用户可以使用瑞典公司Yubico制造的硬件安全密钥登录Windows 10上的本地帐户。该公司最近发布了Yubico Login for Windows 应用程序(Login for Windows application)的第一个稳定版本。在这篇文章中,我们将向您展示如何安装和配置YubiKey以在 Windows 10 PC 上使用。
YubiKey是一款硬件认证设备,支持一次性密码、公钥加密和认证,以及FIDO联盟开发的(FIDO Alliance)Universal 2nd Factor(U2F)和FIDO2协议。它允许用户通过发出一次性密码或使用设备生成的基于 FIDO 的公钥/私钥对来安全地登录他们的帐户。YubiKey还允许存储静态密码,以便在不支持一次性密码的网站上使用。Facebook使用YubiKey作为员工凭证,谷歌(Google)支持员工和用户使用它。一些密码管理器支持YubiKey。Yubico还生产Security Key,这是一种类似于YubiKey的设备,但专注于公钥认证。
YubiKey 允许用户在不将私钥暴露给外界的情况下对消息进行签名、加密和解密。此功能以前仅适用于Mac和Linux用户。
To configure/set up YubiKey on Windows 10, you’ll need the following:
- YubiKey USB 硬件。
- 适用于 Windows 的 Yubico 登录软件。
- YubiKey 管理器软件。
所有这些都可以在yubico.com的Product选项卡下找到。此外,您应该注意YubiKey应用程序不支持由Azure Active Directory ( AAD ) 或 Active Directory (AD) 以及Microsoft Accounts管理的本地Windows帐户。
YubiKey硬件认证设备
在安装Yubico Login for Windows软件之前,记下本地帐户的Windows用户名和密码。安装软件的人必须拥有其帐户的Windows用户名和密码。没有这些,什么都不能配置,账户也无法访问。Windows凭据提供程序的默认行为是记住您的上次登录,因此您不必输入用户名。
因此,许多人可能不记得用户名。但是,一旦您安装了该工具并重新启动,新的Yubico凭据提供程序就会被加载,因此管理员和最终用户实际上都必须输入用户名。由于这些原因,不仅是管理员,而且要通过Yubico Login for Windows配置帐户的每个人都应该在管理员安装工具和配置之前检查以确保他们可以使用本地帐户的Windows用户名和密码登录- 用户的帐户。
还必须注意的是,一旦配置了适用于Windows的(Windows)Yubico 登录(Yubico Login),就会有:
- 没有Windows 密码提示
- 无法重置密码
- 不Remember Previous User/Login功能。
此外,Windows自动登录与(Windows)Yubico Login for Windows不兼容。如果在Yubico Login(Yubico Login) for Windows配置生效时,账户设置为自动登录的用户忘记了原来的密码,则无法再访问该账户。通过以下方式抢先解决(Address)此问题:
- 在禁用自动登录之前让用户设置新密码。
- 在使用 Yubico Login for Windows配置他们的帐户之前,让所有用户验证他们可以使用用户名和新密码访问他们的帐户。
安装软件需要管理员权限。
YubiKey 安装
首先,验证您的用户名。安装Yubico Login for Windows并重新启动后,除了密码之外,您还需要输入此密码才能登录。为此,请从“开始”菜单打开(Start)命令提示符(Command Prompt)或PowerShell并运行以下命令
whoami
记(Take)下完整的输出,其格式应为DESKTOP-1JJQRDF\jdoe,其中 jdoe 是用户名。
- (Download)从这里(here)下载Yubico Login for Windows软件。
- 双击下载运行安装程序。
- 接受最终用户许可协议。
- 在安装向导中,指定目标文件夹位置或接受默认位置。
- 重新启动已安装软件的机器。重新启动后,Yubico凭证提供程序会显示提示输入YubiKey的登录屏幕。
由于YubiKey尚未配置,因此您必须切换用户并输入本地Windows帐户的密码,还要输入该帐户的用户名。如有必要,您可能需要将 Microsoft Account 更改为 Local Account。
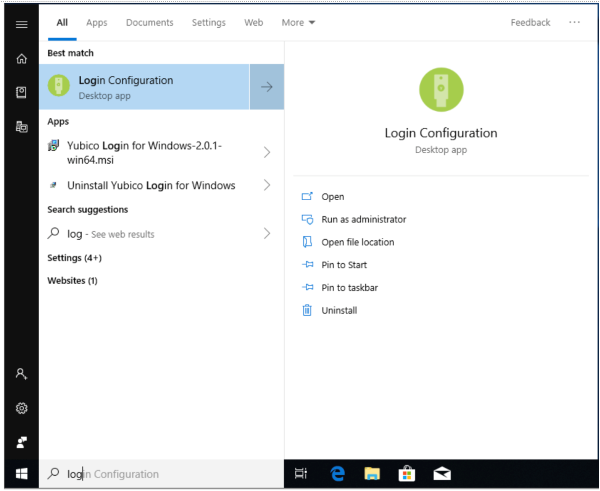
登录后,搜索带有绿色图标的“登录配置”。(实际上标记为Yubico Login for Windows的项目只是安装程序,而不是应用程序。)
YubiKey 配置
(Administrator)配置软件需要管理员权限。
只能为Yubico Login for Windows配置受支持的帐户。如果您启动配置向导,但未显示您要查找的帐户,则说明该帐户不受支持,因此无法进行配置。
在配置过程中,将需要以下内容;
- 主密钥和备用密钥(Primary and Backup Keys):每次注册使用不同的YubiKey。如果您要配置备份密钥,每个用户应该有一个YubiKey作为主密钥,第二个作为备份密钥。
- 恢复代码(Recovery Code):如果所有 YubiKey 丢失,恢复代码是验证用户身份的最后手段。恢复(Recovery)代码可以分配给您指定的用户;但是,仅当帐户的用户名和密码也可用时,恢复代码才可用。在配置过程中会显示生成恢复代码的选项。
第 1 步:在 Windows开始(Start)菜单中,选择Yubico >登录配置(Login Configuration)。
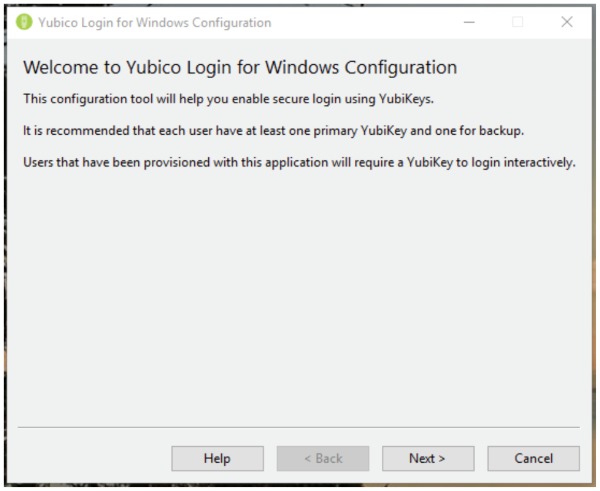
第 2 步:出现“用户帐户控制(User Account Control)”对话框。如果您从非管理员帐户运行此操作,系统将提示您输入本地管理员凭据。欢迎页面介绍了Yubico 登录配置配置(Yubico Login Configuration)向导:
第 3 步:单击下一步(Next)。出现Yubico Windows 登录配置(Yubico Windows Login Configuration)的默认(Default)页面。
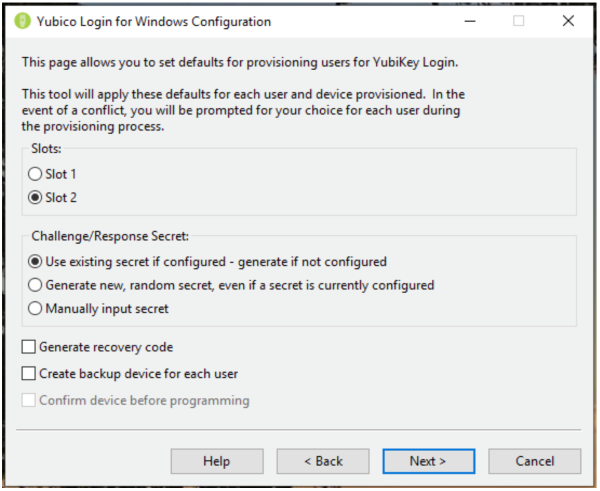
第四步:可配置的项目有:
Slots:选择将存储质询-响应密钥的插槽。所有未自定义的 YubiKey 都在插槽 1 中预加载了凭据,因此如果您使用Yubico Login for Windows配置已用于登录其他帐户的 YubiKey,请不要覆盖插槽 1。
Challenge/Response Secret:此项目使您可以指定如何配置密钥以及将其存储在何处。选项包括:
- 如果已配置,则使用现有密钥 - 如果未配置,则生成(Use existing secret if configured – generate if not configured):密钥的现有密钥将在指定的插槽中使用。如果设备没有现有的秘密,则配置过程将生成一个新的秘密。
- 生成新的随机秘密,即使当前配置了秘密(Generate new, random secret, even if a secret is currently configured):将生成新秘密并将其编程到插槽中,覆盖任何先前配置的秘密。
- 手动输入密码(Manually input secret): 对于高级用户(For advanced users):在配置过程中,应用程序将提示您手动输入 HMAC-SHA1 密码(20 个字节 - 40 个字符的十六进制编码)。
生成恢复代码(Generate Recovery Code):对于配置的每个用户,将生成一个新的恢复代码。此恢复代码使最终用户在丢失 YubiKey 时能够登录系统。
注意:如果您在为用户配置第二个密钥时选择保存恢复代码,则任何以前的恢复代码都将失效,并且只有新的恢复代码可以使用。
为每个用户创建备份设备(Create Backup Device for Each User):使用此选项让配置过程为每个用户注册两个密钥,一个主YubiKey和一个备份YubiKey。如果您不想向您的用户提供恢复代码,最好给每个用户一个备份YubiKey。有关详细信息,请参阅上面的主(Primary)密钥和备份密钥(Backup Keys) 部分。
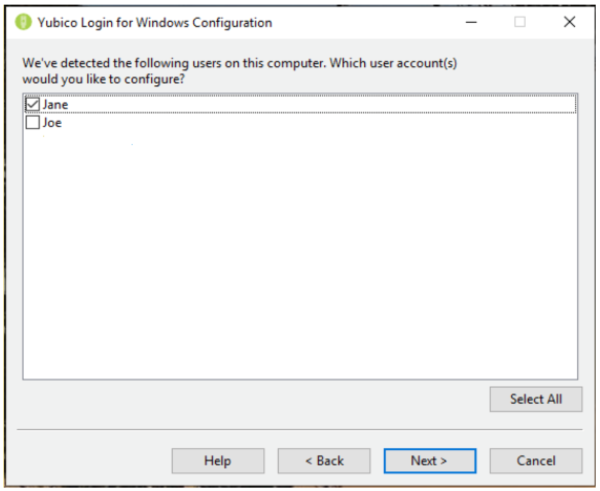
步骤 5:单击Next,选择要配置的用户。出现选择用户帐户(Select User Accounts)页面(如果Yubico Login for Windows不支持本地用户帐户,则列表将为空)。
第 6 步:通过选中用户名旁边的复选框,选择当前运行Yubico Login(Yubico Login) for Windows期间要配置的用户帐户,然后单击Next。出现配置用户(Configuring User)页面。
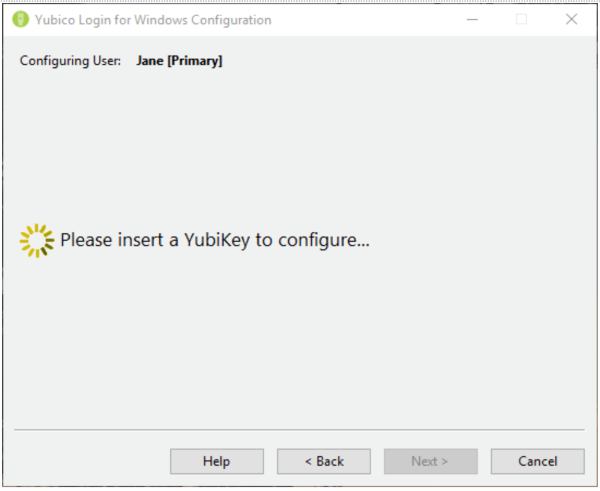
第 7 步:上面显示的配置用户(Configuring User)字段中显示的用户名是当前正在为其配置 YubiKey 的用户。在显示每个用户名时,该过程会提示您插入 YubiKey 以注册该用户。
第 8 步:在检测到插入的 YubiKey 并为用户名在页面顶部的配置用户字段中的用户注册之前,将显示(Configuring User)等待设备页面。(Wait for Device)如果您在默认(Defaults)页面中选择了为每个用户创建备份设备,(Create Backup Device for Each User)配置用户(Configuring User)字段还将显示正在注册的YubiKey中的哪个,(YubiKeys)主要(Primary)或备份(Backup)。
第 9 步:如果您已将配置过程配置为使用手动指定的密码,则会显示 40 个十六进制数字密码的字段。输入密码并单击Next。
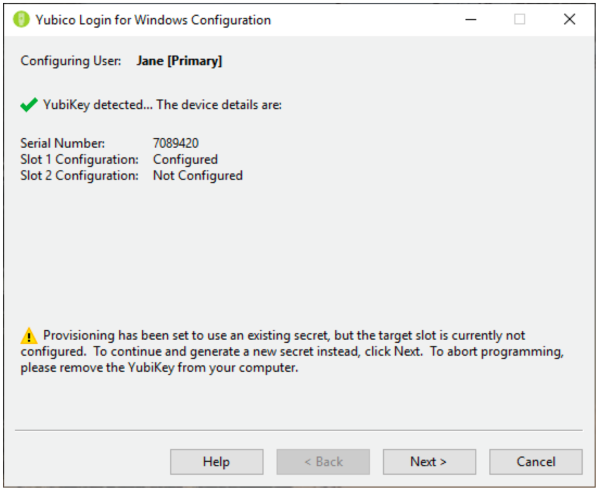
第 10 步:编程设备(Programming Device)页面显示每个YubiKey的编程进度。下面显示的设备确认(Device Confirmation)页面显示了配置过程检测到的YubiKey的详细信息,包括设备序列号(如果有)和每个一次性密码(One-Time Password)( OTP ) 插槽的配置状态。如果您设置的默认值与检测到的YubiKey之间存在冲突,则会显示一个警告符号。如果一切顺利,将显示一个复选标记。如果状态行显示错误图标,则说明错误,并在屏幕上显示修复说明。
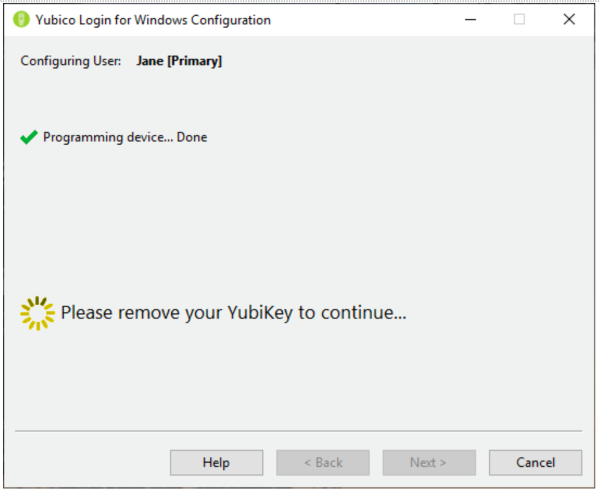
第 11 步:一旦用户帐户的编程完成,没有相应的YubiKey(YubiKey)将无法再访问该帐户。系统会提示您删除刚刚配置的YubiKey,并且配置过程会自动进行到下一个用户帐户/ YubiKey组合。
第 12 步:毕竟,指定用户帐户的YubiKeys已配置:
- 如果在Defaults页面 上选择了Generate Recovery Code ,则会显示Recovery Code页面。(Recovery Code)
- 如果 未选择生成恢复代码,则配置过程将自动继续到下一个用户帐户。(Generate Recovery Code)
- 最后一个用户帐户完成(Finished)后,预配过程将移至 已完成。
恢复代码是一个长字符串。(为了消除最终用户将数字 1 误认为小写字母 L 而将 0 误认为字母 O 而导致的问题,恢复代码以Base32进行编码,它将看起来相似的字母数字字符视为相同。)
配置指定用户帐户的所有YubiKey(YubiKeys)后,将显示恢复代码(Recovery Code)页面。
第 13 步:在恢复代码(Recovery Code)页面上,为所选用户生成并设置恢复代码。完成此操作后,恢复代码字段右侧的复制(Copy) 和 保存(Save)按钮将变为可用。
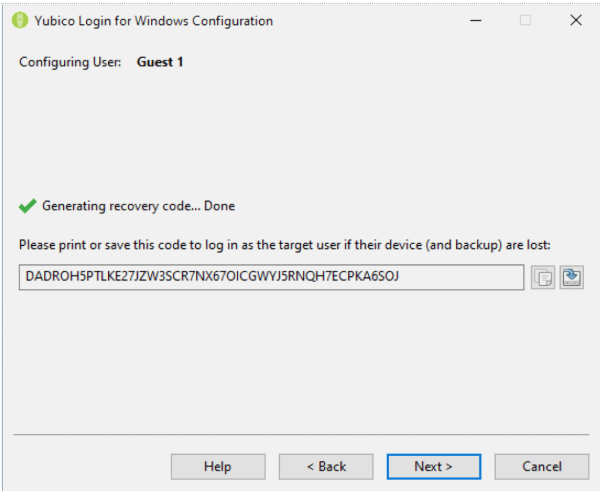
第 14 步:复制恢复代码并保存,以免与用户共享,并保留以防用户丢失。
注意(Note):请务必在此过程中保存恢复代码。进入下一个屏幕后,将无法检索代码。
第 15 步:要从“选择用户(Select Users)”页面移至下一个用户帐户,请单击“下一步”(Next)。配置最后一个用户后,供应过程将显示“已完成(Finished)”页面。
第 16 步:为每个用户提供他们的恢复代码。最终用户应将其恢复代码保存到无法登录时可访问的安全位置。
YubiKey 用户体验
当本地用户帐户已配置为需要YubiKey时,用户将由Yubico 凭据提供程序(Yubico Credential Provider)而不是默认的Windows 凭据提供程序进行身份验证。提示用户插入他们的YubiKey。然后出现Yubico 登录(Yubico Login)屏幕。用户输入他们的用户名和密码。
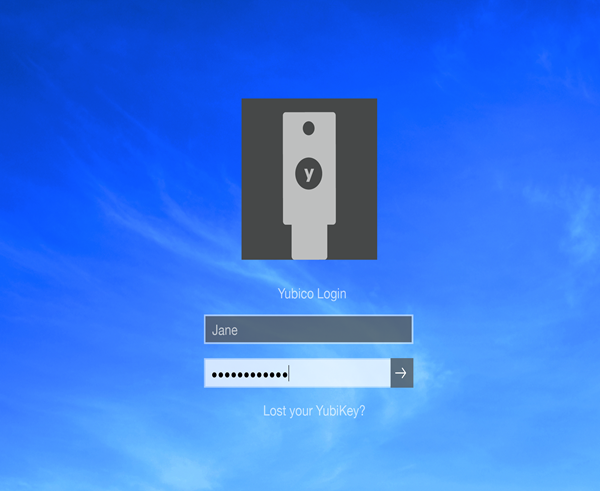
注意(Note):无需按下YubiKey USB硬件上的按钮即可登录。在某些情况下,按下按钮会导致登录失败。
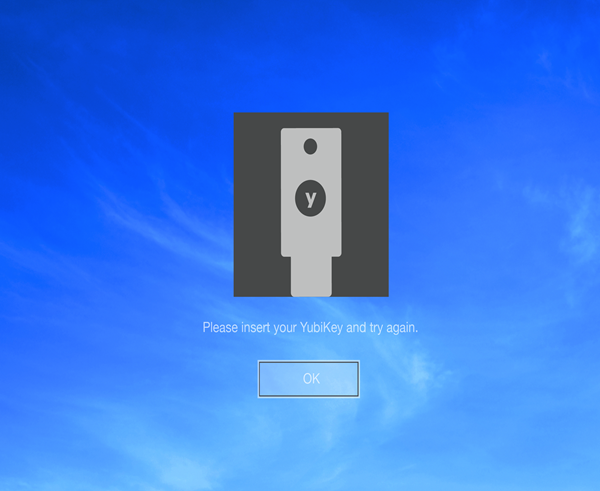
当最终用户登录时,他们必须将正确的YubiKey插入系统上的USB端口。如果最终用户在没有插入正确的YubiKey的情况下输入了他们的用户名和密码,则身份验证将失败,并且将向用户显示错误消息。
如果最终用户的帐户配置为Yubico Login for Windows,并且如果生成了恢复代码,并且用户丢失了 YubiKey,他们可以使用他们的恢复代码进行身份验证。最终用户使用他们的用户名、恢复代码和密码解锁他们的计算机。
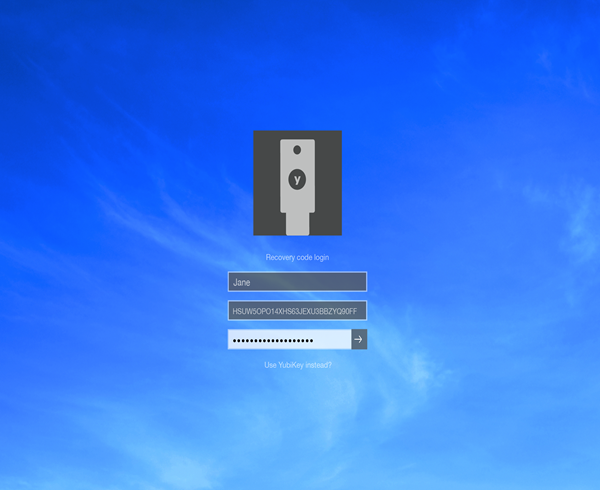
在配置新的YubiKey之前,最终用户每次登录时都必须输入恢复代码。
如果Yubico Login for Windows没有检测到YubiKey已插入,可能是由于密钥未启用OTP模式,或者您插入的不是YubiKey,而是与此应用程序不兼容的Security Key 。使用YubiKey Manager 应用程序确保所有要配置的 YubiKey 都启用了OTP(YubiKeys)接口(OTP)。
重要提示: (Important)Windows支持的替代登录方法不会受到影响。因此,您必须限制使用Yubico Login for Windows保护的用户帐户的其他本地和远程登录方法,以确保您没有打开任何“后门”。
如果您试用 YubiKey,请在下面的评论部分告诉我们您的体验。(If you try out YubiKey, let us know your experience in the comments section below.)
Configure & use YubiKey Secure Login for Local Account in Windows 10
Users can use hardware security keys, manufactured by Swediѕh company Yubico to log into a Local account on Windows 10. The company recently released the first stable version of the Yubico Login for Windows application. In this post, we will show you how to install and configure YubiKey for use on Windows 10 PCs.
YubiKey is a hardware authentication device that supports one-time passwords, public-key encryption and authentication, and the Universal 2nd Factor (U2F) and FIDO2 protocols developed by the FIDO Alliance. It allows users to securely log in to their accounts by emitting one-time passwords or using a FIDO-based public/private key pair generated by the device. YubiKey also allows for storing static passwords for use at sites that do not support one-time passwords. Facebook uses YubiKey for employee credentials, and Google supports it for both employees and users. Some password managers support YubiKey. Yubico also manufactures the Security Key, a device similar to the YubiKey, but focused on public-key authentication.
YubiKey allows users to sign, encrypt, and decrypt messages without exposing the private keys to the outside world. This feature was previously available only for Mac & Linux users.
To configure/set up YubiKey on Windows 10, you’ll need the following:
- A YubiKey USB hardware .
- Yubico Login software for Windows.
- YubiKey Manager software.
All of them are available on yubico.com under their Products tab. Also, you should note that the YubiKey app does not support local Windows accounts managed by Azure Active Directory (AAD) or Active Directory (AD) as well as Microsoft Accounts.
YubiKey hardware authentication device
Before installing the Yubico Login for Windows software, make a note of your Windows username and password for the local account. The person who installs the software must have the Windows username and password for their account. Without these, nothing can be configured, and the account is inaccessible. The default behavior of the Windows credential provider is to remember your last login, so you do not have to type in the username.
For this reason, many people may not remember the username. However, once you install the tool and reboot, the new Yubico credential provider is loaded, so that both admins and end-users have actually to type in the username. For these reasons, not only the admin but also everybody whose account is to be configured via Yubico Login for Windows should check to ensure that they can log in using the Windows username and password for their local account BEFORE the admin installs the tool and configures end-users’ accounts.
It’s also imperative to note that, once Yubico Login for Windows has been configured, there is:
- No Windows Password Hint
- No way to reset passwords
- No Remember Previous User/Login function.
Additionally, Windows automatic login is not compatible with Yubico Login for Windows. If a user whose account was set up for automatic login no longer remembers their original password when the Yubico Login for Windows configuration takes effect, the account can no longer be accessed. Address this issue preemptively by:
- Having users set new passwords before disabling automatic login.
- Have all users verify they can access their accounts with username and their new password before you use Yubico Login for Windows to configure their accounts.
Administrator permissions are required to install the software.
YubiKey Installation
First, verify your username. Once you have installed Yubico Login for Windows and rebooted, you will need to enter this in addition to your password to log in. To do this, open Command Prompt or PowerShell from the Start menu and run the command below
whoami
Take note of the full output, which should be in the form DESKTOP-1JJQRDF\jdoe, where jdoe is the username.
- Download the Yubico Login for Windows software from here.
- Run the installer by double-clicking on the download.
- Accept the end-user license agreement.
- In the installation wizard, specify the destination folder location or accept the default location.
- Restart the machine on which the software has been installed. After the restart, the Yubico credential provider presents the login screen that prompts for the YubiKey.
Because the YubiKey has not yet been provisioned, you must switch user and enter not only the password for your local Windows account, but also your username for that account. If necessary, you may have to change Microsoft Account to Local Account.
After you have logged in, search for “Login Configuration” with the green icon. (The item actually labeled Yubico Login for Windows is just the installer, not the application.)

YubiKey Configuration
Administrator permissions are required to configure the software.
Only accounts that are supported can be configured for Yubico Login for Windows. If you launch the configuration wizard, and the account you are looking for is not displayed, it is not supported and therefore not available for configuration.
During the configuration process, the following will be required;
- Primary and Backup Keys: Use a different YubiKey for each registration. If you are configuring backup keys, each user should have one YubiKey for the primary and a second one for the backup key.
- Recovery Code: A recovery code is a last-resort mechanism to authenticate a user if all YubiKeys have been lost. Recovery codes can be assigned to the users you specify; however, the recovery code is only usable if the username and password for the account are also available. The option to generate a recovery code is presented during the configuration process.
Step 1: In the Windows Start menu, select Yubico > Login Configuration.
Step 2: The User Account Control dialog appears. If you are running this from a non-Administrator account, you will be prompted for local administrator credentials. The Welcome page introduces the Yubico Login Configuration provisioning wizard:

Step 3: Click Next. The Default page of Yubico Windows Login Configuration appears.

Step 4: The configurable items are:
Slots: Select the slot where the challenge-response secret will be stored. All YubiKeys that have not been customized come pre-loaded with a credential in slot 1, so if you are using Yubico Login for Windows to configure YubiKeys that are already being used for logging into other accounts, do not overwrite slot 1.
Challenge/Response Secret: This item enables you to specify how the secret will be configured and where it will be stored. The options are:
- Use existing secret if configured – generate if not configured: The key’s existing secret will be used in the specified slot. If the device has no existing secret, the provisioning process will generate a new secret.
- Generate new, random secret, even if a secret is currently configured: A new secret will be generated and programmed to the slot, overwriting any previously configured secret.
- Manually input secret: For advanced users: During the provisioning process, the application will prompt you to input manually an HMAC-SHA1 secret (20 bytes – 40 characters hex-encoded).
Generate Recovery Code: For each user provisioned, a new recovery code will be generated. This recovery code enables the end-user to log in to the system if they have lost their YubiKey.
Note: If you select to save a recovery code while provisioning a user for a second key, any previous recovery code becomes invalid, and only the new recovery code will work.
Create Backup Device for Each User: Use this option to have the provisioning process register two keys for each user, a primary YubiKey and a backup YubiKey. If you do not want to provide recovery codes to your users, it is good practice to give each user a backup YubiKey. For more information, refer to the Primary and Backup Keys section above.
Step 5: Click Next, to select the user(s) to provision. The Select User Accounts page (If there are no local user accounts supported by Yubico Login for Windows, the list will be empty) appears.

Step 6: Select the user accounts to be provisioned during the current run of the Yubico Login for Windows by selecting the checkbox next to the username, and then click Next. The Configuring User page appears.

Step 7: The username shown in the Configuring User field shown above is the user for whom a YubiKey is currently being configured. As each username is displayed, the process prompts you to insert a YubiKey to register for that user.
Step 8: The Wait for Device page is shown while an inserted YubiKey is being detected and before it is registered for the user whose username is in the Configuring User field at the top of the page. If you have selected Create Backup Device for Each User in the Defaults page, the Configuring User field will also display which of the YubiKeys is being registered, Primary or Backup.
Step 9: If you have configured the provisioning process to use a manually specified secret, the field for the 40 hex-digit secrets is displayed. Enter the secret and click Next.
Step 10: The Programming Device page displays the progress of programming each YubiKey. The Device Confirmation page shown below displays the details of the YubiKey detected by the provisioning process, including the device serial number (if available) and the configuration status of each One-Time Password (OTP) slot. If there are conflicts between what you have set as defaults and what is possible with the detected YubiKey, a warning symbol is displayed. If everything is good to go, a check mark will be shown. If the status line shows an error icon, the error is described, and instructions for fixing it are displayed on the screen.

Step 11: Once programming is complete for a user account, that account can no longer be accessed without the corresponding YubiKey. You are prompted to remove the YubiKey just configured, and the provisioning process automatically proceeds to the next user account/YubiKey combination.

Step 12: After all, the YubiKeys for the specified user account have been provisioned:
- If the Generate Recovery Code was selected on the Defaults page, the Recovery Code page is displayed.
- If Generate Recovery Code was not selected, the provisioning process would automatically continue to the next user account.
- The provisioning process moves to Finished after the last user account is done.
The recovery code is a long string. (To eliminate problems caused by the end-user mistaking the numeral 1 for lowercase letter L and 0 for the letter O, the recovery code is encoded in Base32, which treats alphanumeric characters that look similar as if they were the same.)
The Recovery Code page is displayed after all the YubiKeys for the specified user account has been configured.
Step 13: On the Recovery Code page, generate and set a recovery code for the selected user. Once this has been done, the Copy and Save buttons to the right of the recovery code field become available.

Step 14: Copy the recovery code and save it from being shared with the user and keep it in case the user loses it.
Note: Be sure to save the recovery code at this point in the process. Once you proceed to the next screen, it is not possible to retrieve the code.
Step 15: To move to the next user account from the Select Users page, click Next. When you have configured the last user, the provisioning process displays the Finished page.

Step 16: Give each user their recovery code. End-users should save their recovery code to a safe location accessible when they cannot log in.
YubiKey User Experience
When the local user account has been configured to require a YubiKey, the user is authenticated by the Yubico Credential Provider instead of the default Windows Credential Provider. The user is prompted to insert their YubiKey. Then the Yubico Login screen is presented. The user enters their username and password.

Note: It is not necessary to press the button on the YubiKey USB hardware to log in. In some instances, pressing the button causes the login to fail.
When the end-user logs in, they must insert the correct YubiKey into a USB port on their system. If the end-user enters their username and password without inserting the correct YubiKey, authentication will fail, and the user will be presented with an error message.

If an end user’s account is configured for Yubico Login for Windows, and if a recovery code was generated, and a user loses their YubiKey(s), they can use their recovery code to authenticate. The end-user unlocks their computer with their username, recovery code, and password.

Until a new YubiKey is configured, the end-user must enter the recovery code each time they log in.
If Yubico Login for Windows does not detect that a YubiKey has been inserted, it is likely due to the key not having OTP mode enabled, or you are not inserting a YubiKey, but instead a Security Key, which is not compatible with this application. Use the YubiKey Manager application to ensure that all the YubiKeys to be provisioned have the OTP interface enabled.
Important: Alternative sign-in methods supported by Windows will not be affected. You must, therefore, restrict additional local and remote login methods for the user accounts you are protecting with Yubico Login for Windows to ensure you have not left open any ‘back doors.’
If you try out YubiKey, let us know your experience in the comments section below.












