如果您在企业工作或拥有企业,那么您需要知道发生网络攻击和诈骗的风险总是很高。电子邮件诈骗(Email Scams)是其中最常见的。网络钓鱼有多种形式,例如Tabnabbing、 Spear 网络钓鱼(Spear Phishing)以及Vishing 和 Smishing。几天前,我们研究了Pharming 在线欺诈(Pharming online frauds)——今天我们将研究捕鲸诈骗(Whaling Scams),它是新兴的网络安全威胁。
什么是捕鲸骗局
在捕鲸(Whaling)诈骗中,您通常会通过电子邮件成为目标——这是一种专门的网络钓鱼诈骗(Phishing scam)。攻击者研究您的在线活动并从其他来源获取有关您的有用信息。该信息用于创建具有专业外观的个性化电子邮件。看到官方电子邮件可能会导致您放弃防御,并且您很可能会信任此类电子邮件。我们的想法是从您那里获取信息以进行进一步的欺诈活动。
现在您必须意识到捕鲸(Whaling)和鱼叉式网络钓鱼之间存在细微差别(Spear Phishing)。 捕鲸(Whaling)通常针对高级管理人员,而后者的骗局通常针对公司的员工,公司的客户。之所以称为捕鲸(Whaling),是因为目标通常很大或很重要。因此选择鲸鱼(Whales)是因为它们在组织内的权威和访问权限。
捕鲸(Whaling)是如何运作的,为什么你会成为目标
大多数目标通常是商人、企业家、首席执行官(CEOs)和企业员工。目标通常是特定于业务的,并且计划攻击的目的是获取有关组织活动的任何敏感信息。
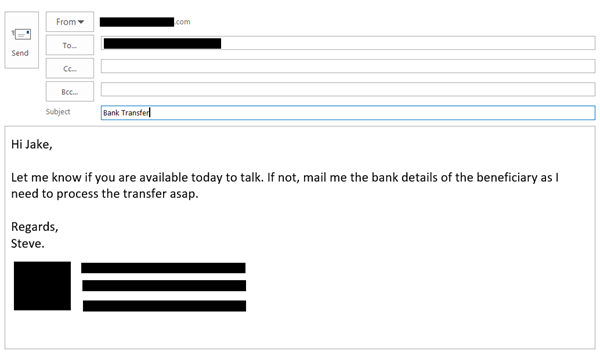
此类社会工程攻击很难识别,人们通常最终会将数据提供给此类诈骗者。诈骗者会从您可能熟悉的地址发送一封个性化的电子邮件。骗子可能会伪装成您的老板或其他友好组织。或者他/她可能会模仿你的财务顾问或律师。电子邮件的内容主要是寻求关注,以便您可以及时回复,并且他们被抓住的机会最小。
该电子邮件可能会要求您转帐一些钱作为到期账单的付款,或者它可能会要求您提供总部所需的一些公司数据。或者它可能会询问有关组织员工的个人详细信息。
诈骗者或攻击者已经对您进行了研究,为您创建了个性化的电子邮件。该研究可能基于您的在线活动或从其他来源获得的任何信息。捕鲸电子邮件(Whaling emails)看起来很正常和完美,这是人们落入陷阱的唯一原因。电子邮件中使用的名称、徽标和其他信息可能是真实的,也可能不是。但它的呈现方式通常人们无法标记这些电子邮件之间的差异。
此外,发件人的电子邮件地址或提及的网站与您可能认识的人相似。附件可能是恶意的,也可能不是恶意的。这些骗局的唯一目的是让您相信该电子邮件是完全正常的,需要采取紧急措施。当您按照电子邮件中的说明进行操作时,您最终会将一些机密数据泄露给未经授权的人员或网站。
如何保护免受捕鲸攻击
您必须学会识别网络钓鱼攻击(identify Phishing Attacks),以了解更多关于一般网络钓鱼防护的信息,这样您就可以避免网络钓鱼诈骗(avoid Phishing scams)。
保持保护的关键是保持专注。端到端阅读所有与工作相关的电子邮件,并留意可疑的事情。如果您只是觉得电子邮件有问题,请联系该电子邮件所在的组织。
1]验证(Verify)发件人的电子邮件,然后只回复电子邮件。通常,您从中接收电子邮件的网站或电子邮件地址与您可能知道的普通电子邮件地址几乎相同。'o' 可以替换为 '0'(零),或者可能有两个 'ss' 而不是一个 's'。这种错误很容易被人眼忽略,这些错误构成了此类攻击的基础。
2] 如果电子邮件需要一些紧急操作,那么您必须仔细查看然后做出决定。如果有任何出站网站链接,请在向该网站提供任何信息之前验证其地址。此外,检查挂锁标志或验证网站的证书。
3] 不要向任何网站或电子邮件提供任何财务或任何联系方式。知道何时信任网站,(Know when to trust a website)在点击任何网络链接之前(precautions before clicking on any web links)采取预防措施,并遵守基本的互联网使用安全规范。
4] 有适当的防病毒、防火墙软件保护您的计算机,并且不要从任何这些电子邮件中下载任何附件。RAR/7z或任何其他可执行文件最怀疑包含任何恶意软件或木马(Trojans)。定期更改密码并在安全位置创建重要文件的备份。
5 ](] Completely)在处理它们之前彻底销毁您的物理文件,以便它们无法提供有关您和您的组织的任何信息。
捕鲸攻击示例
虽然您可以在网上找到大量此类骗局故事。即使是像Snapchat和希捷(Seagate)这样的大公司也落入了这些骗局的陷阱。去年,Snapchat的一名高级员工成为此类骗局的受害者,在该骗局中,一封冒充公司首席执行官的电子邮件询问了员工的工资单。看一些例子:
- 希捷(Seagate):一次成功的捕鲸攻击让窃贼获得了所有现任和前任员工多达 10,000 份 W-2 税务文件。
- Snapchat:一名员工因一封冒充CEO Evan Spiegel请求的电子邮件而堕落,并泄露了 700 名员工的工资数据。
- FACC:这家奥地利飞机工业供应商因捕鲸袭击损失了 5000 万欧元。
- Ubiquiti Networks:这家网络技术公司因捕鲸攻击而损失 3910 万美元。
- Weight Watchers International:一封捕鲸电子邮件让窃贼获得了近 450 名现任和前任雇员的税务数据。
已经被骗了?
你认为你是捕鲸(Whaling)骗局的受害者吗?立即通知您的组织负责人并寻求法律帮助。如果您向他们提供了任何银行详细信息或任何类型的密码,请立即更改它们。请咨询网络安全专家以追溯路径并了解攻击者是谁。寻求法律帮助并咨询律师。
有多种在线服务可供您举报此类诈骗。请举报此类骗局,以免他们的活动受到干扰,让更多人不受影响。
如果您有兴趣了解更多信息,可以免费下载这本名为Whaling, Anatomy of an attack 的优秀电子书。(Whaling, Anatomy of an attack)
保护您自己、您的员工和您的组织免受此类欺诈和在线诈骗。传播信息并帮助您的同事、朋友和家人受到保护。(Protect yourself, your employees and your organization from such frauds and online scams. Spread the word and help your colleagues, friends, and family stay protected.)
在此处阅读有关最常见的在线和电子邮件诈骗和欺诈(most common Online and Email scams & frauds)的信息。
What are Whaling scams & how to protect your Enterprise
If уou work in or own an enterprise, then you need to know that therе is always a high risk of cyber-attacks & scams taking рlace. Emaіl Scаms аre the most common among them. Phishing comes in many flavors like Tabnabbing, Spear Phishing as well as Vishing and Smishing. A few days back, we took a look at Pharming online frauds – today we will take a look at Whaling Scams which is the emerging cyber-security threat.
What are Whaling scams

In Whaling scams, you are targeted usually by email – it is a specialized Phishing scam. The attacker studies your online activity and obtains useful information about you from other sources. And that information is used to create a professional looking personalized e-mail. Seeing an official email can cause you to drop your defenses and you are very likely to trust such email. The idea is to obtain information from you for further fraudulent activities.
Now you have to realize that there is a thin line of difference between Whaling and Spear Phishing. Whaling typically targets high-level executives, whereas the latter scam targets employees of a company, customers of a company generally. It is called Whaling because the targets are usually large or important. And so Whales are chosen because of their authority and access within an organization.
How does Whaling work and why are you targeted

Most of the targets are usually businessmen, entrepreneurs, CEOs, and corporate employees. The targets are usually business specific and attacks are planned for the purpose of obtaining any sensitive information about the activities of an organization.
These kind of socially engineered attacks are very difficult to identify and people usually end up giving data to such scammers. The scammer sends a personalized email from an address you may be familiar with. The scammer may mimic to be your boss or another friendly organization. Or he/she may mimic as your financial consultant or your lawyer. The content of the email is mostly attention seeking so that you may reply promptly and there is the least chance of them getting caught.
The email might require you to transfer some money as a payment to a due bill or it may ask you for some company data that is required at a head office. Or it may ask personal details about the employees of the organization.
The scammer or the attacker has already researched you to create a personalized email for you. And the research may be based upon your online activities or upon any information obtained from other sources. Whaling emails just seem normal and perfect and that is the only reason people fall into the trap. The names, logos and other information used in the email may be real or not. But it is presented in such a way that normally people cannot mark a difference between these emails.
Also, the email address of the sender or the website mentioned is similar to someone you may know. The attachments may or may not be malicious. The sole purpose of these scams is to convince you that the email is completely normal and requires urgent action. And when you follow the instructions in the email, you end up leaking out some confidential data to an unauthorized person or website.
How to stay protected from Whaling attacks
You have to learn to identify Phishing Attacks to know more about protection from phishing in general so that you can avoid Phishing scams.
The key to staying protected is to stay attentive. Read all your work related emails end to end and keep an eye on something fishy. If you just felt that there is something wrong with the email, contact the organization from which the email is said to be.
1] Verify the sender’s email and then only respond to emails. Usually, the websites or email addresses from where you are receiving emails are almost identical to normal email addresses that you may know. An ‘o’ may be replaced with a ‘0’ (zero) or there may be two ‘ss’ instead of one ‘s’. This kind of errors are easily overlooked by a human eye, and these forms the basis of such attacks.
2] If the email requires some urgent action, then you must look carefully and then take the decision. If there are any outbound website links, verify their address before supplying any information to that website. Also, check for the padlock sign or verify the website’s certificate.
3] Do not provide any financial or any contact details to any website or an email. Know when to trust a website, take precautions before clicking on any web links and follow the basic internet usage safety norms.
4] Have proper antivirus, firewall software protecting your computer and do not download any attachments from any of these emails. RAR/7z or any other executable files are most suspected to contain any malware or Trojans. Regularly change passwords and create a backup of important documents at a secure location.
5] Completely destroy your physical documents before disposing of them so that they cannot provide any information about you and your organization.
Whaling attack examples
While you can find a ton of such scam stories online. Even the major companies like Snapchat and Seagate have fallen into the traps of these scams. Last year, a high-rank employee of Snapchat was a victim of such a scam where an email impersonating the CEO of the company inquired about the payroll of the employees. Take a look at some examples:
- Seagate: A successful whaling attack landed thieves up to 10,000 W-2 tax documents for all current and past employees.
- Snapchat: An employee fell for an email impersonating a request from CEO Evan Spiegel and compromised payroll data for 700 employees.
- FACC: The Austrian aircraft industry supplier lost 50 million euros due to a whaling attack.
- Ubiquiti Networks: This networking tech company suffered a $39.1 million loss as a result of a whaling attack.
- Weight Watchers International: A whaling email allowed thieves to obtain tax data for nearly 450 current and former employees.
Already Scammed?
Do you think that you’ve been a victim of a Whaling scam? Immediately inform the head of your organization and seek legal help. If you provided them with any bank details or any sort of passwords, change them immediately. Consult a cyber-security expert to track back the path and know who the attacker was. Seek out for legal help and consult a lawyer.
There are various online services available where you can report such scams. Please report such scams so that their activity can be disrupted and more people are not affected.
If you are interested in knowing more, there is this excellent eBook titled Whaling, Anatomy of an attack, which you can download free.
Protect yourself, your employees and your organization from such frauds and online scams. Spread the word and help your colleagues, friends, and family stay protected.
Read here about the most common Online and Email scams & frauds.


