你(Are)想知道什么是校验和吗?您可能已经注意到,当您从某些网站下载文件时,它们有很长的数字和字母字符串,称为校验和或 MD5 校验和(checksum or MD5 checksum)或SHA-1等。这些非常长的字符串基本上充当该特定文件的指纹,无论是它是EXE、ISO、ZIP等。
校验和用于确保文件从一个存储设备(storage device)传输到另一个存储设备后的完整性。这可以通过Internet或只是在同一网络上的两台计算机之间。无论哪种方式,如果要确保传输的文件与源文件(source file)完全相同,可以使用校验和。
校验和是使用散列函数(hash function)计算的,通常与下载一起发布。为了验证文件的完整性,用户使用校验和计算器程序(calculator program)计算校验和,然后比较两者以确保它们匹配。
校验和不仅用于确保无损坏传输,还用于确保文件未被篡改。当使用好的校验和算法(checksum algorithm)时,即使是对文件的微小更改也会导致完全不同的校验和值(checksum value)。
最常见的校验和是MD5 和 SHA-1(MD5 and SHA-1),但都被发现存在漏洞。这意味着恶意篡改可能导致两个不同的文件具有相同的计算哈希值。由于这些安全问题,较新的SHA-2被认为是最好的加密散列函数(hash function),因为目前还没有针对它的攻击证明。

正如您在上面的屏幕截图中看到的,我尝试从Microsoft下载的(Microsoft)ISO 文件(ISO file)列出了SHA1 校验和。(SHA1 checksum)下载文件后,我将使用校验和计算器(checksum calculator)来验证文件的完整性。
大约 99.9% 的情况下,从Internet(Internet)下载文件时,您真的不需要关心或担心校验和。但是,如果您正在下载敏感软件,例如杀毒软件或(anti-virus or privacy software)Tor等隐私软件,验证校验和可能是个好主意,因为黑客可以创建受恶意软件感染的关键软件版本,以获得对系统的完全访问权限。
计算校验和有很多不同的实用程序,我在这里只提到一两个,因为好的实用程序可以为您创建多个哈希值,也可以验证哈希值。
MD5 和 SHA 校验和实用程序
MD5 和 SHA 校验和实用程序(MD5 & SHA Checksum Utility)是我最喜欢的校验和处理实用程序,因为它具有我在免费版本中需要的所有功能。下载后,只需运行EXE 文件(EXE file)即可打开程序。
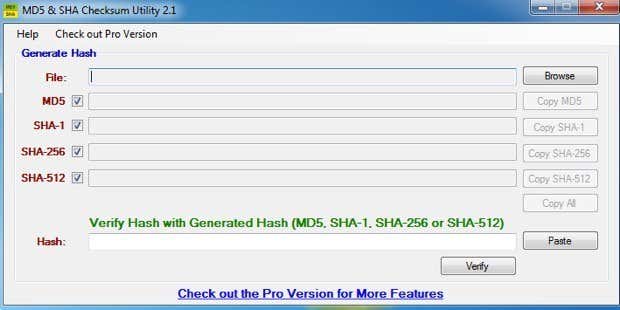
该界面非常简单易用。只需单击(Simply click)“浏览(Browse)”按钮选择您的文件,就会自动计算MD5、SHA-1、SHA-256 和 SHA-512(SHA-256 and SHA-512)的哈希值。
如您所见,MD5 散列(MD5 hash)最短,而SHA-512 散列(SHA-512 hash)很长。哈希值越长,它就越安全。

要验证哈希,只需将其复制并粘贴(copy and paste)到最底部的哈希框中。(Hash)单击(Click)验证(Verify),它将与四个生成的哈希进行比较,以查看是否匹配。
在线校验和计算器
对于那些不想在他们的系统上下载任何软件的人来说,在线校验和计算器(online checksum calculator)将是更好的选择。在线计算器有更多限制,主要是文件的最大上传大小,但对于较小的文件,它们工作得很好。
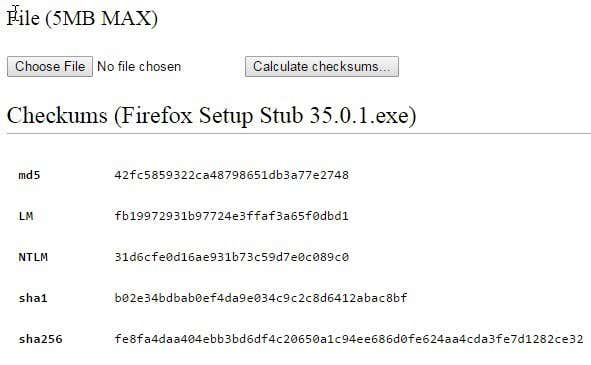
一个名为Defuse的网站有一个免费的文件校验和计算器(file checksum calculator),用于上传大小高达 5MB 的文件。这非常小,因此您需要使用桌面应用程序或下面提到的下一个在线工具来处理比这更大的任何事情。(online tool)
如果 5 MB 太小,请查看OnlineMD5,这是另一个免费网站,可让您为最大 4 GB 的文件生成校验和。显然,它没有将实际文件上传到他们的服务器就可以做到这一点。我不确定它是如何工作的,但它似乎只是在系统上本地运行算法,然后在浏览器中显示它。这是一种非常聪明的方法,因为您不必下载额外的软件,也不必永远等待上传大文件。
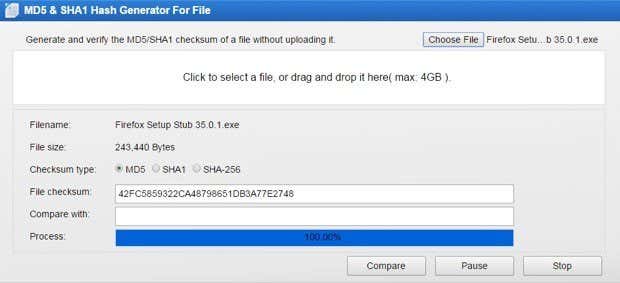
这个站点也很不错,因为除了计算校验和之外,您还可以验证校验和。希望(Hopefully)您现在对什么是校验和以及如何使用和计算校验和有了更好的理解。如果您发送或接收安全文件,校验和是双方验证这些文件完整性的最佳方式。如果您有任何问题,请发表评论。享受!
What is a Checksum and How to Calculate a Checksum
Are you wondering what a checksum is? You may have noticed that when you download files from certain websites, they have a very long string of numbers and letters called a сhecksum or MD5 checksum or SHA-1, etc. Thesе really long strings basically act as fingerрrintѕ fоr that particular file, whether it be an EXE, ISO, ZIP, etc.
Checksums are used to ensure the integrity of a file after it has been transmitted from one storage device to another. This can be across the Internet or simply between two computers on the same network. Either way, if you want to ensure that the transmitted file is exactly the same as the source file, you can use a checksum.
The checksum is calculated using a hash function and is normally posted along with the download. To verify the integrity of the file, a user calculates the checksum using a checksum calculator program and then compares the two to make sure they match.
Checksums are used not only to ensure a corrupt-free transmission, but also to ensure that the file has not been tampered with. When a good checksum algorithm is used, even a tiny change to the file will result in a completely different checksum value.
The most common checksums are MD5 and SHA-1, but both have been found to have vulnerabilities. This means that malicious tampering can lead to two different files having the same computed hash. Due to these security concerns, the newer SHA-2 is considered the best cryptographic hash function since no attack has been demonstrated on it as of yet.

As you can see in the screenshot above, the ISO file I am trying to download from Microsoft has a SHA1 checksum listed. Once I download the file, I would use a checksum calculator to verify the integrity of the file.
About 99.9% of the time, you really don’t need to care or worry about checksums when downloading files off the Internet. However, if you are downloading something sensitive like anti-virus or privacy software like Tor, it’s probably a good idea to verify the checksum because hackers can create malware-infested versions of critical software in order to gain full access to a system.
There are a ton of different utilities for calculating checksums and I’ll mention only one or two here since the good ones can create multiple hashes for you and can also verify hashes.
MD5 & SHA Checksum Utility
The MD5 & SHA Checksum Utility is my favorite utility for working with checksums because it has all the features I need in the free version. Once you download it, simply run the EXE file to open the program.

The interface is very straightforward and easy to use. Simply click on the Browse button to choose your file and the hashes will automatically be calculated for MD5, SHA-1, SHA-256 and SHA-512.
As you can see the MD5 hash is the shortest and the SHA-512 hash is very long. The longer the hash, the more secure it is.

To verify a hash, just copy and paste it into the Hash box at the very bottom. Click on Verify and it will compare it to the four generated hashes to see if there is a match.
Online Checksum Calculator
For those who would rather not download any software onto their systems, an online checksum calculator would be the better choice. The online calculators have more restrictions, mostly the max upload size of the file, but for smaller files, they work just fine.
A site called Defuse has a free file checksum calculator for uploads up to 5MB in size. That’s pretty tiny, so you’ll need to use either the desktop application or the next online tool mentioned below for anything bigger than that.

If 5 MB is just too small, then check out OnlineMD5, another free site that allows you to generate checksums for files up to 4 GB in size. Apparently, it does this without uploading the actual file to their servers. I’m not sure how it works, but it seems to just run the algorithm locally on your system and then just displays it in the browser. Quite a smart way to do it because you don’t have to download extra software and you don’t have to wait forever uploading a large file.

This site is also very nice because you can verify a checksum in addition to just calculating one. Hopefully, you now have a better understanding of what a checksum is and how it can be used and calculated. If you are sending or receiving secure files, a checksum is the best way for both parties to verify the integrity of those files. If you have any questions, post a comment. Enjoy!





