我最近在法兰克福(Frankfurt)机场时,看到一个商人把他非常昂贵的MacBook Air笔记本电脑放在桌子上去喝咖啡。他离开了五分钟,但在那五分钟内,有人可能偷走了计算机,或者入侵了计算机以获取有价值的数据。
不过,如今,黑客不需要对机器进行物理访问。使用网络嗅探器,他们可以在公共wifi 热点中(wifi spots)寻找弱点,或进入没有密码的私人 wifi 热点。

因此,从一开始,您就需要保护您的 macOS 计算机免受这些“坏人”的侵害。但是,您必须记住,在我们继续之前,您永远不会拥有 100% 的铁定安全,如果您遇到政府机构,这些基本步骤将无济于事。
但是要阻止偶然的机会主义者?继续阅读。
将密码添加到您的计算机(Add a Passcode
To Your Computer)

这绝对是不费吹灰之力,但我对不理会它的人的数量感到震惊。这就像去度假,前门没上锁,想知道什么时候回来,为什么会被盗。
添加密码很简单。转到系统偏好设置 - 安全和隐私(System Preferences – Security & Privacy)。在“常规(General )”选项卡中,您可以设置密码,以及指定计算机休眠多长时间后需要密码。显然立即(immediately)是最好的选择。

您还可以添加密码提示,以防您忘记密码,但除非您让其他人阅读的提示非常模糊,否则我不建议您这样做。只需将密码设置为您保证记住的密码即可。
打开文件保险箱(Turn On
FileVault)
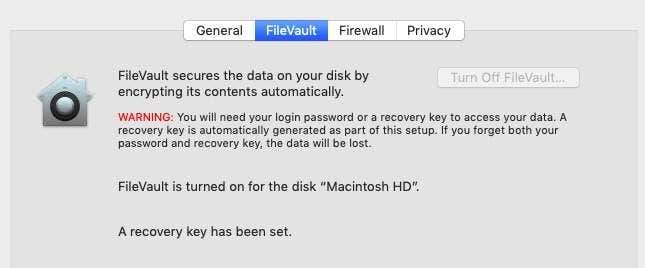
MacOS设备的一大优点是,当您完全关闭它时,硬盘驱动器上包含的文件完全无法访问。但要利用这一点,您需要打开FileVault。
FileVault位于系统偏好设置 - 安全和隐私( System Preferences – Security & Privacy)中,对硬盘进行加密,但只有在计算机完全关闭时才会启动加密。所以尽量不要太频繁地使用睡眠模式,尤其是当你带着笔记本电脑外出时。
当您打开它时,整个硬盘驱动器需要几个小时才能被加密,但为了安心,这是完全值得的。如果您在本文中只需要做一件事,那就是FileVault。剩下的只是锦上添花。
确保挂锁在系统偏好设置中打开(Make Sure The
Padlock Is On In System Preferences)

使用左下角的小挂锁图标可以防止对计算机的系统偏好设置(System Preferences )进行未经授权的更改。
如果您想确保系统偏好设置(System Preferences)的安全,请单击挂锁以将其关闭。如果您想再次打开它来更改任何内容,您将需要输入管理员密码。
不要以管理员身份登录(Do Not Log In
As An Administrator)

另一个禁忌是登录计算机并将其作为“管理员”用于日常任务。
具有管理员权限的用户可以在计算机上执行所有操作。安装(Installing)和删除软件,以及添加和删除只是其中两个的用户。如果进入您计算机的任何人已经以管理员身份登录,它会将王国的钥匙交给他们。
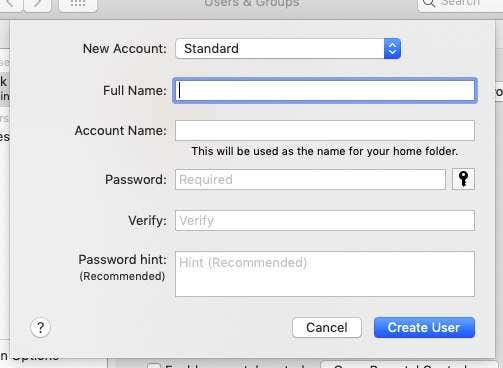
解决方案是创建一个普通的非管理员帐户并将其用于日常计算机使用。保留管理员帐户,仅在计算机请求时使用这些登录详细信息。
要创建新用户,请转到系统偏好设置 - 用户和组(System Preferences – Users & Groups)。确保挂锁在底部已解锁,然后单击Login Options下方的“+” 。使新帐户成为标准(Standard)帐户。
禁止访客用户(Disallow Guest
Users)

很多人说,拥有一个访客用户帐户以供其他人使用您的计算机是个好主意。但我持相反的观点。
尽管来宾用户对您的计算机的访问受到更多限制,但他们仍然可以访问两个重要区域。首先(First),他们可以访问所有已安装的应用程序,他们可以使用这些应用程序执行任何形式的恶意操作。
其次,他们还可以访问可以存储恶意脚本和恶意软件的 tmp 目录。
因此,请转到系统偏好设置 - 用户和组(System Preferences – Users & Groups)并关闭访客用户(Guest User)选项。
确保自动更新已打开(Make Sure
Automatic Updates Are Turned On)
与任何其他操作系统一样,Apple会
定期推出MacOS更新。(MacOS)软件也是如此——如果需要补丁,开发人员会制作一个并将其发送出去。
因此,如果补丁已准备好安装而您没有打开自动更新,那将毫无意义。除非您喜欢每天手动检查,否则谁有时间?
要打开自动更新(Automatic Updates),请转到系统偏好设置 - 软件更新(System Preferences – Software Update)。勾选“自动使我的 Mac 保持最新(Automatically keep my Mac up to date)”框。
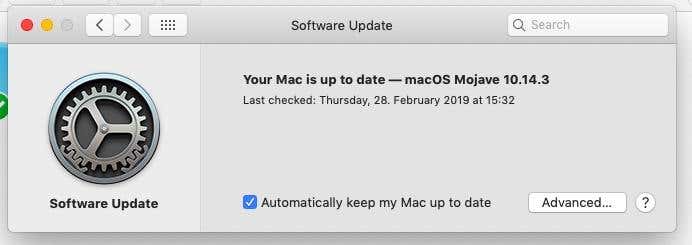
如果您随后单击“高级(Advanced)”框,您将看到可用的选项。我建议你全部勾选。

打开防火墙(Turn On The
Firewall)

这也有点简单,但同样,很多人只是不打扰。
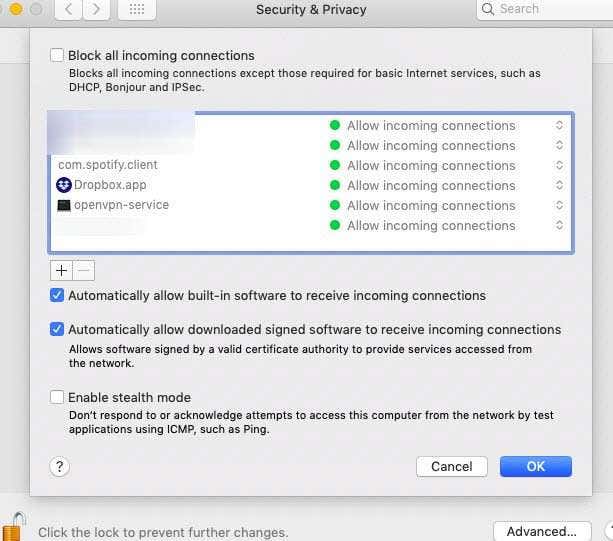
与可能需要大量调整的Windows防火墙相比,macOS 防火墙是一键式交易。通过转到系统偏好设置 - 安全和隐私(System Preferences – Security & Privacy),然后转到防火墙(Firewall )选项卡,您可以一键打开防火墙。就是这样。
我从来(never)没有接触过防火墙选项(Firewall Options)部分中的任何内容。我很快就会写一篇关于 MacOS 防火墙的“隐身模式”的文章,但总的来说,请保持下面截图中的样子。
匿名化您计算机的网络名称(Anonymize The
Network Name Of Your Computer)
这是不久前一位朋友向我建议的,这是我以前从未真正考虑过的。
如果有人入侵您的网络,他们显然会看到连接到该网络的所有设备的名称。如果只有一个设备(您的MacOS设备),那么这将限制为无效。但是,如果您的网络中有多个设备,您可以尝试通过匿名化名称来伪装您的MacOS设备。(MacOS)
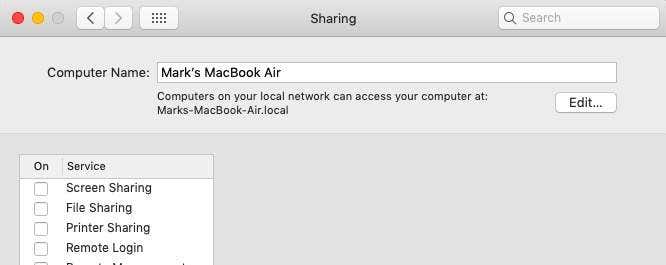
例如,在我被告知之前,我的电脑名称是“Mark's MacBook Air”。我的意思是,我还不如竖个牌子说:“进来吧!把(Get)我所有的文件都拿在这里!”。但是通过将名称更改为无害的名称,它现在位于我所有其他连接的设备中。
显然,这并非万无一失。任何人都可以逐一检查每台设备,但这会花费更长的时间,并且会给他们带来更多麻烦。
转到系统偏好设置 - 共享(System-Preferences – Sharing),在顶部,您将看到您的计算机的名称。单击屏幕底部的挂锁,输入您的管理员密码,计算机名称旁边的编辑按钮将突然变为活动状态。点击它。
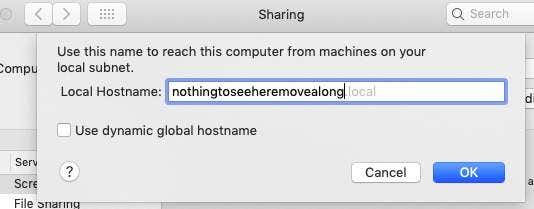
您现在将被邀请将名称更改为您想要的任何名称。保持“使用动态全局主机名”(“Use dynamic global hostname”)
未选中。
关闭共享(Turn Off
Sharing)

当您在“共享(Sharing )”部分时,是时候关闭所有这些选项——除了一个——内容缓存。
据我所知,内容缓存(Content Caching)很好,似乎实际上对您有益。这反过来又打开了Internet 共享(Internet Sharing),所以我想你也可以离开那个。但是其他的,例如屏幕共享(Screen Sharing)、文件共享(File Sharing)、远程登录——(Remote Login –)关闭它们(除非你非常需要打开它们)。
结论(Conclusion)
正如我在开头所说的那样,这些措施只会阻止咖啡店里的随意窥探者,或者想要抢夺您的笔记本电脑以快速获得现金的小偷。
如果您受到政府机构或其他形式的专业人士的攻击,这些措施会减缓他们的速度——但只会持续很短的时间。
但是,总比没有好,对吧?为什么要让他们轻松?
How to Make it Harder For Someone to Hack into Your Mac
When I was at Frankfurt aіrpоrt recently, I saw a businessman leave his very expensive MacBook Air laptop on the table to go and get coffee. He waѕ gone for five minutes but in those five minutes, somebody сould either have stolen the computer or hacked into it for valuable data.
These days though, hackers don’t need physical access to the machine. Using network sniffers, they can prowl public wifi spots looking for weaknesses, or enter private wifi spots which don’t have passwords.

So from the get-go, you need to protect your macOS computer from these “bad actors”. You have to bear in mind, though, before we continue that you are never going to have 100% iron-clad security, and if you are up against a government agency, these basic steps are nowhere near going to help.
But to stop the casual opportunist? Read on.
Add a Passcode
To Your Computer

This is an absolute no-brainer, but I am stunned at the number of people who don’t bother with it. This is like going on vacation and leaving your front door unlocked, and wondering when you got back why you were burglarized.
Adding a passcode is simple. Go to System Preferences – Security & Privacy. In the General tab, you can set a password, as well as specify how long after the computer sleeps the password is required. Obviously immediately is the best option.

You can also add a password hint in case you forget your password, but unless you make the hint extremely vague for anyone else reading it, I wouldn’t recommend doing this. Just make the password something you are guaranteed to remember.
Turn On
FileVault

One of the great things about a MacOS device is that when you have it fully powered down, the files contained on the hard drive are totally inaccessible. But for you to take advantage of that, you need to turn on FileVault.
Located in System Preferences – Security & Privacy, FileVault encrypts the hard drive, but the encryption only kicks in if the computer is shut down completely. So try not to use sleep mode too often, especially if you are out and about with your laptop in your bag.
When you switch it on, it will take a few hours for the entire hard drive to be encrypted, but it is totally worth it for peace of mind. If there is only one thing you should do from this article, it is FileVault. The rest is just icing on the cake.
Make Sure The
Padlock Is On In System Preferences

Unauthorized changes to the computer’s System Preferences are prevented by the use of a small padlock icon in the bottom left-hand corner.
If you want to keep System Preferences secure, click the
padlock to close it. If you want to open it again to change anything, you will
be required to enter the administrator password.
Do Not Log In
As An Administrator

Another no-no is logging into the computer and using it for
routine tasks as the “administrator”.
A user with administrator privileges is able to do everything on the computer. Installing and removing software, as well as adding and removing users being just two of them. If anyone that got into your computer is already logged in as the administrator, it hands them the keys to the kingdom.
The solution to this is to make an ordinary non-administrator account and use that for everyday routine computer usage. Leave the administrator account alone and use those login details only when the computer requests them.
To make a new user, go to System Preferences – Users & Groups. Make sure the padlock is unlocked at the bottom then click the “+” below Login Options. Make the new account a Standard one.

Disallow Guest
Users

A lot of people say it is a good idea for you to have a guest
user account for other people to use your computer. But I take the opposite
view.
Although the guest user has much more restricted access to your computer, they still have access to two important areas. First, they have access to all the installed applications which they can use to perform any manner of malicious action.
Second, they also have access to the tmp directory where
malicious scripts and malware can be stored.
So go to System Preferences – Users & Groups and turn off the Guest User option.
Make Sure
Automatic Updates Are Turned On
Like any other operating system, Apple pushes out MacOS
updates on a regular basis. The same with software – if a patch is needed, the
developer will make one and send it out.
So it is pointless if the patch is sitting there ready to be
installed and you don’t have automatic updates switched on. Unless you like to
manually check every single day and who has time for that?
To switch on Automatic Updates, go to System Preferences – Software Update. Tick the box that says Automatically keep my Mac up to date.

If you then click the Advanced box, you will see the options available. I suggest you tick all of them.

Turn On The
Firewall

This one is also a bit of a no-brainer, but again, many
people just don’t bother.
Compared to Windows firewalls, which can involve a lot of tweaking, macOS firewalls are a one-click deal. By going to System Preferences – Security & Privacy, and then the Firewall tab, you can switch the firewall on with one click. And that is really it.
I have never had to touch anything in the Firewall Options section. I will shortly be doing an article on MacOS Firewall’s “Stealth Mode”, but in general, keep things as they are in the screenshot below.

Anonymize The
Network Name Of Your Computer

This is one which was suggested to me by a friend not that
long ago, and it was something I had never really previously considered.
If someone hacks into your network, they are going to
obviously see the names of all the devices connected to that network. If there
is only one device (your MacOS device), well then this is going to have limited
to no effect. But if you have multiple devices in your network, you can try to
camouflage your MacOS device by anonymizing the name of it.
For example, until I was advised of this, my computer’s name
was “Mark’s MacBook Air”. I mean, I may as well have put up a sign saying “Come
on in! Get all my files here!”. But by changing the name to something
innocuous, it is now sitting amongst all of my other connected devices.
Obviously, this is not foolproof. Anyone can check each device one by one but it will take them longer and make things more of a hassle for them.
Go to System-Preferences – Sharing and at the top, you will see the name of your computer. Click the padlock at the bottom of the screen, enter your administrator password and the edit button next to the computer name will suddenly become active. Click it.

You will now be invited to change the name to whatever you
want. Keep “Use dynamic global hostname”
unchecked.
Turn Off
Sharing

While you are in the Sharing section, it’s time to turn off all of these options – except for one – content caching.
From what I have been able to find, Content Caching is fine and seems to actually benefit you. This in turn turns on Internet Sharing, so I guess you can leave that one too. But the others, such as Screen Sharing, File Sharing, Remote Login – switch them off (unless you have a huge need to have them on).
Conclusion
As I stated at the beginning, these measures are only going to stop the casual snooper at the coffee shop, or a thief looking to snatch your laptop for some quick cash.
If you are being assaulted by a government agency or another form of professional, these measures will slow them down – but only for a very short while.
But nevertheless, better than nothing, right? Why make it
easy for them?















