您是否怀疑邻居正在使用您的无线Internet 连接(Internet connection)?可能是您的Internet 连接(Internet connection)速度比应有的速度慢,或者您的设备不断与路由器断开连接。连接到您的无线路由器的人也可以访问您网络上的共享文件夹,因此数据盗窃是一个真正的威胁。幸运的是,有一些方法可以检测到您的网络的未知连接以及(network and ways)阻止它们连接的方法。
针对无线窃听器的主要防御措施是保护您的无线路由器(wireless router)。尽管大多数来自ISP的(ISPs)无线路由器(wireless router)都带有长密码,但仍然有人可以通过简单地复制印在您的无线路由器(wireless router)上的密码来获得访问权限,因为大多数人不会更改其(t change)ISP设置的默认密码(default password)。
如果您有自己购买的路由器,除非您不更改(t change)默认密码(default password),否则任何人都无法使用写在路由器上的密码。我们将在下面讨论所有这些。我们先来说说如何检测无线窃听器。

检测未经授权的无线连接(Detect Unauthorized Wireless Connections)
基本上有两种方法可以检测连接到无线路由器的所有设备:检查路由器本身或使用已连接到网络的设备扫描整个网络。我更喜欢后一种方法,因为它不太复杂,但是,我会提到两种方法。
第一步是从您的网络浏览器连接到您的(web browser)无线路由器(wireless router)。为此,您必须输入路由器的IP 地址(IP address)。如果您不知道,请阅读我关于确定无线路由器(wireless router)IP 的帖子。完成后,您需要使用用户名和密码登录(username and password)。
如果您不记得密码或者您从未更改过默认密码(default password),那就是个问题。在这两种情况下,我建议您将无线路由器(wireless router)重置为出厂默认(factory default)设置并从头开始。这听起来像是一项艰巨的任务,但实际上并非如此。
首先,阅读我关于重置无线路由器(wireless router)的帖子,这很容易做到。接下来(Next),如果您没有路由器的文件,请不要担心,因为您可以在路由器本身上找到默认密码,也可以在线找到默认路由器密码。(default password)
一旦您能够登录到您的路由器,您就可以检查网络上分配了哪些 IP 地址。通常,此信息位于主页上的某个位置,可以称为Devices、My Network、IP Address Allocation、Attached Devices、Wireless Status、Connected Devices、DHCP Clients Table等。这实际上取决于您拥有的路由器,但您应该会看到如下所示的列表。
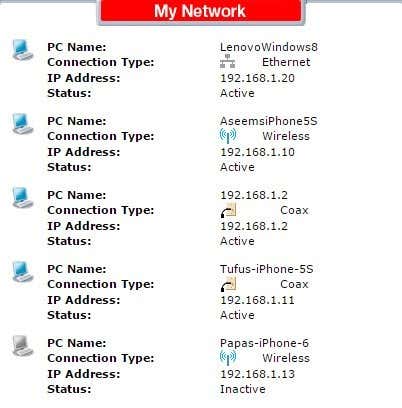
大多数新路由器还会向您显示设备的名称,因此很容易判断设备是手机、平板电脑、打印机、IP 摄像头(IP camera)、NAS、流媒体设备、笔记本电脑还是计算机(laptop or computer)。如果您无法确定与IP 地址(IP address)相关联的设备,您可以随时尝试将该 IP 粘贴到您的网络浏览器(web browser)中,看看它是否加载了网页。一些打印机、相机等将有自己的 Web 界面,您可以通过浏览器连接到这些界面。
如果所有这些都太复杂,另一种查找连接客户端的方法是使用智能手机应用程序(smartphone app)。对于Apple设备,我推荐Net Analyzer Lite和Fing Network Scanner。Fing 也可在Google Play 商店(Google Play Store)中找到。

在大多数情况下,这些应用程序实际上比直接访问路由器要好,因为它们可以为您提供有关设备的更多信息。Fing 甚至可以确定您的网络上是否有控制台,这非常酷。
现在应该很容易找到不应该连接到网络的设备。如果是这种情况,你能做什么?继续阅读以了解如何保护您的无线网络(wireless network)。
安全无线网络
如果您认为您的网络受到威胁,您应该采取的第一步是完全重置您的路由器,如前所述,或者如果当前路由器是旧的,则购买新路由器。如果有人能够连接到您的无线路由器(wireless router),他们也可能已经入侵了路由器,并且可能能够监控网络上的所有活动。
下一步是登录您的路由器并立即更改路由器的默认登录(default login)名。许多人认为设置一个强大的WiFi 密码(WiFi password)就是他们所需要的,但事实并非如此。确实,为了让某人登录您的路由器,他们首先必须连接到无线网络(wireless network)。但是,很多时候,您无法完全信任的客人需要在短时间内连接到您的无线网络。(wireless network)
路由器管理员
连接后,如果他们是黑客类型(hacker type),他们可能会尝试连接到您的路由器并尝试使用默认用户名和密码(default username and password)登录。如果您从未更改过,他们现在可以访问您的路由器并完全控制您的WiFi 网络(WiFi network)。所以请立即更改路由器登录密码(router login password)。

如果您也可以更改用户名,请继续执行此操作。管理员(Admin)绝对是路由器上最常见的用户名,更改它会使某人更难访问您的路由器。如果您有来自ISP的无线路由器,则路由器管理界面(router admin interface)的用户名和密码(username and password)也会直接打印在设备上,因此请务必将其更改为默认值。
您必须浏览各种设置和配置页面(setting and configuration pages),因为这些选项位于不同供应商的不同位置。现在您已经更改了路由器登录信息(router login info),下一步是设置无线安全性。
WPA/WPA2
目前有三种主要方法可以保护您的路由器:在WEP、WPA和WPA2 加密(WPA2 encryption)之间进行选择、禁用SSID 广播(SSID broadcast)和启用无线MAC 身份验证(MAC authentication)。我坚信您确实只需要使用带有长密钥的WPA2 加密(WPA2 encryption)即可非常安全,但有些人喜欢采取额外的预防措施,如果您的设备上存储了非常敏感的信息,那么额外的努力可能是值得的。

某些路由器使您可以轻松完成此操作,例如上面显示的Verizon FIOS 路由器(Verizon FIOS router)高级安全设置页面。如果可能,您应该只使用WPA2 。WEP 非常不安全,WPA很容易被破解。如果您的网络上有设备在设置WPA2后无法连接,那么您应该选择具有WPA + WPA2 Personal的选项。确保选择长密码。请注意,为了安全,它不必是一堆随机数字、符号或字母。强密码必须是长密码。
如果您已按照上述步骤,重置您的路由器,配置管理员密码(admin password)并使用WPA2,您几乎可以确定以前连接到您的无线网络(wireless network)的任何人现在都已断开连接。
如果你想更进一步,你可以阅读我关于禁用SSID 广播(SSID broadcast)的帖子,但它确实不会让你的网络更加安全。启用 MAC 地址过滤(Enabling MAC address filtering)将使您的网络更加安全,但它会让一切变得不那么方便。每次要将新设备连接到网络时,都必须找到设备的MAC 地址(MAC address),登录路由器并将其添加到过滤列表中。
总之,如果您怀疑网络上有异常活动,则应立即执行上述步骤。如果有人连接到您的网络,他们可能会监视您的计算机,因此安全总比抱歉好。如果您有任何问题,请发表评论。享受!
Prevent Someone Else from using Your Wireless Internet Connection
Do you suspect that a neighbоr is using your wireless Internet connection? It could be that yоur Internet connection is slower than it should be or that your devices keep dіsconnecting from the router. Someone connected to уour wireless router can also access shared folders on your network, so data thеft is a real threаt. Luckily, there are ways to detect unknown connections to your network and ways to stop them from connecting.
The main defense against wireless leechers is securing your wireless router. Even though most wireless routers from ISPs come with long passwords, someone can still gain access by simply copying the password printed on your wireless router, since most people don’t change the default password set by their ISP.
If you have a router that you bought on your own, no one will be able to use the password written on the router unless you don’t change the default password. We’ll talk about all this below. Let’s first talk about how to detect wireless leechers.

Detect Unauthorized Wireless Connections
There are basically two ways to go about detecting all the devices connected to your wireless router: either check on the router itself or use a device already connected to the network to scan the entire network. I prefer the latter method because it’s less complicated, however, I will mention both ways.
The first step is to connect to your wireless router from your web browser. In order to do that, you have to type in the IP address for your router. If you don’t know it, read my post on determining the IP of your wireless router. Once you have that, you’ll need to login using the username and password.
If you don’t remember the password or you never changed the default password, that’s a problem. In either of these cases, I recommend resetting your wireless router to factory default settings and starting from scratch. It may sound like a monumental task, but it’s really not.
First, read my post on resetting your wireless router, which is fairly easy to do. Next, don’t worry if you don’t have the paperwork for your router anymore because you can either find the default password on the router itself or you can find default router passwords online.
Once you are able to log into your router, you can check what IP addresses have been allocated on the network. Usually, this information is located somewhere on the main page and can be called something like Devices, My Network, IP Address Allocation, Attached Devices, Wireless Status, Connected Devices, DHCP Clients Table, etc. It really depends on the router you have, but you should see a list like the one shown below.

Most new routers will also show you the name of the devices, so it’s easy to tell if the device is a phone, tablet, printer, IP camera, NAS, streaming device, laptop or computer. If you can’t figure out what device is associated with an IP address, you can always try to paste that IP into your web browser and see if it loads a web page. Some printers, camera, etc. will have their own web interfaces that you can connect to via the browser.
If all of that is too complicated, another method to find connected clients is to use a smartphone app. For Apple devices, I recommend Net Analyzer Lite and Fing Network Scanner. Fing is also available in the Google Play Store.

These apps are actually better than going directly to the router most of the time because they can give you more information about the device. Fing can even figure out if you have a console on your network, which is pretty cool.
Now it should be pretty easy to find a device that is not supposed to be connected to your network. If this is the case, what can you do? Keep reading to find out how to secure your wireless network.
Secure Wireless Network
The first step you should take if you think your network has been compromised is to completely reset your router as mentioned earlier or buy a new router if the current one is old. If someone was able to connect to your wireless router, they could have also compromised the router and may be able to monitor all activity on the network.
The next step is to log into your router and to immediately change the default login for the router. Many people assume that setting a strong WiFi password is all they need, but this is not case. It is true that in order for someone to log into your router, they first have to be connected to the wireless network. However, there are many times when you have guests who you cannot trust fully that need to connect to your wireless network for a short time.
Router Admin
Once connected, if they are the hacker type, they might try connect to your router and try the default username and password to log in. If you never changed it, they now can access your router and have full control over your WiFi network. So change the router login password immediately.

If you can change the username also, go ahead and do that. Admin is the absolute most common username on routers and changing it makes it much harder for someone to gain access to your router. If you have a wireless router from an ISP, the username and password for the router admin interface is also printed right on the device, so make sure to change it from the default values.
You’ll have to poke around the various setting and configuration pages as these options are located in different places for different vendors. Now that you have changed the router login info, the next step is to setup the wireless security.
WPA/WPA2
There are three main ways to secure your router at this point: choosing between WEP, WPA, and WPA2 encryption, disabling SSID broadcast and enabling wireless MAC authentication. I firmly believe you really only need to use WPA2 encryption with a long key to be very secure, but some people like to take extra precautions and it could be worth the extra effort if you have very sensitive information stored on your devices.

Some routers make this really easy for you, like the Verizon FIOS router advanced security settings page shown above. You should only use WPA2, if possible. WEP is very insecure and WPA can be cracked fairly easily. If you have devices on your network that cannot connect once you setup WPA2, then you should pick the option that has WPA + WPA2 Personal. Make sure you choose a long password. Note that it doesn’t have to be a bunch of random numbers, symbols, or letters to be secure. A strong password just has to be a long passphrase.
If you’ve followed the steps above, resetting your router, configuring the admin password and using WPA2, you can pretty much be certain that anyone previously connected to your wireless network is now disconnected.
If you want to go further, you can read my post on disabling SSID broadcast, but it really doesn’t make your network much more secure. Enabling MAC address filtering will make your network more secure, but it makes everything a lot less convenient. Every time you want to connect a new device to your network, you’ll have to find the MAC address for the device, log into your router and add that to the filtering list.
In conclusion, if you suspect unusual activity on your network, you should immediately follow the steps outlined above. There are chances someone may be monitoring your computer if they are connected to your network, so it’s better to be safe than sorry. If you have any questions, post a comment. Enjoy!





