我最近订阅了一项VPN 服务(VPN service)供我个人使用,因此我在家中的Internet 连接(Internet connection)是完全加密的。这些天来,随着所有间谍和黑客(spying and hacking revelations)事件的曝光,我不介意(t mind)在我身边有一点额外的安全措施,以防万一。一旦我在计算机上安装了软件并连接到VPN,据我所知,它似乎工作正常。
然而,作为一个技术人员(techie person),我不能在没有实际验证加密是否启用的情况下接受一切正常。因此,即使我没有使用数据包嗅探器和协议分析器(packet sniffer and protocol analyzer),我还是继续下载了一个网络实用程序(network utility),它让我可以真正看到从我的计算机来回传输的数据。
我在未连接到VPN时检查了连接并捕获了一些数据包,然后在连接时做了同样的事情。很容易,我能够看到正在传输的数据在发送到VPN时实际上是加密的。在本文中,我将向您展示如何验证您的连接是否也已加密。
如果您没有任何技术专长,请不要担心。您需要做的就是按下记录按钮(record button),滚动列表并检查一些文本。您可以忽略其他所有内容,因为除非您对计算机和网络有所了解,否则它们大多都是胡言乱语。在Mac上,我们将使用CocoaPacketAnalyzer,在 PC 上,我们将使用Wireshark。
在 Mac 上验证加密
首先,继续在您的Mac上下载(Mac)CocoaPacketAnalyzer并运行它。您应该会看到带有四个大按钮的启动屏幕。(startup screen)

捕获是您单击以开始捕获网络流量(network traffic)的内容。如果您保存捕获会话(capture session),它称为跟踪文件(trace file),您可以稍后使用第二个按钮再次打开这些文件。但是,出于我们的目的,我们只想看到数据是加密的,并且不会真正保存任何这些捕获。
在我们执行捕获之前,继续并单击Preferences以设置我们将如何捕获数据。单击(Click)顶部的Capture,我们需要在这里检查的唯一设置是Capture Interface。

首先(First),一定要按下位于列表框右侧的小(list box)刷新按钮(Refresh button)。当您单击该框时,您会看到几个选项,所有这些看起来都令人困惑。您唯一需要选择的是那些在其后列出了IPv4并带有一些数字的那些。您无需选择具有 127.0.0.1 的那个。您需要选择具有您当前正在使用的连接的IP 地址的那个。(IP address)您可以通过转到System Preferences然后单击Network来解决这个问题。

单击左侧(Click)列表框中(list box)带有绿点的连接,然后检查右侧部分的IP 地址字段。(IP address)如您所见,它显示 192.168.1.x,因此与程序下拉列表中的en0 – IP4 – 192.168.1.68选项匹配。(en0 – IP4 – 192.168.1.68)现在继续并关闭 Capture Preferences 窗口以返回主屏幕。
继续并单击捕获(Capturing),您现在将看到一个新对话框弹出(dialog pop),您可以在其中选择一些设置,然后开始捕获。

在这里,您无需为我们的目的进行任何更改,因此您只需按Start即可开始。然而,在你这样做之前,有一些事情需要注意。首先,您应该尝试关闭所有正在运行的程序和任务栏程序(program and taskbar programs),只保持浏览器窗口(browser window)打开。网络(Network)捕获了创纪录的大量数据,甚至几秒钟就会产生数千行数据。因此,为了简单起见,请先关闭所有内容并杀死尽可能多的后台进程,然后单击Start。
之后,立即加载一两个站点,然后单击停止(Stop)。您只想捕捉几秒钟,仅此而已。将网址输入到浏览器的选项卡中甚至是一个好主意,然后您可以在开始捕获后按Enter加载页面。
按下Stop后,您将看到一个如下所示的窗口:
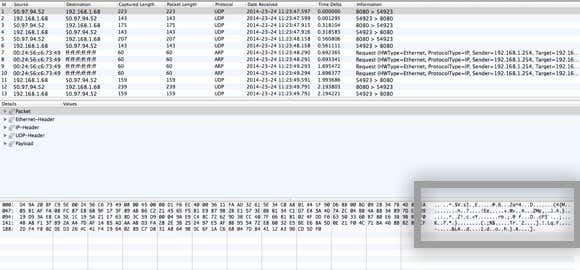
现在这可能看起来像绝对的胡言乱语,但没关系。您需要做的就是滚动顶部的列表,它是表格格式,然后查看(format and look)您在右下角框中看到的数据,我在上面突出显示了这些数据。现在由于可能有数千行,您可以快速按住向下箭头键并查看底部的数据更改。

如果您的VPN 连接(VPN connection)实际上是加密的,则您滚动浏览的每一行都应显示类似于上图中的数据的数据。由于它不可读且只是一堆随机字符,因此已加密。使用加密连接,所有这数千行中的任何行都不应该是可读的。现在让我向您展示在未加密的连接上会看到什么,例如当您没有连接到 VPN 时:

正如您在上面看到的,由于没有加密,我可以阅读更多内容。我看到我使用Mac 和 Safari(Mac and Safari)以及许多其他数据访问了 aseemkishore.com。并非每个数据包在未加密的连接上都是可读的,但对于大多数数据包,您将能够看到实际数据、HTML 代码(HTML code)、协议标头等。正如我之前提到的,在加密连接上,甚至不是单个数据包将是可以理解的。
在 PC 上验证加密
在 PC 上进行检查的过程与我上面展示的几乎相同,只是您使用的是另一个名为Wireshark的程序。下载后,启动它,主屏幕(home screen)应如下所示:

就像在Mac上一样,您需要做的第一件事是选择要为其捕获数据的接口(网络接口)。(network interface)点击(Click)Interface List,你会看到network interface的列表。我更喜欢Wireshark,因为您实际上可以看到每个接口上传输了多少数据,这使得很容易看出哪个是主要连接。

继续并选中相应界面旁边的框,然后单击Close。现在您所要做的就是单击“开始”按钮(Start button)(在“接口列表”按钮(Interface List button)下方),一切顺利。出于我们的目的,您不必更改任何其他选项或其他任何内容。完成捕获后,您应该会看到如下屏幕:
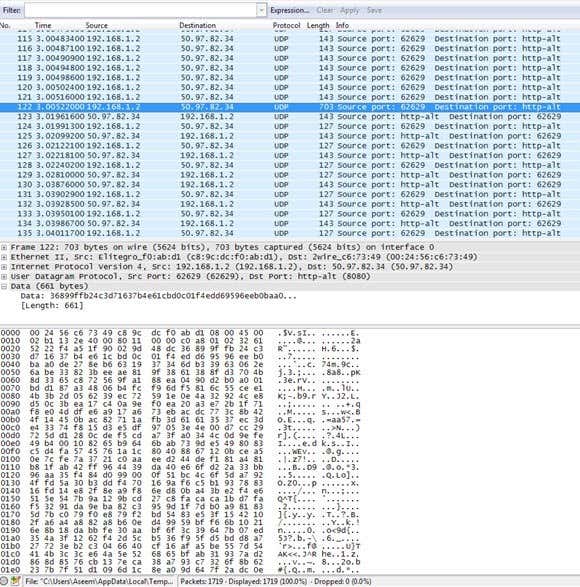
您可能必须全屏展开窗口,然后相应地调整底部和顶部窗格,但您可以看到数据的格式与Mac上的CocoaPacketAnalyzer 完全相同(CocoaPacketAnalyzer)。滚动(Scroll)顶部的列表并确保数据部分(data section)完全是乱码,这意味着您的连接已加密。如果您能够阅读任何文字或文字,则表示数据未加密。确保您使用箭头键(arrow keys)快速浏览至少几百行。
一旦您知道您的VPN 连接(VPN connection)实际上是安全加密的,希望这篇文章能让您放心!我知道这让我感觉好多了。如果您对程序有任何疑问或无法解释结果,请发表评论,我会尽力提供帮助。享受!
How to Check if Your VPN Connection is Actually Encrypted
I recently subscribed to a VPN service for my personal use sо that my Internet connection from home is completely encrypted. With all the spying and hacking revelations going on thеse days, І don’t mind hаving a little bit of extra sеcurity on my side just in case. Onсe I had inѕtalled the software on cоmputer and connected to thе VPN, it seemed to be working fine as far as I could tell.
However, being a techie person myself, I couldn’t just accept that everything was working without actually verifying that the encryption was enabled. So even though I hadn’t played around with a packet sniffer and protocol analyzer, I went ahead and downloaded a network utility that let me actually see the data being transferred back and forth from my computer.
I checked the connection when not connected to the VPN and captured some packets and then did the same thing when connected. Easily, I was able to see that the data being transferred was actually encrypted when being sent to the VPN. In this article, I’ll show you how you can verify if your connection is encrypted also.
If you don’t have any technical expertise, don’t really worry. All you need to do is press a record button, scroll through a list and check some text. You can ignore everything else as it’ll mostly be gibberish unless you know something about computers and networking. On the Mac we’re going to use CocoaPacketAnalyzer and on the PC we’re going to use Wireshark.
Verify Encryption on a Mac
Firstly, go ahead and download CocoaPacketAnalyzer on your Mac and run it. You should see the startup screen with four large buttons.

Capturing is what you’ll click on to start a capture of network traffic. If you save a capture session, it’s called a trace file and you can open those again later on using the second button. However, for our purposes, we just want to see the data is encrypted and won’t really be saving any of these captures.
Before we perform a capture, go ahead and click on Preferences to set up how we are going to capture the data. Click on Capture at the top and the only setting we need to check here is Capture Interface.

First, be sure to press the little Refresh button that is located to the right of the list box. When you click on the box, you’ll see a couple of options, all of which look confusing as heck. The only ones you’ll need to choose from are the ones that have IPv4 listed with some numbers after it. You don’t need to pick the one that has 127.0.0.1. You’ll want to pick the one that has the IP address for the connection you’re currently using. You can figure this out by going to System Preferences and then clicking on Network.

Click on the connection that has the green dot in the list box on the left and then check the IP address field on the right-hand section. As you can see, it says 192.168.1.x, so that matches the en0 – IP4 – 192.168.1.68 option in the dropdown list in the program. Now go ahead and close the Capture Preferences window to get back to the main screen.
Go ahead and click on Capturing and you’ll now see a new dialog pop up where you can pick a few settings and then start the capture.

Here you don’t need to change anything for our purposes, so to get start you just need to press Start. Before you do, however, there are some things to note. Firstly, you should try to close all program and taskbar programs running and only keep your browser window open. Network captures record tons of data and even a few seconds will result in more than a thousands rows of data. So to keep it simple, close everything and kill as many background processes as possible first, then click Start.
After doing that, immediately load one or two sites and then click Stop. You only want to capture for a few seconds and nothing more. It might even be a good idea to have the web addresses already typed into tabs in your browser and then you can just press Enter to load the pages once you start the capture.
Once you press Stop, you will see a window that looks like this:

Now this may look like absolute gibberish, but that’s fine. All you need to do is scroll through the list at the top, which is in table format and look at the data you see in the box in the lower right, which I highlighted above. Now since there are probably thousands of rows, you can just keep pressing the down arrow key fast and looking at the data change at the bottom.

If your VPN connection is actually encrypted, every line you scroll through should show data that looks like the data in the above image. Since it’s unreadable and just a bunch of random characters, it’s encrypted. With an encrypted connection, nothing should be readable for any row in all those thousands of rows. Now let me show you what you’ll see on an unencrypted connection, such as when you’re not connected to a VPN:

As you can see above, I can read a whole lot more stuff now that there is no encryption. I see I visited aseemkishore.com using a Mac and Safari and lots of other data. Not every packet will be this readable on an unencrypted connection, but for most packets you’ll be able to see the actual data, HTML code, protocol headers, etc. As I mentioned before, on an encrypted connection, not even a single packet will be understandable.
Verify Encryption on a PC
The process for checking on a PC is pretty much the same as I have shown above, except that you are using a different program called Wireshark. Once you download it, start it up and the home screen should look like this:

Like on the Mac, the first thing you’ll need to do is pick the interface (network interface) that you want to capture the data for. Click on Interface List and you’ll see the list of network interfaces. I like Wireshark a little better in that you can actually see how much data is being transferred on each interface, which makes it easy to see which one is the primary connection.

Go ahead and check the box next to the appropriate interface and then click Close. Now all you have to do is click on the Start button (below the Interface List button) and you’ll be good to go. You don’t have to change any other options or anything else for our purposes. Once you complete a capture, you should see an screen like this:

You may have to expand the window full-screen and then adjust the bottom and top panes accordingly, but as you can see the data is in the exact same format as CocoaPacketAnalyzer on the Mac. Scroll through the list at the top and make sure that data section is complete gibberish, which means your connection is encrypted. If you’re able to read any words or text, it means the data is not being encrypted. Make sure you browse through at least a couple of hundred rows quickly using the arrow keys.
Hopefully this post will put your mind at ease once you know your VPN connection is actually securely encrypted! I know it made me feel a lot better. If you have any questions about the programs or are having trouble interpreting the results, post a comment and I’ll try to help. Enjoy!










