Windows内置了一个不错的小功能,可让您跟踪某人何时查看、编辑或删除指定文件夹内的内容。因此,如果您想知道谁在访问某个文件夹或文件(folder or file),那么这是内置方法,无需使用第三方软件。
此功能实际上是 称为组策略的( Group Policy)Windows 安全(Windows security)功能的一部分,大多数IT 专业人员(IT Professionals)通过服务器管理公司网络中的计算机,但它也可以在没有任何服务器的 PC 上本地使用。使用组策略的唯一缺点是它在较低版本的(Group Policy)Windows中不可用。对于Windows 7,您需要拥有Windows 7 Professional或更高版本。对于Windows 8,您需要 Pro 或Enterprise。
组策略(Group Policy)一词基本上是指一组可以通过图形用户界面(user interface)控制的注册表设置。您启用或禁用各种设置,然后这些编辑会在Windows 注册表(Windows registry)中更新。
在Windows XP中,要进入策略编辑器(policy editor),请单击开始(Start),然后单击运行(Run)。在文本框中,键入不带引号的“ gpedit.msc ”,如下所示:

在Windows 7中,您只需单击“开始”按钮并在“(Start button and type)开始”菜单(Start Menu)底部的搜索框中键入(search box)gpedit.msc。在Windows 8中,只需转到“开始”屏幕(Start Screen)并开始输入或将鼠标光标移动(mouse cursor)到屏幕的最上方或右下方以打开Charms栏并单击“搜索”(Search)。然后只需输入gpedit。现在您应该看到类似于下图的内容:
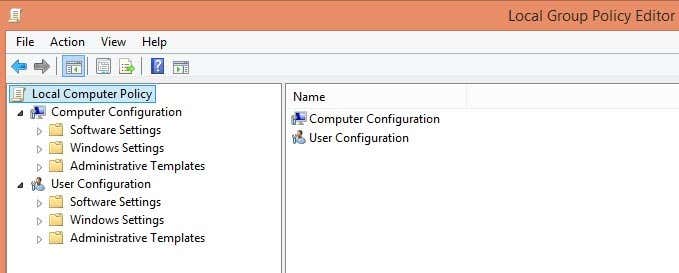
有两个主要类别的策略:用户(User)和计算机(Computer)。正如您可能已经猜到的那样,用户策略控制每个用户的设置,而计算机设置将是系统范围的设置,并将影响所有用户。在我们的例子中,我们希望我们的设置适用于所有用户,因此我们将展开“计算机配置(Computer Configuration)”部分。
继续扩展到Windows Settings -> Security Settings -> Local Policies -> Audit Policy。我不会在这里解释很多其他设置,因为这主要集中在审核文件夹上。现在,您将在右侧(hand side)看到一组策略及其当前设置。审核策略(Audit policy)控制操作系统(operating system)是否已配置并准备好跟踪更改。

现在通过双击它并选择Success和Failure来检查Audit Object Access的设置。单击确定(Click OK),现在我们完成了第一部分,告诉 Windows 我们希望它准备好监视更改。现在下一步是告诉它我们到底(EXACTLY)想要跟踪什么。您现在可以关闭组策略控制台(Group Policy console)。
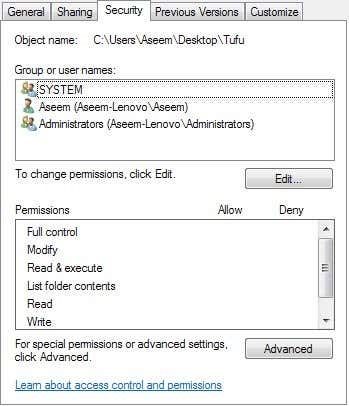
现在使用Windows 资源管理器(Windows Explorer)导航到您要监视的文件夹。在资源管理器(Explorer)中,右键单击文件夹并单击(folder and click) 属性(Properties)。单击安全选项卡( Security Tab),您会看到与此类似的内容:
现在单击“高级(Advanced)”按钮,然后单击“审核(Auditing)”选项卡。这是我们实际配置我们要为此文件夹监视的内容的地方。

继续并单击添加(Add)按钮。将出现一个对话框,要求您选择用户或组(User or Group)。在框中,输入单词“ (word “)users ”,然后单击Check Names。该框将自动更新为您计算机的本地用户组的名称,格式为COMPUTERNAME\Users。

单击“确定(Click OK)”,现在您将看到另一个名为“ Audit Entry for X ”的对话框。这是我们一直想做的真正的肉。您可以在此处选择要为此文件夹观看的内容。您可以单独选择要跟踪的活动类型,例如删除或创建新文件/文件夹等。为了使事情更容易,我建议选择Full Control,它将自动选择其下方的所有其他选项。这样做是为了成功(Success)和失败(Failure)。这样,无论对该文件夹或其中的文件做什么,您都会有记录。

现在单击 OK 并再次单击 OK 并再次单击 OK 以退出多个对话框(dialog box)集。现在您已经成功配置了对文件夹的审核!所以你可能会问,你如何看待这些事件?
为了查看事件,您需要转到控制面板并单击(Control Panel and click)管理工具(Administrative Tools)。然后打开事件查看器(Event Viewer)。单击“安全”部分,您将在(Security)右侧(hand side)看到大量事件列表:

如果您继续创建文件,或者只是打开文件夹并单击事件查看器(Event Viewer)中的Refresh 按钮(带有两个绿色箭头的按钮),您将在(Refresh button)File System类别中看到一堆事件。这些与您正在审核的文件夹/文件上的任何删除、创建、读取、写入操作有关。在Windows 7中,现在所有内容都显示在文件系统任务(File System task)类别下,因此为了查看发生了什么,您必须单击每个任务并滚动浏览它。
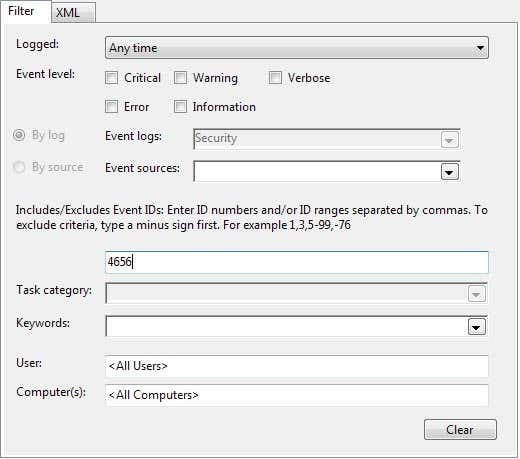
为了更容易查看这么多事件,您可以放置一个过滤器,只查看重要的东西。单击(Click)顶部的View菜单,然后单击(View)Filter。如果没有Filter选项,则右键单击左侧页面中的Security log并选择(Security log)Filter Current Log。在事件 ID 框中(Event ID box),键入数字4656。这是与执行文件系统 (File System )操作的特定用户相关的事件,它将为您提供相关信息,而无需查看数千个条目。
如果您想获得有关活动的更多信息,只需双击它即可查看。
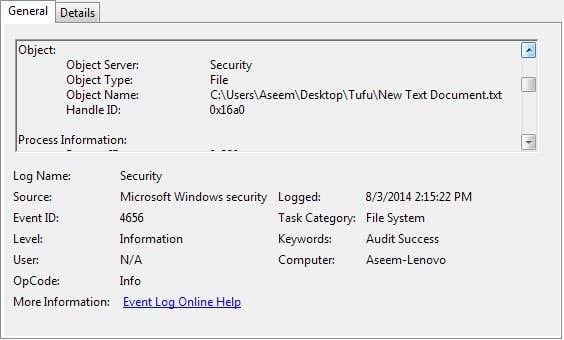
这是来自上面屏幕的信息:
请求了对象的句柄。(A handle to an object was requested.)
主题:(Subject:)
Security ID: Aseem-Lenovo\Aseem
帐户名称:Aseem( Account Name: Aseem)
帐户域:Aseem-Lenovo( Account Domain: Aseem-Lenovo)
登录 ID:0x175a1( Logon ID: 0x175a1)
对象:(Object:)
对象服务器:安全( Object Server: Security)
对象类型:文件( Object Type: File)
Object Name: C:\Users\Aseem\Desktop\Tufu\New Text Document.txt
句柄 ID:0x16a0( Handle ID: 0x16a0)
进程信息:(Process Information:)
进程 ID:0x820( Process ID: 0x820)
Process Name: C:\Windows\explorer.exe
访问请求信息:(Access Request Information:)
事务 ID:{00000000-0000-0000-0000-000000000000}( Transaction ID: {00000000-0000-0000-0000-000000000000})
访问:DELETE ( Accesses: DELETE)
SYNCHRONIZE
ReadAttributes
在上面的示例中,处理的文件是我桌面上Tufu 文件夹(Tufu folder)中的New Text Document.txt,我请求的访问是DELETE后跟SYNCHRONIZE。我在这里所做的是删除文件。这是另一个例子:
对象类型:文件( Object Type: File)
Object Name: C:\Users\Aseem\Desktop\Tufu\Address Labels.docx
句柄 ID:0x178( Handle ID: 0x178)
进程信息:(Process Information:)
进程 ID:0x1008( Process ID: 0x1008)
Process Name: C:\Program Files (x86)\Microsoft Office\Office14\WINWORD.EXE
访问请求信息:(Access Request Information:)
事务 ID:{00000000-0000-0000-0000-000000000000}( Transaction ID: {00000000-0000-0000-0000-000000000000})
访问:READ_CONTROL ( Accesses: READ_CONTROL)
SYNCHRONIZE
ReadData(或 ListDirectory)( ReadData (or ListDirectory))
WriteData(或 AddFile)( WriteData (or AddFile))
AppendData(或 AddSubdirectory 或 CreatePipeInstance)( AppendData (or AddSubdirectory or CreatePipeInstance))
ReadEA
WriteEA
ReadAttributes
WriteAttributes
访问原因:READ_CONTROL:由所有权授予( Access Reasons: READ_CONTROL: Granted by Ownership)
SYNCHRONIZE:由 D:(A;ID;FA;;;S-1-5-21-597862309-2018615179-2090787082-1000) 授予( SYNCHRONIZE: Granted by D:(A;ID;FA;;;S-1-5-21-597862309-2018615179-2090787082-1000))
当您阅读本文时,您可以看到我使用WINWORD.EXE 程序访问了(WINWORD.EXE program)Address Labels.docx并且我的访问包括READ_CONTROL并且我的访问原因也是READ_CONTROL。通常,您会看到更多访问,但只关注第一个访问,因为这通常是主要的访问类型。在这种情况下,我只是使用Word(Word)打开文件。确实需要进行一些测试并阅读(testing and reading)事件以了解正在发生的事情,但是一旦您将其关闭,它就是一个非常可靠的系统。我建议创建一个包含文件的测试文件夹(test folder)并执行各种操作以查看Event Viewer中显示的内容。
差不多就是这样!一种快速且免费的方式来跟踪对文件夹的访问或更改(access or changes)!
How to Track When Someone Accesses a Folder on Your Computer
There’s a nice little feature built into Windows that allows you to track when someone vіewѕ, edits, or deletеs ѕоmething inside оf a specified foldеr. So if there’s a folder or file that you want to know who is accessing, then this is the built-in method without haνing to use third-pаrty software.
This feature is actually part of a Windows security feature called Group Policy, which is used by most IT Professionals who manage computers in the corporate network via servers, however, it can also be used locally on a PC without any servers. The only downside to using Group Policy is that it is not available in lower versions of Windows. For Windows 7, you need to have Windows 7 Professional or higher. For Windows 8, you need Pro or Enterprise.
The term Group Policy basically refers to a set of registry settings that can be controlled via a graphical user interface. You enable or disable various settings and these edits are then updated in the Windows registry.
In Windows XP, to get to the policy editor, click on Start and then Run. In the text box, type “gpedit.msc” without the quotes as shown below:

In Windows 7, you would just click on the Start button and type gpedit.msc into the search box at the bottom of the Start Menu. In Windows 8, simply go to the Start Screen and start typing or move your mouse cursor to the far top or bottom right of the screen to open the Charms bar and click on Search. Then just type in gpedit. Now you should see something that is similar to the image below:

There are two main categories of policies: User and Computer. As you might have guessed, the user policies control the settings for each user whereas the computer settings will be system wide settings and will effect all users. In our case we’re going to want our setting to be for all users, so we’ll expand the Computer Configuration section.
Continue expanding to Windows Settings -> Security Settings -> Local Policies -> Audit Policy. I’m not going to explain much of the other settings here since this is primarily focused on auditing a folder. Now you’ll see a set of policies and their current settings on the right hand side. Audit policy is what controls whether or not the operating system is configured and ready to track changes.

Now check the setting for Audit Object Access by double clicking on it and selecting both Success and Failure. Click OK and now we’re done the first part which is telling Windows that we want it to be ready to monitor changes. Now the next step is to tell it what EXACTLY we want to track. You can close out of the Group Policy console now.
Now navigate to the folder using Windows Explorer that you would like to monitor. In Explorer, right click on the folder and click Properties. Click on the Security Tab and you see something similar to this:

Now click on the Advanced button and click on the Auditing tab. This is where we’ll actually configure what we want to monitor for this folder.

Go ahead and click the Add button. A dialog will appear asking you to select a User or Group. In the box, type in the word “users” and click Check Names. The box will automatically update with the name of the local users group for your computer in the form COMPUTERNAME\Users.

Click OK and now you’ll get another dialog called “Audit Entry for X“. This is the real meat of what we’ve been wanting to do. Here is where you’ll select what you want to watch for this folder. You can individually choose which types of activity you want to track, such as deleting or creating new files/folders, etc. To make things easier, I suggest selecting Full Control, which will automatically select all the other options below it. Do this for Success and Failure. This way, whatever is done to that folder or the files within it, you will have a record.

Now click OK and click OK again and OK one more time to get out of the multiple dialog box set. And now you have successfully configured auditing on a folder! So you might ask, how do you view the events?
In order to view the events, you need to go to the Control Panel and click on Administrative Tools. Then open up the Event Viewer. Click on the Security section and you’ll see a large listing of events on the right hand side:

If you go ahead and create a file or simply open the folder and click the Refresh button in the Event Viewer (the button with the two green arrows), you’ll see a bunch of events in the category of File System. These pertain to any delete, create, read, write operations on the folders/files you are auditing. In Windows 7, everything now shows up under File System task category, so in order to see what happened, you’ll have to click on each one and scroll through it.
In order to make it easier to look through so many events, you can put a filter and just see the important stuff. Click on the View menu at the top and click on Filter. If there is no option for Filter, then right-click on the Security log in the left-hand page and choose Filter Current Log. In the Event ID box, type in the number 4656. This is the event associated with a particular user performing a File System action and will give you the relevant information without having to look through thousands of entries.

If you want to get more information about an event, simply double click on it to view.

This is the information from the screen above:
A handle to an object was requested.
Subject:
Security ID: Aseem-Lenovo\Aseem
Account Name: Aseem
Account Domain: Aseem-Lenovo
Logon ID: 0x175a1
Object:
Object Server: Security
Object Type: File
Object Name: C:\Users\Aseem\Desktop\Tufu\New Text Document.txt
Handle ID: 0x16a0
Process Information:
Process ID: 0x820
Process Name: C:\Windows\explorer.exe
Access Request Information:
Transaction ID: {00000000-0000-0000-0000-000000000000}
Accesses: DELETE
SYNCHRONIZE
ReadAttributes
In the example above, the file worked on was New Text Document.txt in the Tufu folder on my desktop and the accesses that I requested were DELETE followed by SYNCHRONIZE. What I did here was delete the file. Here’s another example:
Object Type: File
Object Name: C:\Users\Aseem\Desktop\Tufu\Address Labels.docx
Handle ID: 0x178
Process Information:
Process ID: 0x1008
Process Name: C:\Program Files (x86)\Microsoft Office\Office14\WINWORD.EXE
Access Request Information:
Transaction ID: {00000000-0000-0000-0000-000000000000}
Accesses: READ_CONTROL
SYNCHRONIZE
ReadData (or ListDirectory)
WriteData (or AddFile)
AppendData (or AddSubdirectory or CreatePipeInstance)
ReadEA
WriteEA
ReadAttributes
WriteAttributes
Access Reasons: READ_CONTROL: Granted by Ownership
SYNCHRONIZE: Granted by D:(A;ID;FA;;;S-1-5-21-597862309-2018615179-2090787082-1000)
As you read through this, you can see I accessed Address Labels.docx using the WINWORD.EXE program and my accesses included READ_CONTROL and my access reasons were also READ_CONTROL. Usually, you’ll see a bunch more accesses, but just focus on the first one as that’s usually the main type of access. In this case, I simply opened the file using Word. It does take a little testing and reading through the events to understand what’s going on, but once you have it down, it’s a very reliable system. I suggest creating a test folder with files and performing various actions to see what shows up in the Event Viewer.
That’s pretty much it! A quick and free way to track access or changes to a folder!










