当大型电信、公用事业甚至政府都受到数据泄露(data breaches)的打击时,您还有什么机会?如果您采取一些关键措施,这是一个令人惊讶的好机会。其中一项措施是加密您的硬盘驱动器或 SSD(encrypting your hard drive or SSD)。

Windows 10 可以使用 Microsoft 的BitLocker(BitLocker)技术加密内置驱动器。它易于实施,易于使用,并且不需要任何特殊技能或硬件。但是,您确实需要拥有Windows 10的(Windows 10)Windows Pro、Enterprise或Education版本。如果你有Windows 10 Home,VeraCrypt 加密(VeraCrypt encryption)是一个很好的选择。您甚至可能更喜欢它而不是BitLocker。

什么是 BitLocker?(What Is BitLocker?)
加密是将信息更改为无意义的过程,除非您拥有密钥。BitLocker对硬盘驱动器上的信息进行加密,以便只有在输入密钥后才能读取它。密钥可以由计算机中的可信平台模块 (TPM)(Trusted Platform Module (TPM))芯片、存储密钥的USB驱动器或什至只是密码来管理。如果您尝试使用BitLocker但不喜欢它,可以轻松关闭 BitLocker(turn BitLocker off)。
为什么要加密我的 Windows 硬盘驱动器?(Why Should I Encrypt My Windows Hard Drive?)
假设您使用密码最佳实践(password best practices)。您的密码很复杂,很难猜到,而且您不会写下来或与任何人分享。如果有人想从您的驱动器获取数据,但他们没有您的Windows密码,他们可以移除硬盘驱动器,将其插入另一台计算机,然后使用Linux live CD 恢复文件(Linux live CD to recover files)。

如果您使用的是BitLocker,他们就不能这样做。BitLocker必须能够从某个地方获取密钥。理想情况下(Ideally),这将是可信平台模块(Trusted Platform Module)( TPM )。它也可以是密码短语或专用于BitLocker密钥的 USB 驱动器。
“但没有人会偷走我的驱动器,”你回答。你有没有扔过电脑?你的硬盘也随之而来,不是吗?除非您安全地处理硬盘驱动器(safely dispose of a hard drive),否则有人可以获取数据。这每天都在发生,而且很容易。我们甚至有一篇关于如何访问旧驱动器上的文件(how to access files on old drives)的文章。
如果您使用BitLocker并将驱动器从计算机中取出,然后将计算机和驱动器分开处理,那么您只会使临时数据窃贼的工作变得更加困难。它甚至需要数据恢复专家才能远程获取您的数据。还信(Convinced)吗?
如何检查计算机是否有 TPM(How to Check if a Computer Has a TPM)
理想的BitLocker情况是在具有TPM的设备上。您的设备有TPM吗?很容易检查。
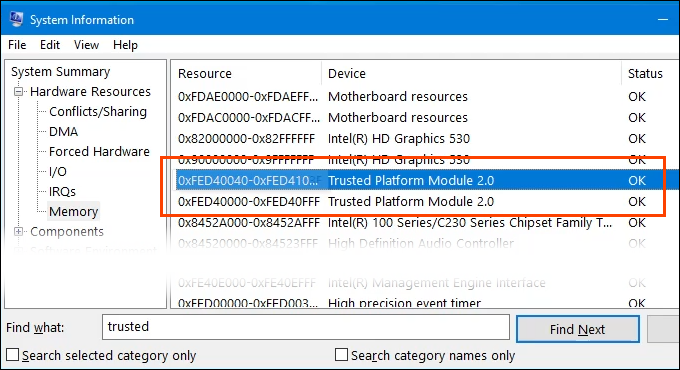
- 选择开始(Start )菜单并输入system。第一个结果应该是System Information。选择那个。

- 当系统信息(System Information)窗口打开时,在底部的Find what:框中输入(Find what:)trusted ,然后选择(trusted )Find或按Enter。

- 如果设备有TPM,它将显示在结果中。在此示例中,TPM确实存在,并且它是 2.0 版本的TPM。版本在未来可能很重要,尤其是在 Windows 11 公开可用后。
如何在具有 TPM 的设备上启用 BitLocker(How to Enable BitLocker On a Device With a TPM)
你的设备有一个TPM,所以下一部分很简单。
- 打开文件资源管理器(File Explorer )并导航到要使用BitLocker加密的驱动器。
右键单击(Right-click)驱动器并选择打开 BitLocker(Turn on BitLocker)。

可能有一条带有进度条的正在启动的 BitLocker消息。(Starting BitLocker )让它完成。

- 它会提示您选择如何解锁此驱动器(Choose how you want to unlock this drive)。有2个选择;使用密码解锁驱动器(Use a password to unlock the drive),或使用我的智能卡解锁驱动器(Use my smart card to unlock the drive)。如果该设备在企业中使用,您可能有一张智能卡并且想要使用它。如果没有,则选择使用密码。创建一个强大、安全的密码(Create a strong, secure password)。

仅当驱动器从该设备中移除并安装在另一台设备上时才需要密码。否则,TPM将处理密码的输入,使加密驱动器与其他所有设备无缝协作。
现在它询问您要如何备份恢复密钥?(How do you want to back up your recovery key?)

有 4 个选项:
- 保存到您的 Microsoft 帐户(Save to your Microsoft account):如果您使用Microsoft帐户登录设备,这是最简单的方法。这是本示例中使用的内容。
- 保存到 USB 闪存驱动器(Save to a USB flash drive):如果选择此方法,请仅将USB闪存驱动器用于此目的。不要尝试在该闪存驱动器上存储其他东西。
- 保存到文件(Save to a file):如果选择此方法,请不要将文件保存到正在加密的驱动器中。将其保存到另一个驱动器或云存储。
- 打印恢复密钥(Print the recovery key):选择此方法意味着打印的密钥需要安全存储,防止火灾、盗窃和洪水。当需要密钥时,需要手动输入。
根据选择的方法,可能会有一些额外的步骤,但所有方法最终都会导致下一个屏幕。
此步骤要求选择要加密的驱动器数量(Choose how much of your drive to encrypt)。这可能会令人困惑。如果要加密的驱动器上没有任何内容,请选择仅加密已用磁盘空间(Encrypt used disk space only)。它非常快。
在此之后添加到驱动器的任何内容都将自动加密。如果驱动器上已有文件和文件夹,请选择加密整个驱动器(Encrypt entire drive )以确保它们都立即加密。然后选择下一步(Next)。

根据您使用的Windows版本,下一个屏幕可能不会显示。(Windows)花时间阅读和理解它很重要。

总而言之,如果有人从该设备中取出驱动器并将其放入Windows 10版本 1511(Version 1511)之前的任何版本的Windows中,驱动器将无法工作。大多数人永远不会这样做,所以大多数人会选择New encryption mode,然后选择Next。
加密是一项严肃的业务,可能会出错。这就是为什么进程会最后一次询问,你准备好加密这个驱动器了吗?(Are you ready to encrypt this drive? )如果是这样,请选择开始加密。(Start encrypting.)

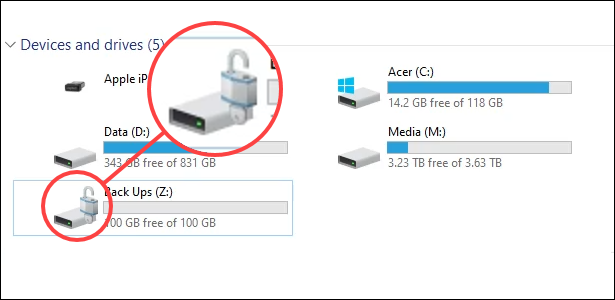
BitLocker完成对驱动器(BitLocker)的加密后,返回文件资源管理器(File Explorer)。请注意(Notice),驱动器图标现在有一个未锁定的挂锁。这意味着驱动器已加密但已准备好接收文件。如果挂锁被锁定,您需要输入密码才能访问它。
如何在没有 TPM 的设备上启用 BitLocker(How to Enable BitLocker On a Device Without TPM)
目前,有一种方法可以使用BitLocker加密驱动器,即使设备没有TPM也是如此。由于Windows 11 需要 TPM 2.0才能从(Windows 11 requires TPM 2.0)Windows 10升级到Windows(Windows 11) 11 ,因此预计Windows 11会发生这种变化。此方法需要具有管理员权限。
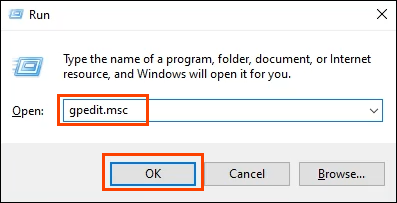
- 按组合键Win Key + R打开运行实用程序。在Open字段中输入gpedit.msc,然后选择OK或按Enter。这将打开本地组策略编辑器(Local Group Policy Editor)(Local Group Policy Editor)。
- 本地组策略编辑器(Local Group Policy Editor)打开后,导航到计算机配置(Computer Configuration )>管理模板(Administrative Templates )> Windows 组件(Windows Components )> BitLocker 驱动器加密(BitLocker Drive Encryption )>操作系统驱动器(Operating System Drives)。双击Require additional authentication at startup设置。

- 选择已启用(Enabled ),然后选择确定( OK)以更改设置。请注意显示“在没有兼容TPM的情况下允许BitLocker ”的复选框。(BitLocker)” 这允许使用密码或安全密钥来访问BitLocker加密驱动器。重新启动(Restart)Windows 以激活设置。

- 按照与上一节相同的过程启动BitLocker并加密驱动器。警告:(WARNING: )如果加密了Windows驱动器,每次Windows启动时,都必须输入密码才能加载Windows 。将密码记录在设备外的安全位置。
- 下次启动Windows时,BitLocker将要求输入密码来解锁驱动器。这样做并按Enter继续。

你现在安全吗?(Are You Secure Now?)
BitLocker加密只是保护数据的一部分。您还采取了哪些措施来确保您的隐私和身份受到保护?让我们知道!请(Make)务必查看我们所有的数据安全和隐私(data security and privacy)文章。
How to Encrypt Windows 10 Hard Drive with Bitlocker
When large telecomѕ, utilities, and even the government are getting hit with data breaches, what chance do you stand? A surprisingly good chance if you take a few key measures. One of those measures is encrypting your hard drive or SSD.

Windows 10 has a way to encrypt your built-in drive with Microsoft’s BitLocker technology. It’s easy to implement, easy to use, and doesn’t require any special skills or hardware. However, you do need to have Windows Pro, Enterprise, or Education versions of Windows 10. If you have Windows 10 Home, VeraCrypt encryption is an excellent option. You may even prefer it to BitLocker.

What Is BitLocker?
Encryption is the process of changing information into something meaningless unless you have the key. BitLocker encrypts information on hard drives so that it can only be read once the key is entered. The key may be managed by a Trusted Platform Module (TPM) chip in the computer, a USB drive that stores the key, or even just a password. If you try BitLocker and don’t like it, it’s easy to turn BitLocker off.
Why Should I Encrypt My Windows Hard Drive?
Let’s assume you use password best practices. Your password is complex, hard to guess, and you don’t write it down or share it with anyone. If someone wants to get data from your drive and they don’t have your Windows password, they could remove the hard drive, plug it into another computer, and use a Linux live CD to recover files.

If you’re using BitLocker, they can’t do that. BitLocker has to be able to get the key from somewhere. Ideally, that would be the Trusted Platform Module (TPM). It could also be a passphrase or a USB drive dedicated as a BitLocker key.
“But no one is going to steal my drive,” you respond. Have you ever thrown a computer out? Your hard drives went with it too, didn’t they? Unless you safely dispose of a hard drive, someone can get the data. This happens every day, and it’s easy. We even have an article on how to access files on old drives.

If you used BitLocker and took the drive out of the computer then disposed of the computer and drive separately, you just made the casual data thief’s job exponentially harder. It would require a data recovery specialist to even have a remote chance of getting your data. Convinced yet?
How to Check if a Computer Has a TPM
The ideal BitLocker situation is on a device with a TPM. Does your device have a TPM? It’s easy to check.
- Select the Start menu and type system. The first result should be System Information. Select that.

- When the System Information window opens, enter trusted in the Find what: box at the bottom, then select Find or press Enter.

- If the device has a TPM, it will show in the results. In this example, TPM does exist and it’s a version 2.0 TPM. Version may be important in the future, especially once Windows 11 is publicly available.

How to Enable BitLocker On a Device With a TPM
Your device has a TPM, so this next part is simple and easy.
- Open File Explorer and navigate to the drive to be encrypted with BitLocker.
Right-click on the drive and select Turn on BitLocker.

There may be a Starting BitLocker message with a progress bar. Let it finish.

- It will prompt you to Choose how you want to unlock this drive. There are 2 choices; Use a password to unlock the drive, or Use my smart card to unlock the drive. If the device is being used in a business, you may have a smart card and want to use that. If not, then choose to use a password. Create a strong, secure password.

The password will only be needed if the drive is removed from this device and installed on another device. Otherwise, the TPM will handle the entering of the password, making the encrypted drive work seamlessly with everything else.
Now it asks How do you want to back up your recovery key?

There are 4 options:
- Save to your Microsoft account: If you use a Microsoft account to log in to the device, this is the easiest method. It’s what’s being used in this example.
- Save to a USB flash drive: If this method is chosen, only use the USB flash drive for this purpose. Do not try to store other things on that flash drive.
- Save to a file: If choosing this method, don’t save the file to the drive being encrypted. Save it to another drive or cloud storage.
- Print the recovery key: Choosing this method means the printed key needs secure storage, safe from fire, theft, and flood. When the key is needed, it’ll need to be manually typed in.
Depending on the method selected, there may be some additional steps, but all methods will eventually lead to the next screen.
This step asks to Choose how much of your drive to encrypt. That may be confusing. If there’s nothing on the drive being encrypted, select Encrypt used disk space only. It’s very fast.
Anything added to the drive after this will be automatically encrypted. If the drive already has files and folders on it, choose Encrypt entire drive to ensure they’re all encrypted immediately. Then select Next.

The next screen might not display depending on the version of Windows you’re using. It’s important to take the time to read and understand it.

To sum up, if anyone ever takes the drive out of this device and puts it into any version of Windows prior to Windows 10 Version 1511, the drive won’t work. Most people won’t ever do that, so most will choose New encryption mode, then select Next.
Encryption is serious business and things can go wrong. That’s why the process will ask one last time, Are you ready to encrypt this drive? If so, select Start encrypting.

Once BitLocker is done encrypting the drive, go back to File Explorer. Notice that the drive icon now has an unlocked padlock. That means the drive is encrypted but ready to receive files. If the padlock was locked, you would need to enter the password to access it.

How to Enable BitLocker On a Device Without TPM
For now, there is a way to use BitLocker to encrypt a drive even if the device doesn’t have TPM. Expect that to change in Windows 11 as Windows 11 requires TPM 2.0 to upgrade from Windows 10 to Windows 11. This method requires having administrator rights.
- Press the key combo Win Key + R to open the Run utility. In the Open field enter gpedit.msc, then select OK or press Enter. This will open the Local Group Policy Editor.

- After the Local Group Policy Editor opens, navigate to Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption > Operating System Drives. Double-click on the setting Require additional authentication at startup.

- Select Enabled and then OK to change the setting. Note the checkbox where it reads, “Allow BitLocker without a compatible TPM.” This allows for the use of a password or security key to be used to access the BitLocker encrypted drive. Restart Windows to activate the setting.

- Follow the same procedure as in the section above to start BitLocker and encrypt a drive. WARNING: If encrypting the Windows drive is done, every time Windows starts, the password must be entered for Windows to load. Record the password in a secure place off of the device.
- The next time Windows is started, BitLocker will require the password to be entered to unlock the drive. Do that and press Enter to continue.

Are You Secure Now?
BitLocker encryption is only one part of securing your data. What else are you doing to ensure your privacy and identity are protected? Let us know! Make sure to check out all of our data security and privacy articles.



















