什么是路过式下载(Drive-by downloads)?当易受攻击的计算机仅通过访问网站而受到感染时,就会发生偷渡式下载攻击。(Drive-by)Microsoft 安全情报报告(Microsoft Security Intelligence Report)及其前许多卷的调查结果表明,Drive -by Exploit(Drive-by Exploits)已成为最值得担心的网络安全威胁。甚至欧盟网络安全组织、欧洲网络(European Network)和信息安全局(Information Security Agency)( ENISA ) 也同意这一点。
路过式下载
人们普遍认为,路过式(Drive-by)下载攻击仍然是许多攻击者最喜欢的攻击类型。这是因为通过向合法网站注入恶意代码可以很容易地发起攻击。一旦注入,恶意代码可能会利用操作系统、Web 浏览器和 Web 浏览器插件(如Java、Adobe Reader和Adobe Flash )中的(Adobe Flash)漏洞。下载的初始代码通常很小。但是一旦它登陆您的计算机,它将联系另一台计算机并将其余的恶意编码器拉到您的系统中。
简而言之,易受攻击的计算机只需访问此类网站即可感染恶意软件,而无需尝试下载任何内容。此类下载在此人不知情的情况下发生。这些被称为路过式下载。(In short, vulnerable computers can be infected with malware simply by visiting such a website, without attempting to download anything. Such downloads happen without the person’s knowledge. These are called Drive-by downloads.)
新的(New)数据和发现突出了托管不同网络服务器平台的路过式下载网站的相对流行。
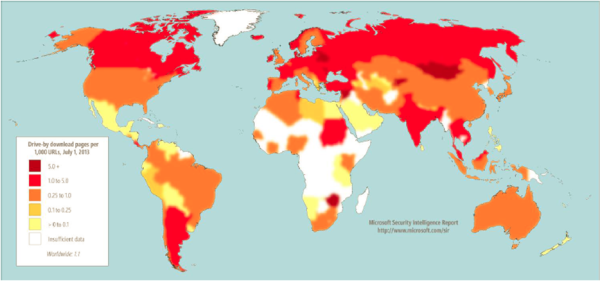
文章中通过数字进行的某些表述可以很好地说明世界各国和地区的免下车下载页面的集中度。在两个季度中,路过式下载URL(URLs)相对集中的位置包括:
- 叙利亚(Syria)——每 1,000 个 URL 有9.5(URLs)个路过 URL(URLs)
- 拉脱维亚(Latvia)– 6.6
- 白俄罗斯(Belarus)– 5.6。
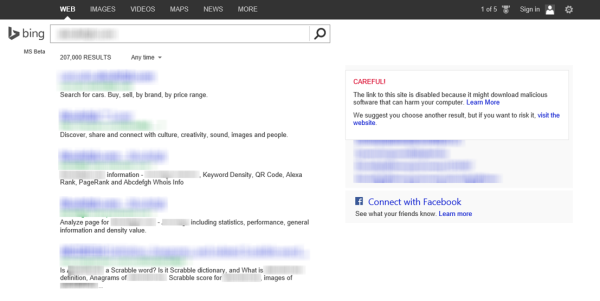
必应在 2013 年第二季度末跟踪了路过式下载(Drive-by Download)集中度。因此,搜索引擎为帮助保护用户免受路过式下载攻击而采取的措施包括在索引网站和显示网站时分析网站是否存在漏洞当路过下载页面的列表出现在搜索结果列表中时的警告消息。
防止路过式下载攻击
TechNet文章为开发人员和IT 专业人员(IT Professionals)提供了管理与偷渡式下载攻击相关的风险的步骤。其中一些措施包括:
防止 Web 服务器被入侵。如果 Web 服务器没有使用最新的安全更新进行更新,它们可能会受到威胁。所以,
- 使服务器的操作系统保持最新
- 这些 Web 服务器上安装的软件(Software)是最新的
- 查看SDL 快速安全参考指南(SDL Quick Security Reference Guides)以获取最新更新
- 避免(Avoid)从 Web 服务器浏览Internet或使用它们打开电子邮件和电子邮件附件。
- (Register)使用Bing(Bing)网站管理员工具和Google 网站管理员(Google Webmaster)注册您的网站,以便搜索引擎在检测到您网站上的不良内容时主动通知您。
作为用户,您可以采取以下预防措施:
- 确保(Make)您的Windows操作系统和网络浏览器是最新的。
- 使用良好的安全软件(good security software )并再次确保它始终具有最新定义
- 使用(Use)最少的浏览器插件,因为它们经常受到损害
- 为您的浏览器使用URL 扫描器插件(URL Scanner addons )也可能是您可能要考虑的一个选项
- 如果您使用Internet Explorer,请确保您的SmartScreen已打开。
- 最后,养成安全浏览的习惯,并选择您经常浏览的网站。
如果您的计算机曾经感染过路过式下载攻击,请告诉我们。
现在阅读(Now read):什么是恶意广告?(What is Malvertising?)
Prevent Drive-by downloads and related malware attacks
What are Drive-by downloads? Drive-by download attacks occur when vulnerable computers get infected by just visiting a website. Findings from Microsoft Security Intelligence Report and many of its previous volumes reveal that Drive-by Exploits have become the top web security threat to worry about. Even the EU cybersecurity group, the European Network and Information Security Agency (ENISA) agree.
Drive-by downloads
It’s accepted that Drive-by download attacks continue to be many attackers’ favorite type of attack. This is because the attack can be easily launched through the injection of malicious code to legitimate websites. Once injected, malicious code may exploit vulnerabilities in operating systems, web browsers, and web browser plugins such as Java, Adobe Reader, and Adobe Flash. The initial code that gets downloaded is usually small. But once it lands on your computer, it will contact another computer and pull the rest of the malicious coder to your system.
In short, vulnerable computers can be infected with malware simply by visiting such a website, without attempting to download anything. Such downloads happen without the person’s knowledge. These are called Drive-by downloads.
New data and findings have highlighted the relative prevalence of drive-by download sites, hosted different web server platforms.
Certain representations made in the article via figures give a fair idea of the concentration of drive-by download pages in countries and regions throughout the world. Locations with relatively high concentrations of drive-by download URLs in both quarters include,
- Syria – 9.5 drive-by URLs for every 1,000 URLs
- Latvia – 6.6
- Belarus – 5.6.

The Drive-by Download concentrations were tracked by Bing at the end of the second quarter of 2013. Accordingly, the measures taken by the search engine to help protect users from drive-by download attacks include analysis of websites for exploits when indexing them and displaying warning messages when listings for drive-by download pages appear in the list of search results.

Prevent Drive-by download attacks
A TechNet article features steps for developers and IT Professionals to be taken for managing the risk related to drive-by download attacks. Some of the measures include:
Preventing web servers from being compromised. Web servers can be compromised if they are not kept updated with the latest security updates. So,
- Keep the server’s operating system(s) up to date
- Software installed on these web servers up to date
- Check out SDL Quick Security Reference Guides for the latest updates
- Avoid browsing the Internet from web servers or using them to open email and email attachments.
- Register your site with Bing webmaster tools and Google Webmaster, so that search engines can proactively inform you if they detect something bad on your site.
As a user, you can take the following precautions:
- Make sure your Windows operating system and web browser is fully up-to-date.
- Use a good security software and again ensure that it has the latest definitions always
- Use minimum browser addons as they often get compromised
- Using a URL Scanner addons for your browser might also be an option you may want to consider
- If you are using Internet Explorer make sure your SmartScreen is turned on.
- And finally, develop a habit of safe browsing and be selective about which sites you browse regularly.
Do let us know if your computer has ever been infected with a drive-by download attack.
Now read: What is Malvertising?


