的且功能齐全,而有些则需要付费升级才能获得所有功能。所有人都在安全研究中占有一席之地。在应用程序(Applications)菜单中,请注意工具是如何按功能分组的。

另外,请注意有一个指向 Offensive Security 培训的链接。这些是工具,而不是玩具,需要认真研究。让我们看一下Kali Linux(Kali Linux)中一些最流行的工具。
如果您想从事 IT 工作,请学习使用Wireshark。它是最著名的网络分析仪。使用 Wireshark(Use Wireshark)查看网络上发生的事情,并且知道Wireshark在简历上看起来不错。
您可以捕获数据包以分析内容并了解网络如何运行以及在其上传输的数据,例如用户名和密码。Wireshark有很棒的内置文档,而且Wireshark社区很大而且很有帮助。
顾名思义,Aircrack-ng可以收集飞来飞去的Wi-Fi数据并帮助破解正在传输的安全密钥。这可以帮助您在不进入建筑物的情况下进入网络。
它不是一个单一的工具,而是一个框架或平台,可以帮助您发现和验证漏洞。它可以发现设备、收集证据、获得访问权并控制系统。免费版本非常适合大多数笔测试初学者,但当你成为专业人士时,你会想要升级。笔(Pen)测试人员严重依赖Metasploit。

这个工具已经存在了很长时间,并且有充分的理由。它是测试 Web 应用程序安全性的首选工具。如果您开发 Web 应用程序,请学习Burp Suite并使用它来确保您的最终项目是无懈可击的。

破解密码是让我们大多数人进入Kali Linux之类的东西的原因。您可以使用开膛手(Ripper)约翰(John)来测试人们拥有的密码并让他们知道以制作更好的密码。
它还可用于恢复忘记的密码,例如 Excel(recover forgotten passwords for things like Excel)。它通过破译系统存储的散列密码来做到这一点。您可以看到这对计算机取证和安全专业人员有何价值。

你会用 Kali Linux 做什么?(What Will You Do With Kali Linux?)
无论是保护您的网络、渗透测试、白帽黑客、计算机取证,还是成为一名安全专家,Kali Linux都是终极的多功能工具。价格合适,您可以在几分钟内启动并运行。你会用Kali Linux做什么?
How to Install and Setup Kali Linux
Whether you’re interested in a сareer in cуbersecurіty, or јust want to learn more about Linux and computers, Kali is a good Linux distribution to use. It’s free, comes from a reputable cybersecurity company, Offensive Security, and is pre-loaded with most of the security research tools a person needs. Let’s learn how to install and use Kali Linux.
Kali Linux installs on ARM devices like Raspberry Pi, virtual machine hosts like VMWare and VirtualBox, or directly onto hardware like a laptop or PC. Installation is roughly the same for Kali Linux on VMWare, VirtualBox, Raspberry Pi, or as the main operating system of your laptop or desktop computer.

Installing Kali Linux On a Laptop or Desktop Computer
An ISO is a file that is a copy of the data you would find on an installation DVD, including the filesystem. So, if you had a disk to install Kali Linux and made a copy that you could use to install it, that copy would be an ISO file.

There are a few ways that you can install Kali from an ISO. You could make a bootable USB drive or DVD and then install it on hardware like a laptop or PC. Use our article How to Create, Mount, and Burn ISO Image Files for Free to help. Or you could use it to create a virtual machine (VM).
- Go to Offensive Security’s Kali Linux Downloads page and select the right download for you. We’ll be using the Kali Linux 64-Bit Installer. You can do a direct download or use their Torrent links.

Use the ISO to create a bootable USB drive or DVD or use it as the install disk for a VM.
- Start the device you’re installing Kali Linux on. If you made a bootable USB or DVD, make sure that’s inserted first. In a few moments, the Kali Linux Installer appears. For first timers, select Graphical install.

What looks like a failure error message may appear. Let it continue.

- Select a language, then Continue.

- Select your location. If the time zone you want to use isn’t in that location, don’t select it. It’s common for Canadians to just use the United States. If they do that, they’ll miss out on some time zones, like the Atlantic (UTC -4). Select Continue.

- Select a keymap to use with the keyboard, there are plenty to choose from.

Select Continue and it will detect and mount the ISO. Once it finds it, it will do some automatic procedures.

- To put the Kali Linux machine on the network, set a hostname.

- Now set up users and passwords. These are not for administrative users, but for normal users.

- Create a secure password.

- Choose your time zone.

- Now the Linux Kali installation will take you through disk partitioning. If you’re using the device only for Kali, choose Guided – use the entire disk.

- The disk can be partitioned, but a basic install doesn’t require that.

- Choose the partition type. For new users, choose All files in one partition.

- Since it’s not being partitioned, choose Finish partitioning and write changes to disk.

- It will ask if you’re sure. Select Yes and Continue.

Linux Kali will install now.

- Now you can choose what tools to install. If you’re not sure, go with the defaults. That will give you an excellent selection of tools to learn.

The tools will install.

- Now Kali Linux will ask to install the GRUB bootloader or not. Yes is the default.

It will ask what device to install GRUB on. There’s only one, so select that.



- Once the installation completes, make sure to eject the USB drive or DVD. Select Continue to finish it.

The installation will start finishing. Yes, the wording is strange in the install.

Some white text on a black background may scroll by. Just wait.

Kali Linux will boot and give the option to boot into Kali GNU/Linux or Advanced options for Kali GNU/Linux. The first is the default and will auto select if you don’t choose.

- Login to Kali Linux and enjoy.

Installing Kali Linux As a Virtual Machine
A custom VM image is the fastest way to create a Kali Linux virtual machine. Offensive Security provides images to use on VirtualBox or VMWare. We’ll be using VirtualBox for this installation and we’ll assume you have VirtualBox already installed.

Prepare by downloading the Kali Linux image from Offensive Security’s site. Note that all images have the username kali and the password kali already set. Change that when you log in for the first time.
- In Oracle VM VirtualBox Manager, select Import.

- Source defaults to Local File System. Leave it as it is. Select the yellow folder icon to navigate to the downloaded image. Then select Next.

- The default Appliance settings will work, barely. Increase the RAM and CPU if you can. Select Import.

- After you’ve read the Software License Agreement, select Agree to continue.

Importing will begin. This could finish in under 10 minutes.

- Once the import finishes, you’ll see the Kali Linux install listed in VirtualBox. Select it and then select Start.

- It will briefly give you the option to boot into Kali Gnu/Linux or Advanced options for Kali Gnu/Linux. It will default to the first option.

Log in to your new Kali Linux VM using the username kali and password kali. Remember to change them immediately.

What Can You Do With Kali Linux?
Kali is essentially ordinary Linux with a bunch of security tools already installed and ready to go. You can also add more tools to Kali easily. Some are free and fully featured, while some require a paid upgrade to get all the functions. All have their place in security research. In the Applications menu, notice how the tools are grouped by function.

Also, notice there is a link to Offensive Security’s training. These are tools, not toys and will require serious study. Let’s look at a few of the most popular tools in Kali Linux.
If you want to work in IT, learn to use Wireshark. It’s the best-known network analyzer. Use Wireshark to see what’s happening on a network, and knowing Wireshark looks good on a resume.

You can capture packets to analyze the contents and figure out how the network functions and the data traveling on it, like usernames and passwords. Wireshark has great built-in documentation and the Wireshark community is large and helpful.
As the name suggests, Aircrack-ng can gather Wi-Fi data that’s flying around and help crack the security keys being transmitted. This helps you get into a network without being in the building.

It’s not a single tool, but more a framework or platform to help you find and validate vulnerabilities. It can discover devices, collect evidence, gain access and take control of systems. The free version is great for most pen-testing beginners, but you’ll want to upgrade when you go pro. Pen testers rely heavily on Metasploit.

This tool has been around for a long time, and for good reason. It’s the go-to tool for testing web application security. If you develop web apps, learn Burp Suite and use it to make sure your end project is watertight.

Cracking passwords is what gets most of us into things like Kali Linux. You can use John the Ripper to test passwords that people have and let them know to make better passwords.
It can also be used to recover forgotten passwords for things like Excel. It does this by deciphering hashed passwords stored by your system. You can see how this is valuable to computer forensics and security professionals.

What Will You Do With Kali Linux?
Whether it’s for securing your network, penetration testing, white-hat hacking, computer forensics, or becoming a security professional, Kali Linux is the ultimate multi-tool. The price is right, and you can be up and running in minutes. What will you do with Kali Linux?













































