您可能认为在您的帐户上启用双重身份验证可以使其 100% 安全。双重身份验证(Two-factor authentication)是保护您的帐户的最佳方法之一。但是您可能会惊讶地发现,尽管启用了两因素身份验证,您的帐户仍可能被劫持。在本文中,我们将告诉您攻击者绕过双重身份验证的不同方式。
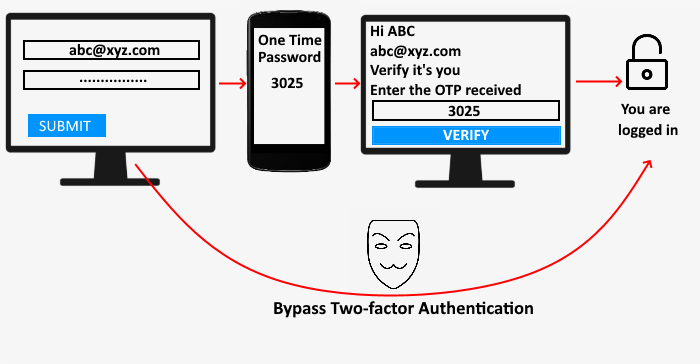
什么是两因素身份验证(Authentication)(2FA)?
在开始之前,让我们看看 2FA 是什么。您知道您必须输入密码才能登录您的帐户。如果没有正确的密码,您将无法登录。2FA 是为您的帐户添加额外安全层的过程。启用后,您无法仅通过输入密码登录您的帐户。您必须再完成一个安全步骤。这意味着在 2FA 中,网站分两步验证用户。
阅读(Read):如何在 Microsoft 帐户中启用两步验证(How to Enable 2-step Verification in Microsoft Account)。
2FA 如何工作?
让我们了解两因素身份验证的工作原理。2FA 要求您验证自己两次。当您输入您的用户名和密码时,您将被重定向到另一个页面,您必须在该页面提供第二个证明,证明您是真正尝试登录的人。网站可以使用以下任何一种验证方法:
OTP(一次性密码)
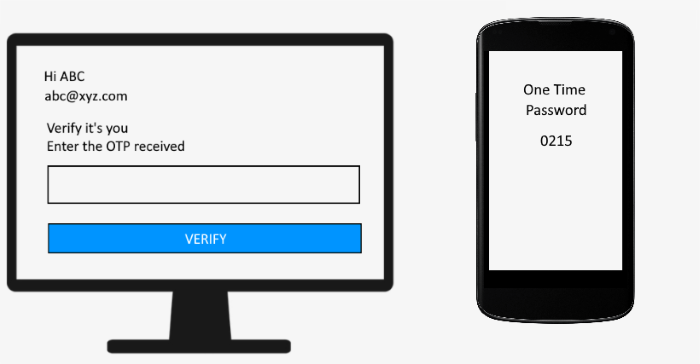
输入密码后,网站会告诉您通过输入您注册的手机号码上发送的OTP来验证自己。(OTP)输入正确的OTP后,您可以登录您的帐户。
提示通知
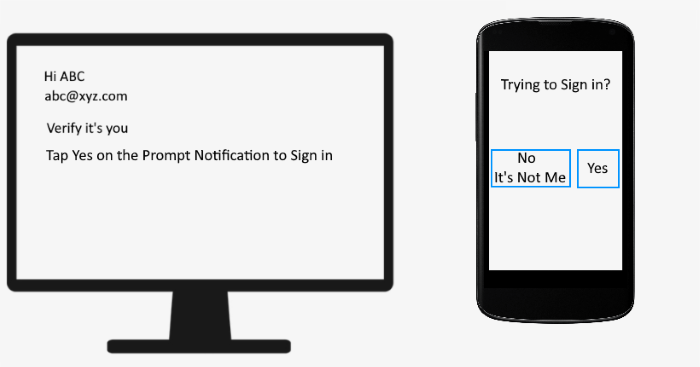
如果您的智能手机连接到互联网,则会在您的智能手机上显示提示通知。您必须通过点击“是(Yes)”按钮来验证自己。之后,您将在 PC 上登录您的帐户。
备用代码
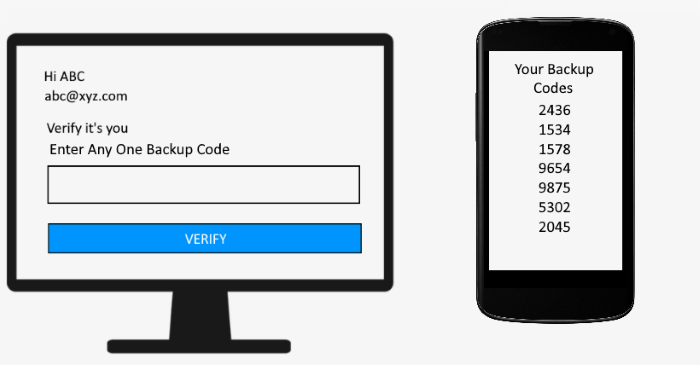
(Backup)当上述两种验证方法不起作用时,备用代码很有用。您可以通过输入从您的帐户下载的任何一个备份代码来登录您的帐户。
身份验证器应用
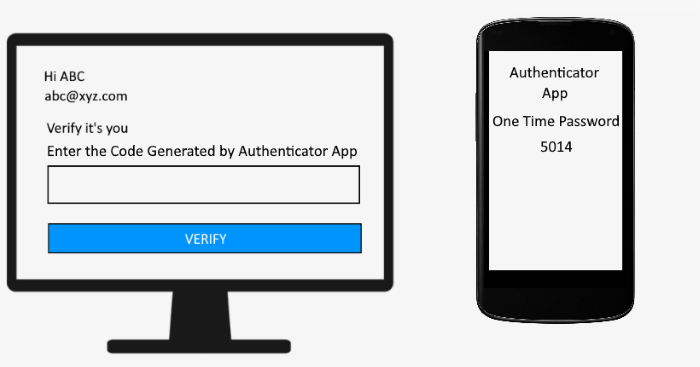
在这种方法中,您必须将您的帐户与验证器应用程序连接起来。每当您想登录您的帐户时,您都必须输入安装在智能手机上的身份验证器应用程序上显示的代码。
网站可以使用其他几种验证方法。
阅读(Read):如何向您的 Google 帐户添加两步验证(How To Add Two-step Verification To Your Google Account)。
黑客如何绕过两因素身份验证(Two-factor Authentication)
毫无疑问,2FA 让您的帐户更加安全。但是黑客仍然有很多方法可以绕过这个安全层。
1] Cookie窃取(Cookie Stealing)或会话劫持(Session Hijacking)
cookie窃取或会话劫持(Cookie stealing or session hijacking)是窃取用户会话cookie的方法。一旦黑客成功窃取了会话cookie,他就可以轻松绕过双因素身份验证。攻击者知道许多劫持方法,如会话固定、会话嗅探、跨站点脚本、恶意软件攻击等。Evilginx是黑客用来执行中间人攻击的流行框架之一。在这种方法中,黑客向用户发送钓鱼链接,将他带到代理登录页面。当用户使用 2FA 登录他的帐户时,Evilginx 会(Evilginx)捕获他的登录凭据以及身份验证代码。由于OTP使用后过期并且在特定时间范围内有效,捕获验证码没有用。但是黑客拥有用户的会话 cookie,他可以使用它来登录他的帐户并绕过双重身份验证。
2]重复代码生成
如果您使用过Google Authenticator应用程序,您就会知道它会在特定时间后生成新代码。Google Authenticator和其他身份验证器应用程序使用特定的算法。随机(Random)码生成器通常以种子值开始以生成第一个数字。该算法然后使用这个第一个值来生成剩余的代码值。如果黑客能够理解这个算法,他可以很容易地创建一个重复的代码并登录到用户的帐户。
3]蛮力
蛮力(Brute Force)是一种生成所有可能的密码组合的技术。使用暴力破解密码的时间取决于其长度。密码越长,破解它所需的时间就越多。通常,验证码长度为 4 到 6 位,黑客可以尝试暴力破解 2FA。但是今天,蛮力攻击的成功率较低。这是因为验证码仅在短时间内有效。
4]社会工程学
社会工程是一种攻击者试图欺骗用户的思想并强迫他在虚假登录页面上输入登录凭据的技术。无论攻击者是否知道您的用户名和密码,他都可以绕过双重身份验证。如何?让我们来看看:
让我们考虑攻击者知道您的用户名和密码的第一种情况。他无法登录您的帐户,因为您启用了 2FA。为了获取代码,他可以向您发送一封带有恶意链接的电子邮件,让您担心如果您不立即采取行动,您的帐户可能会被黑客入侵。当您单击该链接时,您将被重定向到模仿原始网页真实性的黑客页面。输入密码后,您的帐户将被黑客入侵。
现在,让我们再看一个黑客不知道您的用户名和密码的情况。同样(Again),在这种情况下,他会向您发送网络钓鱼链接并窃取您的用户名和密码以及 2FA 代码。
5] OAuth
OAuth集成为用户提供了使用第三方帐户登录其帐户的便利。它是一个著名的 Web 应用程序,它使用授权令牌来证明用户和服务提供商之间的身份。您可以考虑使用 OAuth(OAuth)作为登录帐户的替代方式。
OAuth机制的工作方式如下:
- 站点 A 向站点 B(Site B)(例如Facebook)请求身份验证令牌。
- 站点 B(Site B)认为请求是由用户生成的,并验证用户的帐户。
- 然后站点 B(Site B)发送回调代码并让攻击者登录。
在上述过程中,我们看到攻击者不需要通过 2FA 验证自己。但是要使这种绕过机制起作用,黑客应该拥有用户的帐户用户名和密码。
这就是黑客可以绕过用户帐户的双重身份验证的方式。
如何防止2FA绕过?
黑客确实可以绕过双因素身份验证,但在每种方法中,他们都需要通过欺骗获得用户的同意。在不欺骗用户的情况下,绕过 2FA 是不可能的。因此(Hence),您应该注意以下几点:
- 在点击任何链接之前,请检查其真实性。您可以通过检查发件人的电子邮件地址来做到这一点。
- 创建一个(Create a strong password)包含字母、数字和特殊字符组合的强密码。
- 仅使用(Use)正版身份验证器应用程序,例如Google身份验证器、Microsoft身份验证器等。
- 下载(Download)备份代码并将其保存在安全的地方。
- 永远不要相信黑客用来欺骗用户的网络钓鱼电子邮件。
- 不要与任何人共享安全代码。
- 在您的帐户上设置(Setup)安全密钥,替代 2FA。
- 保持定期更改密码。
阅读(Read):让黑客远离您的 Windows 计算机的提示(Tips to Keep Hackers out of your Windows computer)。
结论
双重身份验证是一种有效的安全层,可保护您的帐户免遭劫持。黑客总是希望有机会绕过 2FA。如果您了解不同的黑客机制并定期更改密码,则可以更好地保护您的帐户。
How Hackers can get around Two-factor Authentication
You may think that enabling two-faсtor authentication on your аccount makеs it 100% secure. Two-factor authentication is among the best methods to protect your account. But you may be surprised to hear that your account can be hijacked despite enabling two-factor authentication. In this article, we will tell you the different ways by which attackers can bypass two-factor authentication.

What is Two-factor Authentication (2FA)?
Before we begin, let’s see what 2FA is. You know that you have to enter a password to log into your account. Without the correct password, you cannot log in. 2FA is the process of adding an extra security layer to your account. After enabling it, you cannot log into your account by entering the password only. You have to complete one more security step. This means in 2FA, the website verifies the user in two steps.
Read: How to Enable 2-step Verification in Microsoft Account.
How Does 2FA Work?
Let’s understand the working principle of two-factor authentication. The 2FA requires you to verify yourself two times. When you enter your username and password, you will be redirected to another page, where you have to provide a second proof that you are the real person trying to log in. A website can use any of the following verification methods:
OTP (One Time Password)

After entering the password, the website tells you to verify yourself by entering the OTP sent on your registered mobile number. After entering the correct OTP, you can log into your account.
Prompt Notification

Prompt notification is displayed on your smartphone if it is connected to the internet. You have to verify yourself by tapping on the “Yes” button. After that, you will be logged into your account on your PC.
Backup Codes

Backup codes are useful when the above two methods of verification won’t work. You can log into your account by entering any one of the backup codes you have downloaded from your account.
Authenticator App

In this method, you have to connect your account with an authenticator app. Whenever you want to log into your account, you have to enter the code displayed on the authenticator app installed on your smartphone.
There are several more methods of verification that a website can use.
Read: How To Add Two-step Verification To Your Google Account.
How Hackers can get around Two-factor Authentication
Undoubtedly, 2FA makes your account more secure. But there are still many ways by which hackers can bypass this security layer.
1] Cookie Stealing or Session Hijacking
Cookie stealing or session hijacking is the method of stealing the session cookie of the user. Once the hacker gets success in stealing the session cookie, he can easily bypass the two-factor authentication. Attackers know many methods of hijacking, like session fixation, session sniffing, cross-site scripting, malware attack, etc. Evilginx is among the popular frameworks that hackers use to perform a man-in-the-middle attack. In this method, the hacker sends a phishing link to the user that takes him to a proxy login page. When the user logs into his account using 2FA, Evilginx captures his login credentials along with the authentication code. Since the OTP expires after using it and also valid for a particular time frame, there is no use in capturing the authentication code. But the hacker has the user’s session cookies, which he can use to log into his account and bypass the two-factor authentication.
2] Duplicate Code Generation
If you have used the Google Authenticator app, you know that it generates new codes after a particular time. Google Authenticator and other authenticator apps work on a particular algorithm. Random code generators generally start with a seed value to generate the first number. The algorithm then uses this first value to generate the remaining code values. If the hacker is able to understand this algorithm, he can easily create a duplicate code and log into the user’s account.
3] Brute Force
Brute Force is a technique to generate all the possible password combinations. The time for cracking a password using brute force depends on its length. The longer the password is, the more time it takes to crack it. Generally, the authentication codes are from 4 to 6 digits long, hackers can try a brute force attempt to bypass the 2FA. But today, the success rate of brute force attacks is less. This is because the authentication code remains valid only for a short period.
4] Social Engineering
Social Engineering is the technique in which an attacker tries to trick the user’s mind and forces him to enter his login credentials on a fake login page. No matter whether the attacker knows your username and password or not, he can bypass the two-factor authentication. How? Let’s see:
Let’s consider the first case in which the attacker knows your username and password. He cannot log into your account because you have enabled 2FA. To get the code, he can send you an email with a malicious link, creating a fear in you that your account can be hacked if you do not take immediate action. When you click on that link, you will be redirected to the hacker’s page that mimics the authenticity of the original webpage. Once you enter the passcode, your account will be hacked.
Now, let’s take another case in which the hacker does not know your username and password. Again, in this case, he sends you a phishing link and steals your username and password along with the 2FA code.
5] OAuth
OAuth integration provides users with a facility to log into their account using a third-party account. It is a reputed web application that uses authorization tokens to prove identity between the users and service providers. You can consider OAuth an alternate way to log into your accounts.
An OAuth mechanism works in the following way:
- Site A requests Site B (e.g. Facebook) for an authentication token.
- Site B considers that the request is generated by the user and verifies the user’s account.
- Site B then sends a callback code and lets the attacker sign in.
In the above processes, we have seen that the attacker does not require to verify himself via 2FA. But for this bypass mechanism to work, the hacker should have the user’s account username and password.
This is how hackers can bypass the two-factor authentication of a user’s account.
How to prevent 2FA bypassing?
Hackers can indeed bypass the two-factor authentication, but in each method, they need the users’ consent which they get by tricking them. Without tricking the users, bypassing 2FA is not possible. Hence, you should take care of the following points:
- Before clicking on any link, please check its authenticity. You can do this by checking the sender’s email address.
- Create a strong password that contains a combination of alphabets, numbers, and special characters.
- Use only genuine authenticator apps, like Google authenticator, Microsoft authenticator, etc.
- Download and save the backup codes at a safe place.
- Never trust phishing emails that hackers use to trick the users’ minds.
- Do not share security codes with anyone.
- Setup security key on your account, an alternative to 2FA.
- Keep changing your password regularly.
Read: Tips to Keep Hackers out of your Windows computer.
Conclusion
Two-factor authentication is an effective security layer that protects your account from hijacking. Hackers always want to get a chance to bypass 2FA. If you are aware of different hacking mechanisms and change your password regularly, you can protect your account better.





