即使是非极客也可能听说过“ TCP/IP ”,但每个人都知道它是什么或如何使用命令行在(using the command line)Linux服务器上配置它吗?
它有助于首先定义基本术语。至少,它允许您开发一个框架来建立您的理解。TCP/IP也不例外。
本节有关术语的内容并非详尽无遗。它将为您提供了解网络以及如何在Linux上配置(Linux)TCP/IP文件的旅程的基础。

The *Nix World
你有没有想过*nix是什么意思?Unix 和 Linux 是(Unix and Linux are related)如何相关的(更不用说每个版本的所有不同版本了)?
*nix是一种使用通配符(星号)引用Linux和/或Unix(或任何发行版)的方法。
* Nix是在 1960 年代后期开发的。AT& T 贝尔实验室(T Bell Labs)大约在同一时间开发了Unix 。经过各种迭代和发展,Linux也应运而生。
这些并行创新的结果是,一旦您学会了如何通过命令行在一台服务器上执行安装,您就学会了一项可能与各种Unix或Linux服务器上的许多其他任务兼容的技能。
手册页——触手可及的信息(Man Pages – Information at Your Fingertips)
与Google(Google)非常相似,Linux拥有自己的一套搜索和研究工具,使用户能够找到他们需要的资源。这些资源被称为“手册页”。当您登录到Linux服务器(或基于Linux的操作系统)时,您可以打开命令行应用程序并输入您想要研究的内容,例如在交互式文档文件中输入搜索词。
如果你选择一个你想研究的主题,比如一个Linux实用程序、工具、守护进程、脚本(daemon, script),你可以通过输入“man”然后输入单词来查找它。您将在本文后面学习如何执行此操作。
手册页易于使用。只需(Just)开始输入几个单词,Linux 操作系统(Linux OS)就会开始将信息返回给您。如果没有特定主题的手册页,Linux会告诉你。

在大多数情况下,手册页对于它们出现的软件版本来说是相当准确的。例如,如果您登录到一台已有 10 年历史的Linux服务器,则手册页会显示与该版本(和年龄)相关的信息。
手册页易于使用且准确,但有一些注意事项。让我们通过图像说明这些警告。
在下图中, ARP(ARP)的手册页表明ARP已过时(在“注释”部分下),应该查找ip neigh。通过这种表示法,人们可能想要键入“ man ip neigh ”来访问有关替换工具/协议的信息。
但是,键入“ man ip neigh ”不会查找“ip neigh”的手册页。相反,它会查找两个手册页……一个用于“ip”,另一个用于“neigh”。
确实,如果您键入“man ip neigh”,您会得到一个手册页,但除非您密切注意,否则您可能会错过它实际上并不是您要查找的内容。
您可以添加一个破折号(即使在引用替换工具时手册页中没有显示)......所以,如果您添加一个破折号并输入“man ip-neigh”,它也可以正常工作,但它不正确任何一个。
您可以尝试输入“ man ip-neighbour ”(注意英国拼写)。当您键入该特定短语时,您将看到用于替换ARP手册页(或替换ARP协议)的正确手册页。底线是:如果找不到所需的内容,请尝试使用不同的组合,直到获得所需的手册页。

例如,尝试查找 nslookup 工具的手册页。您可以通过键入“man nslookup”来执行此操作。当你这样做时,你会看到一个类似于下面的图像/屏幕截图的手册页。您将了解有关 nslookup 工具的所有信息。
手册页在屏幕上弹出后,您可以向下滚动、阅读、应用、测试甚至关闭手册页(通过键入字母“q”并让手册页自动关闭)。
如果您请求的手册页不存在,Linux将向您提供该手册页没有条目的反馈并尝试另一个。

IPv4 和 IPv6(IPv4 and IPv6)
IPv4和IPv6在技术上是相同的,但在我们人类(IPv4)看来(IPv6)它们并不相同。它们是一种在局域网 ( LAN ) 上识别机器或设备的方法。它们在识别LAN中的设备时是私有的。
IPv4使用由点/句点分隔的数字。我们大多数人都熟悉使用IPv4(IPv4)格式连接到我们的专用网络的计算机的 IP 地址类型。
网络上的计算机也有IPv6地址,但看起来不同。IPv6由用冒号 ( : ) 分隔的字母数字字符组成。

那么IPv4(IPv4)和IPv6之间有什么区别呢?把(Think)它想象成一个网络名称。一个就像名字,另一个是姓氏。这两个名字都指向同一个人(或者在这种情况下,是一台计算机)。正如我们通常有一个不同的名字与我们的姓氏一样,IPv4“名称”将与IPv6“名称”不同,即使它们都指向同一台机器。
Carla Schroeder撰写了(Carla Schroeder)一篇关于 IPv4 和 IPv6(useful article about IPv4 and IPv6)的易于阅读且有用的文章。
Linux 服务器上的根访问权限(以及 su 和 sudo)(Root Access on a Linux Server (and su and sudo))
对于许多需要完成的任务,需要 root 访问权限(也称为管理员或超级用户)。这是因为许多这些实用程序和应用程序足够敏感,以至于出于安全原因而受到限制。
以 root 身份登录或触发超级用户访问 (su) 的另一种解决方案是在命令前添加“sudo”,告诉Linux机器该特定命令需要以超级用户/root 身份运行,但后续命令不需要(除非前面加上“sudo”指令)。
如果使用“sudo”并将其添加到命令前,Linux将请求 su 密码以验证超级用户身份和权限。
网络协议(Networking Protocols)
讨论Linux(Linux)时需要考虑许多不同的协议。本文主要的两个协议是TCP和 IP。
传输控制协议 (TCP)(Transmission Control Protocol (TCP))
传输控制协议(Transmission Control Protocol),通常称为TCP,顾名思义,是一种用于数据包传输的协议。
有关各种工具的说明,请参见下文,包括名为Traffic Control (tc) 的Linux工具。(Linux)
TCP指导Linux操作系统如何将数据包从一个地方移动到另一个地方。它还控制网络流量并指导信息包的传输(例如从一个地方移动到另一个地方 的数据文件夹)。(data)
这就是该协议被称为 传输控制协议(Transmission Control Protocol)(TCP) 的原因。
互联网协议 (IP)(Internet Protocol (IP))
Internet 协议(Internet Protocol)通常以其首字母缩写词 IP 来表示。
在IP的情况下,您有更广泛的区域(互联网(Internet))来传输数据包。这就像拥有一条更宽、更长、更多人的超级高速公路……称为互联网。TCP控制数据包在网络上的移动,而 IP 控制数据包在互联网上的移动。

ICMP 协议(ICMP Protocol)
ICMP代表Internet 控制消息传递协议(Internet Control Messaging Protocol)。虽然它是一种在大多数Linux发行版中都可用的协议,但它可能并非在所有Linux发行版中都可用。当前的Centos安装中缺少手册页证明了这一点。(Man)
乍一看,这个特定的协议似乎并不那么重要,但实际上确实如此。如果/当数据包未正确到达其目的地时, ICMP(ICMP)负责提供错误消息。ICMP对于接收正在传输的信息包的传递(或接收)状态更新是必不可少的。
用户图协议 (UDP)(User Diagram Protocol (UDP))
用户图协议(User Diagram Protocol)( UDP ) 与传输控制协议(Transmission Control Protocol)( TCP ) 类似,是一种用于将信息包从一个点传输到另一个点的协议。在TCP的情况下,作为过程/传输的一部分,对数据包的成功传递进行验证,使其比UDP更可靠。
在UDP的情况下,没有验证过程,因此您将不知道数据包是否成功传输或接收且没有错误。因此,它是一个很容易使用的协议,但它不可验证或无法验证。
Linux 配置(Linux Configuration)
Linux操作系统 中有几个可用的配置文件。
例如,如果您在Linux机器上运行Apache服务器,则Apache配置文件很重要。这些文件让Apache Web 服务器知道域发生了什么,更具体地说,是该服务器上托管的站点。
有时配置文件被标记为 httpd.conf。有时它被标记为 apache.conf。或者它可能是一个完全不同的标签/名称。您可能会在一台服务器上的一个位置找到配置文件,而有时它们在另一台服务器上的完全不同的位置。
幸运的是,有一些有用的命令可以帮助定位特定的配置文件。例如,您可以键入以下内容来定位“ httpd.conf ”配置文件(如果存在):
find / -name “httpd.conf”

第一个词“find”,让Linux知道您正在使用什么命令/实用程序,在本例中是“find”实用程序。命令行的第二个组成部分是“/”,它让 find 实用程序知道它应该从服务器的根级别开始搜索路径。
如果你正在寻找一个更具体的位置,你可能有类似“/etc”的东西让Linux知道从 etc 目录开始并遵循该路径。通过提供特定的路径/位置,您可以潜在地加快该过程,因为Linux不必在多余的地方进行搜索。
“ -name ”选项让Linux知道您在文件或目录的名称中要查找的内容。将名称包含在引号中会很有帮助,您还可以在搜索时使用星号 ( * ) 作为通配符。
“/etc”目录/路径中的配置文件和目录的一些示例包括:
- pam.d –包含与身份验证模块相关的实用程序的目录。例如,在那里可以找到“Su”和“sudo”。
- sysconfig – 包含计算机功能的目录,如电源管理、鼠标等。
- resolv.conf – 一个有助于域名服务器功能的文件,如果Linux机器正在以该容量使用。
- services – 该文件包含(services)Linux机器上可用的连接(即开放端口) 。

如果您想知道是否有任何文件、路径或实用程序已过时或已弃用,请使用手册页进行检查。这是密切关注最新内容和已更改内容的有用方法。
了解 Linux 文件系统(Understanding the Linux File System)
在许多Linux 发行版中,可以在“ (Linux distributions)etc/sysconfig ”路径下的 network-scripts 目录中找到配置文件。如果它们不在那里,则很可能存在类似的位置/路径。在这种特殊情况下存在的文件显示在下面的屏幕截图中。
正如您将在下面的屏幕截图中看到的那样,有两个配置文件。它们中的每一个都根据各自的接口进行标记(即 ifcfg-eth0)。
配置文件前面有“ ifcfg ”,它替换了ifconfig 命令(ifconfig command)(以及成为接口文件名的一部分)。也就是说,由于 ifcfg 与IPv6不兼容,它现在也已被替换。
两个接口引用(ifcfg-eth0和ifcfg-lo)指的是特定类型的接口。Linux开发人员在这方面很有帮助,以文件名的形式提供定义和方向。对于以“ eth0(eth0) ”结尾的接口,它是通过“以太网”连接或具有以太网能力的接口。

使用字母“ eth ”为您指明了正确的方向。“eth”后面的数字提供了设备的编号。因此,下一个以太网设备可能类似于“ ifcfg-eth1 ”等等。
以“lo”结尾的文件名指的是“环回”接口。它也被称为“ localhost ”。这是一个网络连接,在技术上不是真正的网络连接。它只是允许进程在设备上进行通信,而无需通过网络进行通信。在考虑这个特定界面时,请考虑“虚拟”。
所有Linux发行版都能够具有环回(或本地主机),并且通常默认设置为一个。他们使用以“-lo”结尾的接口。本地主机的 IP 地址通常是 127.0.0.1。在许多情况下,环回虚拟接口可用于测试连接并排除其他潜在的网络问题。
文件(The Files)
有不同的方法可以编辑配置文件(以及查看它们)。一种方法是使用通过命令“ vi ”访问的“ (vi)vi 编辑器(vi editor)”,后跟文件名。在这种情况下,当键入“ vi ifcfg-eth0 ”(不带引号)时,他们能够查看该特定接口(eth0)的网络信息。
但是,最好按照传统方式进行操作,并按照 ifcfg 手册页中的网络配置说明进行操作。
对于非技术人员来说,这也可能更容易。使用 vi 编辑器确实需要注意细节,因此如果您注重细节(或者您已经是程序员或系统管理员),vi 编辑器可能是处理Linux配置文件时的最佳解决方案。

在访问手册页时,我们可以查看有关替换 ifconfig 脚本的 ifcfg 脚本的信息(如上面的手册页屏幕截图所示)。此外,在查看Linux发行版中的接口列表时,我们会注意到 ifup 和 ifdown 命令。这些也可以在他们的手册页中查看。
手册页的屏幕截图如下图所示。正如您将在手册页中看到的那样,在 Linux 上的 TCP/IP 文件的设置和配置中可以查阅(和修改)额外的LinuxTCP/IP文件(以及获取这些文件的路径)(Linux)。

如果您使用 vi 编辑器等命令行文本编辑器查看配置文件,您会注意到一些已定义的选项。例如,在查看网络接口时,您可能会看到全部大写的单词,然后是等号 (=),然后是另一个单词。
例如,可能有一个指令是“ ONBOOT ”,它可能会说“ONBOOT=yes”作为配置选项的示例。还有其他几个配置点和选项。例如,另一个是NETMASK。
如果您看到配置指令“ NETWORKING ”,则应在后面加上“yes”。如果后面是“否”,则可能表示存在问题,因为这表明网络接口未激活用于联网。
以下是纠正刚刚描述的情况的分步过程:
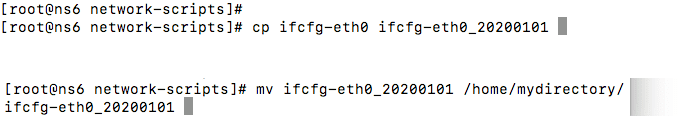
- 为安全起见,制作配置文件的副本。有几种方法可以做到这一点。最简单的方法之一是使用命令窗口。
输入:cp ifcfg-eth0 ifcfg-eth0_20200101
然后在下一行输入:mv ifcfg-eth0_20200101 /home/mydirectory/ifcfg-eth0_20200101
这会将您刚刚创建的文件副本移动到您用于备份的目录中。
- 现在您已经备份了配置文件,是时候更改该配置文件了。如果您使用 vi 编辑器,您将键入以下内容:
vi ifcfg-eth0
执行此操作后,该文件将在终端/命令应用程序中打开(类似于触发它时打开手册页的方式)。
打开配置文件后,您将查找包含“ NETWORKING=no ”的行并删除该行或将其更改为“NETWORKING=yes”。这可以通过“ cw” vi 编辑器中的指令。通过输入一个正斜杠,你告诉 vi 编辑器你正在搜索一些东西。在这种情况下,您让编辑器知道您正在搜索“NETWORKING”,当找到它时(将鼠标指向该位置),您可以使用右箭头键移动到“no”一词。
当你遇到“no”这个词时,停在“n”上并输入“ cw ”,这样你就可以将“no”改为“yes”。“cw”代表更改词,Linux允许您将整个词从一个词(“no”)更改为另一个(“yes”)。如果您只想更改一个字母,您可以使用“r”来替换一个字母或字符。
下面的屏幕截图显示了这个过程。
- 保存配置文件后(即键入 esc 退出INSERT模式,然后键入双 Z 保存文件),是时候重新启动服务或计算机了。这可以通过几种不同的方式来完成。重新启动计算机的一种方法是键入以下命令行:
shutdown -r now
关闭命令告诉Linux机器关闭。-r 选项告诉命令它不仅仅是关闭,而是重新启动并立即执行。
提示:如果您想知道计算机或服务器何时完成重启,请键入“ping”,然后键入计算机/服务器的公共 IP 地址(或托管在(Tip:)Linux服务器上的站点的域名)。
通过使用 ping 命令,您将看到服务器不可“ping”(在重新启动期间发生),然后当服务器成功重新启动时,ping 将以肯定响应响应,表示重新启动成功。
以下是一些有助于说明上述列表中步骤的图像。
第1步:
第2步:


提示:(Tip:)请记住,服务器世界中没有什么是单一的。例如,您可以更改特定接口(在本例中为 eth0)的配置,但这可能只是网络上的一个接口,并且可能受(或影响)另一台服务器的影响。
因此,在上面的示例中,通过重新启动服务器,它会触发网络设备也重新启动。这不是该接口的唯一选项,但该接口会受到重启命令的影响。
/etc/hosts File(s)
/ /etc/hosts文件可能存在也可能不存在。如果它确实存在,它可能会或可能不会在配置中使用。例如,您可能有一个不同的系统来处理主机配置,而不是直接管理文件。此外,主机文件本身也会有所不同。例如,IPv4和IPv6处理配置的方式不同,如下图所示。

Configuration Files; Locations/Paths; Terms; and More
一些其他有用的文件名和文件位置是:
- /etc/sysconfig/network-scripts/(配置文件路径)
- /etc/sysconfig/network-scripts/ifcfg-eth0(配置文件)
- /etc/hosts(配置文件)
- /etc/resolv.conf(带有名称服务器信息的配置文件)
在许多情况下,系统或服务器软件会自动创建配置文件。此外,如果使用DHCP,网络配置的其他方面也会即时计算,因为在这种情况下不使用静态 IP 地址。
以下命令行 (CL) 命令曾(或正在)在大多数 Linux 发行版中使用。如果它们已过时或不推荐使用,则会列出替换命令。
- 路线(route)(obsolete / deprecated):用于显示和编辑路线。替换为ip route。
- hostname:用于显示或操作和编辑机器的主机名。
- netstat:查看网络连接、路由表、接口统计信息、多播成员资格等。
- arp : ( obsolete / deprecated ) 用于显示IPv4信息;特别是网络邻居缓存。IPv6已成为网络地址,取代了由句点分隔的四个数字的IPv4集合。鉴于这些变化,这个过时的命令已被ip neigh取代。
- ip:IP 不仅代表“互联网协议”和终极WAN(广域网),而且还是一个实用程序,允许系统管理员或计算机用户查看TCP/IP参数并将它们设置为需要。
- tc:这代表“流量控制”,是一个帮助管理Linux机器上的入站和出站流量的实用程序。
配置工具:GUI Vs。命令行 (CL)(Configuration Tools: GUI Vs. Command Line (CL))
为了提供参考,以下三个图像显示了一个图形用户界面 ( GUI ) 机制来处理网络配置,包括TCP/IP。
第一个图像是Apple Mac GUI(System Preferences > Networking),后两个图像是Windows 操作系统(Windows Operating System)的图像(尽管版本不同)。正如您在屏幕截图中看到的那样,它可以通过Microsoft 控制面板(Microsoft Control Panel)和网络连接访问。(Network Connections)



GUI 与文本编辑器或命令行 (CL) 的优缺点(Pros and Cons of GUI Versus Text Editor or Command Line (CL))
虽然许多人更喜欢图形用户界面 ( GUI ),因为它们易于使用、视觉呈现和整体简单,但了解配置文件(在这种情况下与网络相关)很有帮助,以便您可以排除故障并纠正任何问题。
您可能想先获取GUI,但它有助于充分了解信息……以防万一。此外,有些操作系统不一定有GUI(或者还没有),所以又一次。做好准备是有帮助的。
在下一节中,我们将介绍配置文件以及如何访问、更新它们,以及文件和实用程序的管理。
Linux 命令行 (CL) 工具、实用程序、脚本和守护程序(Linux Command-Line (CL) Tools, Utilities, Scripts, and Daemons)
有许多可用于Linux发行版的工具。同样(Again),与其他命令一样,这些工具在不同发行版中的使用方式也有相似之处(和不同之处)。在某些情况下,工具是可用的,但需要先安装,并且安装过程往往会有所不同。
命令行工具通常被称为shell并且在早期被称为终端(terminal)。它还有其他术语,但一般来说,它是一个允许用户通过在窗口中键入命令来访问操作系统的应用程序。
让我们看几个例子。第一个来自Windows操作系统,Windows用户可能看起来很熟悉。通过键入CMD打开该工具(如下面的屏幕截图所示)。
第二个屏幕截图是预装在大多数Apple计算机上的名为Terminal的应用程序的屏幕截图。(Terminal)



NSLookup (nslookup)
对于nslookup,ns代表名称服务器(nameserver),命令的查找(lookup)部分是信息的“查找”。所以,这个工具的名字告诉我们的是,它会通过名称服务器查找通常可用的信息。
NSLookup是一个方便的工具。在这种情况下,我们使用它来查找有关 eBay 的信息。为此,我们键入“nslookup ebay.com”,我们会看到类似于下图所示的信息。
该命令显示在屏幕截图的顶部(在模糊的私人信息之后)。然后,该请求的输出(nslookup)如下所示,其中包含诸如服务器(Server)(公共 IP 地址)、特定IP 地址(IP address)等 信息。

交通管制 (tc)(Traffic Control (tc))
另一个工具是“交通控制”工具(也称为“tc”)。它是一种允许调度和处理数据包的工具。
该命令告诉您数据包如何(how)通过网络移动。方式(how)方面包括对时间、速度、设备等问题的答案。这是使用交通控制(Traffic Control)(tc) 的命令行 (CL) 表示:

虽然对某些人来说可能看起来像“胡言乱语”,但命令行中的每个单词都代表着重要的东西。这是清单:
- tc:这是工具,在本例中为“交通控制”(又名“tc”)。这告诉命令行应用程序/软件使用哪个Linux工具。
- qdisc:这个缩写代表排队规则(queuing discipline),是描述简单调度程序的另一种方式。
- add:由于我们正在构建一个配置(是的,从技术上讲是一个文件),我们告诉工具我们正在添加(adding)到控件中。
- dev eth0:“dev”指的是“设备”,让工具知道我们即将定义设备。在这种情况下,“eth0”是对设备的引用。您会注意到这类似于设备标签的图形用户界面 ( GUI ) 中显示的内容。(GUI)
- root:这告诉工具我们正在从根级别或出口修改出站流量。
- netem:这个词代表短语“网络模拟器”。虽然它可能不是硬件网络,但它模拟的是相同的。这类似于Parallels软件模拟Apple计算机的Windows软件的方式。当然,它是一个完全不同的软件,但它是仿真软件,就像 netem 仿真网络一样。在这种情况下,netem 代表WAN(广域网),而不是LAN(局域网)。
- delay:这个词告诉 tc 工具我们正在修改事务的“延迟”组件。
- 400ms:我们已经告诉工具我们正在影响延迟,但现在我们需要定义我们对延迟的影响程度。在这种情况下,它是 400 毫秒。
网络管理员(Network Manager)
网络管理器(Network Manager)的目的是简化和自动化您的网络配置。对于DHCP用户,网络管理器(Network Manager)可以获取 IP 地址、取代默认路由并自动换出名称服务器。
用于使用网络管理器(Manager)的 nmtui 工具在大多数(但不是全部)Linux发行版中都可用。另外,请记住,有些工具是“可用的”但不可用。换句话说,有一些工具和守护程序需要安装,而不必预先安装在相关的Linux发行版上。
其他网络主题(Other Networking Topics)
TCP/IP的许多方面特别令人着迷,尤其是在处理Linux发行版时。不要(Don)忘记在Linux安装中您有可用的手册页(也称为手册页)。因此,虽然这可能看起来像是一份不相关的不应该做的事情的列表,但您始终可以使用手册页来确定您应该做什么。
Linux 作为路由器(Linux as the Router)
如今,大多数人使用专用于路由任务的硬件(即路由器)来管理网络路由任务(manage the network route task)。
很多时候,这是因为路由器是家庭或办公室互联网套餐/合同的一揽子交易的一部分。客户通常会被抓到每月(或每年)支付租金/租赁费或不得不购买路由器。
不管如何处理, Linux(Linux)几乎不需要作为路由器运行,即使它能够作为路由器运行。上面描述的场景为Linux(Linux)创建了一个几乎伪弃用的情况,但这并不意味着Linux完全退出了游戏。如果需要,可以将Linux服务器设置为硬件(和后续软件)路由器。
IP 路由(以前的“路由”)(IP Route (Formerly “Route”))
下图显示了“Route”手册页的屏幕截图以及该工具可能使用的指令。


SNORT——入侵者检测系统(SNORT – An Intruder Detection System)
Snort 软件(Snort Software)是一个开源入侵检测系统(Intrusion Detection System)( IDS ),最初由Martin Roesch 开发,后来被 Cisco Systems 收购(Martin Roesch and since acquired by Cisco Systems)。它根据利用网络TCP/IP层的规则运行。定义这些规则可以识别入侵以保护网络。
How to Set Up Linux > TCP/IP Settings for Linux
以下迷你教程将帮助您完成在Linux(Linux)世界 中可能遇到的一些常见任务。
请记住,时代变化很快,因此使用您的手册页以及Google中的搜索来验证以下步骤并确保没有任何其他工具可以更好地完成这项工作会很有帮助。在撰写本文时,情况并非如此。
教程 01:为 Linux 机器分配静态 IP 地址(Tutorial 01: Assigning a Static IP Address to a Linux Machine)
您应该问的第一个问题是计算机/服务器是否需要静态 IP 地址(不会更改的)或可更改的 IP 地址(如DHCP – 动态主机配置协议(DHCP – Dynamic Host Configuration Protocol))。如果这是您的个人计算机(不是服务器),您可能正在使用DHCP访问 Internet。
这意味着您不必为您的计算机分配静态 IP 地址而烦恼。您的互联网服务提供商 ( ISP ) 和提供/租用的任何硬件都会自动即时计算 IP 地址,以使您能够连接到互联网。换句话说,如果您不需要静态 IP 地址,那么动态更改 IP 地址就可以满足您的非服务器计算机。
如果您有一台服务器并且需要其他人可以访问它(即在您的家外;WAN/internet;非 LAN),那么您将需要一个静态 IP 地址,以便将您使用的域映射到它通过分配给域的主机名称服务器,或通过静态 IP 地址直接访问。
如果没有人需要在家外访问您的计算机或服务器,那么更改 IP 地址(动态;非静态)就可以了,因为没有人使用静态 IP 地址。
注意:有些人使用DHCP IP地址进行公共访问(是的,即使作为服务器),但是,
- 它需要一个非常有技术头脑的人才能这样做,所以它并不常见。
- 它比静态 IP 地址更难维护(由于其不断变化的性质)。
如果您确实需要静态 IP 地址,请继续并按照此处的步骤操作。如果没有,您可以跳过本节。

如您所见,该命令(如上所示)在行首包含“sudo”。虽然可以使用“su”命令(超级用户)并以超级用户身份登录,但使用“sudo”只能以超级用户身份运行该命令。
另一种方法,以超级用户身份登录,允许以超级用户身份完成所有任务,从而更方便地做需要做的事情。
但是,随之而来的是安全风险,这就是为什么简单地使用 sudo 启动命令并允许应用程序请求密码(根据需要)以作为该任务/命令的超级用户完成命令更安全的原因。
选择是你的,应该基于任何更容易的方法。以下屏幕截图所示的文件可通过以下命令访问:
sudo vi /etc/sysconfig/network-scripts/ifcfg-eth0
在使用该命令之前,会验证网络设备号( eth0 )以确保它是正确的。您还记得,Linux配置是在接口文件中管理的,因此在编辑配置文件之前,必须从该文件中验证接口编号。
需要注意的配置文件的另一个方面是“静态”一词的使用。由于我们要添加静态 IP 地址,因此让配置文件知道是这种情况很重要。
出于说明原因,在下面的屏幕截图中添加了注释,但不应包含在您的配置文件中。此外,在某些Linux发行版中,引号是必需的。在这个特定的配置文件中,自动创建的配置文件中没有引号,因此趋势继续并且没有添加引号。

以下屏幕截图显示了文件的实际显示方式,删除了注释和多余的空格。

要编辑的下一个(也是最后一个)配置文件可通过键入以下内容访问:
sudo vi /etc/resolv.conf
在该文件中,可以添加(或修改)名称服务器。这些名称服务器应该与刚刚修改的其他配置文件匹配。在这种情况下,位于/etc/sysconfig/network-scripts/ifcfg-eth0(上面的屏幕截图)。
将使用的措辞是“名称服务器”。因此,设备配置文件显示DNS1=8.8.8.8时,resolv.conf 文件应显示名称服务器 8.8.8.8(nameserver 8.8.8.8)。
DNS2=4.4.4.4的对应项将在 resolv.conf 文件中显示为名称服务器 4.4.4.4 。(nameserver 4.4.4.4 )
粗略地说,上述步骤适用于Red Hat Linux发行版,但不能保证它在未来会随着技术的变化而起作用。这就是为什么应该测试和验证配置。
配置完成后,使用上述首选方法重新启动网络接口。这将应用更改。如果测试静态 IP 地址也很有帮助。您可以通过尝试从另一台设备(最好在不同的网络上)连接到该公共静态 IP 地址来做到这一点。
您也可以打电话给朋友或同事,让他们尝试从另一个地理位置(和不同的网络)连接到静态 IP 地址。
教程 02:网络 IP 别名(Tutorial 02: Network IP Aliasing)
可以为一张网络接口卡 ( NIC(NIC) )分配多个 IP 地址。这被称为网络 IP 别名(Network IP Aliasing),因为只有一个 IP 是实际的,所以额外的 IP 地址是同一张卡的别名。为了分配 IP 地址,请使用教程 01 中描述的您最喜欢的分配 IP 地址的方法。
并不是它必须是静态的,而是为了使用Network IP Aliasing分配多个 IP 地址,必须使用静态 IP 分配 IP 地址。
教程 03:更改 Linux 机器的主机名(Tutorial 03: Change Host Name of the Linux Machine)
使用您喜欢的编辑器按照以下步骤更改Linux机器的主机名:
1. 通过在命令行应用程序中键入以下内容来修改主机名配置文件:
sudo vi /etc/hostname
无论您在该配置文件中的何处看到旧主机名,都将其替换为新主机名。
2. 通过在命令行应用程序中键入以下内容来修改主机配置文件:
sudo vi /etc/hosts
无论您在该文件中的何处看到旧主机名,都将其替换为新选择/指定的主机名,方法与上述第一步中使用主机名配置文件的方式相同。(hostname)
3. 重新启动服务器或Linux计算机。执行此操作的一种方法(取决于您的Linux发行版)是在命令行应用程序中键入以下内容:
sudo shutdown –r now
需要重新启动才能使更改生效。
教程 04:启用和禁用您的 NIC(Tutorial 04: Enable and Disable Your NIC)
在Linux(Linux)中通过命令行可以做的最有趣的事情之一是启用或禁用以太网(Ethernet)连接。
为此,请从以下两个中键入适当的命令:
sudo ip link setup
sudo ip link setdown
对于较旧版本的Linux,您可以运行 ifconfigup 或 ifconfigdown,但这些命令可能在较新的Linux发行版中已被弃用或过时。在这种情况下,较新的 ip 命令更可取。
教程 05:启用网络转发(Tutorial 05: Enable Network Forwarding)
您的Linux操作系统能够连接各种网络,并且可以充当路由器。您需要做的就是uncomment the net.ipv4.ip_fporward=1 line ,这将使您能够转发 IP 地址。
必要的配置文件通常存储在/etc/sysctl.conf:
有关如何设置的示例,请查看“How to enable IP forwarding on Linux (IPv4 / IPv6)”。
如果您使用DHCP(DHCP) (而不是静态 IP 地址)设置Linux服务器,您可以选择一种网络转发形式。这并不常见,但在这里引用,因为它是可行的,并且它代表了某人可能倾向于这样做的情况。
教程 06:通过 Shell 的远程命令(Tutorial 06: Remote Commands Via Shell)
如果您需要访问Linux服务器并且该服务器与您的地理位置不同,您可能需要使用远程命令来访问该远程Linux服务器。
对于程序员或系统管理员来说,“远程进入”服务器是很正常的事情。
最流行的方法之一是使用“ ssh ”命令,让命令行应用程序知道您想要安全地访问Linux服务器,即使您是通过不安全的连接进行的。
除了使用“ssh”命令外,您还需要提供连接位置和连接方式的信息(以及其他可用选项)。

您可以使用域名来访问Linux服务器,甚至可以使用公共静态 IP 地址。名称或 IP 地址告诉 ssh 命令它正在访问什么以及在哪里可以找到它。
其他选项可能包括用于登录远程服务器的用户名。如果没有定义该选项,可能会请求它,但它也是与 ssh 命令同时定义它的选项。
例如:
ssh username myserver.com
密码也可以配置到命令中,但出于安全原因,建议您在与远程服务器连接时输入密码。
为什么?如果密码以纯文本形式输入到命令中,则下一个人使用同一台计算机可以访问该密码,并且他们可以访问该密码。
出于其他安全原因,您可能希望通过特定端口访问Linux服务器。(Linux)通过指定一个可能使用的端口,您可以阻止其他端口并防止黑客企图或DOS(拒绝服务)攻击。
ssh 有许多不同的配置点。其中一些列在shellhacks.com 上(shellhacks.com)。
教程 07:网络监控工具(Tutorial 07: Network Monitoring Tools)
管理网络的一个重要组成部分是验证一切正常并继续正常工作。您可以通过网络监控来做到这一点。适应网络监控的工具各不相同,但最终实现了相似的目标。
Cacti就是这样一种网络监控工具。Cacti 是一个开源的网络监控工具。Cacti监控网络并提供已记录内容的图形表示。这有助于用户(尤其是新手)确定可能存在问题的地方。
前端可以容纳大量用户,有时被托管服务用于在下图中显示实时带宽信息和其他数据。

数据可以通过任何外部脚本或命令输入Cacti 。Cacti将通过 cron-job 将数据汇集在一起,并在将其呈现为前端用户图之前填充您的MySQL数据库。(MySQL)

要处理数据收集,您可以向 cacti 提供任何外部脚本/命令的路径以及用户需要“填写”的任何数据。然后Cacti(Cacti)将在 cron-job 中收集这些数据并填充MySQL数据库。
(Cacti)对于想要监控网络使用情况并为消费者提供易于理解的视觉效果的网络管理员来说,Cacti是一个有用的工具。Cacti可以在cacti.net免费下载。该网站包含安装和配置网络监控工具的文档。
您可以尝试的Cacti替代品包括Solarwinds NPM、PRTG和Nagios。Solarwinds将支持SNMP以及ICMP/Ping、WMI、Netflow、Sflow、Jflow和IPFIX等等。预建模板、图表和警报可帮助您快速开始监控网络。
PRTG免费提供多达一百个传感器。它具有与Solarwinds类似的功能,以及适用于(Solarwinds)智能手机(Smartphones)、平板电脑、ipad的灵活警报和应用程序。
Nagios拥有您在(Nagios)Cacti中可以找到的所有工具,但确实需要更多配置。有很多插件可供选择。作为最古老的网络管理和监控工具之一,它享有盛誉。但是,您将不得不亲自维护其配置文件。
How To Set Up & Configure TCP/IP Files On Linux (TCP/IP Settings For Linux)
Even non-geeks hаve likely heard of “TCP/IP” but does everyone know what it is or how to configure it on a Linux server using the command line?
It helps to define basic terminology first. At the very least, it allows you to develop a framework on which to build your understanding. TCP/IP is no exception.
This section on terminology is not an exhaustive list. It’ll give you a basis on which to start your journey into understanding networking and how to configure TCP/IP files on Linux.

The *Nix World
Have you ever wondered what *nix means? What about how Unix and Linux are related (let alone all of the various versions of each)?
*nix is a method of referencing Linux and/or Unix (or any distribution) using a wildcard (the asterisk) to do so.
*Nix was developed in the late 1960’s. AT&T Bell Labs developed Unix at around the same time. hrough various iterations and developments, Linux was also born.
The result of these parallel innovations is that once you learn how to perform installations on one server via the command line, you’ve learned a skill that’s likely compatible with many other tasks on a variety of Unix or Linux servers.
Man Pages – Information at Your Fingertips
Much like Google, Linux has its own set of search and research tools that enable users to find the resources they need. Those resources are known as, “man pages.” When you are logged into a Linux server (or Linux-based operating system), you can open the command-line application and type in what you would like to research, like typing in a search term in an interactive documentation file.
If you pick a topic you want to research, like a Linux utility, tool, daemon, script, you can look that up by typing “man” and then the word. You will learn how to do this later in this article.
Man pages are easy to use. Just start typing a couple of words and the Linux OS will begin returning the information to you. If there’s no man page for a particular topic Linux will tell you that.

For the most part, man pages are reasonably accurate for the software version on which they appear. For example, if you are logged into a Linux server that’s 10 years old, the man page displays information relative to that version (and age).
Man pages are easy to use and accurate, but there are a couple of caveats. Let’s illustrate those caveat(s) via images.
In the image below, the man page for ARP indicates that ARP is obsolete (under the “notes” section) and that one should look up ip neigh instead. It would seem, by that notation, that one may want to type “man ip neigh” to access information about the replacement tool/protocol.
However,, typing “man ip neigh” does not look up the man page for “ip neigh”. Instead, it’ll look up two man pages… one for “ip” and the other for “neigh.”
While it’s true that you’ll get a man page if you type “man ip neigh,” unless you are paying close attention, you may miss that it’s not actually what you were looking for.
You could add a dash (even though that isn’t what shows in the man page when referencing the replacement tool)… So, if you add a dash and type “man ip-neigh” that also works fine but it isn’t correct either.
You might try typing “man ip-neighbour” (note the British spelling). When you type that particular phrase, you’ll see the correct man page for replacing the ARP man page (or replacing the ARP protocol). The bottom line is this: If you can’t find what you need, try using different combinations until you get the desired man page.

As an example, try looking up the man page for the nslookup tool. You do this by typing “man nslookup”. When you do that, you’ll see a man page that looks similar to the image/screenshot below. You’ll learn all you’d want to know about the nslookup tool.
After the man page pops up on your screen you can scroll down, read, apply, test, and even close out the man page (by typing the letter “q” and letting the man page automatically close).
If you request a man page that doesn’t exist, Linux will provide you with the feedback that there’s no entry for that man page and to try another one.

IPv4 and IPv6
Both IPv4 and IPv6 are technically the same, but they don’t appear the same to us humans. They’re a means of identifying machines or devices on a local area network (LAN). They’re private in the way that they identify the devices in the LAN.
IPv4 uses numbers separated by dots/periods. Most of us are familiar with the type of IP addresses we see for computers connected to our private networks using the IPv4 format.
Computers on a network also have an IPv6 address, but it looks different. IPv6 is composed of alphanumeric characters separated by colons ( : ).

So what are the differences between IPv4 and IPv6? Think of it like a network name. One is like the first name and the other is the last name. Both names point to the same person (or in this case, a computer). Just as we generally have a different first name compared to our last name, the IPv4 “name” will be different from the IPv6 “name” even though they both point to the same machine.
Carla Schroeder has written an easy-to read and useful article about IPv4 and IPv6.
Root Access on a Linux Server (and su and sudo)
For many of the tasks that need to be completed, root access (a.k.a. Administrator or superuser) is required. That’s because many of these utilities and apps are sensitive enough that they’re restricted for security reasons.
An alternative solution to logging in as root or triggering superuser access (su) is to prepend a command with “sudo” telling the Linux machine that that particular command needs to be run as superuser/root, but that subsequent commands do not (unless also prepended with the “sudo” directive).
In cases where “sudo” is used and prepended to the command, Linux will request the su password in order to authenticate the superuser identity and permissions.
Networking Protocols
there are many different protocols to consider when discussing Linux. The two protocols that are primary to this article are TCP and IP.
Transmission Control Protocol (TCP)
Transmission Control Protocol, more often referred to as TCP, is a protocol used for the transmission of packets, just as the name describes.
See below for an explanation of various tools, including the Linux tool called Traffic Control (tc).
TCP directs the Linux operating system on how packets should move from one place to another. It also controls network traffic and directs the transmission of packets of information (like folders of data moving from one place to another).
This is why the protocol is called Transmission Control Protocol (TCP).
Internet Protocol (IP)
Internet Protocol is commonly referred to by its acronym, IP.
In the case of the IP you have a wider area (the Internet) to transmit packets. It’s like having a wider, longer, and more travelled super highway… called the internet. While TCP controls the movement of packets across a network, IP controls the movement of packets across the internet.

ICMP Protocol
ICMP stands for Internet Control Messaging Protocol. While it’s a protocol that’s available in most Linux distributions, it may not be available on all Linux distributions. This was evidenced by the lack of a Man page within a current Centos installation.
At first glance, it may not seem like this particular protocol is that essential but in reality it is. ICMP is responsible for providing error messages if/when a packet doesn’t properly reach its destination. ICMP is essential for receiving status updates on the delivery (or receipt) of the packets of information being transmitted.
User Diagram Protocol (UDP)
User Diagram Protocol (UDP), like Transmission Control Protocol (TCP), is a protocol for the transmission of packets of information from one point to another. In the case of TCP, as a part of the process/transmission, there’s a verification of successful delivery of the packet(s), making it more reliable than UDP.
In the case of UDP, there’s no verification process so you won’t know whether the packets were transmitted or received successfully and without error. As such, it’s an easy enough protocol to utilize but it’s not verifiable or able to be authenticated.
Linux Configuration
There’s several configuration files available in the Linux operating system.
For example, if you’re running an Apache server on your Linux machine, the Apache configuration files are important. Those files let the Apache web server know what’s going on with the domain and more specifically, the site that’s hosted on that server.
Sometimes the configuration file is labeled as httpd.conf. Sometimes it’s labeled as apache.conf. Or it could be a completely different label/name. You may find the configuration files in one location on one server, and other times they’re in a completely different location on another server.
Fortunately, there are helpful commands that may assist in locating specific configuration files. For example, you can type the following to locate the “httpd.conf” configuration file, if it exists:
find / -name “httpd.conf”

The first word, “find”, let’s Linux know what command/utility you’re using, which in this case is the “find” utility. The second component of the command line is the “/” which lets the find utility know that it should be searching the path starting from the root level of the server.
If you were looking in a more specific location, you may have something like “/etc” to let Linux know to start in the etc directory and follow that path. By providing a specific path/location, you can potentially speed up the process, because Linux doesn’t have to search in places that are redundant.
The “-name” option lets Linux know what you’re looking for in the name of the file or directory. It’s helpful to include the name in quotation marks, and you can also use an asterisk ( * ) as a wild card when searching.
Some examples of configuration files and directories in the “/etc” directory/path include:
- pam.d – a directory that contains utilities related to authentication modules. “Su” and “sudo” are found there, as an example.
- sysconfig – a directory that includes functions of the computer, like power management, mouse, and more.
- resolv.conf – a file that aids in the functionality of the domain name server, if the Linux machine is being used in that capacity.
- services – this file contains the available connections (i.e. open ports) available on the Linux machine.

If you’re wondering if any files, paths, or utilities are obsolete or deprecated, use the man pages to check. This is a helpful way to keep tabs on what is current and what has changed.
Understanding the Linux File System
In many Linux distributions, configuration files are found in the network-scripts directory under the “etc/sysconfig” path. If they’re not located there, it’s likely that there’s a similar location/path. The files that are present in this particular case are shown in the screenshot below.
As you’ll see in the screenshot below, there are two configuration files. Each of them are labeled according to their respective interfaces (i.e. ifcfg-eth0).
The configuration files are preceded by “ifcfg” which replaces the ifconfig command (as well as becoming a part of the interface file name). That said, it has now been somewhat replaced as well since the ifcfg is not compatible with IPv6.
The two interfaces references (ifcfg-eth0 and ifcfg-lo) refer to specific types of interfaces. Linux developers were helpful in this area, providing definition and direction in the form of file names. In the case of the interface ending in “eth0”, it’s an interface that’s connected via “ethernet” or has ethernet capability.

The use of the letters “eth” point you in the right direction. The number that follows “eth” provides the number of the device. So, the next ethernet device may be something like “ifcfg-eth1” and so forth.
The file name that ends in “lo” refers to a “loopback” interface. It’s also referenced as the “localhost.” This is a network connection that isn’t technically a real network connection. It simply allows processes to communicate on the device without communicating over the network. Think “virtual” when thinking about this particular interface.
All Linux distributions are capable of having a loopback (or localhost) and are usually set up for one by default. They use an interface that ends in “-lo.” The IP address for the localhost is usually 127.0.0.1. In many cases, the loopback virtual interface can be used to test connections and rule out other potential network issues.
The Files
There are different ways to edit configuration files (as well as view them). One method is to use the “vi editor” that’s accessed via the command “vi” followed by the filename. In this case, when one types “vi ifcfg-eth0” (without the quotation marks) they are able to view the network information for that particular interface (eth0).
However, it would be more advisable to do it the traditional way and follow the network configuration instructions found in the man page for ifcfg.
This may also be easier for the non-technical person. Using the vi editor does require a bit of attention to detail so if you’re detail-oriented (or you’re already a programmer or system administrator) the vi editor may be an optimal solution when working with Linux configuration files.

In accessing the man pages, we’re able to review information about the ifcfg script that replaced the ifconfig script (as shown in the above screenshot of the man page). Also, when looking at the list of interfaces in the Linux distribution, we notice the ifup and ifdown commands. Those, too, can be reviewed in their man page(s).
A screenshot of the man page is shown in the image below. As you will see in the man page, there’s additional Linux configuration files (and the paths to get to those files) that can be consulted (and modified) in the set up and configuring of the TCP/IP files on Linux.

If you use a command-line text editor like the vi editor to view the configuration file, you will notice some options that are defined. For example, in looking at the network interface, you may see words in all caps, followed by an equals sign (=), and then another word.
For example, there may be a directive that’s “ONBOOT” and it may say “ONBOOT=yes” as an example of a configuration option. There’s several other configuration points and options as well. For example, another one is NETMASK.
If you see the configuration directive, “NETWORKING,” it should be followed by a “yes.” If it’s followed by “no” it may represent a problem because that would indicate that the network interface is not activated for networking.
Here is a step-by-step process to correcting the situation just described:
- Make a copy of the configuration file, to be safe. There are a few ways to do this. One of the easiest is with the command window.
Type: cp ifcfg-eth0 ifcfg-eth0_20200101
Then on the next line, type: mv ifcfg-eth0_20200101 /home/mydirectory/ifcfg-eth0_20200101
This moves the file copy you just made to a directory you’re using for backups.
- Now that you’ve made a backup of the configuration file,, it’s time to make changes to that configuration file. If you’re using the vi editor, you would type the following:
vi ifcfg-eth0
After doing so, the file will open in the terminal/command application (similar to the way a man page opens when you trigger it).
Once the configuration file is open, you would look for the line that includes “NETWORKING=no” and delete that line or change it to “NETWORKING=yes”. This can be done with the “cw” directive in the vi editor. By typing a forward slash, you’re telling the vi editor that you’re searching for something. In this case, you let the editor know that you are searching for “NETWORKING” and when it’s found (directing the mouse to that location) you can use the right arrow key to move to the word “no”.
When you get to the word “no”, stop on the “n” and type “cw” allowing you to change the “no” to “yes.” The “cw” stands for change word and Linux allows you to change the entire word from one word (“no”) to another (“yes”). If you only wanted to change one letter, you could use an “r” to replace one letter or character.
The screenshots show this process below.
- After saving the configuration file (i.e. typing esc to get out of the INSERT mode and then a double Z to save the file), it’s time to restart the service or the computer. This can be done in several different ways. One method to reboot the computer is typing the following command line:
shutdown -r now
The shutdown command tells the Linux machine to shutdown. The -r option tells the command that it isn’t just a shutdown, but a reboot and to do it now.
Tip: If you want to know when the computer or server has completed the reboot, type “ping” and then the public IP address of the computer/server (or a domain name of a site hosted on the Linux server).
By using the ping command, you will see that the server is not “pingable” (which happens during the reboot) and then when the server successfully restarts, the ping will respond with a positive response, indicating a successful reboot.
The following are some images that help to illustrate the steps in the above list.
Step 1:

Step 2:


Tip: Keep in mind that nothing in the server world is singular. For example, you may change the configuration for a particular interface (in this case eth0) but that may be just one interface on a network and may be affected by (or affect) another server.
So, in the example above, by restarting the server, it will trigger network devices to also restart. This is not the singular option for this interface but this interface would be affected by a command to restart.
/etc/hosts File(s)
The /etc/hosts file may or may not exist. If it does exist, it may or may not be used in the configuration. For example, you may have a different system that handles host configurations, rather than managing the file directly. Also, the hosts file itself varies. For example, IPv4 and IPv6 handle the configuration differently, as you can see in the image below.

Configuration Files; Locations/Paths; Terms; and More
Some additional helpful filenames and file locations are:
- /etc/sysconfig/network-scripts/ (configuration file path)
- /etc/sysconfig/network-scripts/ifcfg-eth0 (configuration file)
- /etc/hosts (configuration file)
- /etc/resolv.conf (configuration file with nameserver information)
In many cases, system or server software creates the configuration files automatically. Also, if DHCP is used, there are other aspects of the networking configuration that are calculated on-the-fly, since static IP addresses are not used in that case.
The following command-line (CL) commands were (or are) used in most Linux distributions. Where they are obsolete or deprecated, the replacement command is listed.
- route (obsolete / deprecated): Was used to show and edit routes. Replaced by ip route.
- hostname: Used to display or amanipulate and edit the hostname of the machine.
- netstat: View network connections, routing tables, interface statistics, multicast memberships, etc.
- arp: (obsolete / deprecated) Used to be used to show IPv4 information; specifically the network neighbor cache. IPv6 has become the network address, replacing the IPv4 collection of four numbers separated by periods. In light of these changes, this obsolete command has been replaced by ip neigh.
- ip: Not only does IP stand for “internet protocol” and the ultimate WAN (wide area network”) but it’s also a utility that allows the system administrator or computer user the ability to view the TCP/IP parameters as well as setting them as needed.
- tc: This stands for “traffic control” and is a utility to help with managing the inbound and outbound traffic on the Linux machine.
Configuration Tools: GUI Vs. Command Line (CL)
To provide a point of reference, the following three images display a graphical user interface (GUI) mechanism to handle the configuration of networking, including TCP/IP.
The first image is the Apple Mac GUI (System Preferences > Networking) and the second two images are that of the Windows Operating System (though it varies from version to version). It’s accessed via the Microsoft Control Panel and Network Connections, as you can see in the screenshots.



Pros and Cons of GUI Versus Text Editor or Command Line (CL)
While many people prefer graphical user interfaces (GUI) because of their ease of use, visual presentation, and overall simplicity, it’s helpful to understand configuration files (in this case related to networking) so that you can troubleshoot and correct any issues.
You may want to grab the GUI first but it helps to be fully informed… just in case. Also, there’s some operating systems that do not necessarily have a GUI (or don’t have one yet) so again; it’s helpful to be prepared.
In the next section we’ll cover configuration files and how to access them, update them, as well as the management of the files and utilities.
Linux Command-Line (CL) Tools, Utilities, Scripts, and Daemons
There are many tools that are available for Linux distributions. Again, like other commands there are similarities (and differences) between how those tools are used in the different distributions. In some cases, tools are available but need to be installed first, and the installation process often varies.
The command line tool is often referenced as shell and in the early days, terminal. There are other terms for it but generally, it’s an application that allows the user to access operating systemsby typing commands in a window.
Let’s look at a couple of examples. The first one is from the Windows operating system and likely looks familiar to Windows users. The tool is openedby typing CMD (as shown in the screenshots below).
The second screenshot is that of an application called Terminal that comes pre-installed on most Apple computers.



NSLookup (nslookup)
In the case of nslookup, the ns stands for nameserver and the lookup portion of the command is a “look up” of information. So, what the name of this tool is telling us is that it’ll look up information generally available via a nameserver.
NSLookup is a handy tool. In this case, we are using it to look up information about eBay. In order to do so, we type “nslookup ebay.com” and we’re presented with information that’s similar to what’s shown in the image below.
The command is displayed at the top of the screenshot (after the blurred out private information). Then, the output from that request (the nslookup) is shown below that, with information such as Server (the public IP address), the specific IP address, etc.

Traffic Control (tc)
Another tool is the “Traffic Control” tool (also referred to as “tc”). It’s a tool that allows the scheduling and processing of data packets.
The command tells you how the packets move over a network. That how aspect includes the answers to questions like timing, speed, devices, and more. Here is a command line (CL) representation of the use of Traffic Control (tc):

While it might look like “gibberish” to some, each word in the command line represents something important. Here is the listing:
- tc: This is the tool, in this case “Traffic Control” (a.k.a. “tc”). This tells the command line application/software which Linux tool to use.
- qdisc: This abbreviation stands for queuing discipline and is another way of describing a simple scheduler.
- add: Since we are building a configuration (yes, technically a file), we are telling the tool that we are adding to the controls.
- dev eth0: The “dev” refers to the “device”, letting the tool know that we’re about to define the device. The “eth0,” in this case, is the reference to the device. You’ll notice that this is similar to what appears in a graphical user interface (GUI) for a device label.
- root: This tells the tool that we are modifying the outbound traffic from the root level, or egress.
- netem: This word represents the phrase, “network emulator”. While it may not be the hardware network, it’s emulating the same. This is similar to how the Parallels software emulates the Windows software for Apple computers. Granted, it’s a completely different piece of software but is emulation software in the same way that netem is emulating a network. In this case, netem represents a WAN (wide-area-network) as opposed to a LAN (local-area-network).
- delay: This word tells the tc tool that we’re modifying the “delay” component of the transaction.
- 400ms: We have already told the tool that we’re affecting the delay, but now we need to define how much we are affecting the delay. In this case, it’s by 400 milliseconds.
Network Manager
The purpose of the Network Manager is to simplify and automate your network configuration. For DHCP users, the Network Manager can obtain an IP address, supersede default routes and automatically swap out nameservers.
The nmtui tool for using your Network Manager is available in most, though not all, Linux distributions. Also, keep in mind that some tools are “available” and yet not available. In other words, there are some tools and daemons that need to be installed and do not necessarily come pre-installed on the Linux distribution in question.
Other Networking Topics
There are many aspects of networking and TCP/IP that are particularly fascinating, especially when dealing with a Linux distribution. Don’t forget that you have manual pages (a.k.a. man pages) available right within the Linux installation. So, while this may appear to be a sort of unrelated list of what you shouldn’t do, you can always use a man page to figure out what you should do.
Linux as the Router
These days, most people use hardware that’s dedicated to the task of routing (i.e. router) to manage the network route task.
Many times, that’s because routers are a part of the package deal with home or office internet packages/contracts. The customer is usually caught paying a rental/lease fee per month (or annually) or having to purchase the router.
However it’s handled, there’s little need for Linux to operate as a router even though it’s capable of functioning as one. The scenarios described above create an almost pseudo-deprecation situation for Linux, but that doesn’t mean Linux is out of the game entirely. It’s possible to set up a Linux server as the hardware (and subsequent software) router if you need to.
IP Route (Formerly “Route”)
The following image shows a screenshot of the man page for “Route” and the directives that are possible with that tool.


SNORT – An Intruder Detection System
Snort Software is an open source Intrusion Detection System (IDS) originally developed by Martin Roesch and since acquired by Cisco Systems. It operates on the basis of rules that utilize the TCP/IP layers of the network. Defining those rules identify intrusions to protect a network.
How to Set Up Linux > TCP/IP Settings for Linux
The following mini tutorials will help you with some common tasks that you may come across in the Linux world.
Keep in mind that times change quickly, so it’s helpful to use your man pages as well as searches in Google to verify the following steps and ensure that there aren’t any other tools that may do the job better. As of the writing of this article, that’s not the case.
Tutorial 01: Assigning a Static IP Address to a Linux Machine
The first question you should ask is whether or not the computer/server needs a static IP address (one that does not change) or a changeable IP address (like DHCP – Dynamic Host Configuration Protocol). If this is your personal computer (not a server), the chances are you may be using DHCP for your access to the internet.
What that means is that you don’t have to mess with assigning a static IP address to your computer. Your internet service provider (ISP) and any hardware provided/leased is automatically calculating an IP address on-the-fly to enable you to connect to the internet. In other words, if you don’t need a static IP address, a dynamically changing one is just fine for your non-server computer.
If you have a server and you need it to be accessible to others (i.e. outside your home; a WAN/internet; non-LAN) then you will need a static IP address so that either the domain that you are using is mapped to it via the hosting nameserver assigned to the domain, or accessible directly via the static IP address.
If no one needs to access your computer or server outside your home, then a changing IP address (dynamic; non-static) is just fine, because no one is using a static IP address.
Note: Some people have used a DHCP IP address for public access (yes, even as a server) but,
- It requires a very technically-minded person to do so, so it’s not as common.
- It’s much more difficult to maintain (because of its ever-changing nature) than a static IP address.
If you do need a static IP address, then go ahead and follow the steps here. If not, you can skip this section.

As you will see, the command (shown above) includes “sudo” at the beginning of the line. While it’s possible to use the “su” command (superuser) and log in as the superuser, the use of “sudo” only runs that one command as superuser.
The other method, logging in as superuser, allows all tasks to be completed as superuser, making it more convenient to do what needs to be done.
However, along with that comes a security risk, which is why it’s safer to simply start the command with sudo and allow the app to request a password (as needed) to complete the command as superuser for that task/command.
The choice is yours and should be based on whatever method is easier. The file represented by the screenshot below is accessed via the following command:
sudo vi /etc/sysconfig/network-scripts/ifcfg-eth0
Prior to using that command, the network device number is verified ( eth0 ) to ensure that it’s correct. As you recall, the Linux configurations are managed within the file for the interface so it’s essential that the interface number is verified from that file prior to editing the configuration file.
Another aspect of the configuration file to take notice of is the use of the word “static.” Since we are adding a static IP address, it’s important to let the configuration file know that that’s the case.
The notes were added in the screenshot below for illustrative reasons, but should not be included in your configuration file. Also, in some Linux distributions, quotation marks are required. In this particular configuration file, no quotation marks were present in the auto-created configuration file so that trend was continued and no quotation marks were added.

The following screenshot shows how the file would actually appear, with the notes and extra spaces removed.

The next (and final) configuration file to be edited is accessed by typing:
sudo vi /etc/resolv.conf
Within that file, the nameservers can be added (or modified). Those nameservers should match the other configuration file that was just modified. In this case, at /etc/sysconfig/network-scripts/ifcfg-eth0 (the screenshot above).
The verbiage that will be used is “nameserver.” So, where the device configuration file shows DNS1=8.8.8.8, the resolv.conf file should show nameserver 8.8.8.8.
The counterpart of DNS2=4.4.4.4 would show as nameserver 4.4.4.4 in the resolv.conf file.
Loosely put, the steps above work on the Red Hat Linux distribution, but there’s no guarantee that it’ll work in the future, with the technology changes that occur. This is why configurations should be tested and verified.
Once the configurations have been completed, restart the network interface with the preferred method as described above. This will apply the changes. It’s also helpful if the static IP address is tested. You can do this by attempting to connect to that public static IP address from another device (preferably on a different network).
You could also call a friend or associate and have them attempt a connection to the static IP address from another geographic location (and different network).
Tutorial 02: Network IP Aliasing
It’s possible to assign more than one IP address to one network interface card (NIC). This is called Network IP Aliasing because only one IP would be an actual one, so the additional IP addresses are aliases to the same card. In order to assign the IP address, use your favorite method of assigning the IP address as described in Tutorial 01.
It isn’t that it has to be static, but in order to have multiple IP addresses assigned using Network IP Aliasing, one has to assign IP addresses using a static IP.
Tutorial 03: Change Host Name of the Linux Machine
Use the following steps to change the hostname of your Linux machine using your preferred editor:
1. Modify the hostname configuration file by typing the following in the command line app:
sudo vi /etc/hostname
Wherever you see the old host name in that configuration file, replace it with the new host name.
2. Modify the hosts configuration file by typing the following in the command line app:
sudo vi /etc/hosts
Wherever you see the old host name in that file, replace it with the newly chosen/designated host name in the same way that you did with the hostname configuration file in the above step one.
3. Restart the server or Linux computer. One method to do this (depending on your Linux distro) is to type the following in the command line app:
sudo shutdown –r now
This restart is needed in order for the changes to take effect.
Tutorial 04: Enable and Disable Your NIC
One of the more fascinating things that you can do via the command line in Linux is to enable or disable your Ethernet connection.
To do this, type the appropriate command from these two:
sudo ip link setup
sudo ip link setdown
With older versions of Linux, you could run ifconfigup or ifconfigdown, but it’s possible that those commands are deprecated or obsolete within newer Linux distributions. In that case, the newer ip command is preferable.
Tutorial 05: Enable Network Forwarding
Your Linux operating system is capable of connecting a variety of networks and can act as a router. All you need to do is uncomment the net.ipv4.ip_fporward=1 line which will enable you to forward the IP address.
The necessary configuration file is normally stored at /etc/sysctl.conf:
For examples on how to set it up take a look at “How to enable IP forwarding on Linux (IPv4 / IPv6).”
If you’re setting up a Linux server using DHCP (instead of a static IP address) you can opt for a form of network forwarding. This is not common, but referenced here because it’s doable and it represents a case where someone may be inclined to do so.
Tutorial 06: Remote Commands Via Shell
In the case where you need to access a Linux server and that server is not geographically located in the same place as you, you may need to use remote commands to access that remote Linux server.
For those who are programmers or system administrators, “remoting in” to a server is a normal occurrence.
One of the most popular ways to do this is to use the “ssh” command, letting the command line app know that you want to securely access the Linux server, even if you are doing so via an insecure connection.
In addition to the use of the “ssh” command, you need to provide information of where you’re connecting and how (among other options available).

You may use a domain name for the Linux server access or even a public static IP address. The name or IP address tells the ssh command what it’s accessing and where to find it.
Other options may include the username that will be used to login to the remote server. Without that option defined, it may be requested but it’s also an option to define it at the same time as the ssh command.
For example:
ssh username myserver.com
The password may also be configured into the command but it’s recommended, for security reasons, that you enter that at the time of the connection with the remote server.
Why? If the password is typed into the command, in plain text, it can be accessed by the next person using that same computer and they would have access to the password.
For additional security reasons you may want to access the Linux server via a specific port. By designating a port that may be used, you can block other ports and prevent hacker attempts or DOS (denial of service) attacks.
There are many different configuration points for ssh. Some of these are listed at shellhacks.com.
Tutorial 07: Network Monitoring Tools
One important component of managing a network is verifying that everything works and continues to work. You can do this through network monitoring. Tools that accommodate network monitoring vary but ultimately accomplish similar goals and objectives.
One such network-monitoring tool is Cacti. Cacti is an open-source network monitoring tool. Cacti monitors the network and provides graphical representations of what has been logged. This helps users (especially newbies) to identify where there may be issues.
The front end can accommodate plenty of users and is sometimes used by hosting services to display real-time bandwidth information and other data in the following graphs..

Data can be fed into Cacti via any external script or command. Cacti will bring the data together via a cron-job and fill your MySQL database before presenting it as a front end user graph.

To handle data gathering, you can feed cacti the paths to any external script/command along with any data that the user will need to “fill in”. Cacti will then gather this data in a cron-job and populate a MySQL database.
Cacti is a useful tool for network administrators who want to monitor network use and provide easy-to-understand visuals to consumers. Cacti can be downloaded for free at cacti.net. The website includes documentation to install and configure the network monitoring tool.
Alternatives to Cacti you could try include, Solarwinds NPM, PRTG and Nagios. Solarwinds will support SNMP as well as ICMP/Ping, WMI, Netflow, Sflow, Jflow and IPFIX, to name a few. The pre-built templates, graphs and alerts help you to start monitoring your network quickly.
PRTG provides up to one hundred Sensors for free. It has similar features to Solarwinds, plus flexible alerts and applications for Smartphones, tablets, ipads.
Nagios has all of the tools you will find in Cacti, but does require a little more configuration. There are plenty of plugins to choose from. It has a solid reputation as one of the oldest network management and monitoring tools. But, you will have to get your hands dirty in the maintenance of its configuration files.































