网络攻击在过去几年中发生了变化。流氓黑客现在可以接管您的 PC 并锁定文件,除非您准备好付钱给他们。这些类型的攻击被称为勒索软件(Ransomware),它们使用内核级漏洞来尝试以最高权限运行恶意软件,例如WannaCry和Petya勒索软件。为了减轻这些类型的攻击,Microsoft推出了一项功能,允许您启用核心隔离和内存完整性(Core Isolation and Memory Integrity)来防止此类攻击。
Windows Defender 安全中心(Defender Security Center)提供此功能。称为设备安全,(Device Security, )它提供状态报告和设备内置安全功能的管理 - 包括切换功能以提供增强的保护。但是,它不适用于软件级别;硬件也需要支持它。您的固件应支持 虚拟化,(Virtualization,)这使Windows 11/10 PC 能够在容器中运行应用程序,因此它们无法访问系统的其他部分。
您的设备必须满足标准硬件安全要求这意味着您的设备应支持内存完整性和内核隔离,并且还应具备:
- TPM 2.0(也称为您的安全处理器)
- 已启用安全启动
- 环保署
- UEFI 垫
在Windows 11中启用核心隔离(Core Isolation)和内存完整性(Memory Integrity)

这可能是在Windows 11中启用或禁用基于虚拟化的(Windows 11)安全(Security)性的最简单方法。换句话说,您需要启用核心隔离(enable Core isolation)才能完成它。为此,请执行以下操作:
- 在任务栏搜索框中搜索 Windows 安全 (windows security )。
- 单击(Click)单个搜索结果。
- 切换到 设备安全(Device security) 选项卡。
- 单击 核心隔离详细信息(Core isolation details )选项。
- 切换 内存完整性 (Memory integrity )按钮以将其打开。
- 重启你的电脑。
在Windows 11/10中启用核心隔离(Core Isolation)和内存完整性(Memory Integrity)
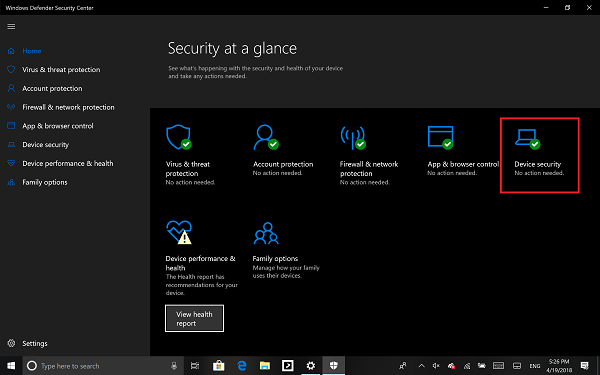
- 以管理员身份登录并打开Windows Defender 安全中心(Windows Defender Security Center)
- 寻找设备安全(Device Security)选项。
- 在这里,您应该检查您的 PC 上是否启用了虚拟化(Virtualization)下的核心隔离。(Core Isolation)
- 核心隔离(Core isolation)提供基于虚拟化的安全功能(y)来保护设备的核心部分。
- 单击(Click)核心(Core)隔离详细信息,您将被提供启用内存完整性(Memory Integrity)。
内存完整性(Memory integrity)(管理程序保护的代码完整性)是核心(Core)隔离的一项安全功能,可防止攻击将恶意代码插入到高安全性进程中。切换(Toggle)以将其打开。
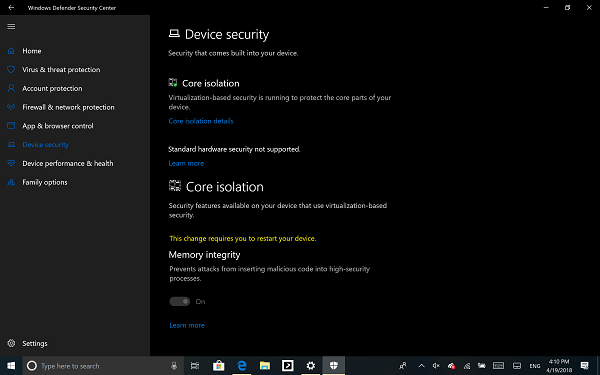
启用后,它将要求您重新启动 PC 以完全启用Memory Integrity。
如果稍后您遇到应用程序兼容性问题,您可能需要将其关闭。
相关(Related):内存完整性显示为灰色或无法打开/关闭。
使用注册表启用或禁用核心隔离(Core Isolation)和内存完整性(Memory Integrity)
您还可以使用注册表,使用(Registry)注册表编辑器(Registry Editor)启用或禁用核心(Core)隔离内存(Memory)完整性,请按照下列步骤操作:
- 按Win+R打开“运行”对话框。
- 键入regedit并点击Enter按钮。
- 单击是(Yes)选项。
- 导航到HKEY_LOCAL_MACHINE中的(HKEY_LOCAL_MACHINE)场景(Scenarios)。
- 右键单击Scenarios > New > Key。
- 将其命名为HypervisorEnforcedCodeIntegrity。
- 右键单击它 >New > DWORD (32-bit) Value。
- 将其命名为Enabled。
- 双击它以将数值(Value)数据设置为1启用,0禁用。
- 单击确定(OK)按钮。
- 重启你的电脑。
要了解有关这些步骤的更多信息,请继续阅读。
注意事项:(Precaution: )在执行REGEDIT步骤之前,不要忘记创建一个系统还原点。
要开始,请按Win+R打开“运行”(Run)对话框,键入 regedit,然后按Enter按钮。如果UAC提示出现在您的屏幕上,请单击是(Yes )选项以打开注册表编辑器。
接下来,导航到以下路径:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\DeviceGuard\Scenarios
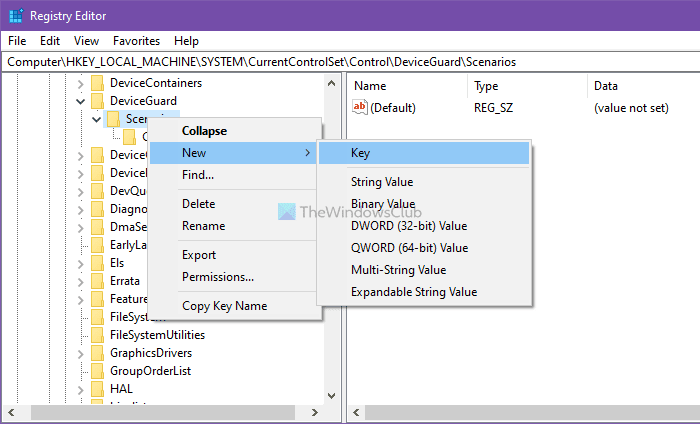
右键单击Scenarios键 > New > Key,并将其命名为HypervisorEnforcedCodeIntegrity。
然后,您必须创建一个REG_DWORD值。为此,右键单击HypervisorEnforcedCodeIntegrity > New > DWORD (32-bit) Value,并将其命名为Enabled。
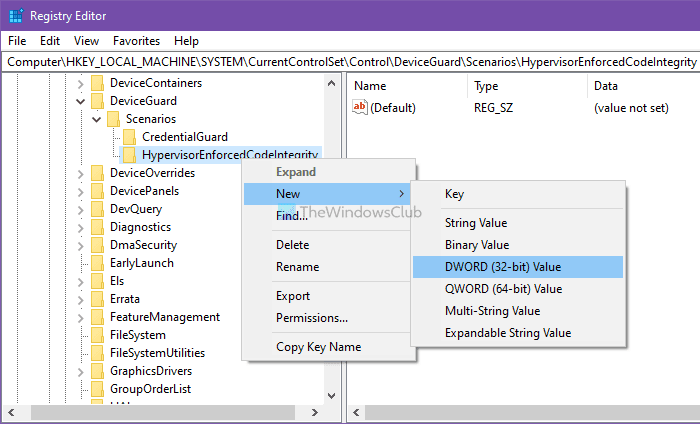
默认情况下,它带有0的(0)值(Value)数据,这意味着它被禁用。但是,如果要启用此功能,请双击它以将Value数据设置为1。
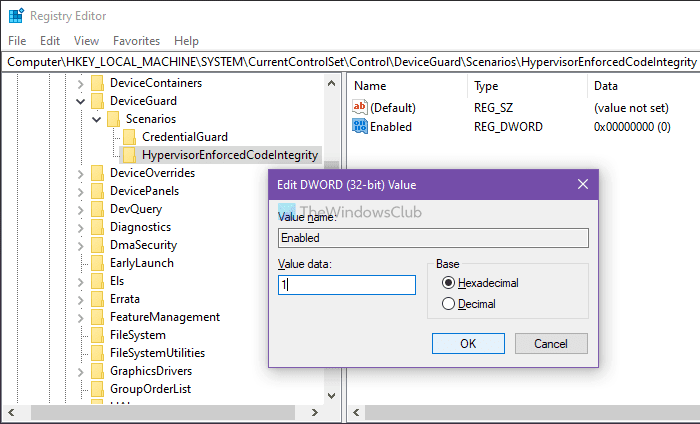
单击确定(OK )按钮并重新启动计算机。
也就是说,根据您的 PC 的硬件,可能还有两个可用的选项。
- (Security Processor)仅当您的 PC 硬件具有可用的TPM时,才会显示安全处理器。它们是由OEM焊接到计算机主板上的离散芯片。为了充分利用TPM,OEM必须小心地将系统硬件和固件与TPM集成,以向其发送命令并对其响应做出反应。较新的TPM(TPMs)还可以为系统硬件本身提供安全和隐私优势。因此,如果您要购买新 PC,请务必检查所有这些。
- 安全启动(Secure Boot)可防止恶意代码在您的操作系统之前加载。它们很难破解,但可以通过安全启动来解决。
当您开始全新安装时, Windows 11/10 还提供Hypervisor 保护的代码完整性(Hypervisor Protected Code Integrity)( HVCI )。使用旧硬件的用户将能够使用Windows Defender 安全中心(Windows Defender Security Center)( WDSC ) 中的 UI 选择加入升级后。此增强功能将确保验证代码完整性的内核进程在安全的运行时环境中运行。
阅读(Read):Windows 11 中未启用基于虚拟化的安全性(Virtualization-based Security not enabled in Windows 11)。
Enable or Disable Core Isolation and Memory Integrity in Windows 11/10
Cyber-attacks havе changed over the past few years. Rogue hackers can now take over your PC and lock down fileѕ unless you are ready tо paу them moneу. These types of attacks are called Ransomware, and they use kernel-level exploits that attempt to run malware with the highest privileges, e.g., WannaCry and Petya ransomware. In order to mitigate these types of attacks, Microsoft has rolled out a feature that allows you to enable Core Isolation and Memory Integrity to prevent such attacks.
Windows Defender Security Center offers this feature. Called Device Security, it offers status reporting and management of security features built into your devices – including toggling features on to provide enhanced protection. However, It doesn’t work on a software level; the hardware needs to support it as well. Your firmware should support Virtualization, which enables the Windows 11/10 PC to run applications in a container, so they don’t get access to other parts of the system.
Your device must meet the requirements for standard hardware security This means your device should support memory integrity and core isolation and also have:
- TPM 2.0 (also referred to as your security processor)
- Secure boot enabled
- DEP
- UEFI MAT
Enable Core Isolation & Memory Integrity in Windows 11

It is probably the easiest way to enable or disable Virtualization-based Security in Windows 11. In other words, you need to enable Core isolation to get it done. For that, do the following:
- Search for windows security in the Taskbar search box.
- Click on the individual search result.
- Switch to the Device security tab.
- Click on the Core isolation details option.
- Toggle the Memory integrity button to turn it on.
- Restart your computer.
Enable Core Isolation & Memory Integrity in Windows 11/10

- Sign in as an administrator and open Windows Defender Security Center
- Look for Device Security option.
- Here you should check if Core Isolation under Virtualization is enabled on your PC.
- Core isolation provides virtualization-based security features to protect core parts of your device.
- Click on Core isolation details, and you will be offered to enable Memory Integrity.
Memory integrity (hypervisor-protected code integrity) is a security feature of Core isolation that prevents attacks from inserting malicious code into high-security processes. Toggle to turn it On.

Once enabled, it will ask you to restart the PC to completely enable Memory Integrity.
If later on, you face application compatibility issues, you may need to turn this off.
Related: Memory Integrity greyed out or won’t Turn On/Off.
Enable or Disable Core Isolation and Memory Integrity using Registry
You can also use the Registry, to enable or disable Core isolation Memory integrity using Registry Editor, follow these steps:
- Press Win+R to open the Run dialog.
- Type regedit and hit the Enter button.
- Click on the Yes option.
- Navigate to Scenarios in HKEY_LOCAL_MACHINE.
- Right-click on Scenarios > New > Key.
- Name it as HypervisorEnforcedCodeIntegrity.
- Right-click on it > New > DWORD (32-bit) Value.
- Name it as Enabled.
- Double-click on it to set the Value data as 1 to enable and 0 to disable.
- Click the OK button.
- Restart your computer.
To learn more about these steps, keep reading.
Precaution: Before heading to the REGEDIT steps, don’t forget to create a System Restore point.
To get started, press Win+R to open the Run dialog, type regedit, and hit the Enter button. If the UAC prompt appears on your screen, click on the Yes option to open the Registry Editor.
Next, navigate to the following path:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\DeviceGuard\Scenarios
Right-click on the Scenarios key > New > Key, and name it as HypervisorEnforcedCodeIntegrity.

Then, you have to create a REG_DWORD value. For that, right-click on HypervisorEnforcedCodeIntegrity > New > DWORD (32-bit) Value, and name it as Enabled.

By default, it comes with a Value data of 0, meaning it is disabled. However, if you want to enable this functionality, double-click on it to set the Value data as 1.

Click the OK button and restart your computer.
That said, there are two more options that might be available depending on the hardware of your PC.
- Security Processor only shows up if you have TPM available with your PC hardware. They are discrete chips soldered to a computer’s motherboard by the OEM. To get the most out of TPM, OEM must carefully integrate system hardware and firmware with the TPM to send it commands and react to its responses. The newer TPMs can also provide security and privacy benefits to the system hardware itself. So make sure to check for all of these if you are buying a new PC.
- Secure Boot prevents malicious code to load up before your OS. They are hard to crack but with secure boot it’s taken care of.
Windows 11/10 also offers Hypervisor Protected Code Integrity (HVCI) when you start with clean installs. Those who are on old hardware, will have the ability to opt-in post the upgrade using the UI in Windows Defender Security Center (WDSC). This enhancement will ensure that the kernel process that verifies code integrity runs in a secure runtime environment.
Read: Virtualization-based Security not enabled in Windows 11.






