每个操作系统和设备都有其安全工具。如果您使用台式计算机,您将熟悉范围广泛的防火墙、病毒和恶意软件检查程序以及一般安全建议(general security advice)。
但是您的智能手机和平板电脑呢?随着越来越多的人转向移动计算,越来越多的平板电脑被用作事实上的计算机(more tablets being used as de-facto computers),对移动安全解决方案的需求变得越来越迫切(becomes ever more pressing)。
一种针对 iOS 设备的新解决方案已经出现,称为iVerify。只需 5 美元,它就会让寻找免费赠品的人群望而却步,但为了换取安心,牺牲你的每日拿铁咖啡是值得的。
But….iOS Devices Can’t Be Hacked!
有一种危险的错觉认为 iOS 设备是坚不可摧的。对它们的加密使它们对任何黑客攻击都永垂不朽。那是错的。
确实(is),iOS 设备具有非常好的加密功能(只要您记得打开它们!)。但没有什么是可以保证的。漏洞一直在被发现,仅 iMessage 就有十个漏洞(ten bugs in iMessage alone)。
iVerify 监控任何潜在的安全漏洞并标记任何它认为可疑的东西。它还为您提供了完全锁定手机所需要做的事情的清单,以使任何人都更难访问您的手机。
为 iOS 设置 iVerify(Setting Up iVerify for iOS)
iVerify 适用于 iPhone 和 iPad。购买一个将为您提供另一个版本,因此如果您同时拥有两个设备,我们强烈建议您在两个设备上都设置该应用程序。
- 下载应用程序后,将其打开并单击绿色的继续(Continue)按钮。

- 然后打开主屏幕,显示它认为的四个主要安全领域——设备扫描、触控 ID、屏幕锁定(Device Scan, Touch ID, Screen Lock)和您当前的iOS 版本(iOS Version)。
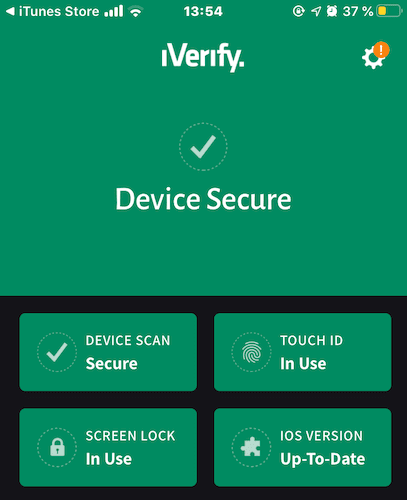
- 由于我正在使用和更新它们,它们目前都是绿色的。但是,如果其中任何一个被禁用或过期,它们将显示为红色,需要立即关注。
- 如果您轻轻点击其中一个按钮,它将为您提供相关信息。
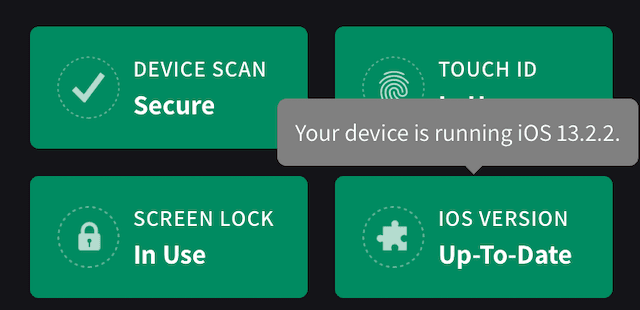
- 如果您现在进一步向下滚动页面,您将看到现在可以采取的安全预防措施清单,以进一步锁定您的设备。

- 如果您点击第一个,防止盗窃,(Protect against theft,)您将获得 iVerify 在该类别中的建议列表。

- 有点缺点的是,iVerify 不会检查您是否已经完成了这些事情。它只是假设你没有。如果您发现您已经完成了某项操作,请点击它,滚动到底部,然后点击我已查看此(I’ve Reviewed This)内容。然后它将被标记为完成。

- 对于您尚未完成的任务,点击它,下一页将为您提供有关如何完成它的完整说明,包括一个带您进入设备设置的按钮。
- 完成后,返回 iVerify,点击Ive Review This(I’ve Reviewed This),它将被标记为完成。继续下一个并重复。
iVerify 检测到对您的 iOS 设备的威胁(iVerify Detects Threats to Your iOS Device)

当 iVerify 检测到威胁时,它会生成一个返回到Trail of Bits的唯一链接,该链接是制作 iVerify 的开发人员。此链接为您提供有关如何消除威胁以及向Trail of Bits报告威胁以改进其威胁数据库的信息。
如屏幕所示,在另一个未受感染的设备上打开链接,关闭受感染的设备并按照给定链接中的说明进行操作。
Not 100% Perfect – But Better Than Nothing
这不应被视为对抗间谍软件、恶意软件和黑客的完美解决方案。没有什么是完美的。威胁一直在演变,显然,如果政府或国家支持的坏人参与其中,那么像 iVerify 这样的东西将毫无用处。
但我们 99% 的人不会成为极权政府或使用语音扰频设备的人的目标,他们要求支付 10 亿美元以换取不搞乱电网。对于我们普通人来说,iVerify 可以证明是一种非常宝贵的资源。
How to Use iVerify to Protect Your iOS Device From Hackers
Evеry operating system and device has itѕ security tools. If you uѕe a desktop computer, you will be familiar with the wіde range of firewalls, virus and malwаre chеckers, and general security advice out there.
But what about your smartphones and tablets? With more people switching to mobile computing, and more tablets being used as de-facto computers, the need for a mobile security solution becomes ever more pressing.

A new solution for iOS devices has presented itself, called iVerify. At $5, it will put off the freebie-searching crowd, but it’s worth sacrificing your daily latte in exchange for peace of mind.
But….iOS Devices Can’t Be Hacked!
There’s a bit of a dangerous delusion that iOS devices are impregnable. That the encryption on them makes them immortal to any hacking attempts. That is wrong.
It is true that iOS devices have extremely good encryption features (provided you remember to switch them on!). But nothing is guaranteed. Bugs are being found all the time, including ten bugs in iMessage alone.
iVerify monitors for any potential security vulnerabilities and flags up anything it deems suspicious. It also gives you a checklist of things you need to do to lock down your phone completely to make it even more difficult for anyone to access your phone.
Setting Up iVerify for iOS
iVerify works on both the iPhone and iPad. Buying for one will give you the version for the other, so we strongly suggest setting the app up on both devices if you have both.
- When the app has been downloaded, open it up and click the green Continue button.

- This then opens up the main screen to show what it believes to be the four main important areas of security – Device Scan, Touch ID, Screen Lock, and your current iOS Version.

- Since I am using and updating them all, they are all currently green. But if any of them were disabled or out-of-date, they would show up as red, requiring immediate attention.
- If you lightly tap on one of the buttons, it will give you relevant information.

- If you now scroll further down the page, you will see checklists of security precautions you can now take to lock down your device even more.

- If you tap on the first one, Protect against theft, you will get a list of iVerify’s recommendations in that category.

- What is a bit of a minus is that iVerify does not check to see if you have already done these things. It just assumes that you haven’t. If you find something you have already done, tap on it, scroll to the bottom, and then tap I’ve Reviewed This. It will then be marked as complete.

- For a task you haven’t completed, tap on it and the next page will give you complete instructions on how to achieve it, including a button to take you to the device settings.

- Once you’ve done it, come back to iVerify, tap I’ve Reviewed This, and it will be marked as complete. Move on to the next one and repeat.
iVerify Detects Threats to Your iOS Device

When iVerify detects a threat, it generates a unique link back to Trail of Bits, the developer which made iVerify. This link gives you information on what to do to eliminate the threat, as well as report the threat to Trail of Bits, to improve its threats database.
As the screen says, open the link on another non-infected device, close down the infected device and follow the instructions in the link given.
Not 100% Perfect – But Better Than Nothing
This should not be seen as a perfect solution to fighting spyware, malware, and hackers. Nothing is perfect. Threats evolve all the time, and obviously, if a government or state-backed bad guy gets involved, well then something like iVerify is going to be useless.
But 99% of us are not going to be targeted by totalitarian governments or someone using a voice scrambling device demanding they be paid a billion dollars in exchange for not messing up the power grid. For us ordinary folks, iVerify could prove to be a very valuable resource.









