今天,黑客很容易破解不安全的网站。即使是网站或应用程序中的一个漏洞,黑客也很容易使用不同的方法对其进行破解。DDoS攻击是广泛使用的方法之一。使用DDoS攻击,任何小型网站都可以很容易地崩溃。所以,让我们更深入地了解它。

如何使用CMD对网站执行(Website)DDoS 攻击(DDoS Attack)
在学习如何执行DDoS攻击之前,您必须了解什么是DDoS攻击。
什么是 DDoS 攻击?(What is a DDoS attack? )
DDoS(D)代表“(o)分布式(D)拒绝服务”(S)。_ DDoS 攻击是一种网络攻击(cyber-attack),其中犯罪者试图通过暂时中断连接到 Internet 的主机的服务来使其目标用户无法使用网站、网络或机器。此类攻击通常通过同时使用过多请求攻击目标资源(如 Web 服务器、网络、电子邮件等)来进行。因此,服务器无法同时响应所有请求并导致其崩溃或变慢。
分布式拒绝服务 (DDoS) 攻击如何工作?(How Distributed Denial of Service (DDoS) attack works?)
每台服务器都具有一次处理请求的预定义容量,并且当时只能处理该数量的请求。为了对服务器实施DDoS攻击,一次向服务器发送大量请求。因此,服务器与用户之间的数据传输断开。结果,网站因失去分配的带宽而崩溃或暂时关闭。
如何防止 DDoS 攻击?(How to prevent a DDoS attack?)
可以通过以下方式防止 DDoS 攻击:
- 安装安全补丁(security patches)。
- 使用入侵检测系统(intrusion detection systems)来识别甚至阻止任何类型的非法活动。
- 使用防火墙通过识别其 IP 来阻止来自攻击者的所有流量。
- 或者使用通过访问控制列表 ( ACL ) 配置的(ACL)路由器(router)来限制对网络的访问并丢弃可疑的非法流量。
执行 DDoS 攻击的工具(Tools for performing a DDoS attack)
以下是执行DDoS(DDoS)攻击的常用工具。
1. 克星(1. Nemesy)
它用于生成随机数据包。它适用于窗户。由于(Due)程序的性质,如果您有防病毒软件,它很可能会被检测为病毒。
2.土地和LaTierra(2. Land and LaTierra)
此工具用于 IP 欺骗和打开TCP连接。
3. 黑豹(3. Panther)
该工具可用于用多个UDP 数据包(UDP packets)淹没受害者的网络。
如果您想知道如何执行DDoS攻击并关闭任何网站,请继续阅读本文,如本文中所述,提供了使用命令提示符 ( CMD ) 执行(CMD)DDoS攻击的分步方法。
如何使用CMD对网站执行(Website)DDoS 攻击(DDoS Attack)
要使用命令提示符 ( CMD ) 对网站执行DDoS攻击,请执行以下步骤:
注意(Note):为了执行此攻击,您应该拥有良好的互联网连接和无限带宽。
1. 选择要进行DDoS攻击的网站。
2. 按照以下步骤查找该网站的 IP 地址。
一种。打开命令提示符(Open the command prompt)。

湾。输入以下命令并按回车键。
ping www.google.com –t
注意:(Note:) 将(Replace)www.google.com 替换为您要执行DDoS攻击的网站。

C。您将在结果中看到所选网站的 IP 地址。
注意(Note):IP 地址看起来像:xxx.xxx.xxx.xxx

3.获取IP地址后,在命令提示符下输入以下命令。
ping [所选网站的ip地址] -t -l 65500(ping [ip address of selected website] –t –l 65500)
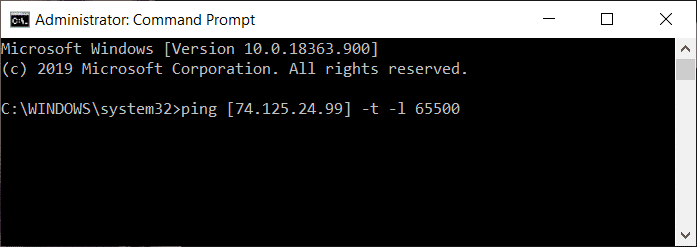
使用上述命令,将用无限的 65500 数据包 ping 受害计算机。
在上面的命令中:
- ping将数据包发送到受害者网站。
- 所选网站的IP地址是受害网站的IP地址
- -t表示应该发送数据包,直到程序停止。
- -l指定要发送到受害者网站的数据负载。
- 值65500是已发送到受害网站的数据包数。
4. 按回车键运行命令并确保运行命令数小时。
注意:(Note:)为了使攻击更有效,您应该使用来自多台计算机的 ping 对受害者的网站执行攻击。为此,只需在多台计算机上同时运行相同的上述命令。
5. 现在,在 2 或 3 小时后访问该网站。您会注意到网站暂时关闭或服务器在那里显示不可用(unavailable)消息。
因此,通过仔细执行每个步骤,您将能够仅使用命令提示符(Command Prompt)对网站执行成功的DDoS攻击,使其关闭或暂时崩溃。

您还可以使用任务管理器(task manager)并通过查看网络活动来查看DDoS攻击对目标网站的影响。
要查看DDoS攻击对目标网站的影响,请按照以下步骤操作。
1.在电脑上打开任务管理器(task manager)。
2. 右键单击并选择启动任务管理器(Start task manager)。
3. 您会注意到菜单栏下有六个选项卡。点击(Click)网络(Networking)_
4. 您将看到类似于下图所示结果的结果。

另请阅读:(Also Read:) 如何在 Windows 10 上安装 Linux Bash Shell(How To Install Linux Bash Shell On Windows 10)
结论是,如果对目标网站的 DDoS 攻击成功(DDoS attack on the targeted website is successful),您将能够看到增加的网络活动,您可以从任务管理器的网络选项卡中轻松验证。
How to Perform a DDoS Attack on a Website using CMD
Today, it is very easy fоr a hacker to hack a website that is not secured. Εven a single loоphole in the website or application makes it easy for the hacker to hack it using different methods. And a DDoS аttack is one of the widely usеd methods for the same. Using a DDoS attack, any small webѕite can bе crashed very easily. So, let us understand it more deeply.

How to Perform a DDoS Attack on a Website using CMD
Before learning how to perform a DDoS attack you must understand what is a DDoS attack.
What is a DDoS attack?
DDoS stands for “Distributed Denial of Service”. A DDoS attack is a cyber-attack in which a perpetrator seeks to make a website, network, or a machine unavailable to its intended user(s) by temporarily disrupting the services of the host connected to the internet. Such attacks are usually carried out by hitting the target resource such as web servers, networks, emails, etc. with too many requests at the same time. Due to this, the server fails to respond to all the requests at the same time and leads to its crashing or slow down.
How Distributed Denial of Service (DDoS) attack works?
Every server has a predefined capacity of handling requests at a time and it can handle only that number of requests at that time. In order to implement a DDoS attack on a server, a large number of requests are sent at a single time to the server. Due to this, the data transmission between the server and the user disconnects. As a result, the website crashes or goes down temporarily as it loses its allotted bandwidth.
How to prevent a DDoS attack?
A DDoS attack can be prevented by:
- Installing security patches.
- Using the intrusion detection systems to identify and even stop any sort of illegal activities.
- Using a Firewall to block all the traffic coming from an attacker by identifying its IP.
- Or by using a router configured via the access control list (ACL) to limit the access to the network and drop the suspected illegal traffic.
Tools for performing a DDoS attack
The following are the tools commonly used for performing a DDoS attack.
1. Nemesy
It is used to generate random packets. It works on windows. Due to the nature of the program, if you have an antivirus, it will most likely be detected as a virus.
2. Land and LaTierra
This tool is used for IP spoofing and opening the TCP connections.
3. Panther
This tool can be used to flood a victim’s network with multiple UDP packets.
If you are curious to know how to perform a DDoS attack and bring down any website, keep reading this article as in this article, a step-by-step method is given to perform a DDoS attack using the command prompt (CMD).
How to Perform a DDoS Attack on a Website using CMD
To perform a DDoS attack on a website using the command prompt (CMD), follow these steps:
Note: In order to perform this attack, you should have a good internet connection with unlimited bandwidth.
1. Select the website on which you want to perform the DDoS attack.
2. Find the IP address of that website by following these steps.
a. Open the command prompt.

b. Enter the below command and hit the enter key.
ping www.google.com –t
Note: Replace www.google.com with the website on which you want to perform the DDoS attack.

c. You will see the IP address of the selected website in the result.
Note: IP address will look like: xxx.xxx.xxx.xxx

3. After getting the IP address, type the below command in the command prompt.
ping [ip address of selected website] –t –l 65500

Using the above command, the victim computer will be pinged with infinite data packets of 65500.
In the above command:
- The ping sends the data packets to the victim website.
- The IP address of the selected website is the IP address of the victim website
- The -t means that the data packets should be sent until the program stops.
- The -l specifies the data load that is to be sent to the victim website.
- The value 65500 is the number of data packets that have been sent to the victim website.
4. Hit the enter button to run the command and make sure to run the command for hours.
Note: In order to make the attack more effective, you should perform an attack on the victim’s website with pings from more than one computer. To do so, just run the same above command on the multiple computers at the same time.
5. Now, visit the website after 2 or 3 hours. You will notice that the website is temporarily down or the server is displaying the unavailable message there.
So, by following each step carefully, you will be able to perform a successful DDoS attack on a website using just Command Prompt to bring it down or temporarily crash it.

You can also see the effect of the DDoS attack on the targeted website using the task manager and by viewing the network activities.
To see the effect of the DDoS attack on the targeted website, follow these steps.
1. Open the task manager on the computer.
2. Right-click and select Start task manager.
3. You will notice six tabs under the menu bar. Click on the Networking
4. You will see the results similar to the results shown in the figure below.

Also Read: How To Install Linux Bash Shell On Windows 10
The conclusion is that if the DDoS attack on the targeted website is successful, you will be able to see the increased network activities which you can easily verify from the networking tab of the task manager.







