跟踪Windows(Windows)用户活动的原因有很多,包括监控孩子在 Internet 上的活动(children’s activity across the internet)、防止未经授权的访问、改进安全问题以及减轻内部威胁。
这里将讨论各种Windows环境的跟踪选项,包括您的家用 PC、服务器网络用户跟踪和工作组。
检查您的网络历史记录(Check Your Web History)
如果您想知道您计算机上的某个人(例如您的孩子)正在访问哪些网站,您可以通过浏览器历史记录找到该信息。尽管精通技术的用户可能知道隐藏此历史记录的方法,但检查一下也无妨。
- 使用谷歌浏览器(Google Chrome),点击右上角的三个点,然后点击历史记录(History)。

- 在Chrome(Chrome)中访问计算机历史记录的另一种方法是使用Ctrl + H快捷键。
- 在Firefox中,导航到顶部栏中如下图所示的图标,然后单击它。


- 在Microsoft Edge中,在窗口的右上角,查找并单击流星图标。然后点击历史(History)。

窗口事件(Windows Events)
Windows 会跟踪您计算机上的所有用户活动(track of all user activity on your computer)。确定其他人是否在使用您的计算机的第一步是确定它的使用时间。
- 在开始菜单中,键入事件查看器(event viewer)并通过单击将其打开。

- 要展开Windows 日志(Windows Logs)文件夹,请单击事件查看器(本地)。(Event Viewer (local).)
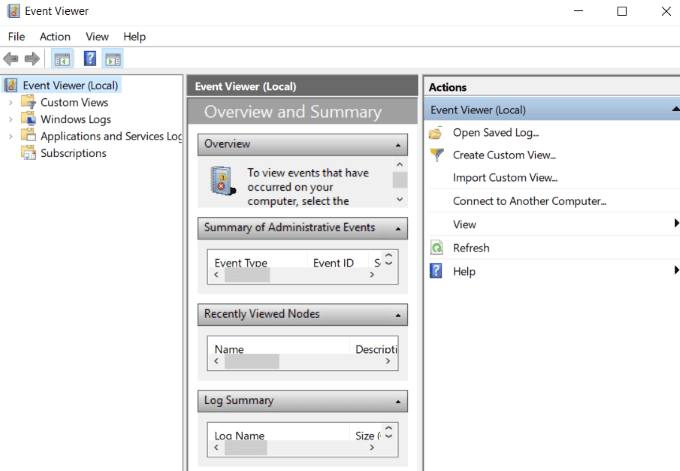
- 通过单击展开Windows 日志(Windows Logs),然后右键单击系统。(System.)
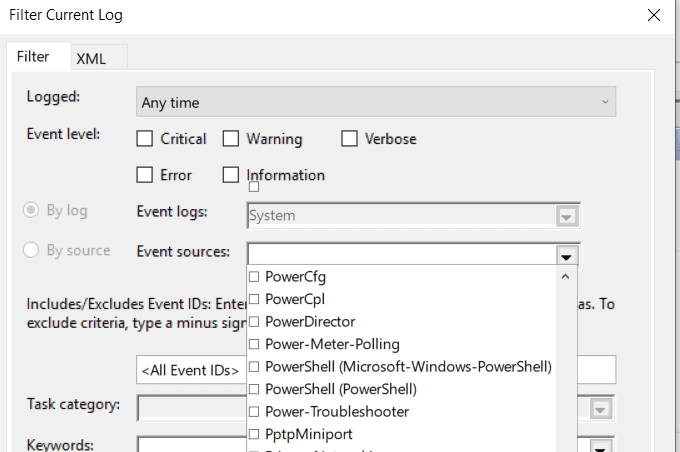
- 双击Filter Current Log并打开(Filter Current Log)Event Sources的下拉菜单。
- 向下滚动到Power-Troubleshooter并勾选它旁边的框。然后单击确定(OK)。
- Windows 事件查看器(Windows Event Viewer)将显示您的计算机何时退出睡眠模式或打开。如果您在这段时间内没有使用它,那么其他人就在使用它。

如何识别 Windows 服务器上的可疑活动(How To Identify Suspicious Activity On a Windows Server)
如果您正在运行具有多个Windows服务器的环境,则安全性至关重要。出于多种原因,审核(Auditing)和跟踪Windows活动以识别可疑活动至关重要,包括:
- Windows 操作系统(Windows OS)中恶意软件和病毒的流行
- 某些应用程序和程序要求用户禁用某些防病毒和本地防火墙
- 用户通常不会断开远程桌面会话,从而使系统容易受到未经授权的访问
与其等到事故发生,不如采取预防措施。您应该有一个强大的安全监控流程,以查看谁在何时登录您的服务器。这将识别Windows服务器安全报告中的可疑事件。
在 Windows 报告中要注意什么(What To Look Out For In Your Windows Reports)
作为服务器的管理员,有几个事件需要密切关注,以保护您的网络免受恶意Windows用户活动的影响,包括:
- 远程桌面会话尝试失败或成功。
- 重复登录尝试导致密码锁定。
- (Group)您未进行的组或审核策略更改。
- (Successful)登录Windows网络、成员服务或域控制器的成功或失败尝试。
- 删除或停止现有服务或添加新服务。
- 注册表设置已更改。
- 事件日志已清除。
- 禁用或更改了Windows防火墙或规则。
如上所述,事件记录在Windows的事件日志中。本机日志的三种主要类型是:
XpoLog7
XpoLog7是一个自动化的日志管理工具,提供:
基本计划永远免费,每天 0.5GB。对于那些需要更多功能的用户,Xpolog7还提供了多个分层定价选项(pricing options)。

如何跟踪工作组中的用户活动(How To Track User Activity In Workgroups)
工作组是有组织的计算机网络。它们使用户能够共享存储、文件和打印机。
这是一种方便的协同工作方式,易于使用和管理。但是,如果没有适当的管理,您的网络就会面临可能影响工作组所有参与者的潜在安全风险。
以下是有关如何跟踪用户活动以提高网络安全性的提示。
使用 Windows 审核策略(Use Windows Audit Policy)
按照以下步骤跟踪工作组参与者在您的网络上所做的事情。
- 按住Windows 键(Windows key)和R打开运行。
- 在Open:(Open:)旁边的框中键入secpol.msc ,然后单击OK。
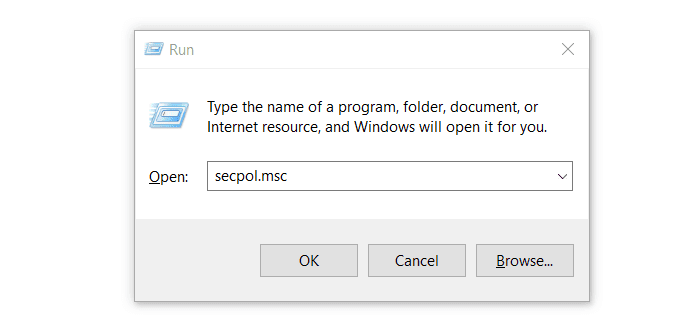
这将打开本地安全策略(Local Security Policy)窗口。

- 在左侧的列中( Settings),双击安全(Securit)设置(y)。然后通过单击展开本地策略设置。(Local Policies)
- 打开Audit Policy,然后在右窗格中的菜单上,您将看到许多设置为未定义的(Not Defined.)审核条目。(Audit)

- 打开第一个条目。在本地安全设置(Local Security Settings)选项卡中,检查审核这些尝试(Audit these attempts)下的成功(Success )和失败( Failure)。然后单击应用(Apply)和确定(OK)。

对所有条目重复上述步骤以跟踪工作组中的用户活动。请记住,您的工作组中的所有计算机都必须得到适当的保护。如果一台计算机被感染,则连接到同一网络的所有其他计算机都处于危险之中。
键盘记录器(Keyloggers)
键盘记录程序(Keylogger programs)监控键盘活动并记录所有键入的内容。它们是监视Windows用户活动以查看是否有人侵犯您的隐私的有效方法。
大多数使用键盘记录程序的人都是出于恶意。因此,您的反恶意软件程序可能会隔离它。因此,您需要删除隔离区才能使用它。
如果您在市场上,有几个免费的键盘记录软件程序供您选择。
How To Track Windows Computer and User Activity
There are many reasons to track Windows user activity, inclυding monіtoring your children’s activity across the internet, protection against unauthorized access, improving security issues, and mitigating insider threats.
Here will discuss tracking options for a variety of Windows environments, including your home PC, server network user tracking, and workgroups.

Check Your Web History
If you want to know which sites someone on your computer (such as your children) are visiting, you can find that information via the browser history. Even though tech-savvy users might know ways to hide this history, it doesn’t hurt to check.
- Using Google Chrome, click on the three dots in the upper right-hand corner and click History.

- Another way to access your computer history in Chrome is to use the Ctrl + H shortcut.
- In Firefox, navigate to the icon in the top bar that looks like the image below and click on it.


- In Microsoft Edge, in the top-right corner of the window, look for and click on the shooting star icon. Then click on History.

Windows Events
Windows keeps track of all user activity on your computer. The first step to determine if someone else is using your computer is to identify the times when it was in use.
- From the Start Menu, type event viewer and open it by clicking on it.

- To expand the Windows Logs folder, click on Event Viewer (local).

- Expand Windows Logs by clicking on it, and then right-click on System.
- Double-click on Filter Current Log and open the dropdown menu for Event Sources.
- Scroll down to Power-Troubleshooter and tick the box next to it. Then click OK.

- The Windows Event Viewer will show you when your computer was brought out of sleep mode or turned on. If you weren’t using it during these times, someone else was.

How To Identify Suspicious Activity On a Windows Server
If you are running an environment with several Windows servers, security is vital. Auditing and tracking Windows activities to identify suspicious activity is paramount for numerous reasons, including:
- The prevalence of malware and viruses in Windows OS
- Some applications and programs require users to disable some antivirus and local firewalls
- Users often don’t disconnect remote desktop sessions, leaving the system vulnerable to unauthorized access
It’s better to take preventative measures than to wait until an incident occurs. You should have a robust security monitoring process in place to see who is logging onto your server and when. This will identify suspicious events in the Windows server security reports.
What To Look Out For In Your Windows Reports
As the administrator of a server, there are several events to keep an eye on to protect your network from nefarious Windows user activity, including:
- Failed or successful attempts of remote desktop sessions.
- Repeated login attempts resulting in password lockouts.
- Group or audit policy changes you didn’t make.
- Successful or failed attempts to log into your Windows network, member services, or domain controller.
- Deleted or stopped existing services or new services added.
- Registry settings changed.
- Event logs cleared.
- Disabled or changed Windows firewall or rules.
As discussed above, events are recorded in the event log in Windows. The three main types of native logs are:
- Security.
- Application.
- System.
XpoLog7
XpoLog7 is an automated log management tool to provide:
- Log data analysis
- Automatic detection of problems
- Proactive monitoring of rules and events
The basic plan is free forever for 0.5GB/day. For those needing more features, Xpolog7 also offers several tiered pricing options.

How To Track User Activity In Workgroups
Workgroups are organized networks of computers. They enable users to share storage, files, and printers.
It is a convenient way to work together and easy to use and administer. However, without proper administration, you are opening your network to potential security risks that can affect all participants of the workgroup.
Below are tips on how to track user activity to increase your network security.
Use Windows Audit Policy
Follow the steps below to track what workgroup participants are doing on your network.
- Open Run by holding down the Windows key and R.
- Type secpol.msc in the box next to Open: and click OK.

This will open the Local Security Policy window.

- From the column on the left, double-click Security Settings. Then expand the Local Policies setting by clicking on it.
- Open Audit Policy, and then on the menu in the right pane you will see many Audit entries that are set to Not Defined.

- Open the first entry. From the Local Security Settings tab, check Success and Failure under Audit these attempts. Then click Apply and OK.

Repeat the steps above for all entries to track user activity in workgroups. Keep in mind that all the computers in your workgroup must be properly protected. If one computer gets infected, all others connected to the same network are at risk.
Keyloggers
Keylogger programs monitor keyboard activity and keep a log of everything typed. They are an effective way to monitor Windows user activity to see if someone has been intruding on your privacy.
Most people who use keylogger programs do so for malicious reasons. Because of this, your anti-malware program will likely quarantine it. So you will need to remove the quarantine to use it.
There are several free keylogger software programs for you to choose from if you are in the market.














