您的 iPhone 最近是否表现出可疑或异常行为?认为它被黑客入侵是正常的。与Android不同,iOS 设备(iPhone、iPad 和 iPod touch)不太容易受到恶意软件感染或黑客攻击。但它们不能免受恶意软件攻击。
本指南将向您展示一些被黑 iPhone 显示的警告信号(warning signs that a hacked iPhone displays)。您还将了解如何提高设备的安全性。如果您的 iPhone 出现以下任何症状,则它可能已被黑客入侵。

您(Your)的iPhone 被黑客入侵的迹象(Signs)是什么?
iPhone hack 以不同的形式存在,没有一种方法可以测试所有这些。您必须手动查找特定症状或异常,如下所示:
- 无法识别的应用程序或不断弹出窗口:(Unrecognized Apps or Incessant Pop-Ups:)恶意软件入侵或感染可能会导致您的 iPhone 不断显示弹出窗口并在您不知情的情况下安装不需要的应用程序。
- 电池耗尽问题:(Battery Drainage Issues:)您的 iPhone 电池是否比平时更快耗尽?这可能是由于恶意软件的后台活动增加所致。
- 性能滞后:(Performance Lag:) 流氓(Rogue)应用程序会过度使用您的 iPhone 的CPU并消耗过多的内存空间,从而导致性能滞后和其他问题。
- 高数据使用率:(High Data Usage: )一些恶意软件通过互联网与开发人员全天候交换信息。因此(Hence),手机日使用量的突然飙升是电话被黑的有效指标。
- 可疑电话、短信和通知:(Suspicious Phone Calls, Text Messages, and Notifications:)您的 iPhone 是否向未知电话号码发送自动短信?您的通话记录中是否有随机拨出电话?这清楚地表明您的 iPhone 已被黑客入侵。

iPhone是如何被黑客入侵的?
黑客攻击的主要目的是访问您设备上的数据。黑客(Hackers)通常使用恶意软件(病毒、间谍软件等)以欺诈手段从您的 iPhone 获取信息。
Apple在防止欺诈性开发人员将恶意应用程序上传到(Apple)App Store方面做得很好。因此,从App Store(App Store)安装恶意软件几乎是不可能的。但是,以下活动可能会使您的 iPhone 面临安全威胁和入侵:
- 越狱你的 iPhone:(Jailbreaking Your iPhone:)如果你在越狱的 iPhone 上下载Apple App Store以外的应用程序,恶意软件感染的机会就会高得多。
- 使用公共 Wi-Fi:(Using Public Wi-Fi:)网络犯罪分子经常利用公共Wi-Fi网络传播恶意软件、渗透人们的设备并窃取敏感数据。如果您不想被黑客入侵,远离公共Wi-Fi是一个很好的起点。
- 运行过时的操作系统:(Running Outdated Operating System:)未能安装软件补丁或更新会使您的 iPhone 面临新的安全威胁。
- 糟糕的 iCloud 安全性:(Poor iCloud Security:)如果黑客掌握了您的Apple ID帐户登录信息,他们就可以直接和间接地访问您的 iPhone。他们可以更改您的帐户密码、访问您的 iCloud 备份或远程抹掉您的 iPhone。
iPhone被黑客入侵时该怎么办(Has Been Hacked)
这里有一些技巧可以结束正在进行的黑客攻击并防止其在未来再次发生。
1.禁用可疑应用程序的(Suspicious Apps)数据(Data)使用
许多恶意软件在后台悄悄运行,将个人数据从您的 iPhone 发送给黑客或开发人员。某些恶意软件甚至会在您的设备上安装间谍软件和其他类型的恶意软件。(spyware and other types of malware)
恶意软件(Malware)活动通常是数据密集型的。如果您比平时更快地用完有限的数据计划,或者电话账单突然激增,请检查 iPhone 的数据使用情况,以查找导致问题的不熟悉的应用程序。
转到设置(Settings)>蜂窝(Cellular)(或移动数据(Mobile Data))并滚动到“蜂窝数据”或“移动数据”部分。

应用程序(Apps)按数据消耗的降序排列。禁用无法识别或虚假应用程序的蜂窝数据访问,然后监控 iPhone 的数据使用情况和行为。
如果数据使用量仍然异常高,请参阅我们的减少 iPhone 数据(reducing data on iPhone)的指南,了解更多故障排除提示。此外,确认您的iPhone 没有任何间谍软件(iPhone doesn’t have any spyware)。
2.检查CPU和RAM使用情况
恶意应用程序过度使用CPU和内存会使(CPU)您的 iPhone 过热(overheat your iPhone)并降低其性能。这些应用程序经常在后台持续运行,耗尽系统资源并过度使用您的 iPhone。
没有本地方法可以检查 iPhone 的CPU使用率。但是, App Store(App Store)中可靠的第三方应用程序(免费和付费)可以完成这项工作。有关详细信息,请参阅我们关于监控 iPhone 上的 RAM 和 CPU(monitoring RAM and CPU on iPhones)的教程。
如果没有无法识别的应用程序正在使用您 iPhone 的CPU或RAM,请尝试其他有助于冷却设备的(cool down your device)已知技巧。移除手机壳、禁用后台应用刷新、拔下充电器、降低屏幕亮度等。
我们还建议您阅读这篇文章,其中重点介绍了15 个维护技巧,以保持您的 iPhone 流畅运行(15 maintenance tips to keep your iPhone running smoothly)。文章中的建议可以极大地提高 iPhone 的性能。
3.检查您的电池使用情况

后台(Background)恶意软件活动还可能导致电池消耗增加和其他与电池相关的问题。幸运的是,iOS 会分析 iPhone 上每个应用程序使用的电池电量。因此,很容易追踪导致电池耗尽问题的任何恶意软件。
转到“设置”(Settings) > “电池(Battery)”并等待几秒钟让 iOS 加载电池使用情况报告。默认情况下,iOS 会显示过去 24 小时内的应用电池使用情况。前往过去 10 天(Last 10 Days)选项卡以查看过去十天的累积电池使用情况报告。

点击第一个应用上方的显示活动(Show Activity)以查看每个应用的屏幕和后台活动。
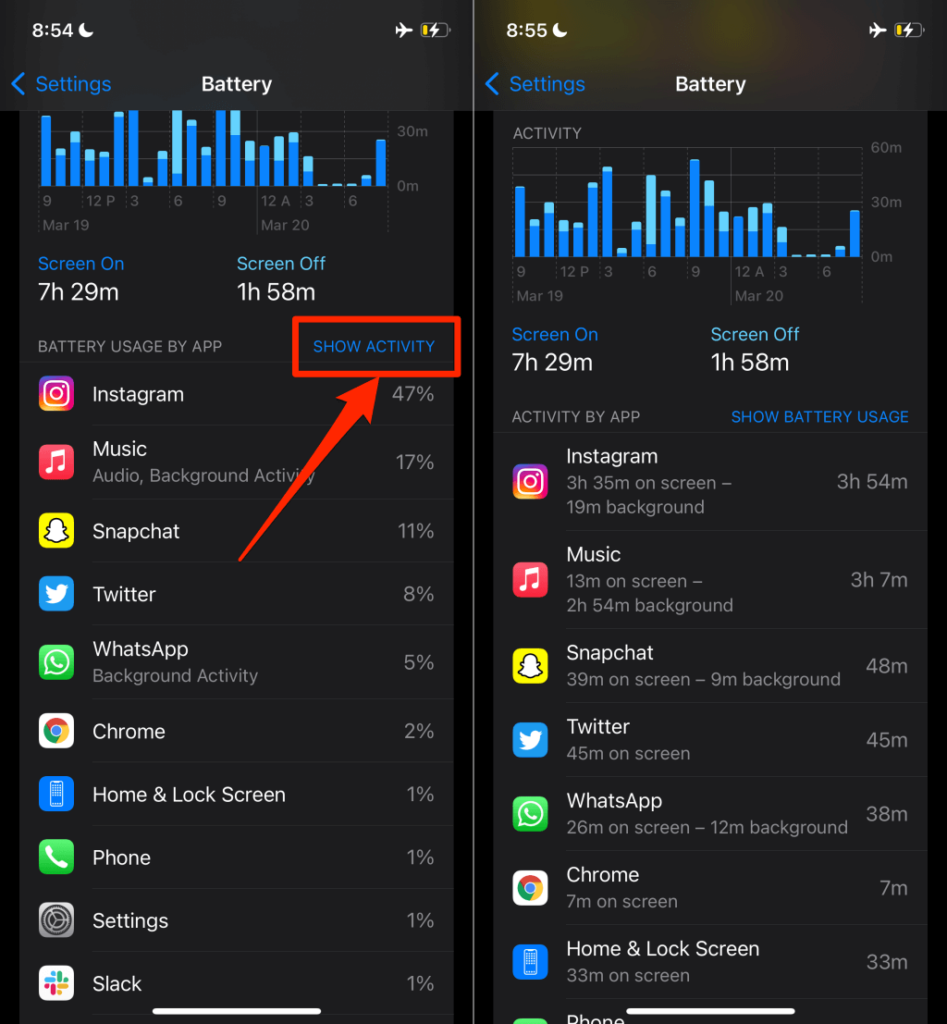
仔细浏览列表并注意任何无法识别或奇怪的具有高背景活动和电池使用的应用程序。跳转(Jump)到下一部分,了解如何从 iPhone 中删除可疑应用程序。
4.卸载可疑应用程序
删除(Delete)任何数据消耗量、电池使用量或后台活动高的无法识别的应用程序,尤其是当它是您几乎不使用的应用程序时。
前往Settings > General > iPhone Storage,选择应用程序,点击Delete App,然后在提示时再次点击Delete App 。

或者,长按主屏幕(Home Screen)上的应用程序,点击删除应用(Remove App)程序,然后在确认提示中选择删除应用程序。(Delete App)

5.重启你的 iPhone
简单的设备重启可能会消除看似黑客攻击或恶意软件攻击的临时故障。例如,如果您的 iPhone 很快死机,但电池使用报告中没有可疑应用程序。重新启动可以解决问题。
前往“设置”(Settings) > “通用(General)” > “关机”(Shut Down),拖动滑块,然后等待 30 秒让 iPhone 完全关机。然后(Afterward),按住 iPhone 的侧边按钮(Side button),直到看到 Apple 标志。

6. 更新你的 iPhone
运行过时操作系统的 iPhone 更容易受到各种形式的攻击。例如,iOS 14.4 和 iPadOS 14.4 更新(iOS 14.4 and iPadOS 14.4 updates)修复了允许恶意应用程序访问和泄露 iPhone 和 iPad 上的敏感信息的问题。iOS 14.3 及更早版本还存在允许攻击者访问您 iPhone 上的私人联系信息的漏洞——即使在使用密码锁定时也是如此。
Apple和一些第三方安全公司发现了黑客可以利用的漏洞,并 ( Apple ) 发布了安全补丁来阻止它们。这凸显了更新 iPhone 的重要性。
打开设置(Settings)应用程序,选择常规(General),点击软件更新(Software Update),然后点击下载并安装(Download and Install)以更新您的 iPhone。

7.避免公共Wi-Fi网络
公共Wi-Fi网络几乎没有可靠的安全系统。这使得黑客很容易拦截您在使用网络时访问的网站上的交换。一些黑客甚至建立了模仿真实网络的虚假公共Wi-Fi网络。

加入此类Wi-Fi网络允许黑客访问您的互联网流量个人数据,例如信用卡信息、密码等。如果您必须使用公共Wi-Fi,请使用虚拟专用网络 (VPN)(Virtual Private Network (VPN))。VPN(VPNs)将通过屏蔽您的 IP 地址和加密网络上交换的数据来保护您的连接。
8. 使用双重验证(Two-Factor Verification)保护 iCloud
如果黑客获得了访问您的 iCloud 帐户的权限,他们就会拥有您从 iPhone 上传到 iCloud 的所有内容。除了使用强密码外,还可以使用双重身份验证保护您的 Apple ID 帐户(secure your Apple ID account with two-factor authentication)。
9.恢复出厂设置你的 iPhone
如果您的 iPhone 继续出现恶意软件入侵的迹象,请擦除您的 iPhone 并将其重置为出厂默认设置。
前往“设置”(Settings) > “通用(General)” > “传输或重置 iPhone(Transfer or Reset iPhone) ” > “抹掉所有内容和设置”(Erase All Content and Settings)。点击继续(Continue)并输入您的 iPhone 密码以继续。

在 iOS 14 或更低版本上,前往“设置”(Settings) > “通用(General)” > “重置(Reset)” > “抹掉所有内容和设置”(Erase All Content and Settings)。
保持您的 iPhone 防黑客攻击
iOS 在沙盒环境中运行应用程序,因此恶意软件几乎不可能在其他应用程序中传播——除非你越狱你的 iPhone。但重申一下,iPhone 不能免于安全威胁或黑客攻击。但是,您现在知道如果您的 iPhone 出现上述任何迹象该怎么办。如果问题仍然存在,请联系 Apple 支持。(Contact Apple Support)
Is There a Test To Know If Your iPhone Has Been Hacked?
Is your iPhone exhibiting susрicious or unusual behavior lately? It’s normal to think it’s been hacked. Unlike Andrоid, iOS deviceѕ (iPhone, iPad, and iPod touch) are less susceptible to malwarе infectiоns or hacks. Βut they aren’t immυne to malware attacks.
This guide will show you some warning signs that a hacked iPhone displays. You’ll also learn how to improve your device’s security. If your iPhone exhibits any of the symptoms below, it’s probably been hacked.

What Are the Signs of Your iPhone Being Hacked?
iPhone hacks exist in different forms, and there’s no one way to test for them all. You have to manually look out for specific symptoms or abnormalities like the ones below:
- Unrecognized Apps or Incessant Pop-Ups: A malware hack or infection could cause your iPhone to display incessant pop-ups and install unwanted apps without your knowledge.
- Battery Drainage Issues: Does your iPhone battery die faster than usual? It could be due to increased background activity of malicious software.
- Performance Lag: Rogue apps will overwork your iPhone’s CPU and consume excessive memory space, resulting in performance lag and other issues.
- High Data Usage: Some malicious software exchanges information with their developers round-the-clock over the internet. Hence, a sudden spike in mobile day usage is a valid indicator of a phone hack.
- Suspicious Phone Calls, Text Messages, and Notifications: Does your iPhone send automated text messages to unknown phone numbers? Are there random outgoing calls in your call log? That’s a clear indication that your iPhone is hacked.

How Do iPhones Get Hacked?
The primary purpose of a hack is to access data on your device. Hackers typically employ malicious software (viruses, spyware, etc.) to obtain information from your iPhone fraudulently.
Apple does a great job of preventing fraudulent developers from uploading malicious apps to the App Store. So, it’s almost impossible to install malware from the App Store. However, the following activities can expose your iPhone to security threats and invasions:
- Jailbreaking Your iPhone: If you download apps outside the Apple App Store on a jailbroken iPhone, the chances of malware infection are much higher.
- Using Public Wi-Fi: Cybercriminals often exploit public Wi-Fi networks to spread malware, infiltrate people’s devices, and steal sensitive data. If you don’t want to get hacked, staying away from public Wi-Fi is an excellent place to start.
- Running Outdated Operating System: Failure to install software patches or updates exposes your iPhone to new security threats.
- Poor iCloud Security: If hackers get hold of your Apple ID account login information, they have direct and indirect access to your iPhone. They can change your account password, access your iCloud backup, or remotely erase your iPhone.
What to Do When iPhone Has Been Hacked
Here are some tips to end an ongoing hack and prevent its reoccurrence in the future.
1. Disable Data Usage for Suspicious Apps
A lot of malware runs quietly in the background, sending personal data to the hacker or developer from your iPhone. Some malware even install spyware and other types of malware on your device.
Malware activities are often data-intensive. If you exhaust your limited data plan faster than usual, or there’s a sudden spike in your phone bill, check your iPhone’s data usage for unfamiliar apps responsible for the problem.
Go to Settings > Cellular (or Mobile Data) and scroll to the “Cellular Data” or “Mobile Data” section.

Apps are arranged in descending order of data consumption. Disable cellular data access for unrecognized or phony apps and monitor your iPhone’s data usage and behavior afterward.
If data usage remains unusually high, refer to our guide on reducing data on iPhone for more troubleshooting tips. Additionally, confirm that your iPhone doesn’t have any spyware.
2. Check CPU and RAM Usage
Excessive CPU and memory usage by rogue apps will overheat your iPhone and slow its performance. These apps often run constantly in the background, using up system resources and overworking your iPhone.
There’s no native method to check your iPhone’s CPU usage. However, reliable third-party apps (free and paid) in the App Store can get the job done. Refer to our tutorial on monitoring RAM and CPU on iPhones for more details.
If no unrecognized apps are using your iPhone’s CPU or RAM, try other known tricks that can help cool down your device. Remove your phone case, disable background app refresh, unplug your charger, reduce the screen brightness, etc.
We also recommend reading this article that highlights 15 maintenance tips to keep your iPhone running smoothly. The recommendations in the article can speed up your iPhone’s performance tremendously.
3. Check Your Battery Usage

Background malware activity can also result in increased battery drainage and other battery-related issues. Luckily, iOS analyzes the amount of battery power each app uses on your iPhone. So, it’s easy to trace any malware responsible for the battery drain problem.
Go to Settings > Battery and wait a few seconds for iOS to load the battery usage report. By default, iOS displays app battery usage for the last 24 hours. Head to the Last 10 Days tab to view a cumulative battery usage report for the past ten days.

Tap Show Activity above the first app to view each app’s on-screen and background activities instead.

Go through the list carefully and note any unrecognized or strange apps with high background activity and battery usage. Jump to the next section to learn how to remove the suspicious apps from your iPhone.
4. Uninstall Suspicious Apps
Delete any unrecognized app with an insane amount of data consumption, battery usage, or high background activity—especially if it’s an app you barely use.
Head to Settings > General > iPhone Storage, select the app, tap Delete App, and tap Delete App again on the prompt.

Alternatively, long-press the app on the Home Screen, tap Remove App and select Delete App on the confirmation prompt.

5. Restart Your iPhone
A simple device reboot might eliminate temporary glitches that seem like a hack or malware attack. For example, if your iPhone dies quickly, but there’s no suspicious app in the battery usage report. A reboot could fix the problem.
Go to Settings > General > Shut Down, drag the slider, and wait 30 seconds for your iPhone to shut down completely. Afterward, press and hold your iPhone’s Side button until you see the Apple logo.

6. Update Your iPhone
iPhones running outdated operating systems are more vulnerable to all forms of attacks. For instance, the iOS 14.4 and iPadOS 14.4 updates fixed issues that allowed malicious applications to access and leak sensitive information on iPhones and iPads. iOS 14.3 and older also had vulnerabilities that allow an attacker to access private contact information on your iPhone—even when locked with a passcode.
Apple and some third-party security companies spot vulnerabilities that hackers can exploit and (Apple) release security patches to block them. That highlights the importance of updating your iPhone.
Open the Settings app, select General, tap Software Update, and tap Download and Install to update your iPhone.

7. Avoid Public Wi-Fi Network
Public Wi-Fi networks barely have solid security systems. That makes it easy for a hacker to intercept exchanges on websites you visit while using the network. Some hackers even set up fake public Wi-Fi networks that mimic genuine networks.

Joining such Wi-Fi networks allows hackers to access your internet traffic personal data like credit card information, passwords, etc. If you have to use public Wi-Fi, do so with a Virtual Private Network (VPN). VPNs will secure your connection by masking your IP address and encrypting data exchanged on the network.
8. Secure iCloud with Two-Factor Verification
If hackers gain access to your iCloud account, they have everything you’ve uploaded from your iPhone to iCloud. In addition to using a strong password, secure your Apple ID account with two-factor authentication.
9. Factory Reset Your iPhone
Erase your iPhone and reset it to factory default if it continues to exhibit signs of malware hack.
Go to Settings > General > Transfer or Reset iPhone > Erase All Content and Settings. Tap Continue and enter your iPhone’s passcode to proceed.

On iOS 14 or older, go to Settings > General > Reset > Erase All Content and Settings.
Keep Your iPhone Hack-Proof
iOS runs applications in a sandboxed environment, so it’s almost impossible for malware to spread across other apps—unless you jailbreak your iPhone. But to reiterate, iPhones aren’t immune to security threats or hacks. However, you now know what to do if your iPhone exhibits any of the abovementioned signs. Contact Apple Support if the issues persist.












