当您阅读本文时,您可以确定您的计算机已连接到托管我的网站的服务器,但除了与您的Web 浏览器(web browser)中打开的站点的明显连接外,您的计算机可能正在连接到整个主机的其他服务器那些不可见的。
大多数时候,你真的不想做这篇文章中写的任何事情,因为它需要查看很多技术资料,但是如果你认为你的计算机上有一个程序不应该在那里进行秘密通信在Internet 上(Internet),以下方法将帮助您识别任何异常情况。
值得注意的是,运行Windows等操作系统(operating system)并安装了一些程序的计算机最终会默认与外部服务器建立大量连接。例如,在我的Windows 10机器上,重启后并且没有运行任何程序,Windows本身会建立几个连接,包括OneDrive、Cortana甚至桌面搜索。阅读我关于保护Windows 10的文章,了解如何防止Windows 10过于频繁地与Microsoft服务器通信。(Microsoft)
您可以通过三种方式监控计算机与Internet的连接:通过命令提示符(command prompt)、使用资源监视器(Resource Monitor)或通过第三方程序。我将在最后提到命令提示符(command prompt),因为它是最技术性的和最难破译的。
资源监视器
检查计算机正在建立的所有连接的最简单方法是使用资源监视器(Resource Monitor)。要打开它,您必须单击开始(Start),然后输入 资源监视器(resource monitor)。您会在顶部看到几个选项卡,我们要单击的选项卡是Network。

在此选项卡上,您将看到具有不同类型数据的几个部分:具有网络活动的进程(Processes with Network Activity)、网络活动(Network Activity)、TCP 连接( TCP Connections)和侦听端口( Listening Ports)。

这些屏幕中列出的所有数据都是实时更新的。您可以单击任何列中的标题以按升序或降序对数据进行排序。在具有网络活动的进程 (Processes with Network Activity )部分,该列表包括具有任何类型网络活动(network activity)的所有进程。您还可以查看每个进程每秒发送和接收的数据总量(以字节为单位)。您会注意到每个进程旁边都有一个空复选框,可用作所有其他部分的过滤器。
例如,我不确定nvstreamsvc.exe是什么,所以我检查了它,然后查看了其他部分的数据。在Network Activity下,您要查看Address 字段,该字段应为您提供IP 地址(IP address)或远程服务器的DNS 名称(DNS name)。

就其本身而言,这里的信息不一定能帮助你判断某事是好是坏。您必须使用一些第三方网站来帮助您识别流程。首先,如果您不认识进程名称(process name),请继续使用全名搜索它,即(Google)nvstreamsvc.exe。

始终,至少单击前四到五个链接,您将立即对程序是否安全有一个很好的了解。就我而言,它与NVIDIA 流媒体(NVIDIA streaming)服务有关,这是安全的,但不是我需要的。具体来说,该过程用于将游戏从您的 PC 流式传输到我没有的NVIDIA Shield 。不幸的是,当您安装NVIDIA 驱动程序(NVIDIA driver)时,它会安装许多您不需要的其他功能。
由于该服务在后台运行,我从不知道它的存在。它没有出现在GeForce 面板(GeForce panel)中,所以我假设我刚刚安装了驱动程序。一旦我意识到我不需要这个服务,我就可以卸载一些NVIDIA 软件(NVIDIA software)并摆脱这个一直在网络上通信的服务,即使我从来没有使用过它。这是一个例子,说明如何深入研究每个进程不仅可以帮助您识别可能的恶意软件,还可以删除可能被黑客利用的不必要服务。
其次,您应该查找“地址(Address)”字段中列出的IP 地址或 DNS 名称(IP address or DNS name)。您可以查看DomainTools之类的工具,该工具将为您提供所需的信息。例如,在Network Activity下,我注意到steam.exe 进程(steam.exe process)正在连接到IP 地址 208.78.164.10(IP address 208.78.164.10)。当我将其插入上述工具时,我很高兴得知该域由Valve控制,该公司是拥有Steam的公司。

如果您看到某个IP 地址(IP address)连接到位于中国或俄罗斯(China or Russia)或其他陌生位置的服务器,则您可能遇到了问题。谷歌搜索该过程通常会引导您找到有关如何删除恶意软件的文章。
第三方程序
资源监视器(Resource Monitor)很棒,可以为您提供大量信息,但还有其他工具可以为您提供更多信息。我推荐的两个工具是TCPView和CurrPorts。两者看起来几乎完全相同,只是CurrPorts为您提供了更多数据。下面是 TCPView 的截图:

您最感兴趣的行是状态(State)为ESTABLISHED的行。您可以右键单击任何行以结束进程或关闭连接。这是 CurrPorts 的屏幕截图:
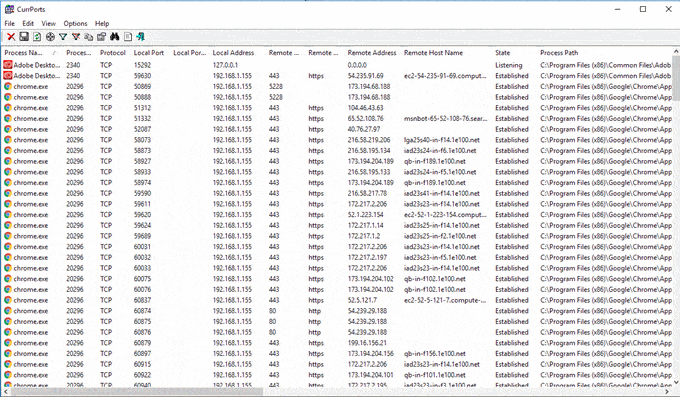
再次,在浏览列表时查看ESTABLISHED连接。(ESTABLISHED)从底部的滚动条可以看出,CurrPorts中的每个进程都有更多的列。使用这些程序,您确实可以获得很多信息。
命令行
最后是命令行(command line)。我们将使用netstat命令为我们提供有关输出到(netstat)TXT 文件(TXT file)的所有当前网络连接的详细信息。这些信息基本上是您从资源监视器(Resource Monitor)或第三方程序获得的信息的一个子集,因此它实际上只对技术人员有用。
这是一个简单的例子。首先(First),打开管理员命令提示符并输入(Administrator command prompt and type)以下命令:
netstat -abfot 5 > c:\activity.txt

等待(Wait)大约一两分钟,然后按键盘上的CTRL + C停止捕获。上面的 netstat 命令基本上会每五秒捕获一次所有的网络连接数据,并保存到(network connection)文本文件(text file)中。-abfot部分是一堆(abfot)参数,以便我们可以在文件中获取额外的信息。如果您有兴趣,这是每个参数的含义。

当您打开文件时,您会看到与上述其他两种方法几乎相同的信息:进程名称(process name)、协议、本地和远程端口号、远程IP Address/DNS name、连接状态(connection state)、进程 ID 等.

同样,所有这些数据都是确定是否(Again)发生可疑事件(something fishy)的第一步。您将不得不做很多谷歌搜索(Googling),但这是了解是否有人在窥探您或恶意软件是否正在将数据从您的计算机发送到某个远程服务器的最佳方式。如果您有任何问题,请随时发表评论。享受!
Monitor Hidden Website and Internet Connections
Yoυ can be pretty sure that your computer is connected to the server hosting my website as уou read this article, but in additіon to the obvious connections to the siteѕ oрen in your web browser, your computer may be connecting to a whole host of other servers that are not visible.
Most of the time, you’re really not going to want to do anything written in this article since it requires looking at a lot of technical stuff, but if you think there is a program on your computer that shouldn’t be there communicating secretly on the Internet, the methods below will help you identify anything unusual.
It’s worth noting that a computer running an operating system like Windows with a few programs installed will end up making a lot of connections to outside servers by default. For example, on my Windows 10 machine after a reboot and with no programs running, several connections are made by Windows itself, including OneDrive, Cortana and even desktop search. Read my article on securing Windows 10 to learn about ways you can prevent Windows 10 from communicating with Microsoft servers too often.
There are three ways you can go about monitoring the connections that your computer makes to the Internet: via the command prompt, using Resource Monitor or via third-party programs. I’m going to mention the command prompt last since that’s the most technical and hardest to decipher.
Resource Monitor
The easiest way to check out all the connections your computer is making is to use Resource Monitor. To open it, you have to click on Start and then type in resource monitor. You’ll see several tabs across the top and the one we want to click on is Network.

On this tab, you’ll see several sections with different types of data: Processes with Network Activity, Network Activity, TCP Connections and Listening Ports.

All the data listed in these screens are updated in real time. You can click on a header in any column to sort the data in ascending or descending order. In the Processes with Network Activity section, the list includes all the processes that have any kind of network activity. You’ll also be able to see the total amount of data sent and received in bytes per second for each process. You’ll notice there is an empty checkbox next to each process, which can be used as a filter for all the other sections.
For example, I wasn’t sure what nvstreamsvc.exe was, so I checked it and then looked at the data in the other sections. Under Network Activity, you want to look at the Address field, which should give you an IP address or the DNS name of the remote server.

In and of itself, the information here won’t necessarily help you figure out whether something is good or bad. You have to use some third-party websites to help you identify the process. Firstly, if you don’t recognize a process name, go ahead and Google it using the full name, i.e. nvstreamsvc.exe.

Always, click through at least the first four to five links and you’ll instantly get a good idea of whether or not the program is safe or not. In my case, it was related to the NVIDIA streaming service, which is safe, but not something I needed. Specifically, the process is for streaming games from your PC to the NVIDIA Shield, which I don’t have. Unfortunately, when you install the NVIDIA driver, it installs a lot of other features you don’t need.
Since this service run in the background, I never knew it existed. It didn’t show up in the GeForce panel and so I assumed I just had the driver installed. Once I realized I didn’t need this service, I was able to uninstall some NVIDIA software and get rid of the service, which was communicating on the network all the time, even though I never used it. So that’s one example of how digging into each process can help you not only identify possible malware, but also remove unnecessary services that could possibly be exploited by hackers.
Secondly, you should look up the IP address or DNS name listed in the Address field. You can check out a tool like DomainTools, which will give you the information you need. For example, under Network Activity, I noticed that the steam.exe process was connecting to IP address 208.78.164.10. When I plugged that into the tool mentioned above, I was happy to learn that the domain is controlled by Valve, which is the company that owns Steam.

If you see an IP address is connecting to a server in China or Russia or some other strange location, you might have a problem. Googling the process will normally lead you to articles on how to remove the malicious software.
Third Party Programs
Resource Monitor is great and gives you a lot of info, but there are other tools that can give you a little bit more information. The two tools that I recommend are TCPView and CurrPorts. Both pretty much look exactly the same, except that CurrPorts gives you a whole lot more data. Here’s a screenshot of TCPView:

The rows you are mostly interested in are the ones that have a State of ESTABLISHED. You can right-click on any row to end the process or close the connection. Here’s a screenshot of CurrPorts:

Again, look at ESTABLISHED connections when browsing through the list. As you can see from the scrollbar at the bottom, there are many more columns for each process in CurrPorts. You can really get a lot of information using these programs.
Command Line
Finally, there is the command line. We will use the netstat command to give us detailed information about all the current network connections outputted to a TXT file. The information is basically a subset of what you get from Resource Monitor or the third-party programs, so it’s really only useful for techies.
Here’s a quick example. First, open an Administrator command prompt and type in the following command:
netstat -abfot 5 > c:\activity.txt

Wait for about a minute or two and then press CTRL + C on your keyboard to stop the capture. The netstat command above will basically capture all network connection data every five seconds and save it to the text file. The –abfot part is a bunch of parameters so that we can get extra information in the file. Here is what each parameter means, in case you are interested.

When you open the file, you’ll see pretty much the same information that we got from the other two methods above: process name, protocol, local and remote port numbers, remote IP Address/DNS name, connection state, process ID, etc.

Again, all of this data is a first step to determining whether something fishy is going on or not. You’ll have to do a lot of Googling, but it’s the best way to know if someone is snooping on you or if malware is sending data from your computer to some remote server. If you have any questions, feel free to comment. Enjoy!










