本勒索软件(Ransomware)预防和保护指南着眼于勒索软件(Ransomware)预防以及您可以采取的阻止和预防勒索软件(Ransomware)的步骤,勒索软件是一种新的恶意软件,它会因错误的原因到处传播新闻。
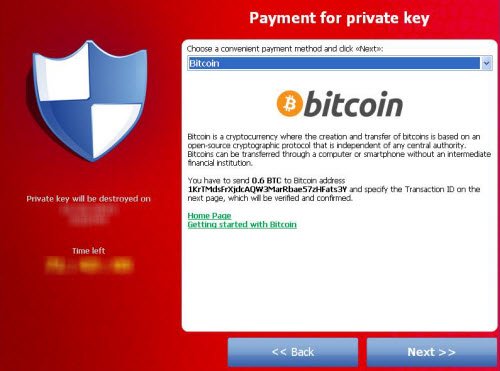
我们一次(Time)又一次地了解威胁,以及对计算机用户构成危险的勒索软件等恶意软件的新变种。(Ransomware)勒索软件病毒会锁定对文件或您的计算机的访问权限,并要求向创建者支付赎金以重新获得访问权限,通常通过匿名预付现金券或比特币(Bitcoin)允许。除了FBI勒索软件 Crilock(Crilock) & Locker之外,最近成功引起关注的一种特定勒索软件威胁是Cryptolocker。
勒索软件的特殊之处在于它可能单独出现(通常通过电子邮件),也可能通过后门或下载程序作为附加组件出现。当您单击电子邮件、即时消息、社交网站或受感染网站中的恶意链接或下载并打开恶意电子邮件附件时,您的计算机可能会感染勒索软件。此外,就像臭名昭著的病毒一样,它可能不会被大多数防病毒程序检测到。即使您的防病毒软件能够删除勒索软件,很多时候,您也只会留下一堆锁定的文件和数据!
如何防止勒索软件
尽管情况令人担忧,并且在大多数情况下,如果您不遵守恶意软件作者的规则,结果是致命的——因为加密的文件可能会损坏到无法修复的地步——但您可以采取某些预防措施来避免问题的发生。您可以防止勒索软件加密!让我们看看您可以采取的一些勒索软件预防措施。(Ransomware prevention steps)这些步骤可以帮助您阻止和防止勒索软件(Ransomware)。
更新的操作系统和安全软件(Updated OS & security software)
不用说,您使用的是完全更新的现代操作系统(fully updated modern operating system),如 Windows 10/8/7、优秀的防病毒软件(antivirus software)或Internet 安全套件(Internet Security Suite)(good antivirus software or an Internet Security Suite)、更新的安全浏览器(updated secure browser)和更新的电子邮件客户端(updated email client)。将您的电子邮件客户端设置为阻止 .exe 文件(block .exe files)。
恶意软件(Malware)作者发现运行过时操作系统版本的计算机用户很容易成为攻击目标。众所周知,它们拥有一些漏洞,这些臭名昭著的犯罪分子可以利用这些漏洞悄悄地进入您的系统。因此,修补或更新您的软件。使用信誉良好的安全套件。始终建议运行结合了反恶意软件和软件防火墙的程序,以帮助您识别威胁或可疑行为,因为恶意软件作者经常发送新变种,以试图避免检测。您可能想阅读这篇关于勒索软件技巧和浏览器行为的文章。
阅读有关Windows 10 中的勒索软件保护的(Ransomware protection in Windows 10)信息。(Read about Ransomware protection in Windows 10.)
备份您的数据(Back up your data)
您当然可以通过定期备份(regular backups)将您的机器感染勒索软件(Ransomware)时造成的损害降到最低。事实上,微软(Microsoft)已经全力以赴,表示备份是对抗包括 Cryptolocker 在内的勒索软件的最佳防御。
切勿单击未知链接或从未知来源下载附件(Never click on unknown links or download attachments from unknown sources)
这个很重要。电子邮件(Email)是勒索软件(Ransomware)用来进入您计算机的常用载体。所以永远不要点击任何你认为可疑的链接。即使你有 1% 的怀疑——不要!附件也是如此。您当然可以从朋友、亲戚和同事那里下载您期望的附件,但要非常小心您甚至可能从您的朋友那里收到的邮件转发。在这种情况下要记住的一条小规则:如果有疑问 - 不要(If in doubt – DONT)!查看打开电子邮件附件(when opening email attachments)或单击 Web 链接(clicking on web links)之前要采取的预防措施。
RansomSaver是 Microsoft Outlook的一个非常有用的插件,可检测并阻止附有勒索软件恶意软件文件的电子邮件。
显示隐藏的文件扩展名(Show hidden file-extension)
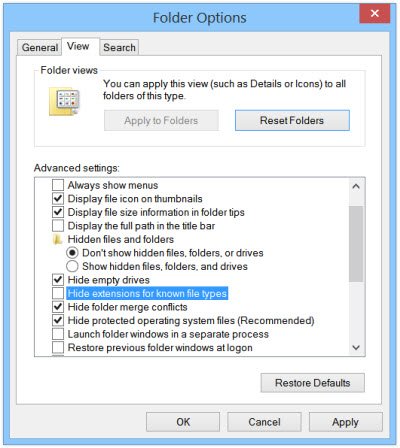
作为Cryptolocker的入口路径的文件之一是以扩展名“.PDF.EXE”命名的文件。恶意软件(Malware)喜欢将它们的 .exe 文件伪装成看起来无害的.pdf。.doc 或 .txt 文件。如果您启用该功能以查看完整的文件扩展名,则可以更轻松地发现可疑文件并首先消除它们。要显示隐藏的文件扩展名,请执行以下操作:
打开控制面板(Control Panel)并搜索文件夹(Folder) 选项(Options)。在View选项卡下,取消选中Hide extensions for known file types选项。
Click Apply > OK.现在,当您检查文件时,文件名将始终带有扩展名,如.doc、.pdf、.txt等。这将帮助您查看文件的真实扩展名。
Disable files running from AppData/LocalAppData folders
尝试在Windows中创建和执行规则,或使用某些入侵防御软件,以禁止多个勒索软件(包括 Cryptolocker)使用的特定显着行为从(Ransomware)App Data(Cryptolocker)或(App Data)Local App Data(Local App Data)文件夹运行其可执行文件。Cryptolocker 预防工具包(Cryptolocker Prevention Kit)是由Third Tier创建的工具,可自动执行组策略(Group Policy)以禁用从App Data和Local App Data文件夹运行的文件,以及禁用从Temp运行的可执行文件(Temp)各种解压缩实用程序的目录。
应用程序白名单(Application whitelisting)
应用程序白名单是大多数 IT 管理员用来防止未经授权的可执行文件或程序在其系统上运行的良好做法。当您这样做时,只有您列入白名单的软件才能在您的系统上运行,因此,未知的执行文件、恶意软件或勒索软件将无法运行。了解如何将程序列入白名单。
禁用 SMB1(Disable SMB1)
SMB或服务器消息块(Server Message Block)是一种网络文件共享协议,用于在计算机之间共享文件、打印机等。共有三个版本 -服务器消息块(Server Message Block)( SMB ) 版本 1 ( SMBv1 )、SMB版本 2 ( SMBv2 ) 和SMB版本 3 ( SMBv3 )。出于安全原因,建议您禁用 SMB1 。
使用 AppLocker(Use AppLocker)
使用(Use)Windows 内置功能AppLocker阻止用户安装或运行 Windows 应用商店应用程序(prevent Users from installing or running Windows Store Apps )并控制应运行哪些软件。您可以相应地配置您的设备,以减少Cryptolocker勒索软件感染的机会。
您还可以通过阻止未签名的可执行文件来使用它来缓解勒索软件,例如:
- <用户配置文件>AppDataLocalTemp
- \AppData\Local\Temp\ *
- AppDataLocalTemp**
这篇文章将告诉您如何使用 AppLocker(create rules with AppLocker)为可执行文件创建规则,并将应用程序列入白名单。
使用 EMET(Using EMET)
增强的缓解体验工具包可保护 Windows 计算机免受网络攻击和未知攻击。它检测并阻止通常用于利用内存损坏漏洞的利用技术。它可以防止漏洞利用删除木马(Trojan),但是如果您单击打开文件,它将无法提供帮助。更新(UPDATE):此工具现在不可用。Windows 10 Fall Creators Update将包含EMET作为Windows Defender的一部分,因此该操作系统的用户无需使用它。
保护 MBR
使用MBR 过滤器(MBR Filter)保护计算机的主引导记录(Master Boot Record)。
禁用远程桌面协议(Disable Remote Desktop Protocol)
大多数勒索软件(Ransomware),包括Cryptolocker恶意软件,都试图通过(Cryptolocker)远程桌面协议(Remote Desktop Protocol)( RDP )访问目标计算机,这是一种允许远程访问您的桌面的Windows实用程序。(Windows)因此,如果您发现RDP对您没有用处,请禁用远程桌面(disable remote desktop)以保护您的计算机免受File Coder和其他RDP漏洞的攻击。
禁用 Windows 脚本宿主(Disable Windows Scripting Host)
恶意软件(Malware)和勒索软件系列经常利用WSH运行 .js 或 .jse 文件来感染您的计算机。如果您没有使用此功能,您可以禁用 Windows 脚本主机以确保安全。
使用勒索软件预防或删除工具(Use Ransomware prevention or removal tools)
使用好的免费反勒索软件(free anti-ransomware software)。BitDefender AntiRansomware和RansomFree是其中一些不错的选择。您可以使用RanSim Ransomware Simulator来检查您的计算机是否受到足够的保护。
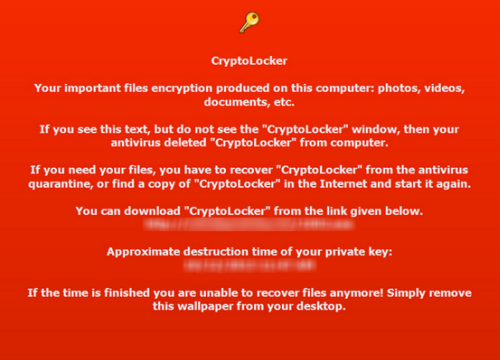
如果勒索软件完全阻止对您的计算机的访问,甚至限制对某些重要功能的访问,(Ransomware)卡巴斯基 WindowsUnlocker 会很有用,因为它可以清理受勒索软件感染的注册表(Registry)。
如果您可以识别勒索软件,它可以使事情变得更容易一些,因为您可以使用可用于该特定勒索软件的勒索软件解密工具。(If you can identify the ransomware, it can make things a bit easier as you can use the ransomware decryption tools that may be available for that particular ransomware.)
这是可以帮助您解锁文件的免费勒索软件解密工具列表。(Ransomware Decryptor Tools)
立即断开网络连接(Disconnect from the Internet immediately)
如果您怀疑某个文件,请在文件完成加密之前迅速停止与 C&C 服务器的通信。为此,只需立即断开自己与互联网(Internet)、WiFi或您的网络(Network)的连接,因为加密过程需要时间,因此虽然您无法消除勒索软件(Ransomware)的影响,但您当然可以减轻损害。
使用系统还原回到已知干净的状态(Use System Restore to get back to a known-clean state)
如果您在Windows机器上启用了系统还原,我坚持认为您已经启用,请尝试将您的系统恢复到已知的干净状态。这不是一个万无一失的方法,但是,在某些情况下,它可能会有所帮助。
重新设置 BIOS 时钟(Set the BIOS clock back)
大多数勒索软件(Ransomware),包括Cryptolocker或FBI 勒索软件,都会提供您可以付款的截止日期或时限。如果延长,解密密钥的价格可能会大幅上涨,而且 - 你甚至无法讨价还价。您至少可以尝试通过将BIOS时钟设置回截止时间窗口结束之前的时间来“击败时钟”。唯一的办法是,当所有技巧都失败时,它会阻止您支付更高的价格。大多数勒索软件会为您提供3-8 天的期限,甚至可能需要高达 300 美元或更多的费用来解锁您锁定的数据文件。
虽然勒索软件的大多数目标群体都在美国和英国,但没有地域限制。任何人都可能受到它的影响——而且随着时间的推移,越来越多的勒索软件被检测到。因此,请采取一些措施来防止勒索软件进入您的计算机。这篇文章更多地讨论了勒索软件攻击和常见问题解答(Ransomware Attacks & FAQ)。
(While most of the targeted groups by Ransomware have been in the US and the UK, there exists no geographical limit. Anyone can be affected by it – and with every passing day, more and more ransomware malware is being detected. So take some steps to prevent Ransomware from getting onto your computer. This post talks a little more about Ransomware Attacks & FAQ.)
现在阅读:(Now read:) 勒索软件攻击后该怎么办(What to do after a Ransomware attack)。
How to protect against and prevent Ransomware attacks & infections
This Ransomware prevention & protection guide takes а look at Ransomware prevention and the steps you can take to block & prevent Ransomware, the new malware which making news all around for thе wrong reasons.
Time and again we learn about threats, and new variants of malware such as Ransomware that pose a danger to computer users. The ransomware virus locks access to a file or your computer and demands that a ransom be paid to the creator for regaining access, usually allowed via either an anonymous pre-paid cash voucher or Bitcoin. One specific ransomware threat that has managed to attract attention in recent times, is Cryptolocker, apart from FBI ransomware, Crilock & Locker.
The specialty of the ransomware is that it may come on its own (often by email) or by way of a backdoor or downloader, brought along as an additional component. Your computer could get infected with ransomware, when you click on a malicious link in an email, an instant message, a social networking site or in a compromised website – or if you download and open a malicious email attachment. Moreover, like a notorious virus, it may go undetected by most antivirus programs. And even if your antivirus software is able to remove the ransomware, many a time, you will just be left with a bunch of locked files and data!

How to prevent Ransomware
While the situation is worrisome and the outcome is fatal in most cases if you fail to comply with the malware author’s rules – since the encrypted files can be damaged beyond repair – you can take certain preventive measures to keep the problem at bay. You can prevent ransomware encryption! Let us see some of the Ransomware prevention steps you can take. These steps can help you block & prevent Ransomware.
Updated OS & security software
Goes without saying that you use a fully updated modern operating system like Windows 10/8/7, a good antivirus software or an Internet Security Suite and an updated secure browser, and an updated email client. Set your email client to block .exe files.
Malware authors find computer users, who are running outdated versions of OS, to be easy targets. They are known to possess some vulnerabilities which these notorious criminals can exploit to silently get onto your system. So patch or update your software. Use a reputable security suite. It is always advisable to run a program that combines both anti-malware software and a software firewall to help you identify threats or suspicious behavior as malware authors frequently send out new variants, to try to avoid detection. You might want to read this post on Ransomware tricks & Browser behaviors.
Read about Ransomware protection in Windows 10.
Back up your data
You can certainly minimize the damage caused in the case of your machine getting infected with Ransomware by taking regular backups. In fact, Microsoft has gone all out and said that backup is the best defense against Ransomware including Cryptolocker.
Never click on unknown links or download attachments from unknown sources
This is important. Email is a common vector used by Ransomware to get on your computer. So never ever click on any link which you may think looks suspicious. Even if you have a 1% doubt – don’t! The same holds true for attachments too. You can surely download attachments you are expecting from friends, relatives & associates, but be very careful of the mail forwards which you may receive even from your friends. A small rule to remember in such scenarios: If in doubt – DONT! Take a look at the precautions to take when opening email attachments or before clicking on web links.
RansomSaver is a very useful add-in for Microsoft’s Outlook that detects and blocks emails that have ransomware malware files attached to them.
Show hidden file-extension

One file that serves as the entry route for Cryptolocker is the one named with the extension “.PDF.EXE”. Malware like to disguise their .exe files as harmless looking .pdf. .doc or .txt files. If you enable the feature to see the full file extension, it can be easier to spot suspicious files and eliminate them in the first place. To show hidden file extensions, do the following:
Open Control Panel and search for Folder Options. Under the View tab, uncheck the option Hide extensions for known file types.
Click Apply > OK. Now when you check your files, the file names will always appear with their extensions like .doc, .pdf, .txt, etc. This will help you in seeing the real extensions of the files.
Disable files running from AppData/LocalAppData folders
Try to create and enforce rules within Windows, or use some Intrusion Prevention Software, to disallow a particular, notable behavior used by several Ransomware, including Cryptolocker, to run its executable from the App Data or Local App Data folders. The Cryptolocker Prevention Kit is a tool created by Third Tier that automates the process of making a Group Policy to disable files running from the App Data and Local App Data folders, as well as disabling executable files from running from the Temp directory of various unzipping utilities.
Application whitelisting
Application whitelisting is good practice that most IT administrators employ to prevent unauthorized executable files or programs from running on their system. When you do this, only software that you have whitelisted will be allowed to run on your system, as a result of which, unknown executive files, malware or ransomware will just not be able to run. See how to whitelist a program.
Disable SMB1
SMB or Server Message Block is a network file sharing protocol meant for sharing files, printers, etc, between computers. There are three versions – Server Message Block (SMB) version 1 (SMBv1), SMB version 2 (SMBv2), and SMB version 3 (SMBv3). It is recommended that you disable SMB1 for security reasons.
Use AppLocker
Use Windows built-in feature AppLocker to prevent Users from installing or running Windows Store Apps and to control which software should run. You may configure your device accordingly to reduce the chances of Cryptolocker ransomware infection.
You can also use it to mitigate ransomware by blocking executable not signed, in places ransomware like:
- <users profile>\AppData\Local\Temp
- <users profile>\AppData\Local\Temp\*
- <users profile>\AppData\Local\Temp\*\*
This post will tell you how to create rules with AppLocker to an executable, and whitelist applications.
Using EMET
The Enhanced Mitigation Experience Toolkit protects Windows computers against cyber-attacks & unknown exploits. It detects and blocks exploitation techniques that are commonly used to exploit memory corruption vulnerabilities. It prevents exploits from dropping Trojan, but if you click open a file, it will not be able to help. UPDATE: This tool is not available now. Windows 10 Fall Creators Update will include EMET as a part of Windows Defender, so users of this OS need not use it.
Protect MBR
Protect your computer’s Master Boot Record with MBR Filter.
Disable Remote Desktop Protocol
Most Ransomware, including the Cryptolocker malware, tries to gain access to target machines via Remote Desktop Protocol (RDP), a Windows utility that permits access to your desktop remotely. So, if you find RDP of no use to you, disable remote desktop to protect your machine from File Coder and other RDP exploits.
Disable Windows Scripting Host
Malware and ransomware families often make use of WSH to run .js or .jse files to infect your computer. If you have no use for this feature, you can disable Windows Scripting Host to stay safe.
Use Ransomware prevention or removal tools
Use a good free anti-ransomware software. BitDefender AntiRansomware and RansomFree are some of the good ones. You may use RanSim Ransomware Simulator to check if your computer is sufficiently protected.
Kaspersky WindowsUnlocker can be useful if the Ransomware totally blocks access to your computer or even restrict access to select important functions, as it can clean up a ransomware infected Registry.

If you can identify the ransomware, it can make things a bit easier as you can use the ransomware decryption tools that may be available for that particular ransomware.
Here is a list of free Ransomware Decryptor Tools that can help you unlock files.
Disconnect from the Internet immediately
If you are suspicious about a file, act quickly to stop its communication with the C&C server before it finishes encrypting your files. To do so, simply disconnect yourself from the Internet, WiFi or your Network immediately, because the encryption process takes time so although you cannot nullify the effect of Ransomware, you can certainly mitigate the damage.
Use System Restore to get back to a known-clean state
If you have System Restore enabled on your Windows machine, which I insist that you have, try taking your system back to a known clean state. This is not a fool-proof method, however, in certain cases, it might help.
Set the BIOS clock back
Most Ransomware, including Cryptolocker, or the FBI Ransomware, offer a deadline or a time limit within which you can make the payment. If extended, the price for the decryption key can go up significantly, and – you cannot even bargain. What you can at least try is “beat the clock” by setting the BIOS clock back to a time before the deadline hour window is up. The only resort, when all tricks fail as it can prevent you from paying the higher price. Most ransomware offer you a 3-8 days period and may demand even up to USD 300 or more for the key to unlocking your locked data files.
While most of the targeted groups by Ransomware have been in the US and the UK, there exists no geographical limit. Anyone can be affected by it – and with every passing day, more and more ransomware malware is being detected. So take some steps to prevent Ransomware from getting onto your computer. This post talks a little more about Ransomware Attacks & FAQ.
Now read: What to do after a Ransomware attack.



