所有系统管理员用户都有一个非常关心的问题——通过远程桌面(Desktop)连接保护凭据。这是因为恶意软件可以通过桌面连接到达任何其他计算机,并对您的数据构成潜在威胁。这就是为什么当您尝试连接到远程桌面时, Windows 操作系统(Windows OS)会闪烁警告“确保您信任此 PC,连接到不受信任的计算机可能会损害您的 PC ”。(Make sure you trust this PC, connecting to an untrusted computer might harm your PC)
在这篇文章中,我们将了解Windows 10中引入 的Remote Credential Guard功能如何帮助保护Windows 10 Enterprise和Windows Server中的远程桌面凭据。
(Remote Credential Guard)Windows 10中的远程凭据保护
该功能旨在在威胁发展为严重情况之前消除威胁。它通过将Kerberos(Kerberos)请求重定向回请求连接的设备来帮助您通过远程桌面连接保护您的凭据。(Desktop)它还为远程桌面(Remote Desktop)会话提供单点登录体验。
万一发生目标设备被盗用的任何不幸事件,用户的凭证不会被暴露,因为凭证和凭证衍生品都不会发送到目标设备。
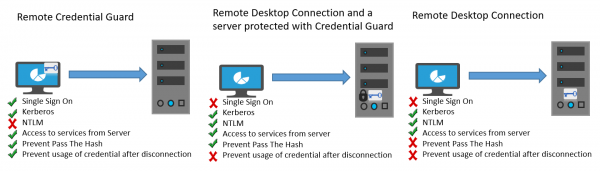
Remote Credential Guard的操作方式与Credential Guard在本地计算机上提供的保护非常相似,只是Credential Guard还通过(Credential Guard)Credential Manager保护存储的域凭据。
个人可以通过以下方式使用Remote Credential Guard -
- 由于管理员(Administrator)凭据具有高度特权,因此必须对其进行保护。通过使用Remote Credential Guard,您可以确保您的凭据受到保护,因为它不允许凭据通过网络传递到目标设备。
- 您组织中的帮助台(Helpdesk)员工必须连接到可能被入侵的已加入域的设备。借助Remote Credential Guard,帮助台员工可以使用RDP连接到目标设备,而不会将其凭据泄露给恶意软件。
硬件和软件要求
要启用Remote Credential Guard的顺利运行,请确保满足远程桌面(Remote Desktop)客户端和服务器的以下要求。
- 远程桌面客户端(Remote Desktop Client)和服务器必须加入 Active Directory 域
- 两台设备必须加入同一个域,或者远程桌面(Remote Desktop)服务器必须加入到与客户端设备的域具有信任关系的域。
- Kerberos身份验证应该已启用。
- 远程桌面(Remote Desktop)客户端必须至少运行Windows 10版本1607 或Windows Server 2016。
- 远程桌面通用 Windows 平台(Remote Desktop Universal Windows Platform)应用不支持远程 Credential Guard(Remote Credential Guard),因此请使用远程桌面(Remote Desktop)经典Windows应用。
通过注册表(Registry)启用远程 Credential Guard(Remote Credential Guard)
要在目标设备上启用Remote Credential Guard,请打开注册表编辑器(Registry Editor)并转到以下项:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa
添加一个名为DisableRestrictedAdmin的新 DWORD 值。将此注册表设置的值设置为0以打开Remote Credential Guard。
关闭注册表编辑器。
您可以通过从提升的 CMD 运行以下命令来启用Remote Credential Guard :
reg add HKLM\SYSTEM\CurrentControlSet\Control\Lsa /v DisableRestrictedAdmin /d 0 /t REG_DWORD
使用组策略(Group Policy)打开Remote Credential Guard
可以通过设置组策略(Group Policy)或使用带有远程桌面连接的参数在客户端设备上使用(Remote Desktop Connection)远程凭据保护(Remote Credential Guard)。
从组策略管理控制台(Group Policy Management Console),导航到Computer Configuration > Administrative Templates > System > Credentials Delegation。
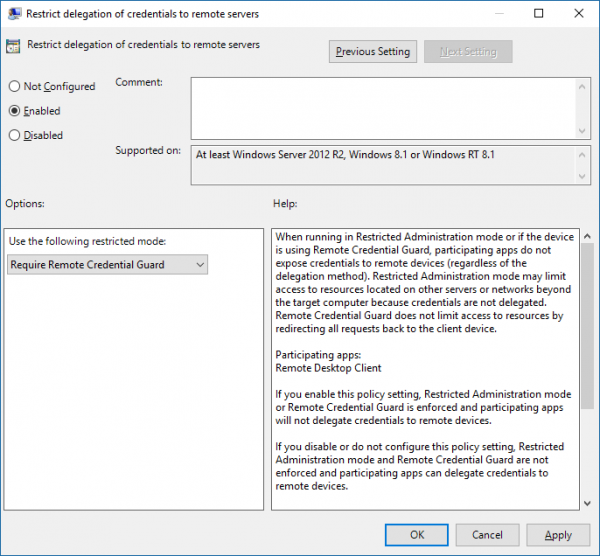
现在,双击“限制将凭据委派给远程服务器(Restrict delegation of credentials to remote servers)”以打开其“属性”框。
现在在使用以下受限模式(Use the following restricted mode)框中,选择需要远程凭据保护。( Require Remote Credential Guard. )另一个选项Restricted Admin mode也存在。它的意义在于当Remote Credential Guard不能使用时,会使用Restricted Admin模式。
在任何情况下,Remote Credential Guard和Restricted Admin模式都不会以明文形式向远程桌面(Remote Desktop)服务器发送凭据。
(Allow Remote Credential Guard)通过选择“首选远程凭据保护(Prefer Remote Credential Guard)”选项,允许远程凭据保护。
单击确定(Click OK)并退出组策略管理控制台(Group Policy Management Console)。
现在,从命令提示符运行gpupdate.exe /force以确保应用组策略(Group Policy)对象。
(Use Remote Credential Guard)使用带有参数的Remote Credential Guard进行远程桌面(Remote Desktop)连接
如果您未在组织中使用组策略(Group Policy),则可以在启动远程桌面连接(Desktop Connection)时添加 remoteGuard 参数,以便为该连接打开远程 Credential Guard(Remote Credential Guard)。
mstsc.exe /remoteGuard
使用Remote Credential Guard(Remote Credential Guard)时应注意的事项
- Remote Credential Guard不能用于连接到已加入Azure Active Directory的设备。
- 远程桌面凭据保护(Remote Desktop Credential Guard)仅适用于RDP协议。
- Remote Credential Guard不包括设备声明。例如,如果您尝试从远程访问文件服务器并且文件服务器需要设备声明,则访问将被拒绝。
- 服务器和客户端必须使用Kerberos进行身份验证。
- 域必须具有信任关系,或者客户端和服务器都必须加入同一个域。
- 远程桌面网关(Remote Desktop Gateway)与Remote Credential Guard不兼容。
- 没有凭据泄露给目标设备。但是,目标设备仍会自行获取Kerberos 服务(Kerberos Service) 票证。(Tickets)
- 最后,您必须使用登录设备的用户的凭据。不允许使用已保存的凭据或与您的不同的凭据。
您可以在Technet上阅读更多相关信息。
相关(Related):如何增加(increase the number of Remote Desktop Connections)Windows 10 中的远程桌面连接数。
Remote Credential Guard protects Remote Desktop credentials
All sуstem administrator users hаve one very genuine concern – securing credentials ovеr а Remote Desktop connectіon. This is because malware can find its way to any other computer over the desktop connection and pose a potential threat to your data. That is why Windows OS flashes a warning “Make sure you trust this PC, connecting to an untrusted computer might harm your PC” when you try to connect to a remote desktop.
In this post, we will see how the Remote Credential Guard feature, which has been introduced in Windows 10, can help protect remote desktop credentials in Windows 10 Enterprise and Windows Server.
Remote Credential Guard in Windows 10
The feature is designed to eliminate threats before it develops into a serious situation. It helps you protect your credentials over a Remote Desktop connection by redirecting the Kerberos requests back to the device that’s requesting the connection. It also provides single sign-on experiences for Remote Desktop sessions.
In the event of any misfortune where the target device is compromised, credentials of the user are not exposed because both credential and credential derivatives are never sent to the target device.

The modus operandi of Remote Credential Guard is very similar to the protection offered by Credential Guard on a local machine except for Credential Guard also protects stored domain credentials via the Credential Manager.
An individual can use Remote Credential Guard in the following ways-
- Since Administrator credentials are highly privileged, they must be protected. By using Remote Credential Guard, you can be assured that your credentials are protected as it does not allow credentials to pass over the network to the target device.
- Helpdesk employees in your organization must connect to domain-joined devices that could be compromised. With Remote Credential Guard, the helpdesk employee can use RDP to connect to the target device without compromising their credentials to malware.
Hardware and software requirements
To enable smooth functioning of the Remote Credential Guard, ensure the following requirements of Remote Desktop client and server are met.
- The Remote Desktop Client and server must be joined to an Active Directory domain
- Both devices must either joined to the same domain, or the Remote Desktop server must be joined to a domain with a trust relationship to the client device’s domain.
- The Kerberos authentication should have been enabled.
- The Remote Desktop client must be running at least Windows 10, version 1607 or Windows Server 2016.
- The Remote Desktop Universal Windows Platform app doesn’t support Remote Credential Guard so, use Remote Desktop classic Windows app.
Enable Remote Credential Guard via Registry
To enable Remote Credential Guard on the target device, open Registry Editor and go to the following key:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa
Add a new DWORD value named DisableRestrictedAdmin. Set the value of this registry setting to 0 to turn on Remote Credential Guard.
Close the Registry Editor.
You can enable Remote Credential Guard by running the following command from an elevated CMD:
reg add HKLM\SYSTEM\CurrentControlSet\Control\Lsa /v DisableRestrictedAdmin /d 0 /t REG_DWORD
Turn on Remote Credential Guard by using Group Policy
It is possible to use Remote Credential Guard on the client device by setting a Group Policy or by using a parameter with Remote Desktop Connection.
From the Group Policy Management Console, navigate to Computer Configuration > Administrative Templates > System > Credentials Delegation.
Now, double-click Restrict delegation of credentials to remote servers to open its Properties box.
Now in the Use the following restricted mode box, choose Require Remote Credential Guard. The other option Restricted Admin mode is also present. Its significance is that when Remote Credential Guard cannot be used, it will use Restricted Admin mode.
In any case, neither Remote Credential Guard nor Restricted Admin mode will send credentials in clear text to the Remote Desktop server.
Allow Remote Credential Guard, by choosing ‘Prefer Remote Credential Guard’ option.
Click OK and exit the Group Policy Management Console.

Now, from a command prompt, run gpupdate.exe /force to ensure that the Group Policy object is applied.
Use Remote Credential Guard with a parameter to Remote Desktop Connection
If you don’t use Group Policy in your organization, you can add the remoteGuard parameter when you start Remote Desktop Connection to turn on Remote Credential Guard for that connection.
mstsc.exe /remoteGuard
Things you should keep in mind when using Remote Credential Guard
- Remote Credential Guard cannot be used to connect to a device that is joined to Azure Active Directory.
- Remote Desktop Credential Guard only works with the RDP protocol.
- Remote Credential Guard does not include device claims. For example, if you’re trying to access a file server from the remote and the file server requires device claim, access will be denied.
- The server and client must authenticate using Kerberos.
- The domains must have a trust relationship, or both the client and the server must be joined to the same domain.
- Remote Desktop Gateway is not compatible with Remote Credential Guard.
- No credentials are leaked to the target device . However, the target device still acquires the Kerberos Service Tickets on its own.
- Lastly, you must use the credentials of the user who is logged into the device. Using saved credentials or credentials that are different than yours are not permitted.
You can read more on this at Technet.
Related: How to increase the number of Remote Desktop Connections in Windows 10.


